Akira Ransomware: How to Test and Validate Your Exposure

Akira Ransomware is back in the headlines after the threat group published a record number of new victims' data on their darknet leak site last Monday. Cymulate first became aware of Akira back in 2023 when they appeared on our radar on multiple occasions and then again on April 18, 2024, when CISA issued the Cybersecurity Alert:
#StopRansomware: Akira Ransomware (Alert Code: AA24-109A)
According to CISA, Akira Ransomware has impacted a wide range of businesses and critical infrastructure entities in North America, Europe and Australia since March 2023. The threat group is responsible for attacks against some 250 organizations (many of which were small to medium sized businesses) and extorting over $42 million in ransom payments.
Akira is believed to have ties to the former Conti ransomware group, employing a ransomware-as-a-service (RaaS) model to scale their operations. Their latest data leaks indicate a possible partnership with new affiliates, leveraging RaaS to target an increasing pool of victims.
Akira Uses Double Extortion Tactics
Akira threat actors gain initial access to organizations by:
- Exploiting known VPN vulnerabilities (e.g., Cisco).
- Absence of multi-factor authentication (MFA).
- Spear phishing campaigns.
- Stolen credentials to infiltrate networks.
Once inside, Akira threat actors:
- Compromise domain controllers to create new domain accounts.
- Establish persistence and conduct reconnaissance.
- Identify high-value systems for exfiltration and encryption.
Akira threat actors apply double extortion tactics:
- Exfiltrate sensitive data and encrypt critical systems.
- Pay ransom to receive encryption keys.
- Refuse to pay ransom and have stolen data leaked to Akira’s darknet site.
Akira recently leaked data from over 30 victims in a single week, marking a sharp rise in their threat activity.
Are Your Security Controls Ready for Akira Ransomware?
