Cloud Security Threats You Can’t Afford to Ignore in 2025

Cloud environments have become mission-critical, but they’re also difficult to secure.
Despite significant investment in cloud security tools, 61% of security leaders agree their organization lacks the ability to identify and remediate exposures in their cloud environments, according to the Cymulate 2025 Threat Exposure Validation Impact Report.
As cloud infrastructures grow more complex, dynamic and ephemeral, attackers are exploiting the widening security gaps faster than most teams can respond.
For CISOs, DevSecOps leaders, and cloud security architects, the takeaway is clear: traditional approaches are no longer enough. Effective cloud security demands validation, not just visibility.
The Challenge of Securing the Cloud
Modern cloud architecture is inherently volatile. With multi-layered deployments spanning hybrid, multi-cloud and containerized environments, assets appear and vanish in real time. Serverless functions, short-lived containers and decentralized development practices exacerbate visibility and control challenges.
This complexity overwhelms conventional cloud security tools. Cloud Security Posture Management (CSPM), Cloud Infrastructure Entitlement Management (CIEM) and Security Information and Event Management (SIEM) solutions provide vital baselines—but they have serious limitations.
- Static snapshots don’t account for the fluidity of ephemeral resources.
- Rules-based detections miss logic errors or chained vulnerabilities.
- Cloud-native controls offer reactive telemetry but lack proactive assurance.
- SIEM platforms generate alert fatigue without prioritization based on exploitability.
These tools don’t validate how secure your cloud environment actually is—or how it would stand up against a real attack.
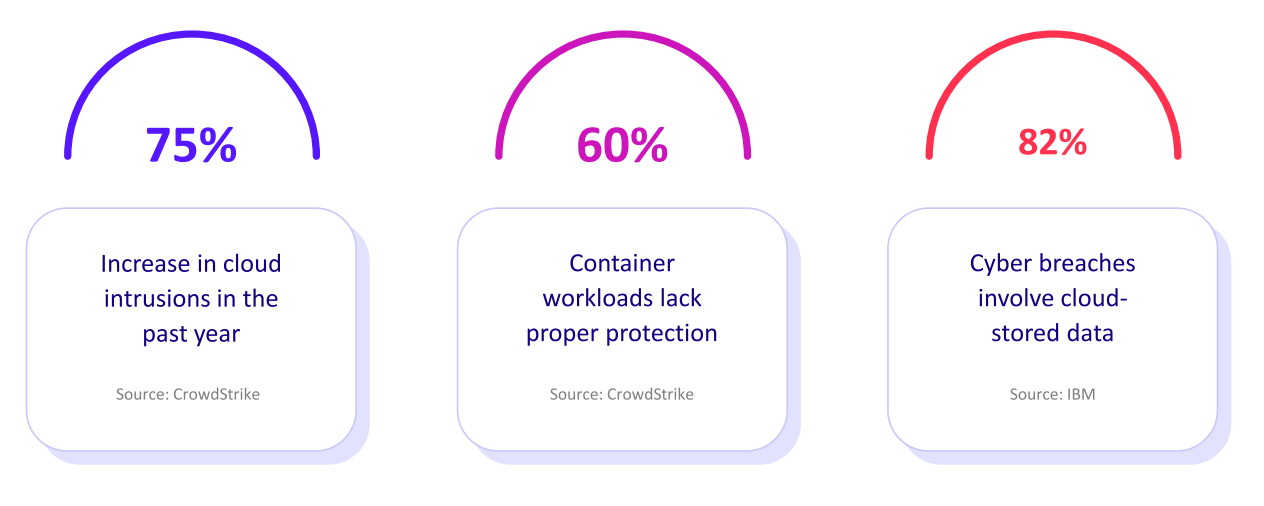
Organizations are Struggling to Identify and Remediate Cloud Exposures
of security leaders agree their organization lacks the ability to identify and remediate exposures in their cloud environments.
of organizations run exposure validation in their cloud environment on a daily basis.
say it can take up to 24 hours to validate cloud exposures.
Cloud Security Threats You Shouldn’t Ignore in 2025
As detailed in the Cloud Security Alliance’s 2024 Top Threats and reinforced by the latest research from Cymulate, the cloud threat landscape continues to evolve. The following threats demand urgent attention from cloud defenders:
1. Misconfigurations
Misconfigured storage buckets, exposed management interfaces and incorrect network controls are responsible for the majority of cloud breaches. In a high-velocity DevOps environment, default settings and human error compound risk.
