Ransomware
From Infection to Extortion: Breaking Down the Ransomware Threat
Ransomware is a form of malicious software (malware) designed to block access to a computer system or data until a ransom is paid. It can encrypt files, lock access to entire systems, or exfiltrate sensitive data with threats of publication. Ransomware has evolved from a disruptive annoyance to one of the most severe threats facing organizations of all sizes across every sector.
All companies are susceptible to ransomware attacks, regardless of the organization’s size or industry. The Sophos State of Ransomware Survey 2024 report found that organizations who paid ransom reported an average payment of $2 million USD. Additionally, the average cost of recovery was $2.73 million USD.
Ransomware campaigns are designed for maximum impact, using increasingly advanced tactics to ensure victims feel they have no choice but to pay. For example:
- They feature unbreakable encryption, preventing victims from decrypting the files on their own.
- They have a dead man’s switch; once the ransom is not paid on time, either the data is destroyed forever or stolen data is published, further tarnishing the brand image of the targeted organization or the individual reputation.
- They can encrypt all kinds of files, including documents, pictures, videos and audio files.
- They can scramble file names, preventing victims from knowing which data was affected.
- It uses a complex set of evasion techniques to bypass traditional antivirus.
- They display a ransom note message with payment instructions in cryptocurrency to avoid detection.
Ransomware Attack Lifecycle
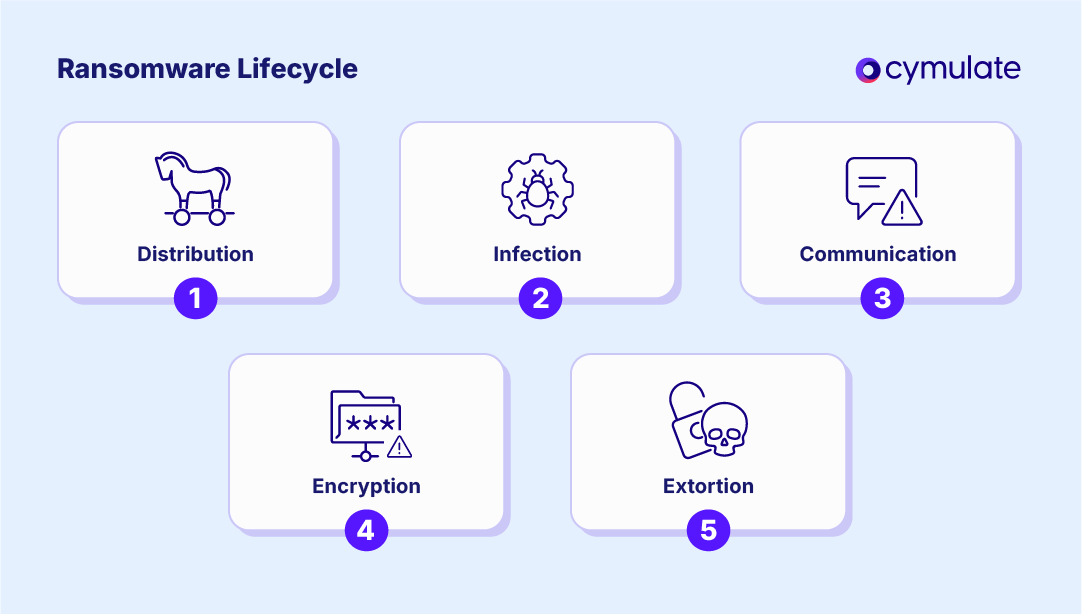
Ransomware attacks usually follow a five-phase lifecycle. Despite variations in delivery methods and malware code, the kill chain often unfolds as follows:
1. Distribution
Typically, the ransomware attacker successfully tricks its target into clicking an infected link, downloading an attachment, or accessing a compromised website, and the malware gains access to the target’s endpoint. They also resort to other distribution techniques, such as acquiring Remote Desktop Protocol (RDP) either through direct attack or by purchasing stolen ones, through exploiting unpatched vulnerabilities, or even through brute force attempts.
2. Infection
The distributed malware installs itself on the infected endpoint, launches new processes, and attempts to progress laterally and vertically within the organization’s network. Depending on the specific degree of malware sophistication, this step might include a stealth phase designed to maximize its reach across a network or immediately proceed to the next step.
3. Communication
In some, still rare cases, the malicious code contacts the attacker’s server and begins exfiltrating as much content and data as possible. At the same time, it scans your content with a view to encrypt it and sometimes also attempts to uncover access to accessible backups it could also infect.
4. Encryption
Having ascertained that it has reached its maximum possible reach prior to detection, the attack proceeds by encrypting files as widely as possible.
