Enterprise Cloud Security: Best Practices and Guide

Enterprise cloud security is the framework of strategies, technologies and processes that protect sensitive workloads, applications and data across cloud environments. In this guide, we’ll explore key threats, frameworks, solutions and best practices to strengthen enterprise resilience, as well as how Cymulate helps continuously validate your cybersecurity defenses.
Key highlights:
- Enterprise cloud security combines tools, policies and frameworks that protect enterprise workloads and data across public, private and hybrid clouds.
- Aligning with standards like NIST SCF, ISO 27001 and CSA CCM strengthens compliance and risk management.
- Continuous validation, least privilege access, encryption and configuration monitoring are core best practices for an effective cloud security strategy for enterprises.
- Cymulate enables continuous security validation and exposure management capabilities to optimize your enterprise cloud posture.
What is enterprise cloud security?
Enterprise cloud security encompasses the strategies and technologies that protect enterprise applications, workloads and data hosted in cloud environments. It extends traditional IT security beyond the perimeter, focusing on identity, access and configuration across distributed infrastructure.
At its core, enterprise cloud security safeguards confidentiality (preventing unauthorized access to sensitive data), integrity (ensuring data and workloads remain accurate and unaltered) and availability (maintaining uptime and operational continuity for critical services).
Why cloud security for enterprises is critical
Enterprises now operate across multi-cloud environments often spanning AWS, Microsoft Azure and Google Cloud. The scale of this movement increases complexity, risk exposure and regulatory obligations. Here’s why enhancing security measures for cloud infrastructures is so critical:
- Protecting sensitive data: With 82% of breaches involving data stored in the cloud (IBM, 2024), enterprises must prioritize encryption, access management and visibility across environments.
- Ensuring compliance: Frameworks like GDPR, HIPAA and PCI DSS require verifiable controls, making compliance automation essential.
- Maintaining business continuity: Cloud incidents can cost an average of $4.88M per breach (IBM, 2024). Proactive monitoring mitigates downtime and loss.
- Reducing risk exposure: Continuous assessment of configurations and vulnerabilities prevents lateral movement by attackers.
- Safeguarding brand trust: Demonstrating robust security governance enhances stakeholder and customer confidence.
Key threats to cloud security for enterprises
Attackers target enterprises for their data scale, complex architectures and often-fragmented security governance. According to Gartner, by 2026 90% of cloud breaches will stem from misconfigurations rather than provider faults.
Here are critical cloud security threats and what you need to know about them:
- Misconfigurations: The leading cause of cloud data exposure, often resulting from overly permissive IAM roles, unsecured APIs or publicly accessible storage buckets. Even minor misconfigurations can expose sensitive workloads and violate compliance mandates across multi-cloud environments.
- Account takeovers: Compromised credentials (through phishing, credential stuffing or leaked API keys) allow attackers to impersonate users, escalate privileges and move laterally between services. Without continuous authentication and behavioral monitoring, account compromise can persist undetected for months.
- Unprotected APIs: APIs without proper authentication, authorization, or rate limiting expose sensitive data and core business logic to attackers. Poorly secured endpoints are frequently exploited to exfiltrate data, trigger privilege escalation or launch automated denial-of-service attacks.
- Data leaks: Weak or inconsistent encryption, combined with unmanaged file sharing and inadequate data loss prevention (DLP), can result in sensitive enterprise data leaking to external parties. Leaks can also occur via misconfigured third-party integrations or unmanaged SaaS tools.
- Denial-of-service (DoS) attacks: Targeted volumetric or application-layer attacks can overwhelm cloud applications, degrade performance and interrupt business-critical services. Even when infrastructure scales automatically, attackers can drive up operational costs and reduce availability for legitimate users.
- Shadow IT: Unmonitored adoption of unsanctioned cloud services or SaaS apps increases untracked attack surfaces and undermines central governance. Managing shadow IT in the enterprise is an entire discipline unto itself and requires dedicated visibility tools and policies to identify, assess and onboard unauthorized services securely.