2. Insecure APIs
Cloud APIs serve as the backbone for application communication. When improperly secured, they become prime entry points for attackers. Broken authentication, lack of rate limiting and excessive permissions are commonly exploited flaws.
3. Identity and Access Mismanagement
With identities functioning as the new perimeter, any misstep in IAM policies—like role sprawl or credential reuse—can lead to full account compromise. Overly permissive roles are a recurring weakness across cloud environments and steps need to be taken to ensure there are no long-term issues.
4. Inadequate Encryption
Data in transit and at rest must be encrypted with modern, properly configured algorithms. However, failure to rotate keys, enforce TLS everywhere or segment encrypted data still leaves many assets exposed.
5. Lack of Visibility into Ephemeral Resources
Kubernetes has revolutionized cloud computing and the way applications are built. But its increasingly ephemeral nature adds layers of abstraction to your environment that can leave you exposed to threats if not properly secured.
Serverless functions and containers often run for seconds or minutes, which is too fast for traditional tools to monitor. This blind spot enables lateral movement and data exfiltration undetected.
6. Overly Permissive Roles and Entitlements
CIEM tools attempt to manage these issues around overly permissive roles and entitlements, but without contextual validation, excessive permissions often persist. Attackers exploit these gaps for privilege escalation and lateral movement.
7. Shadow IT and Unmanaged Services
Developers and business units can easily spin up cloud resources outside of sanctioned infrastructure. Without governance or validation, these “invisible” assets become soft targets despite the best intentions of those within an organization.
Despite these clear risks, the Cymulate2025 research reveals that only 1 in 6 organizations can validate cloud exposures within an hour, leaving attackers with a massive head start.
Why Cloud Security Validation is Critical
Legacy thinking still dominates many cloud security programs. That type of outdated thinking can lead directly to threats to your business. The perimeter-based model doesn’t translate to a cloud-native world where your infrastructure is decentralized, dynamic and ephemeral.
What’s missing is cloud exposure validation. It provides continuous, real-time testing of your actual security posture. Instead of assuming configurations are effective, validation provides hard evidence and answers critical questions such as:
- Are controls working as intended?
- Can attackers exploit chained misconfigurations?
- What’s the blast radius of a compromised credential?
The 2025 Threat Exposure Validation Impact Report found that 37% of organizations say it can take more than 24 hours to validate cloud exposures. That’s a gap that adversaries can easily exploit.
The Cymulate cloud security validation solution addresses this problem head-on. It enables teams to:
- Validate controls across IaaS, PaaS and SaaS layers.
- Test against real-world attack paths in multi-cloud and hybrid environments.
- Simulate breaches to uncover exploitable misconfigurations or identity flaws.
- Automate continuous assessment, enabling rapid remediation and security assurance.
This is not theoretical security—it’s operational, actionable insight delivered at the speed of cloud.
The result? One finance company said they saw a 60% increase in the efficiency of their SecOps team. Another company, in the global transportation sector, saw an 81% reduction in cyber risk in four months. And a healthcare organization saw 168 exploits prevented from one policy change.
Cloud Security Validation in Action
Those examples above aren’t then only ones we can share. Consider a leading IT services consulting firm featured in a recent Cymulate customer story. With sprawling cloud environments supporting global clients, their security team struggled to maintain control over cloud exposures.
After implementing the Cymulate automated cloud validation platform, the organization now enjoys the following benefits:
- Automation: The organization automates security validation to cover every control across on-prem and cloud environments.
- Increased coverage: By mapping assessments to NIST and MITRE frameworks and testing against the latest threats, the security team evaluates its security posture against a broader range of known threats and improves its overall security resilience.
- Strong customer support: Customer support is always readily available, and the company views Cymulate as a full partner in its cybersecurity journey.
This shift enabled them to move from reactive alert handling to proactive exposure management, turning cloud security into a strategic advantage.
What to Know About Cloud Security Threats
Cloud environments are under constant siege, and the threats are evolving faster than traditional defenses can adapt. While CSPM, CIEM and SIEM tools provide important visibility, they fall short of validating whether your security controls work in the face of real-world threats.
Validation is the missing layer.
By adopting the Cymulate real-time cloud exposure validation platform, security teams gain continuous assurance of their posture across the entire cloud stack. In 2025, where breaches are a matter of “when,” not “if,” proactive validation isn’t optional. It’s essential.
Dive deeper into the insights driving modern cloud defense. Download the 2025 Threat Exposure Validation Impact Report and explore the Cymulate Cloud Security Validation Solution.