Frequently Asked Questions
SIEM Validation Features & Capabilities
What is Cymulate's SIEM Validation?
Cymulate's SIEM Validation is an automated solution that uses breach and attack simulations to test and optimize the effectiveness of your SIEM detection rules. It enables organizations to validate SIEM deployments, identify detection gaps, and optimize security controls against the latest attack tactics and techniques. Source
How does Cymulate validate SIEM detections?
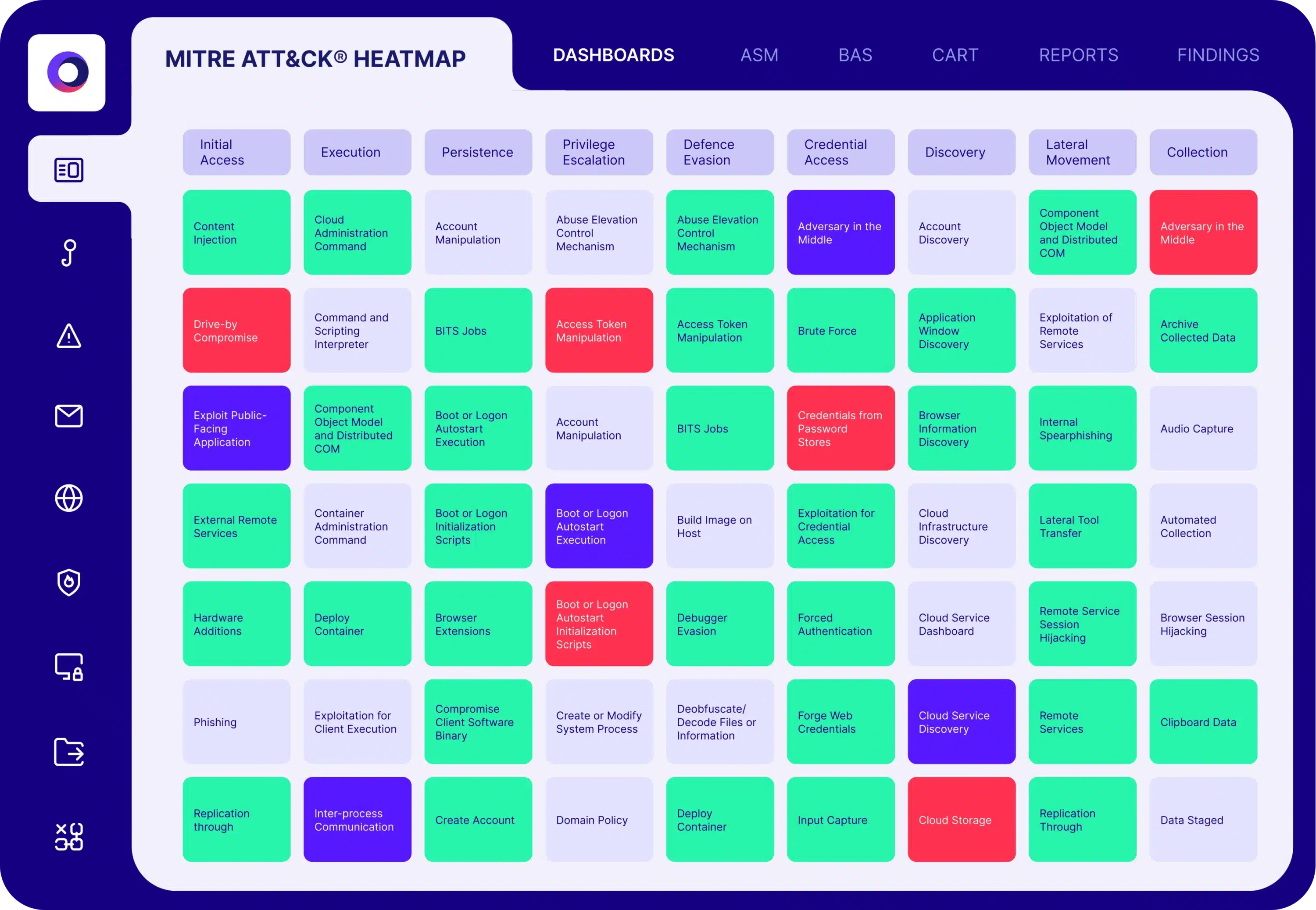
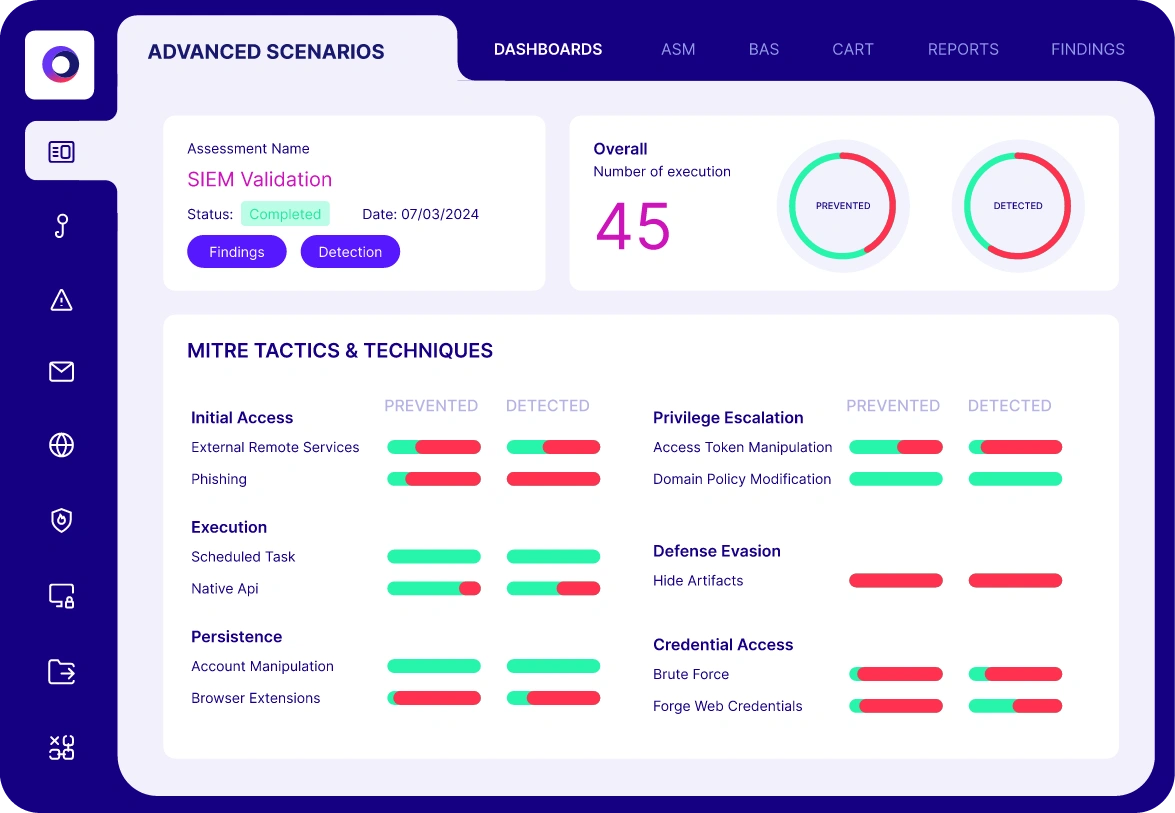
Cymulate automates production-safe testing by simulating various attack scenarios and high-privileged activities. It validates both the visibility of log collection and the analysis that produces actionable alerts, using MITRE ATT&CK heatmaps to visualize threat coverage. Source
What types of threats and scenarios does SIEM Validation cover?
Cymulate's SIEM Validation covers immediate threats, endpoint threats, cloud and container threats, assume breach (high-privilege) threats, and other persistent threats. Source
What are the main features of Cymulate's SIEM Validation solution?
Main features include automated breach and attack simulation, MITRE ATT&CK heatmaps, pre-existing and customizable attack templates, a library of over 2,000 attack techniques, Sigma rule generation, detailed findings and reports, and direct integration with SIEM platforms. Source
How does Cymulate help optimize SIEM detection rules?
Cymulate enables organizations to tune SIEM detection rules by identifying missed detections, reducing false positives, and providing actionable recommendations and Sigma rules for improved detection accuracy. Source
What is Sigma rule generation in Cymulate?
Sigma rule generation in Cymulate allows users to automatically create and translate Sigma rules for their specific SIEM integration, helping to mitigate detection gaps and directly apply improved detection logic. Source
How does Cymulate support custom attack scenarios for SIEM validation?
Cymulate provides pre-existing templates and allows users to build custom attacks from a library of over 2,000 common attack techniques or user-supplied executions, files, and Sigma rules. Source
What kind of reports does Cymulate's SIEM Validation provide?
Cymulate provides detailed findings and reports that offer deep insights into detection results, attack techniques, alerts and events triggered, and includes suggestions and mitigation guidelines for more accurate detection rules. Source
How does Cymulate visualize SIEM threat coverage?
