Cymulate AI Copilot
Cymulate AI Copilot Automates Custom Threat Assessments to Validate New Threats in Minutes and Give Every Security Team the Power to Validate Threat Exposure
Amidst the daily burden of new threats and routine alerts, security operations teams don’t need another assistant to train and clean up after. Today’s SecOps experts need an assist.
Think Lionel Messi playing the perfect pass that positions you for success and makes you look your best. If you’re a basketball fan, maybe it’s a LeBron James drive and behind-the-back pass that finds you wide open at the three-point line.
Cymulate now provides that perfect assist to SecOps teams with its groundbreaking AI Copilot – a new artificial intelligence-powered feature in the Cymulate platform that applies large language models. The Cymulate AI Copilot introduces the first-of-its-kind dynamic attack planner that converts threat intel into custom threat assessments on demand. Other AI-powered features include automated assessment summaries and a support chatbot that connects users to relevant documentation and best practices.
Altogether, the Cymulate AI Copilot uplevels any SecOps analyst, security architect, or blue teamer to automate security validation like an expert pen tester. The Cymulate AI Copilot is now in beta and will be generally available within 30 days.
Apply Latest Threat Intel to Create Custom Threat Assessments in Minutes
Every blue teamer knows the stress of new threat intel that hits too close to home and demands immediate analysis and rigorous testing to answer the question, “Are we protected?” Customized security testing that would normally take hours or even days to build and deploy is now fully automated and can be accomplished in minutes.
