Angler Phishing
Phishing remains a leading cyber threat in 2025, responsible for a vast number of data breaches. Phishers now exploit newer channels beyond email – including social media – to trick victims.
Social platforms like Twitter/X, Facebook and Instagram are home to an emerging phishing scheme called angler phishing.
In an angler phishing attack, the criminal impersonates a company’s customer service account on social media and lures unsuspecting users into scams. By hijacking brand identities and replying to public complaints or queries, angler phishers trick people into revealing credentials or clicking malicious links.
What Is Angler Phishing?
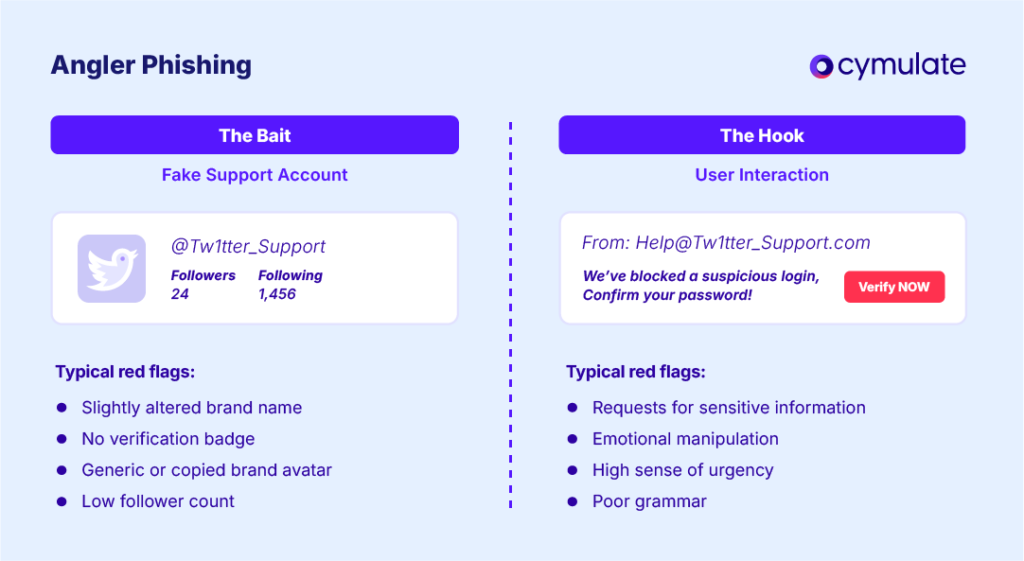
Angler phishing is a social media-based phishing attack in which scammers pose as customer support agents. The attacker creates a fake profile (often using a company’s name, logo, and branding) on a platform like Twitter/X, Facebook or Instagram.
When a real customer publicly complains or asks for help, the phisher “fishes” by responding from the bogus account. They present themselves as helpful support, but their real goal is credential theft or malware delivery.
As Experian notes: “Angler phishing is a type of social engineering attack in which a scammer poses as a customer service representative on social media.” These attacks can be sophisticated: some use nearly perfect copies of official support pages and personalized, friendly messages to fool victims.
How Angler Phishers Manipulate Social Trust
Angler phishers exploit the trust people have in official support channels. They often monitor social feeds for frustrated customers. For example, when someone tweets: “my online order never arrived,” the attacker swoops in pretending to be the brand’s support team.
The fake response might say: “We’re sorry for the trouble! Please click here so we can verify your account and fix the issue.”
The link leads to a malicious site or download. If the user clicks, the site may install malware or prompt for login details. The attacker then harvests this sensitive data to hijack accounts or commit fraud.
Key tactics in angler phishing include:
- Impersonation of Official Accounts: Attackers create accounts with names and avatars mimicking legitimate support channels. They may add words like “support,” “help,” or slight misspellings (e.g. “@Facebokhelp” instead of “@FacebookHelp”).
- Targeting Public Complaints: They focus on users who are already upset or looking for help. Angry or worried customers are more likely to trust a quick reply.
- Malicious Links and Requests: The fake support message typically includes a link or asks for account details. Clicking the link may download malware or open a spoofed login page. Victims might be asked to “confirm” their password or enter a security code – which the attacker then uses to take over accounts.
Unlike email phishing, these scams appear in public or direct messages where people assume official help is nearby. The attacks are insidious and persuasive: victims may genuinely think they’re getting help, when in fact they’re giving attackers the keys to their accounts.
A Realistic Angler Phishing Scenario: How It Unfolds
A typical angler phishing incident might play out like this: Jane posts on Twitter that her internet service has been unexpectedly cut off. Within minutes, a message appears from a handle like @FastNetSupport (note the company name spelled correctly, but the account is newly created).
The message says: “Sorry about your connection issue! Click here to verify your account.” The link points to a web page that looks like the internet provider’s login portal. Jane, grateful for quick help, enters her username and password.