5. Extortion
The attacker ensures that the only content accessible from the infected network or endpoint is the message requiring payment, typically in cryptocurrency, in exchange for a decryption key. Today, double and triple extortion processes are becoming the norm. From a technical perspective, the additional extortion steps leverage the data acquired during the communication phase, so extortion is the last step of the cyber part of the attack.
Why Ransomware Is So Effective
Ransomware is designed with features that make it highly effective and difficult to counter, because it:
- Uses unbreakable encryption, leaving victims unable to recover data without the attacker’s key
- Employs “dead man’s switches”: if the ransom is unpaid, data is deleted or leaked
- Encrypts all file types, including documents, images, videos and executables
- Scrambles file names, making identification and triage difficult
- Uses evasion techniques to bypass antivirus and security controls
- Demands payment via anonymous cryptocurrency to avoid traceability
The Devastating Impact of Ransomware
The impact of ransomware attacks goes far beyond the ransom itself:
- Business interruption: Systems are paralyzed during and after the attack
- Data loss: Even when paid, decryption is not guaranteed
- Legal and regulatory costs: Disclosure obligations and breach response create liability
- Reputational damage: Customers and stakeholders lose trust
- Blackmail risks: Stolen data may be used to further extort victims
- Insurance complications: Claims may be denied if coverage terms were not strictly followed
- Recovery complexity: Restoring systems is time-consuming and may require rebuilding environments from scratch
The Primary Targets of Ransomware
Ransomware attackers do not discriminate. While Banking, Financial Services, Utilities, and Retail have been historically frequent targets, every sector is vulnerable.
Smaller organizations are especially at risk due to limited cybersecurity resources and a lower likelihood of mounting a defense or forensic investigation.
Attackers often tailor ransom amounts to victims’ perceived ability to pay, with smaller ransoms for easier targets and multimillion-dollar demands for larger entities.
Typology: 7 Major Ransomware Types
Modern ransomware falls into several categories, based on tactics and goals:
- Encrypting Ransomware uses advanced encryption algorithms to block system files. Ransom demand is shown on the screen, demanding that the user pays for the decryption key to unblock the files.
- Locker Ransomware locks the victim out of the operating system, which makes it impossible to access the desktop, applications, and files. Although the files are not encrypted, the attackers still ask for a ransom to unlock the infected computer.
- MBR Ransomware is a type of locker ransomware that infects the Master Boot Record (MBR), preventing the operating system from booting up. Failure of the boot process prompts a ransom note to be displayed on the screen, demanding a ransom to unlock the MBR.
- Scareware is a different type of ransomware that falsely claims to have uncovered an issue on your device and requires payment to fix it.
- Doxware or Leakware, is the blackmailing version of ransomware, where the attacker threatens to reveal compromising information about the victim organization or individual unless payment is sent. Now also used as a second-tier attack to encrypting ransomware, as attackers either threaten to publish the stolen data or approach the victim organization’s users directly to make them pressure the organization into paying.
- Wiping Ransomware is a type of ransomware attack where the data is totally erased. In some rare cases, the attackers also demand payment to restore it, even if they have no intention to do so.
- RaaS (Ransomware as a Service) is an off-the-shelf ransomware software that can be purchased as a service, in the same way as a SaaS (Software as a Service) for regular services. The emergence of RaaS has given access to ransomware technology to thousands of wannabe hackers who, until then, lacked the technological capability to launch a ransomware attack.