Understanding enterprise cloud security and governance frameworks
Strong enterprise cloud security governance frameworks guide organizations in assessing cloud security risks, setting control baselines and aligning security with compliance mandates. Frameworks provide consistency across multi-cloud environments and facilitate measurable maturity improvement.
| Key cloud security frameworks | Focus of the frameworks |
| NIST Cybersecurity Framework (CSF) | Risk-based approach built on Identify, Protect, Detect, Respond and Recover functions for scalable governance |
| ISO/IEC 27001 | Global standard for information security management systems (ISMS) that emphasizes continuous improvement |
| CIS Benchmarks | Prescriptive technical configuration guidelines for security cloud setup across providers |
| CSA Cloud Controls Matrix (CCM) | Cloud-specific control framework for aligning governance, compliance and risk management in shared environments |
NIST Cybersecurity Framework (CSF)
NIST CSF enables enterprises to assess, prioritize and mitigate cloud-related risks through standardized controls. Its five core functions (Identify, Protect, Detect, Respond and Recover) form a lifecycle that supports resilience and regulatory compliance.
ISO/IEC 27001
ISO 27001 establishes a systematic approach to managing sensitive enterprise data. Certification ensures consistent application of encryption, access control and risk management policies across all cloud assets.
CIS Benchmarks
CIS Benchmarks provide actionable, vendor-specific configuration guides to harden cloud environments and reduce the attack surface. These are ideal for detecting and correcting misconfigurations before they become significant problems in the future.
CSA Cloud Controls Matrix (CCM)
The CCM focuses on security governance across the shared responsibility model, mapping controls to regulatory standards such as PCI DSS, GDPR and SOC 2.
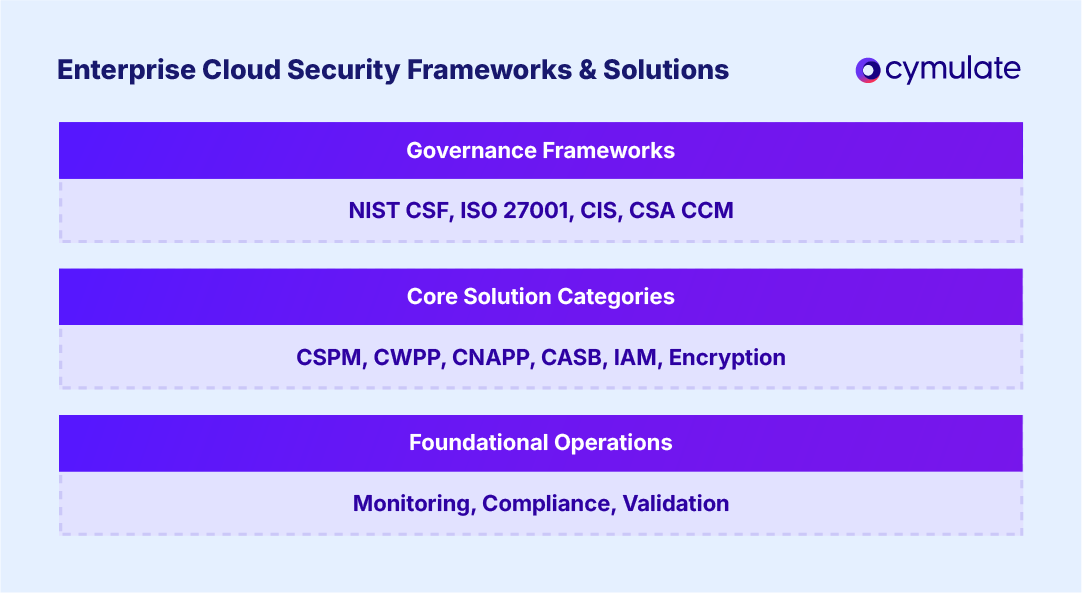
Main types of enterprise cloud security solutions
Enterprises must adopt a layered approach to cloud security because no single product covers all threats across identity, configuration, workloads, data and networks. A layered architecture combines complementary tools so gaps in one layer are covered by controls in another, producing defense in depth and measurable risk reduction. Continuous cloud security validation ensures these solutions perform as expected.
