AI Threat Detection: Supercharging Cyber Defenses with Intelligence & Scale
Security teams face an onslaught of ever-evolving threats, bloated alert queues and sprawling attack surfaces.
Manual detection and periodic pen tests simply can’t keep pace. There are now more options to meet the challenges presented by today’s threat landscape, and that includes the integration of AI into your tech stack.
AI threat detection flips the script, analyzing vast data streams in real time, uncovering subtle anomalies and automating detection with speed and precision. It surfaces threats earlier and with far greater accuracy than traditional methods.
What Is AI Threat Detection?
AI threat detection harnesses machine learning, anomaly scoring, behavioral analytics, natural language processing (NLP) and pattern recognition to identify threats intelligently and at scale. It absorbs vast data sets (logs, network telemetry, user behavior logs, threat intel) and trains itself to distinguish normal activity from malicious.
Traditional detection relies on static rules, signature updates, and periodic investigations—often reactive and limited in scope. AI adds dynamism and adaptability: it scans continuously, tweaks its models with each new anomaly and uncovers subtle, sophisticated threats that manual methods miss.
Unlike traditional systems, which often rely on static rules or known signatures, AI continuously analyzes network traffic, user activity, and system behavior to uncover both familiar and previously unknown threats.
One of the biggest advantages of AI in this domain is its ability to detect anomalies early in the attack cycle before significant damage occurs. By automating the detection, alerting and even initial response processes, AI significantly improves the speed and efficiency of threat mitigation.
Five Key Threats AI Can Detect and Prevent
AI-backed systems are equipped with advanced machine learning and deep learning algorithms that can identify a wide variety of threats across digital, physical and behavioral environments. Here are some of the primary types of threats AI is helping to combat:
1. Malware and Ransomware Detection
AI-powered systems analyze how files interact with systems rather than relying solely on known malware signatures. This behavior-based approach allows systems to detect new and evolving malware variants traditional methods often miss, especially those designed to evade signature-based detection.
2. Phishing and Social Engineering
AI excels at identifying phishing attempts and social engineering tactics by examining email content, sender behavior and metadata. It can detect subtle signs of manipulation, helping prevent sensitive data leaks caused by users falling for deceptive communications.
3. Cyber Threats and Network Intrusions
AI helps secure cloud-based environments by monitoring real-time network activity for suspicious patterns. This is so critical at a time when more and more data is moving into less-structured, ephemeral cloud environments. It’s especially effective against complex, highly-mature threat actors and unauthorized access that traditional tools might miss.
4. Behavioral Anomalies
AI uses behavioral analytics to create a baseline for what "normal" looks like across users, systems and networks. When abnormal activity is detected such as unusual login times or file access, the well-trained AI flags them immediately. When it comes to identifying insider threats and zero-day attacks, AI can provide critical assistance.
5. Access Control Violations
Modern access control systems powered by AI can detect when someone tries to access resources or locations they shouldn’t. By learning from users’ typical access behavior, AI can quickly spot anomalies such as logins from unknown devices or geographic locations and take preventive action.
Threat Detection Processes Empowered by AI
The true strength of AI in cybersecurity lies in its adaptability, learning capability, and automation. Below are some of the most impactful ways AI contributes to threat detection:
Anomaly Detection
AI algorithms use time-series and statistical analysis to monitor changes over time. When behavior or activity diverges from the baseline, it triggers alerts for further investigation. This technique is essential for detecting stealthy or slow-moving attacks.
Natural Language Processing (NLP)
NLP allows AI systems to understand and analyze human language, which is critical in identifying phishing messages, malicious emails or risky communications. Trained on large volumes of text data, NLP models can detect intent and flag messages that attempt to manipulate users.
Machine Learning & Pattern Recognition
Machine learning algorithms are trained by large, sprawling data sets that include network traffic, user patterns and behavior and much more. These models can accurately pinpoint distinctions between safe and suspicious activities. These machine learning models enable early identification of cyberattacks, insider threats or malware as the models become more intelligent over time.