Cymulate uses MITRE ATT&CK heatmaps to visualize SIEM threat coverage, helping organizations understand which attack techniques are detected and where gaps exist. Source
What is the benefit of continuous SIEM validation?
Continuous SIEM validation ensures that detection capabilities are always tested against the latest attack techniques, helping organizations stay ahead of evolving threats and reducing the risk of undetected incidents. Source
SIEM Validation Results & Metrics
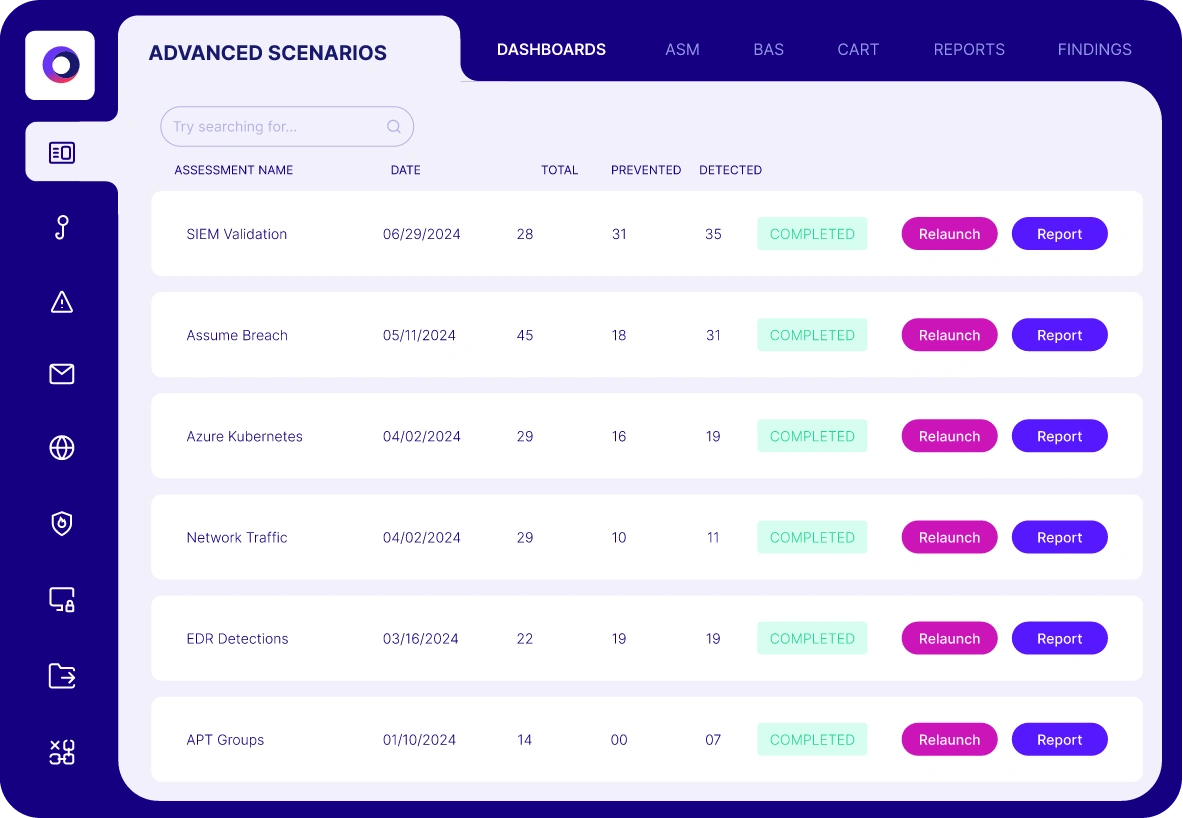
What measurable improvements have organizations seen with Cymulate's SIEM Validation?
Organizations have reported a 91% improvement in malicious file detection, a 50% improvement in the prevention of known exploit techniques, and up to 168 exploits prevented from a single recommended policy change. Source: Cymulate SIEM Validation Solution Page
How does Cymulate help reduce exposure risk?
Cymulate continuously measures and improves SIEM detections, helping organizations reduce the risk of cyber incidents by identifying and closing detection gaps. Source
How does Cymulate help identify missed SIEM detections?
Cymulate's automated testing finds gaps where your SIEM has failed to detect potential threat activity, enabling you to address these weaknesses proactively. Source
How does Cymulate help reduce false positives in SIEM?
By tuning SIEM detection rules and providing actionable recommendations, Cymulate helps reduce false positives, making SIEM alerts more accurate and actionable. Source
What is the average coverage of MITRE techniques in SIEMs, and how does Cymulate address this?