Best Practices for Reducing Ransomware Damage
To minimize the consequences of a ransomware breach, organizations should adopt the following practices:
- Update all systems and software regularly
- Keep IDS and antivirus systems up to date
- Apply the principle of least privilege
- Segment IT and OT networks
- Avoid open access to RDP (port 3389) and SMB (port 445)
- Use MFA extensively
- Maintain encrypted, offline backups and test recovery procedures regularly
- Develop and test incident response playbooks
Proactive Measures Against Ransomware
While hygiene practices help, proactive validation of defenses is essential to prevent breaches:
- Annual or biannual pen-testing is no longer sufficient due to evolving threats and rapid infrastructure changes
- Continuous security validation can test resilience against real-world ransomware payloads
- Emulation of ransomware behaviors-file scanning, asymmetric encryption, exfiltration-is critical
- Integration with EDR and XDR systems enables detection vs. execution gap analysis
How Cymulate Helps Organizations Defend Against Ransomware
Cymulate provides a comprehensive platform for assessing and strengthening an organization’s ransomware resilience, including:
Assessment Capabilities
- Simulates full ransomware kill-chain with production-safe payloads
- Includes daily threat intelligence updates to assess new and emerging ransomware threats
- Evaluates breach feasibility and provides real-time detection feedback
Validation & Reporting
- Runs multi-step attack scenarios across vectors: Email Gateway, Web Gateway, Endpoint, WAF and more
- Correlates simulation outcomes with detection tools to identify gaps
- Generates detailed technical and executive reports for mitigation guidance and strategic planning
Integrated XSPM Modules
- Red Teaming Automation: Simulates end-to-end adversarial campaigns
- Breach and Attack Simulation (BAS): Tests and tunes controls in real-world conditions
- Advanced Purple Teaming: Custom attack chains built on MITRE ATT&CK for response exercises
- Attack-Based Vulnerability Management (ABVM): Prioritizes patching based on actual exploitability
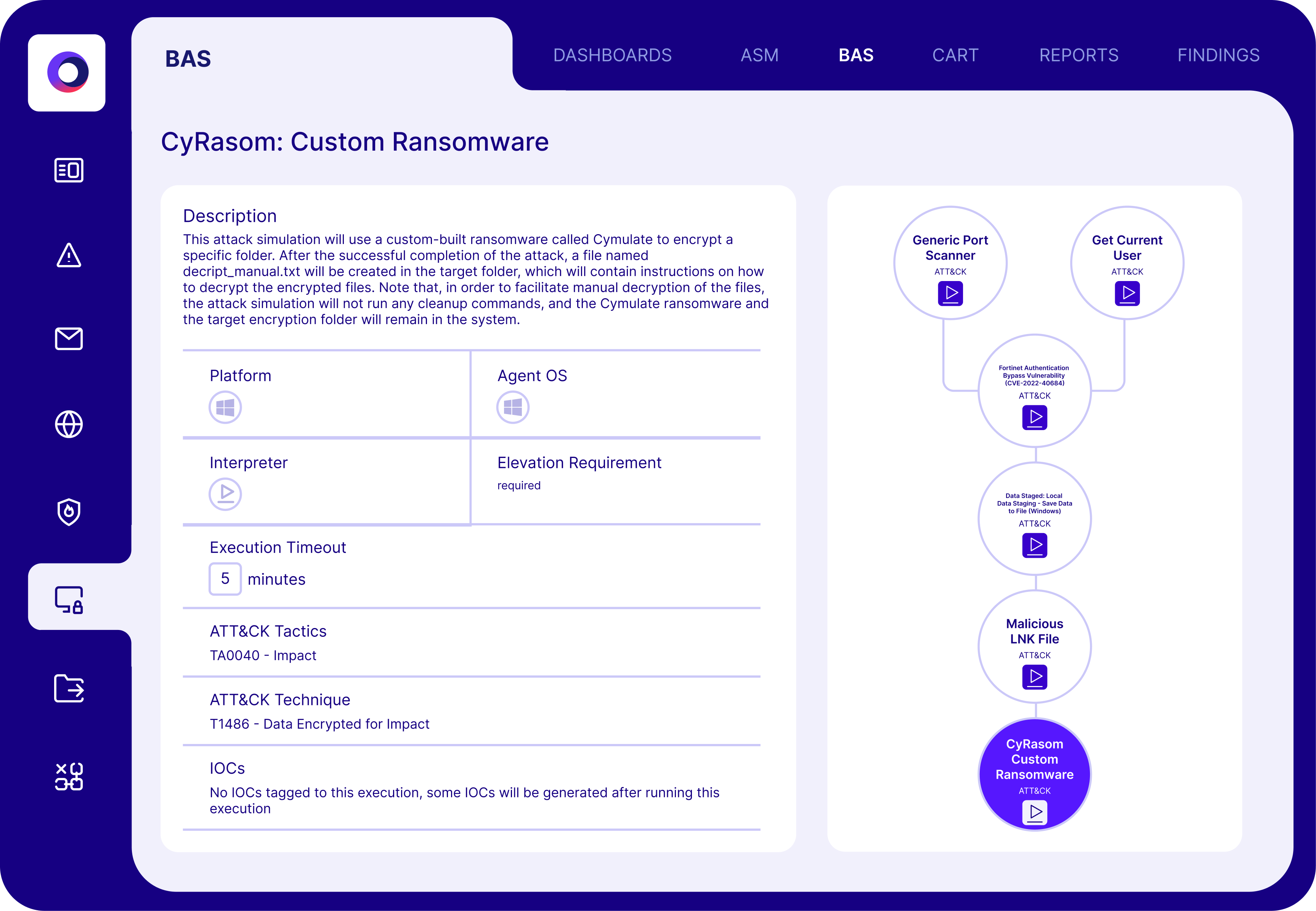
Cymulate empowers security teams, regardless of maturity level, to make informed, data-driven decisions, strengthen their security posture and reduce exposure to ransomware and other attack types.