Many organizations who follow the cyber headlines and see themselves as a potential target in the cross hairs of Akira will be asking themselves the question: Are we exposed?
Given Akira’s sophisticated tactics and techniques, answering this question with conviction is going to test the resolve of any CISO who is willing to speculate that their security controls are indeed configured and tuned to stop this attack.
Cymulate enables organizations to answer this question with confidence. Over the past year, Cymulate has tracked Akira Ransomware and continuously updated threat simulations to help customers test and validate their exposure to this evolving threat.
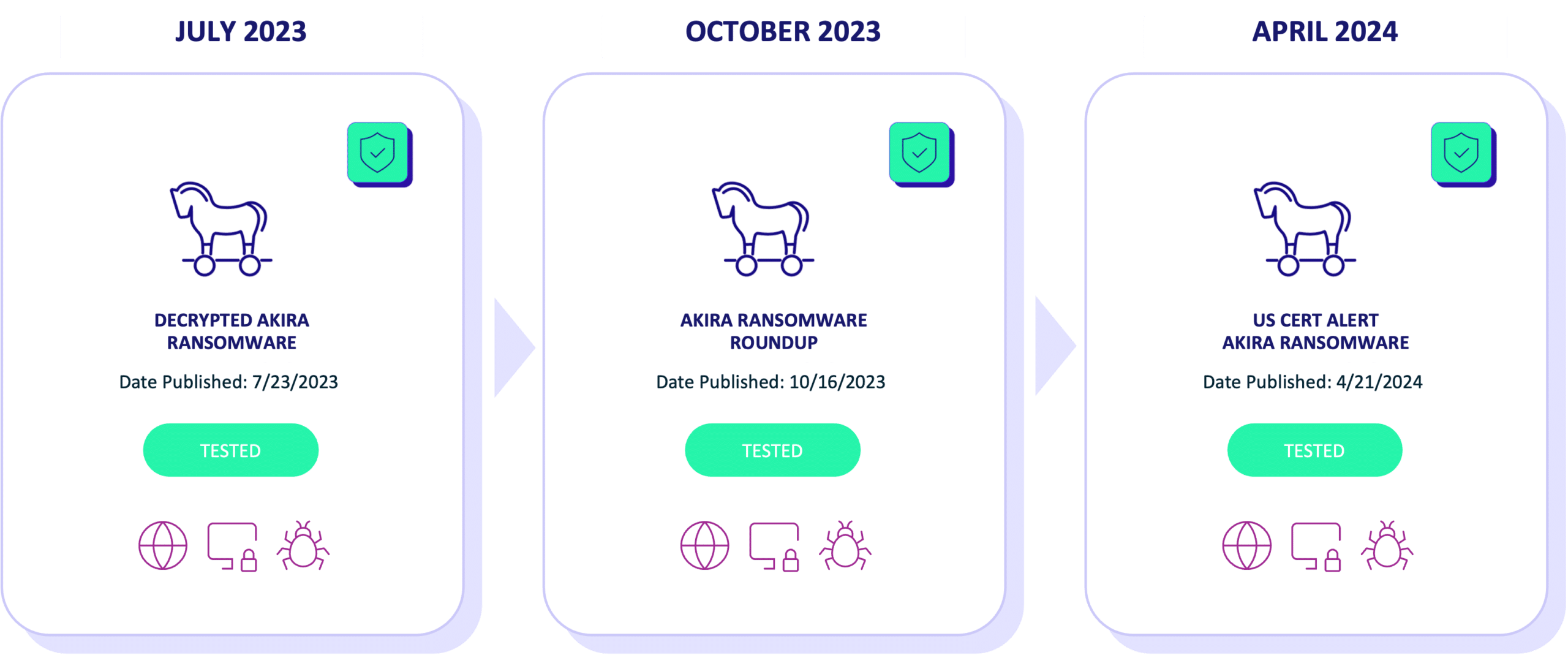
Simulating Akira Ransomware Attacks
When CISA issued the cybersecurity alert on April 18, 2024, the Cymulate Threat Research Group responded quickly, adding an immediate threat simulation to the Cymulate platform within three days. This simulation allowed organizations to test their exposure to Akira Ransomware by replicating the tactics and techniques used by the threat group in a production-safe environment.
How the Simulation Works
- Malicious payload delivery: The simulation sends payloads associated with Akira ransomware in a safe, controlled manner.
- Validation of security controls: It evaluates whether these payloads are blocked or if they penetrate existing defenses to compromise systems.
Key Findings
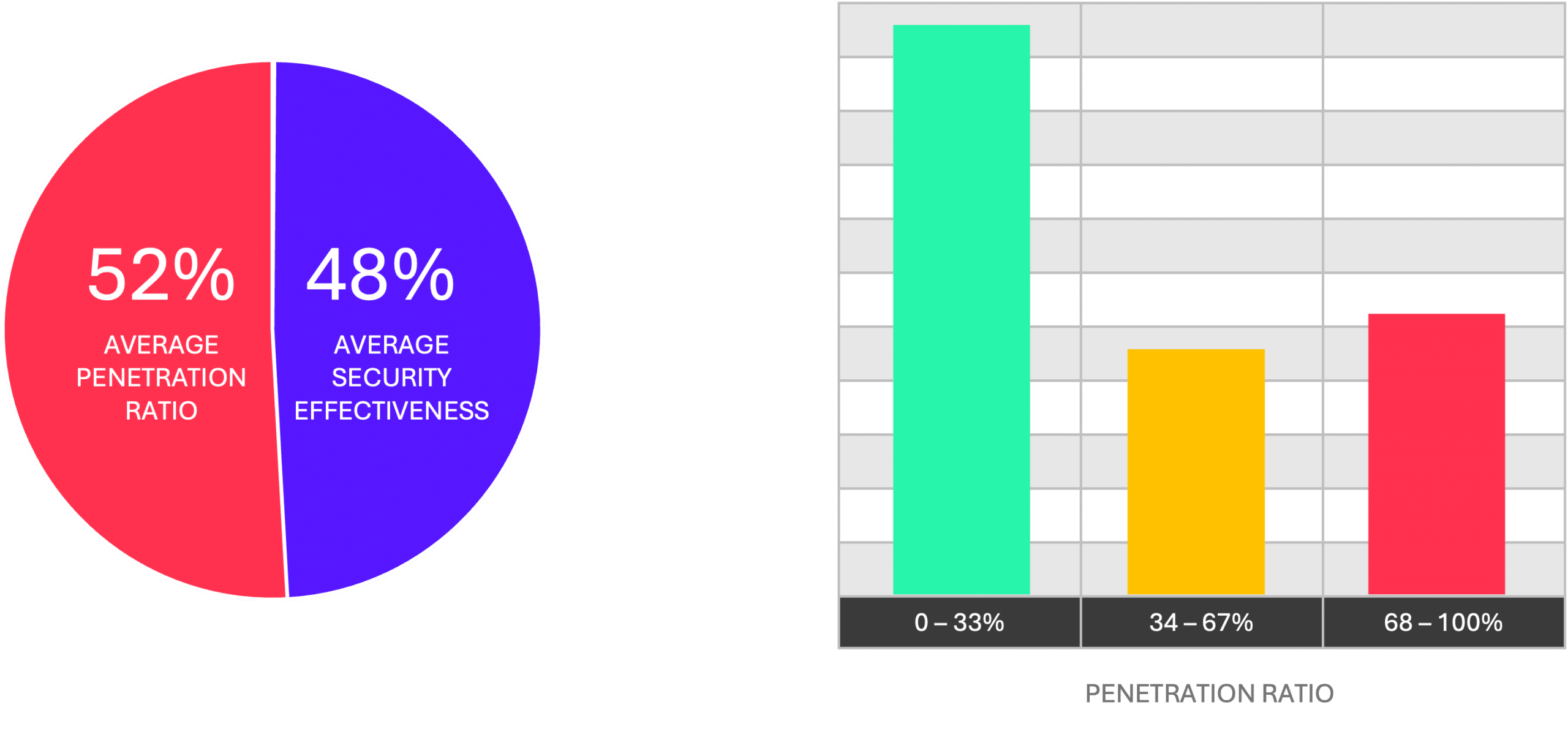
- 52% average penetration ratio: This figure highlights the evolving sophistication of Akira's tactics and their ability to penetrate web gateways and endpoint security solutions in many organizations.
- 100% effectiveness for some customers: Several organizations achieved a 0% penetration ratio, successfully blocking all tested payloads. These results provided clear evidence of effective security configurations and no exposure to Akira ransomware.
- Reduced exposure for many: Customers with penetration ratios below 33% managed to block most of the payloads, significantly lowering their risk of compromise.
