Web Application Firewall (WAF)
In today’s modern cybersecurity network made up of innumerable endpoints, servers and web-based tools, implementing a Web Application Firewall (WAF) has become an integral component of a clever and well-rounded security defense.
What is a Web Application Firewall (WAF)?
A WAF can safeguard web applications from common threats such as command injection, cross-site scripting (XSS), cross-site request forgery (CSRF) as well as other vulnerabilities used by threat actors. Throughout this article, we will cover how WAFs function, their overall importance, and how they can benefit exposure management.
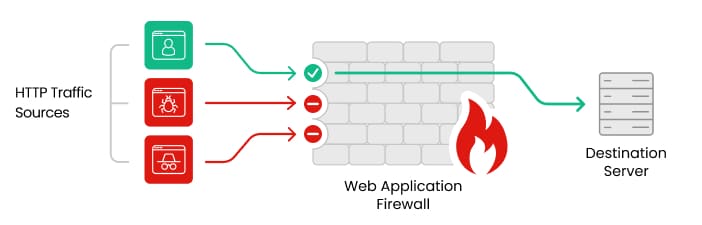
How do Web Application Firewalls (WAFs) work?
By preventing any unauthorized data from escaping a particular web application, a WAF protects an organization’s web application by monitoring, filtering and blocking any malicious HTTP/S traffic . WAFs as their name implies, are most effective at protecting applications against web-based attacks and are a protocol layer 7 defense in the Open Systems Interconnection (OSI) model.
As a traffic monitor, a WAF can analyze incoming and outgoing web traffic to identify and filter harmful requests. Using rule-based filtering, predefined rules or policies are implemented to detect and block suspicious patterns or behaviors. Advanced WAFs can employ machine learning and behavioral analysis, covering rules that might not be static in nature.
Organizations come in all shapes and sizes that require different types of supporting infrastructures. WAFs offer three primary deployment models to help ensure an easy transition from planning to installation: on-premises solutions, cloud-based solutions and hybrid approaches.
- On-premises solutions involve installing WAF appliances or software in a physical on-site location, typically within the organization's data center. This model provides organizations with full control and visibility over their WAF infrastructure but requires dedicated resources for hardware maintenance and management.
- Cloud-based solutions are offered as a service by providers like AWS WAF or Azure Front Door. Organizations can subscribe to a cloud-based WAF service, eliminating the need for on-site hardware and reducing maintenance overhead while scaling and updating easily with quick deployment.
- Hybrid approaches to WAF deployment combine both on-premises and cloud-based solutions. Organizations can use on-premises WAFs for specific applications or data and leverage cloud-based WAF services for others. This approach provides flexibility, allowing organizations to customize their WAF deployment based on specific requirements and security needs.
Selecting the Right WAF for Your Needs
Selecting the right Web Application Firewall (WAF) is crucial to ensure effective protection for your web applications, while also considering business-wide factors. Consider the following factors when choosing a WAF:
- Deployment Options: As mentioned above, ensure that the vendor selected offers the flexibility needed, whether that is cloud-based, on-premises or a hybrid solution.
- Cost and Licensing: Understanding the pricing structure upfront can make all the difference. Pricing can vary based on deployment type, traffic volume, maintenance, support, upgrades, and additional features.
- Compliance Requirements: A good WAF should help meet your organization’s regulatory and compliance requirements, like GDPR, HIPAA, or PCI-DSS.
- Security Requirements: Identify the specific security needs of your organization, including compliance requirements, industry standards, and the sensitivity of your data.
- Scalability and Performance: Evaluate the scalability and performance capabilities of the WAF solution to help ensure it can handle your current and future web application traffic.
- Feature Set: Assess the features and capabilities of the WAF, such as DDoS protection, advanced bot mitigation, and API security, to meet your specific security needs.
- Integration: Determine how the WAF integrates with your existing security infrastructure, such as firewalls, IDS/IPS systems, and SIEM solutions.
- Vendor Support: Consider the vendor's reputation, support services, and availability of updates and patches.
By carefully considering these factors, you can select the best WAF solution that aligns with your organization's security requirements and provides robust protection for your web applications.
Frequently Asked Questions about WAF's
1. What are the most common threats that WAFs protect against?
WAFs protect against common web application threats, including command injection, SQL injection, XML injection, cross-site scripting (XSS), DDoS attacks, malicious bots, and bad bots.
2. How does a WAF differ from a Content Delivery Network (CDN)?
While a Content Delivery Network (CDN) focuses on optimizing web content delivery, a WAF is specifically designed to protect web applications from malicious traffic and attacks.
3. Can WAFs provide complete protection against all web vulnerabilities?
While WAFs provide robust protection against a wide range of web vulnerabilities, they cannot guarantee complete protection against all threats, especially zero-day vulnerabilities. Layered security measures are recommended for comprehensive protection.
4. How do I determine if my organization needs a WAF?
Consider factors such as the nature of your web applications, the sensitivity of the data being processed, and compliance requirements like PCI DSS. A WAF is recommended if your organization handles sensitive data or has compliance requirements.