Cloud security posture management (CSPM)
CSPM continuously scans cloud accounts, infrastructure-as-code (IaC) templates and resource configurations to detect drift, misconfigurations and compliance failures. It’s the primary tool for ensuring cloud environments stay aligned to security baselines and compliance frameworks.
Key features: Automated posture scanning, compliance mapping, remediation playbooks, infrastructure as code (IaC) integration
Limitations: Limited runtime visibility into workloads and some false positives on dynamic environments
Cloud workload protection platforms (CWPP)
CWPPs secure compute workloads (VMs, containers, serverless) at build and runtime by providing vulnerability scanning, behavioral protection and micro-segmentation. They are focused on protecting the workload itself regardless of the cloud provider.
Key features: Runtime threat detection, EDR-like telemetry for cloud workloads, image scanning.
Limitations: Agent overhead, operational complexity in diverse environments.
Cloud-native application protection platforms (CNAPP)
CNAPPs unify CSPM, CWPP and developer-facing security controls to provide end-to-end protection from code to runtime. They help “shift left” (building security best practices into the earliest parts of the development process) by giving DevSecOps teams consolidated findings and actionable remediation.
Key features: Unified risk scoring, IaC and pipeline scanning, workload protection, compliance reporting
Limitations: Maturity varies across vendors; integration with existing DevOps toolchains can require effort
Cloud access security brokers (CASBs)
CASBs broker visibility and control between enterprise users and cloud applications (SaaS/IaaS). They enforce DLP, encryption and police-based access across sanctioned and sometimes unsanctioned apps.
Key features: SaaS discovery, DLP enforcement, policy enforcement for data exfiltration
Limitations: Complex role sprawl and permission creep are still common without continuous review
Identity and access management (IAM)
IAM is the foundation of cloud security: it manages identities, roles and entitlements across services. Strong IAM reduces attack surface by enforcing least privilege, multi-factor authentication and just-in-time access.
Key features: Role-based/attribute-based access control, MFA, privilege elevation workflows
Limitations: Complex role sprawl and permission creep are still common without continuous review
Encryption and key management
Encryption protects data both at rest and in transit while key management centralizes lifecycle and policy enforcement. Proper KMS design prevents simple data exposure even when other controls fail.
Key features: Centralized key rotation, HSM-backed key stores, envelope encryption patterns
Limitations: Mismanagement of keys or embedding keys in code negates encryption benefits
CSPM, CWPP, CNAPP, CASB, IAM and encryption should be integrated with SIEM, SOAR and ticketing systems. That integration enables alerts to flow into operational workflows where automated playbooks and human reviewers close the loop on remediation. Cloud security assessments also help ensure your organization has all the bases covered in these areas.
Benefits of an effective cloud security strategy for an enterprise
Investing in a mature enterprise cloud security program generates measurable outcomes across risk, compliance, operations and reputation. The following benefits show how defensive investment translates into business value.
- Reduced risk exposure: Automated posture monitoring and continuous validation reduce windows of exposure by identifying misconfigurations, risky identities and vulnerable workloads before attackers can exploit them.
- Compliance alignment: Mapping cloud controls to frameworks like NIST and ISO automates evidence collection and audit readiness, lowering the time and cost to achieve and maintain compliance.
- Improved business resilience: Proactive detection and validated incident playbooks reduce mean time to detect and recover from cloud incidents, minimizing downtime and financial impact.
- Operational efficiency: Automation of repetitive tasks like scanning, triage and remediation frees security and ops teams to focus on strategic initiatives and reduces manual error.
- Customer and partner trust: Demonstrable, third-party-auditable controls and continuous validation increase stakeholder confidence and can be a differentiator in vendor and partner evaluations.
Cloud security best practices for enterprises: Top 6 strategies
Best practices move cloud security from a reactive posture to a proactive, measurable program. Each practice below includes pragmatic actions and tactical controls to embed repeatable security across the enterprise.
