Measure and Baseline Cyber Resilience
Continuously validate controls and policies to baseline and measure security resilience and business risk.
Do you have the metrics to prove that your security program is ready for the next threat?
Security executives
manually compile data
Source: Osterman Research
CISOs don’t feel aligned
with their executives
Source: FTI Consulting
CISOs struggle to explain
technical concepts
Source: FTI Consulting
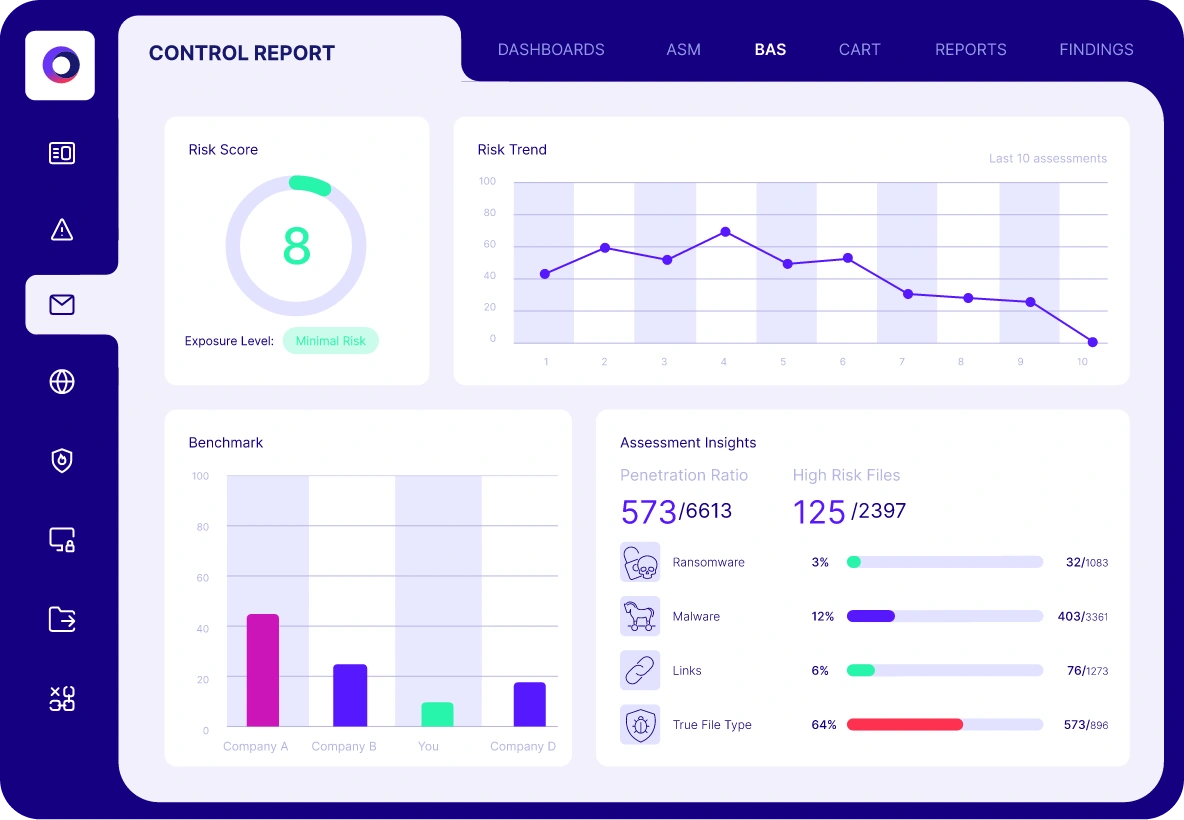
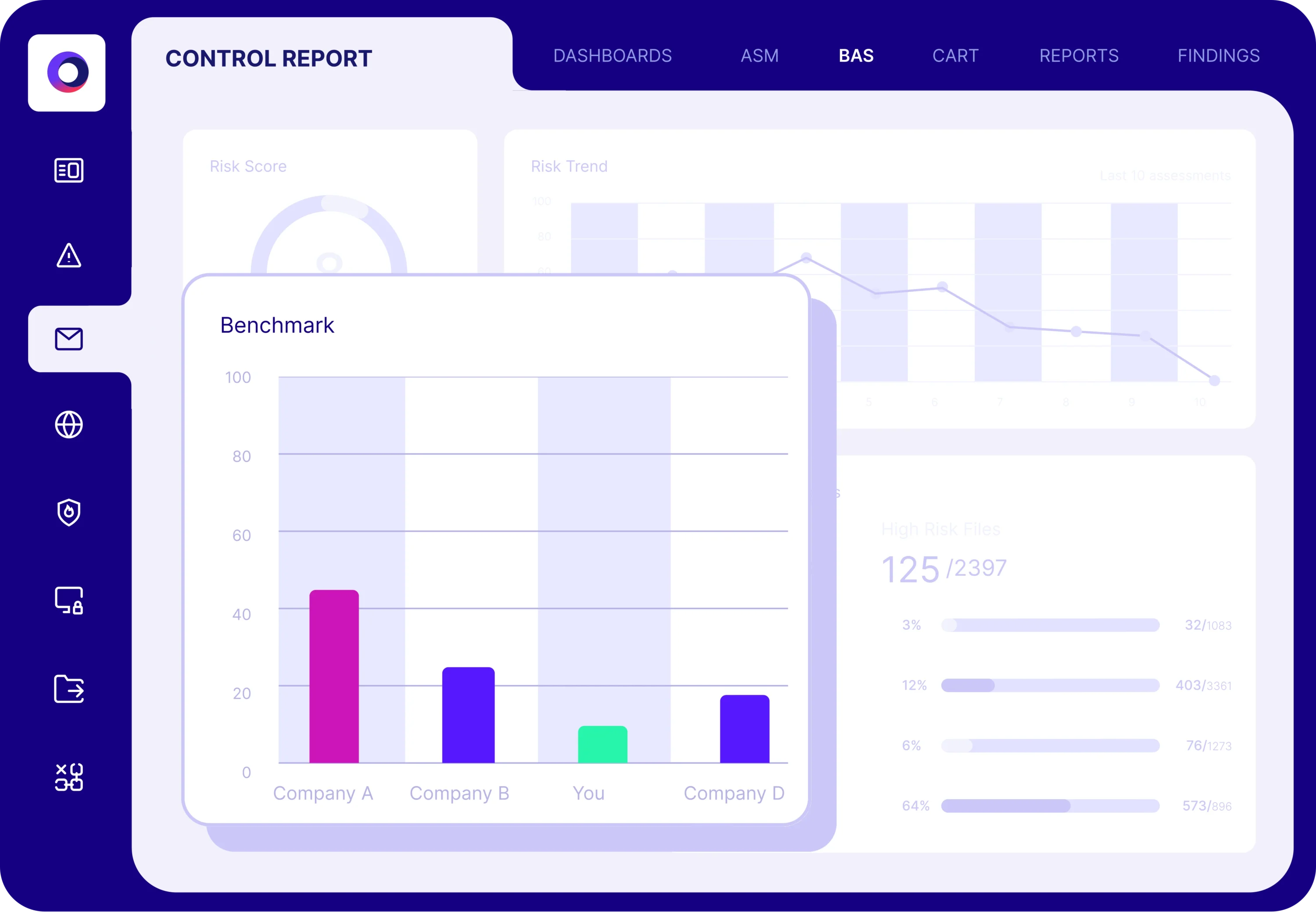
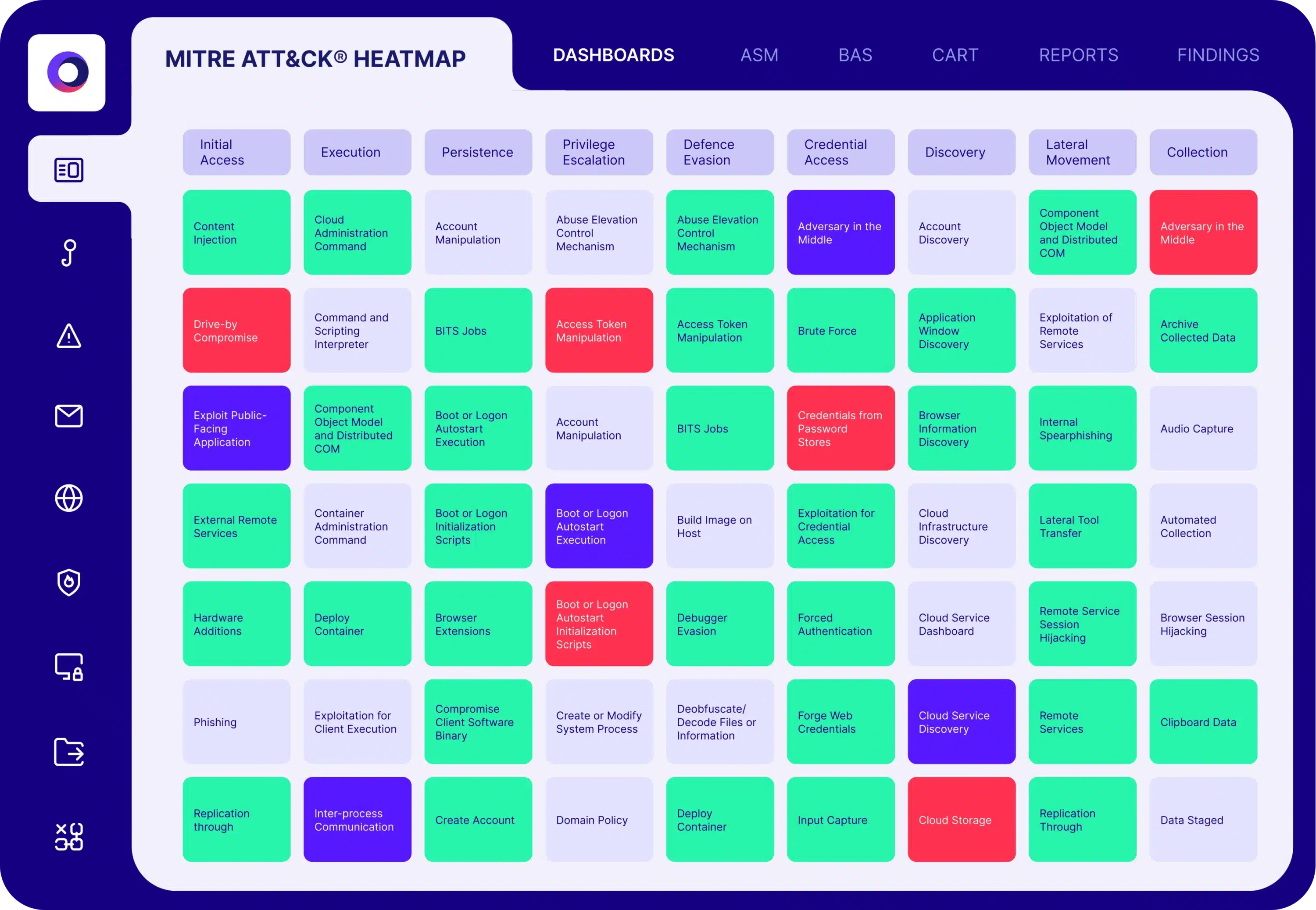
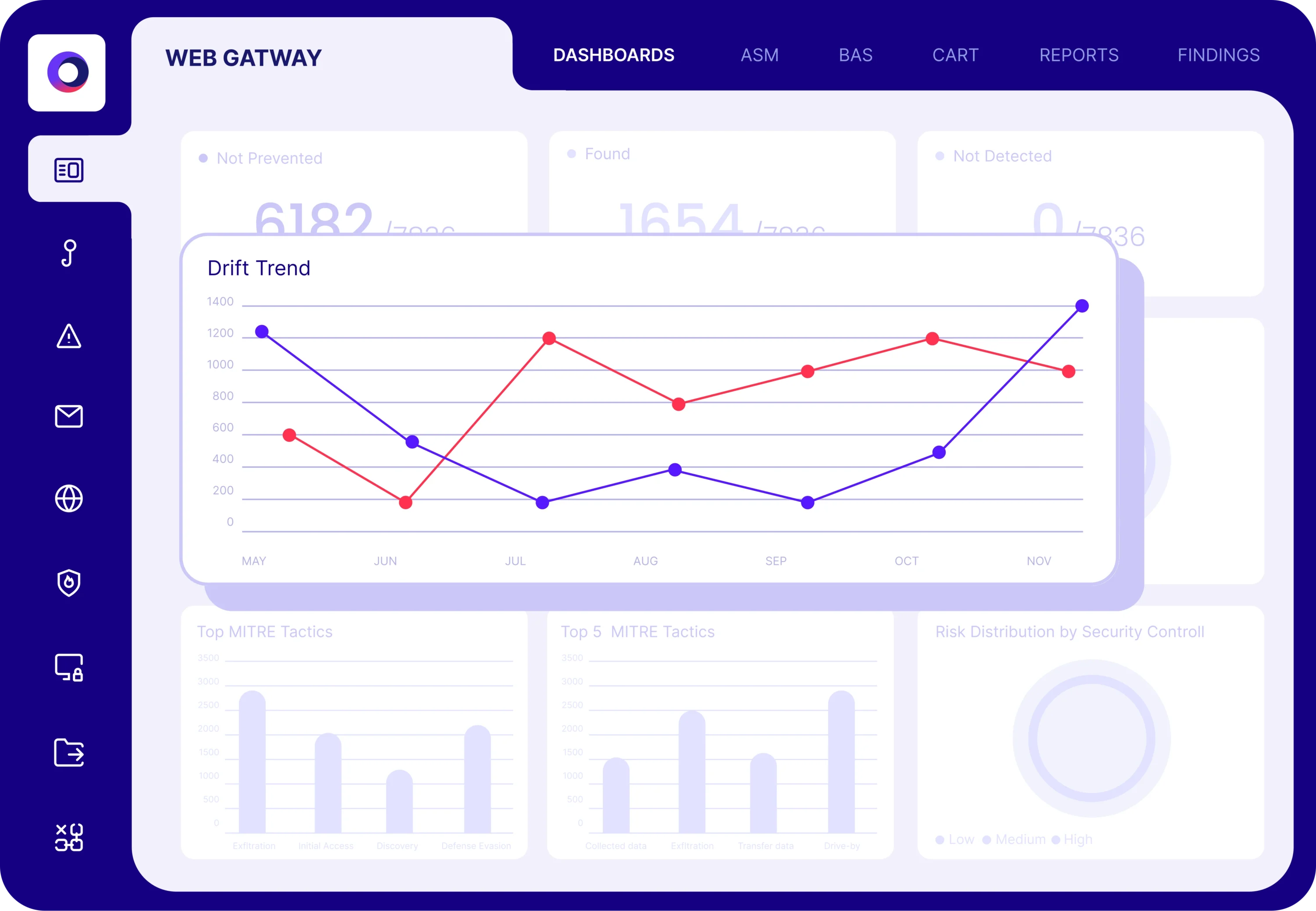
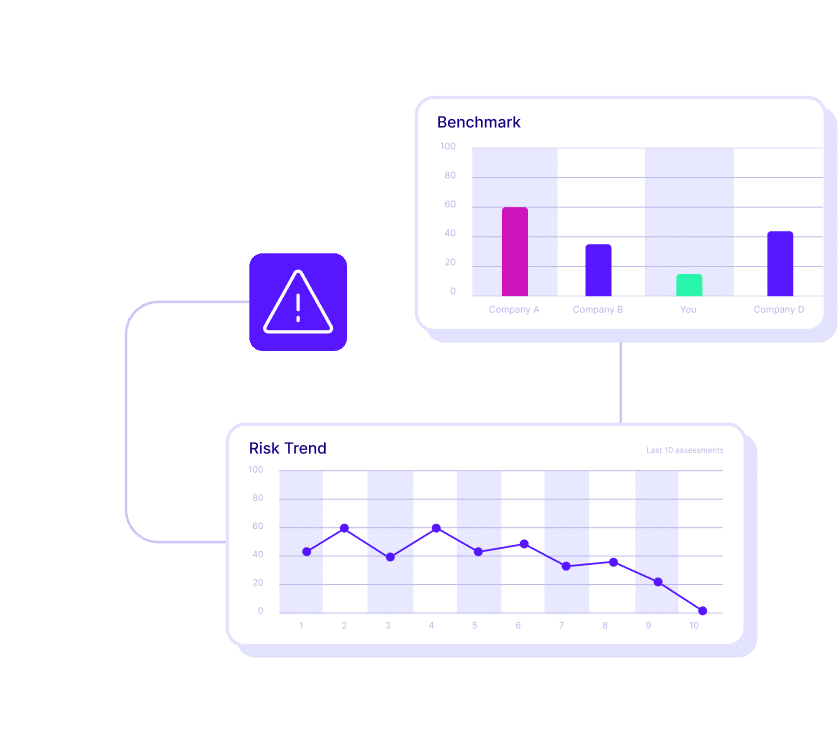
Validation provides metrics to baseline your security program
To deliver measurable results, you must start by evaluating the current state of your organization’s defenses. The Cymulate Exposure Management Platform validates true threat exposure to baseline and measure security resilience and business risk.
The platform’s dynamic dashboards and reporting allow you to measure and communicate cyber resilience to executives, boards and their peers while prioritizing new investments and measuring improvement.
Solution Results
17
Subsidiaries with the same cyber metrics
manufacturing company
81%
Improvement in risk score in four months
global transportation
$2M
Save with cheaper,
on-par email gateway
it company
Solution Benefits
Customers are saying...
Organizations across all industries choose Cymulate for automated security validation, proactively confirming that defenses are robust and reliable-before an attack occurs.