- Critical gaps identified: Organizations with 100% penetration ratios recognized critical security gaps. Using Cymulate’s mitigation guidance and IOCs, these customers can address vulnerabilities and improve defenses against future attacks.
- Remediation actions reduce exposure: Organizations who undertook remediation actions were able to reduce their exposure by an average of 30 basis points within 30 days of conducting their initial assessment.
Continuous Validation: The Key to Cyber Resilience
The Cymulate Threat Research Group monitors the threat intelligence community and loads new immediate threat simulations into the Cymulate platform on a daily basis. Customers who configure immediate threats for auto-run will automatically validate their security controls against new threats and receive notifications any time they have exposure to a threat.
Organizations invest significant time and money when implementing and managing multiple layers of security controls to keep them protected. To keep up with the constantly evolving threat landscape and the latest threat tactics, you need to continuously validate the effectiveness of your controls by simulating the latest immediate threats and attack scenarios. This is the only way to truly know if your controls are operating as intended and doing their job effectively.
Proactive Steps to Prevent an Akira Breach
Unfortunately, organizations who fell victim to Akira Ransomware in the last 18 months had security controls that failed to protect their data. For those organizations that seek more proactive security measures to avoid becoming the next victim, we recommend:
- Simulating Akira Ransomware attacks to identify weaknesses in your defenses.
- Applying mitigation guidance to close security gaps.
- Implementing automated security validation to adapt to these evolving threats.
Validating your security controls will prevent you from becoming the next breach victim.