Image and Video Analysis
In security camera footage or access point monitoring, AI can identify unauthorized individuals, detect suspicious packages or even recognize threatening behaviors. Technologies like convolutional neural networks (CNNs) are central to these visual recognition capabilities.
Why Manual Threat Detection Falls Short
Manual detection is slow, narrow, and labor-intensive. A few key statistics from the Cymulate Threat Exposure Validation Impact Report 2025 underline these hurdles:
- 67% of organizations cite infrequent testing as a major security weakness
- Manual penetration testing suffers from limited scope, missed vulnerabilities, and scheduling bottlenecks
- Care teams drown in alert volume, but only a fraction are actionable, leading to alert fatigue and blind spots
Periodic reviews leave too much time for drift between controls. By the time an issue is uncovered, attackers may already have exploited it.
The AI Advantage: Easier, Faster, Smarter
The Impact report reveals the profound impact of embedding AI into threat detection:
- 230X more threats can be tested using automated security validation compared to manual methods
- Response time shrinks by 24 hours, dramatically reducing the window of risk
- 89% of organizations are implementing AI for exposure validation
- 97% of respondents who use automated security control validation and measure cyber program effectiveness have seen a positive impact since implementation
These gains don’t just improve metrics—they transform capabilities. AI-driven solutions prioritize genuine threats, curb false positives, and shift teams from reactive firefighting to proactive defense.
The Cymulate AI + Threat Exposure Validation Value Proposition
What sets AI-powered validation apart is its ability to continually and intelligently test your actual defenses - not just scan your perimeter. The Cymulate platform integrates expansive MITRE ATT&CK–based simulations across:
- Web
- Network
- Endpoint
- Active Directory
- Cloud-based controls
Rather than one-off pen tests, Cymulate delivers continuous security exposure validation. AI correlates test results with live telemetry, identifying where controls have drifted or degraded. As defenses shift, the platform dynamically adjusts simulations, runs fresh tests and recalibrates AI detection models.
This intel-driven feedback loop closes gaps automatically so there are no more stale assessments or stale rules.
Cymulate empowers security teams to:
- Automate testing and validation, freeing analysts from repetitive tasks
- Detect control drift in real time, surfacing unseen weaknesses