Unbeknownst to her, this is a trap: the fake site captures her credentials, giving the attacker full access to her account. Meanwhile, Jane thinks the issue is resolved – until her account is drained or hijacked.
This scenario illustrates how angler phishing works: by masquerading as official support and leveraging urgency, attackers dupe users into trusting malicious links and divulging sensitive information.
Angler Phishing vs Other Phishing Attacks: Channel of Delivery
Phishing comes in many forms. The table below compares angler phishing with other common phishing types to show their channels, targets, tactics, and examples:
| Type | Channel | Target | Tactics | Example |
| Clone Phishing | General recipients (email users) | The attacker clones a genuine email (e.g. invoice, notification) the victim received, altering links or attachments to malicious ones. Uses familiarity to build trust. | A user receives a copy of a legitimate invoice email from a vendor. The email looks identical, but the “Pay Now” link goes to a fake site that installs malware. | |
| Spear Phishing | Specific individuals or groups | Highly personalized messages crafted for a particular person or small group. Uses personal info (name, role, project details) to appear legitimate and urgent. | An employee gets an email with the company logo addressed personally (“Hi [Name], please review this financial report”). The attachment is malware. | |
| Whaling | Email (or other) | High-level executives (CEO, CFO, etc.) | Targets “big fish” by impersonating trusted executives or business partners. Messages often involve urgent financial requests or sensitive data. | A CFO receives an email appearing to be from the CEO, requesting an immediate wire transfer of company funds to a “trusted vendor.” |
| Vishing | Voice Call (Phone) | Telephone users (usually employees) | “Voice phishing” calls. Scammer pretends to be from a bank, IT department, or helpdesk, asking for codes or account info. Often uses urgency or threats. | A scammer calls an employee claiming to be IT support: “We detected a breach. Tell me your system password and the code sent to your phone to secure your account.” |
| Smishing | SMS/Text Message | Mobile phone users | “SMS phishing.” Fraudulent text messages impersonate banks, delivery companies, etc., with links or callbacks. Aims to get credentials or install mobile malware. | A user receives a text: “Your bank detected unusual activity. Visit bank-verify.app to confirm your identity.” The link leads to a fake banking site that steals login details. |
| Business Email Compromise (BEC) | Email (Business) | Employees managing money (Finance) | Scammer spoofs a trusted corporate email (CEO, lawyer, vendor) to trick employees into wire transfers or revealing sensitive data. Usually involves social engineering over time. | An employee in accounts payable gets an email from “Vendor X” saying payment details changed. The new bank account is owned by the attacker, not the real vendor. |
| Angler Phishing | Social Media (Twitter, Facebook, Instagram, etc.) | Consumers or customers reaching out on social platforms | Fake support accounts mimic real ones and reply to customer complaints. Messages contain malicious links or requests (e.g. “verify account details here”). Victims trust the social proof of support. | A customer tweets about a bank login issue. A fake account “@BankSupportTeam” responds with a link to “secure your account.” The link leads to a phishing page that steals login credentials. |
Recognize and Block Angler Phishing Attempts
Defending against angler phishing requires both technology and awareness. Organizations should educate users and enforce security measures:
1. Verify Official Accounts
Always double-check that social media responses are from legitimate company profiles. Look for verified badges or compare URLs and usernames carefully before interacting. If in doubt, initiate a new support request via the company’s official website or known channels.
2. Be Cautious with Links and Attachments
Never click links or open attachments from unsolicited social media messages. Instead of clicking, independently navigate to the official website or support portal. Hover over links (if possible) to see the actual URL and ensure it matches the real domain.
3. Use Multi-Factor Authentication (MFA)
Require MFA for all important accounts. Even if credentials are phished, MFA can prevent attackers from using stolen passwords alone to log in. (Phishing-resistant methods like hardware tokens or authenticator apps provide stronger protection than SMS codes.)
4. Block and Report Fake Accounts
When users spot suspicious support accounts, they should block and report them immediately to the social platform. Reporting helps the platform take down malicious profiles and protect other users.
5. Train with the SLAM Method
Incorporate phishing awareness training focused on social media threats. For example, the SLAM method teaches users to examine the Sender, Links, Attachments and Message of any communication for red flags.
Encourage employees to stop and analyze any unexpected support request before responding. Regular simulations and refreshers (see Cymulate’s blog on phishing awareness training for tips) will keep vigilance high.
Cymulate’s Phishing Awareness and Continuous Validation
Cymulate helps organizations stay ahead of threats like angler phishing through continuous threat exposure validation. The Cymulate Phishing Awareness Assessment simulates real phishing scenarios (including social media lures) to measure employees' security awareness
Insight from these simulations guides targeted training and highlights weaknesses in user behavior. In addition, Cymulate’s broader Breach and Attack Simulation offering can test email gateways, web filters and endpoint defenses against the full spectrum of phishing threats.
With awareness programs, verification practices and Cymulate’s continuous testing, security teams can protect their organizations and customers from angler phishing and other evolving phishing attack types.