First, security teams provide the Cymulate AI Copilot threat intelligence and other natural language queries to create on-demand, dynamic threat assessments. Then, Cymulate Breach and Attack Simulation runs the assessments to validate security controls and highlight areas of exposure against the specific threat.
The Cymulate AI Copilot allows users to create custom threat assessments from threat advisories, security research findings, news articles, and more. It’s as simple as copying and pasting the URL or content and receiving a highly tailored threat assessment that can be immediately launched.
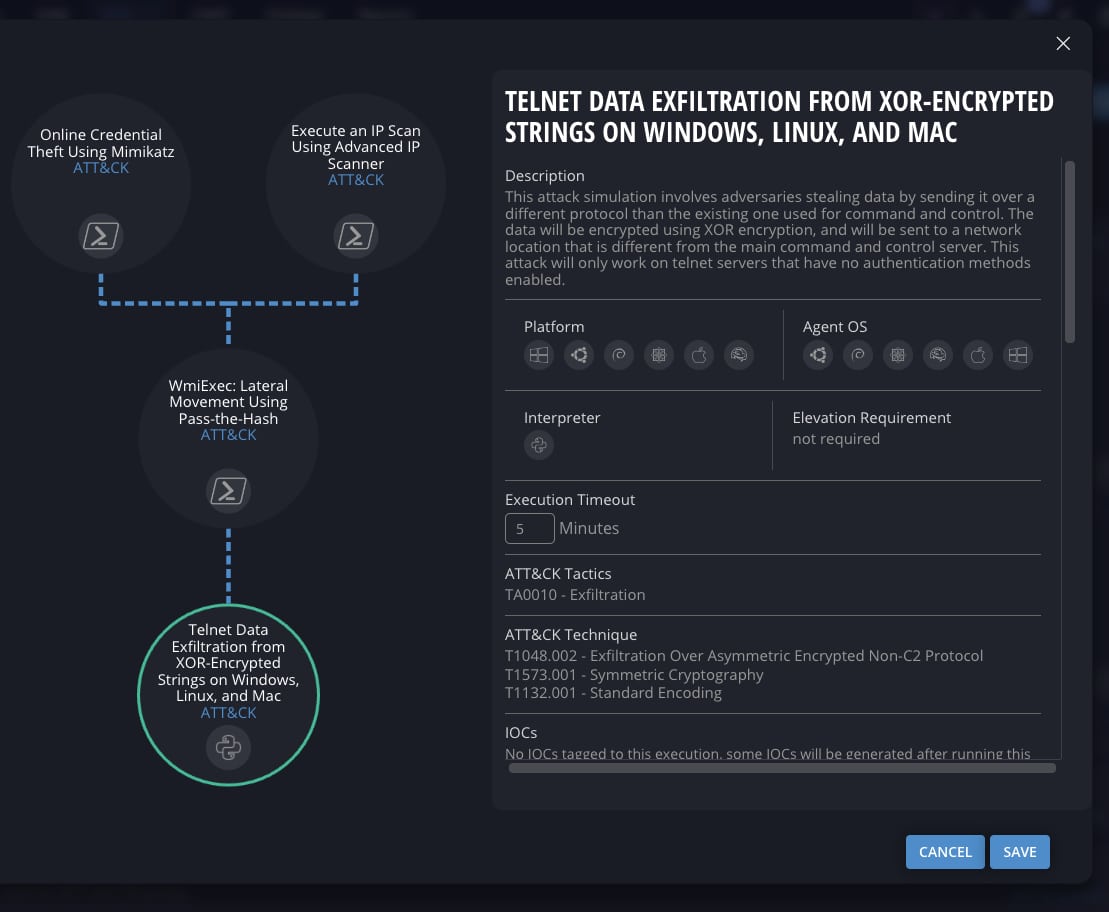
Of course, the natural language prompts also work for basic commands. In a very simple example, the user can submit a query of “Mimikatz to lateral movement with PsExec.” Mimikatz refers to the Microsoft Windows exploit that extracts passwords stored in memory. PsExec is a command line tool that enables remote access. The Cymulate AI Copilot immediately identifies the two attack executions that match and adds the context just as an expert red teamer would to build realistic attack chains that can be immediately run to test the resilience to this threat.
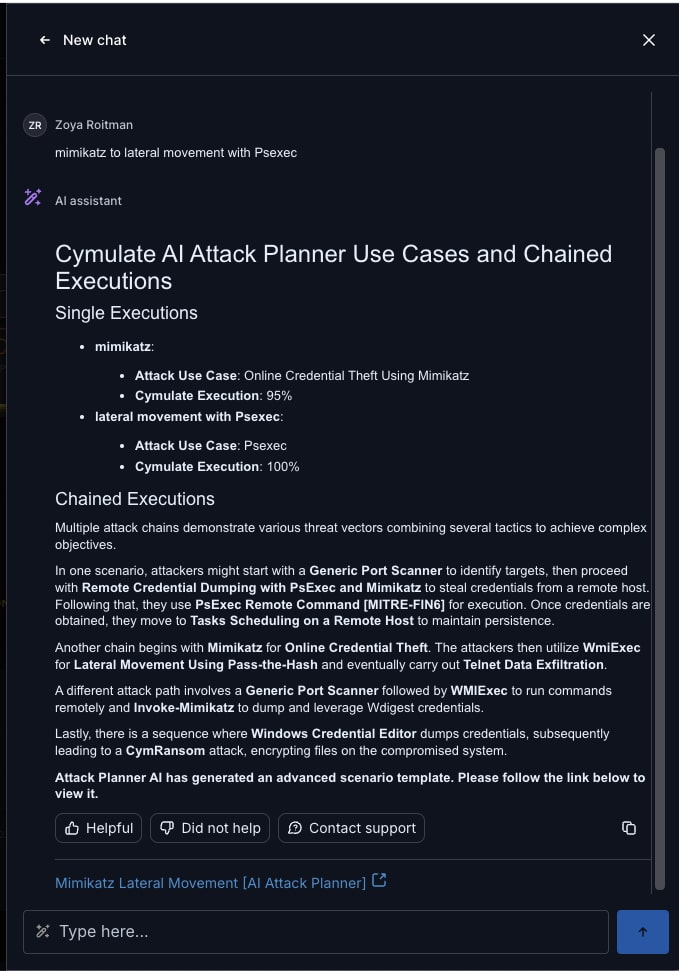
To build realistic attack chains, the Cymulate AI Copilot identifies techniques and associated executions that were not specified in the initial prompt. In this AI-created attack chain, the Cymulate AI Copilot recognized data exfiltration as a likely attack objective and added IP scanning to identify target hosts for lateral movement.