- Prioritize exposures with AI, focusing limited resources where they matter most
- Reduce breach frequency and impact, as validated by the Impact Report
Cymulate spans all MITRE ATT&CK tactics, combining active threat emulation with AI to continuously challenge and refine defenses.
The Cymulate Exposure Validation platform has also added an AI-powered detection engineering assistant for security information and event management (SIEM) rule threat coverage validation.
Using AI-powered analysis and a massive library of real-world attack simulations, you can continuously build, test and fine-tune threat detection so you can see what works, fix what doesn’t and continuously optimize your detections.
With deep integrations into leading SIEM platforms and a continuously updated MITRE ATT&CK heatmap, Cymulate transforms detection engineering from a black-box guessing game into a measurable, repeatable science. You get:
- Automated validation of existing detection rules
- Fast creation of new, high-fidelity detection logic
- Ongoing optimization based on real threat behaviors
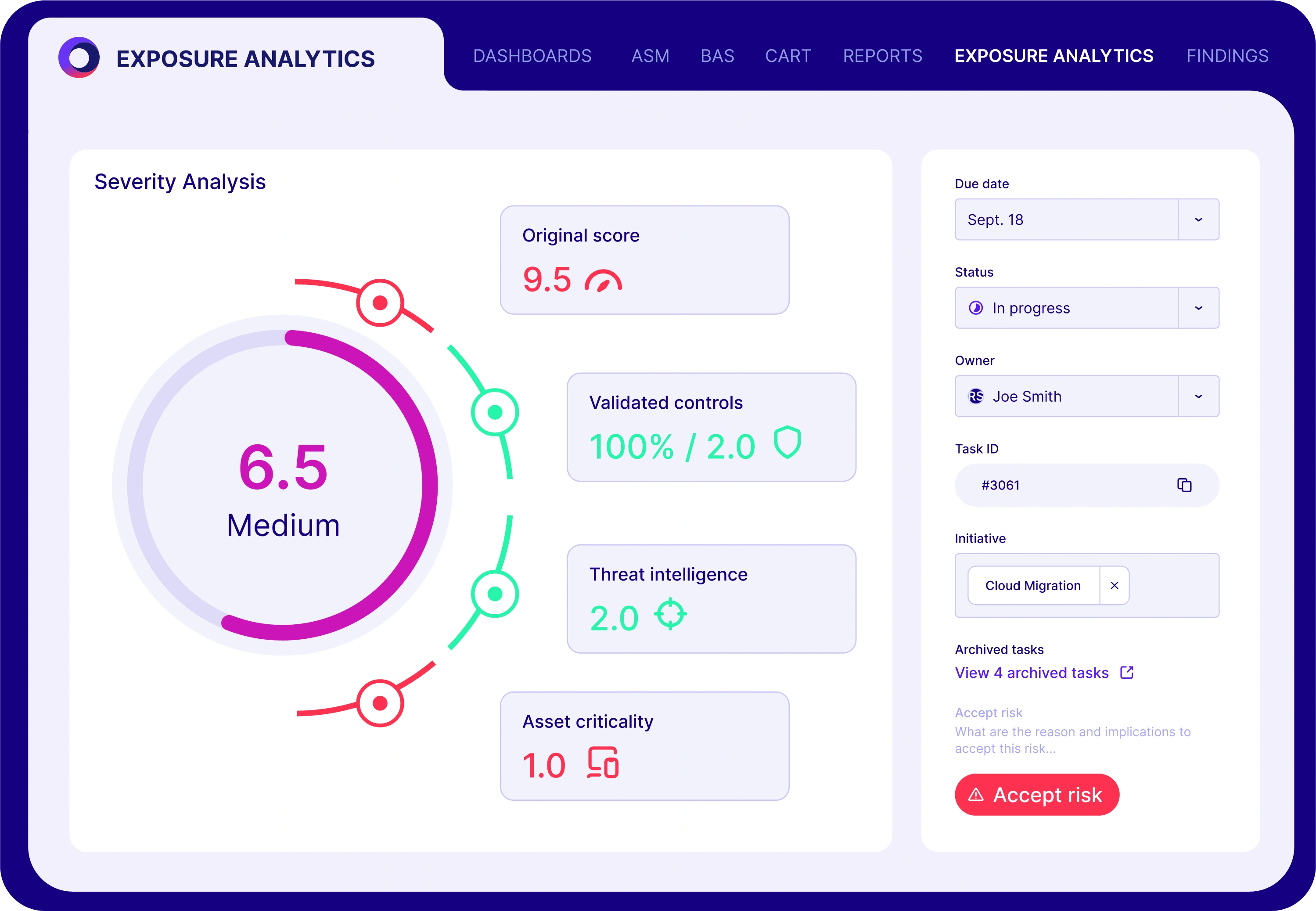
A Smarter Way to Secure Your Environment
Security professionals deserve tools that scale with the threat landscape. Cymulate’s AI-powered exposure validation delivers precisely that.
Experience it firsthand:
- Get ahead of threats with proactive validation - download the full Threat Exposure Validation Impact Report 2025
- Learn how proactive AI‑powered SIEM rule validation and detection engineering boosts efficiency in this guide
- See how Cymulate’s AI Copilot transforms SIEM detection – watch our AI Copilot explainer video
- See how AI automates and enhances threat exposure validation
What to Know and What to Do Next
- AI threat detection – Leveraging machine learning and analytics to identify and respond to security incidents in real time.
- Exposure validation – Actively testing controls using simulations mapped to MITRE ATT&CK to measure effectiveness.
- Security drift – Degradation of security control efficacy over time due to configuration changes or evolving threats.
- Breach & Attack Simulation (BAS) – Autonomous execution of real-world attack techniques against an organization’s environment.
By delivering more coverage, faster detection and real-time prioritization, AI threat detection represents a seismic shift in cybersecurity. Manual methods can’t keep up—but with AI-powered threat exposure validation, your defenses grow stronger every minute.
Secure with intelligence and trust. Secure your cyber defenses proactively. Request a Cymulate demo today.