According to IBM, the average SIEM covers 38 of 201 MITRE techniques. Cymulate helps organizations expand their coverage by simulating a wide range of attack techniques and identifying detection gaps. Source
How long does it typically take to discover a breach, and how can Cymulate help reduce this time?
The average time to discover a breach is 194 days (IBM). Cymulate helps reduce this time by continuously validating SIEM detection capabilities and ensuring faster identification of threats. Source
What is the average cost of a data breach, and how does Cymulate help mitigate this risk?
The average cost of a data breach is .88 million (IBM). By improving SIEM detection and response, Cymulate helps organizations reduce the likelihood and impact of costly breaches. Source
Customer Success & Testimonials
What do customers say about Cymulate's SIEM Validation?
Customers praise Cymulate for providing immediate feedback when fine-tuning SIEM detection rules, enabling continuous and automated testing, and offering actionable insights for risk demonstration and mitigation. For example, Markus Flatscher, Senior Security Manager, states: "When we create a new detection rule in our SIEM that we can’t validate with historical logs, we use Cymulate assessments to generate the appropriate events and see if the rule was successful in its detection. The immediate feedback is useful when fine-tuning our SIEM and practicing detection engineering." Source
Are there case studies demonstrating SIEM Validation success?
Yes. For example, RBI validated and optimized their SIEM detection with Cymulate, increasing efficiency and improving security. Read the case study
How do customers use Cymulate for detection engineering?
Customers use Cymulate to generate events for new SIEM detection rules, validate their effectiveness, and receive immediate feedback for fine-tuning and detection engineering. Source
What industries benefit from Cymulate's SIEM Validation?
Industries such as services, construction, IT, and finance have reported benefits from Cymulate's SIEM Validation, as evidenced by customer testimonials and case studies. Source
Implementation & Integration
How easy is it to implement Cymulate's SIEM Validation?
Cymulate is designed for quick and easy implementation, operating in agentless mode with no need for additional hardware or complex configurations. Customers can start running simulations almost immediately after deployment. Source
What integrations does Cymulate support for SIEM Validation?
Cymulate integrates with a wide range of SIEM and security technologies, including AWS GuardDuty, CrowdStrike Falcon, SentinelOne, and more. For a complete list, visit the Partnerships and Integrations page.
What support resources are available for implementing SIEM Validation?
Cymulate offers comprehensive support, including email and chat support, a knowledge base, webinars, e-books, and an AI chatbot for technical queries and best practices. Source
Security, Compliance & Trust
What security and compliance certifications does Cymulate hold?
Cymulate holds SOC2 Type II, ISO 27001:2013, ISO 27701, ISO 27017, and CSA STAR Level 1 certifications, demonstrating adherence to industry-leading security and compliance standards. Security at Cymulate
How does Cymulate ensure data security for SIEM Validation?
Cymulate ensures data security through encryption in transit (TLS 1.2+) and at rest (AES-256), secure AWS-hosted data centers, a tested disaster recovery plan, and a secure development lifecycle. Security at Cymulate
Is Cymulate's SIEM Validation GDPR compliant?
Yes, Cymulate incorporates data protection by design and has a dedicated privacy and security team, including a Data Protection Officer (DPO) and Chief Information Security Officer (CISO), ensuring GDPR compliance. Security at Cymulate
Pricing & Plans
What is Cymulate's pricing model for SIEM Validation?
Cymulate operates on a subscription-based pricing model tailored to each organization's requirements, including the chosen package, number of assets, and scenarios. For a detailed quote, schedule a demo with the Cymulate team.
Use Cases & Target Audience
Who should use Cymulate's SIEM Validation?
Cymulate's SIEM Validation is designed for CISOs, security leaders, SecOps teams, red teams, and vulnerability management teams in organizations of all sizes and industries, including finance, healthcare, retail, media, transportation, and manufacturing. Learn more
What pain points does SIEM Validation address?
SIEM Validation addresses pain points such as fragmented security tools, resource constraints, unclear risk prioritization, cloud complexity, communication barriers, inadequate threat simulation, operational inefficiencies, and post-breach recovery challenges. Source
How does SIEM Validation help with compliance and audit requirements?
By providing continuous validation, detailed reporting, and quantifiable metrics, Cymulate's SIEM Validation helps organizations demonstrate compliance and readiness for audits. Security at Cymulate
Where can I find more resources about SIEM Validation?
You can download the SIEM Validation solution brief, access guides on AI-powered SIEM rule validation, and read customer case studies on the Cymulate website. Solution Brief | Guide | Case Study