In a more complex and complete example, this Medium article on Akira ransomware includes more than 30 MITRE ATT&CK techniques and sub-techniques. The Cymulate AI Copilot instantly identifies all individual attack executions that match both the technique and the objective of ransomware. The numeric percentage listed for each execution indicates confidence in the match.
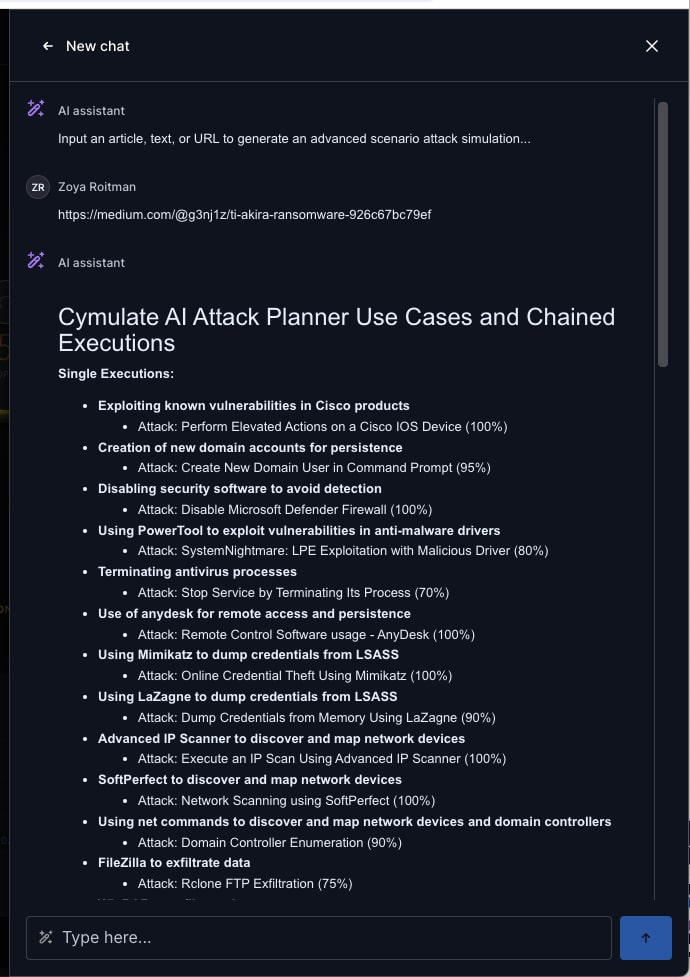
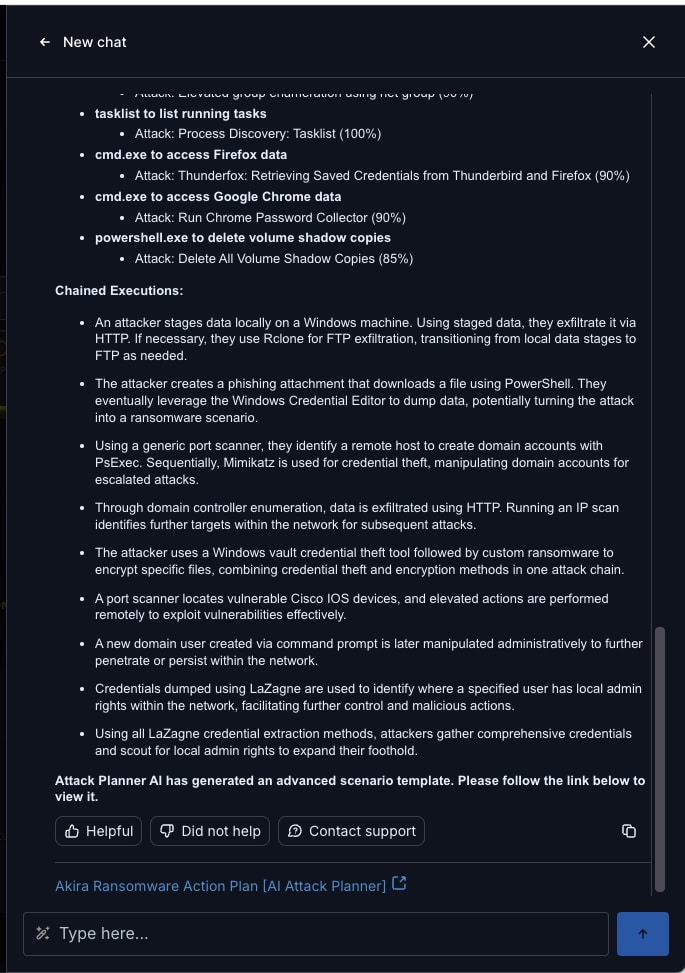
Going beyond this simple association of individual attack executions, the Cymulate AI Copilot creates seven different chained assessments comprised of 57 individual executions in a complex attack sequence that recreates the Akira ransomware attack. In the chained assessment shown here, Cymulate AI Copilot provides a complete attack chain that combines:
- Port scanning
- Discovery of current users
- Authentication bypass that exploits a Fortinet vulnerability
- Data staging by creating Windows files
- Malicious link files
- Ransomware executions for encryption and exfiltration
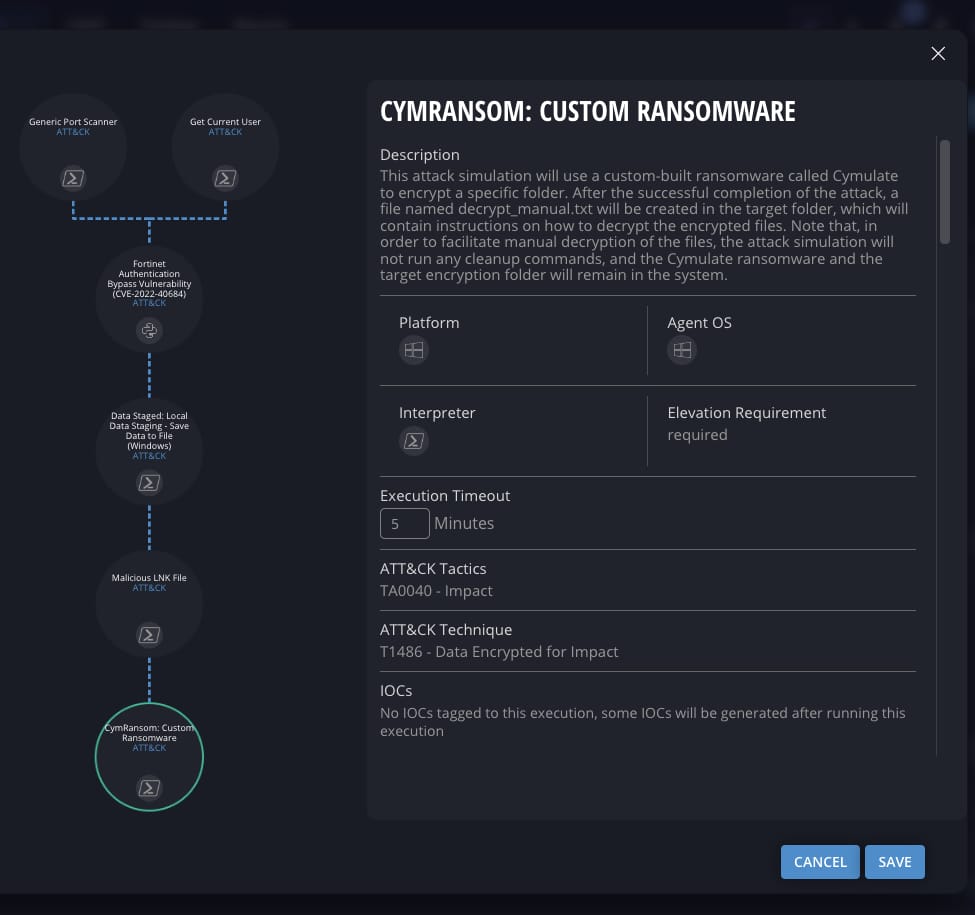
In this example, the Cymulate AI Copilot builds the custom threat assessment in minutes – and automates a process that would take an expert red teamer days to build a test scenario from open-source tools. Even a highly trained Cymulate user would likely spend 30-45 minutes creating this complex attack chain in a user-friendly interface that selects each of the 57 executions individually.
AI-Powered Insights
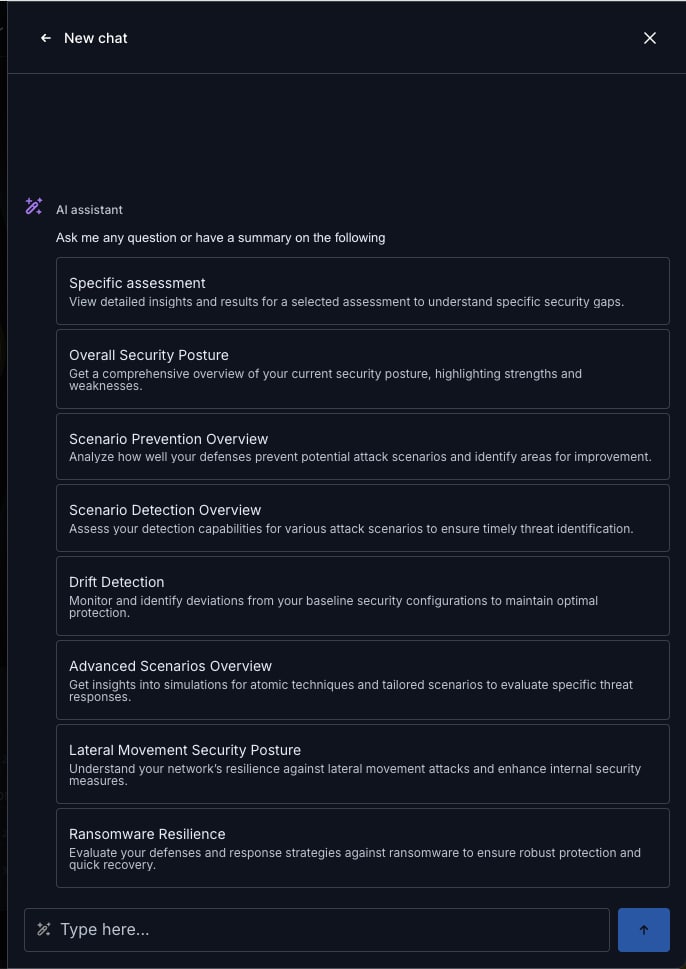
Beyond the attack planner, the Cymulate AI Copilot includes powerful insights and automation that add to the overall user experience of the Cymulate security and exposure validation platform. For automated analysis and insights to specific assessments or the security posture in general, the Cymulate AI Copilot analyzes all assessment results to highlight critical security weaknesses, highest priority mitigations, and summarized results for easier consumption.
For a better user experience and to prevent “AI prompt fatigue,” the Cymulate AI Copilot includes common pre-packaged queries designed to quickly get the analysis and insights needed for:
- Specific assessment summaries
- Overall security posture of all recent assessments
- Threat prevention analysis
- Threat detection analysis
- Drift or change between assessments
- Resilience to lateral movement
- Ransomware defenses
Knowledge Base Chat and Assessment Troubleshooting
For fast and easy access to best practices, documentation, and technical guidance on troubleshooting any issue, the Cymulate AI Copilot applies natural language processing to understand and respond to user queries with accuracy. From deployment requirements to control integrations to understanding what was included in the last product update, the Cymulate AI Copilot retrieves relevant information in seconds, so SecOps teams spend less time searching for information and more time focusing on their core responsibilities.
AI Built for Security and Privacy
Security and privacy are at the core of the Cymulate AI Copilot’s design. Protecting critical customer data will always be our top priority. Cymulate and the AI Copilot never share sensitive information with an external AI model. Built on the private instance of Azure AI, the Cymulate AI Copilot keeps all data secure within the Cymulate platform. The Cymulate AI Copilot is built on a secure foundation with advanced security measures, including encryption at rest and in transit, to safeguard sensitive information against unauthorized access.
See Cymulate AI Copilot in Action
The Cymulate AI Copilot is now in beta with a general availability set for the next 30 days. To see the power of the most advanced security and exposure management platform and its new AI-powered assists, click here to request a demo.