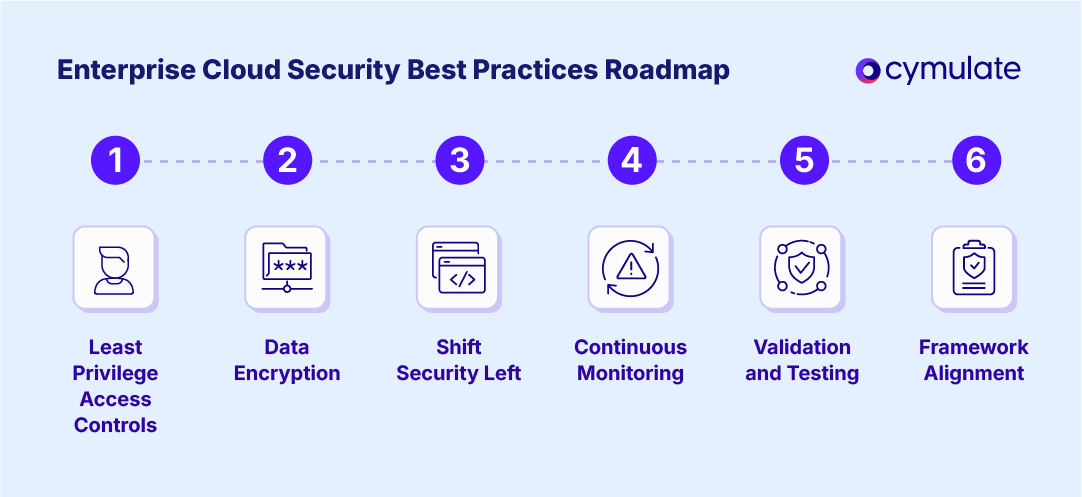
Enforce least privilege access controls
Start by defining roles and scoping permissions so every identity has only the access needed to perform its job. Use role-based or attribute-based access control and automate entitlement reviews.
Regularly audit service and human accounts, remove unused roles, and apply just-in-time access for privileged operations to reduce the risk of privilege escalation.
- Implement RBAC/ABAC, seasonal entitlement reviews and automated deprovisioning
- Combine with MFA and conditional access policies for high-risk operations
Encrypt enterprise data at rest and in transit
Encrypt all sensitive data using strong cryptographic standards and ensure TLS for service communications. Centralize key management with hardware-backed key stores and automated rotation.
Address data discovery and classification so encryption policies are applied where they matter most and implement tokenization or vaulting for highly sensitive elements.
- Use KMS with HSM backing, enforce TLS 1.3 and rotate keys automatically
- Classify data to prioritize encryption and reduce unnecessary exposure
Shift security left in development pipelines
Integrate security checks into the CI/CD pipeline so issues are caught before deployment. Add IaC scanning, dependency checks and container image scanning as part of the build process.
Provide developer-friendly gating and automated fixes where possible to reduce friction and ensure security becomes part of the delivery lifecycle rather than a blocker to digital innovation.
- Embed IaC static analysis, SCA for dependencies, and container scans in CI
- Fail fast on high-risk findings, and automate low-risk remediations
Continuously monitor and audit configurations
Implement continuous configuration monitoring and drift detection across all cloud accounts to catch accidental exposure rapidly. Combine CSPM with telemetry from workload agents for a fuller picture.
Feed findings into a central SIEM and prioritize alerts via risk scoring so response teams can focus on what matters most.
- Use CSPM for config checks, integrate with SIEM and automate remediation playbooks
- Schedule regular configuration audits, and track remediation SLAs
Validate security controls regularly
Regular validation through breach and attack simulation, red teaming and automated testing proves controls work against current threats. Validation helps bridge the gap between policy and real-world effectiveness.
Report validation findings into governance dashboards and use them to prioritize fixes by business impact rather than by severity alone.
- Run BAS tests for IAM, APIs, data exfiltration and lateral movement scenarios
- Use validation results to tune controls and update playbooks
Align with enterprise security frameworks
Map controls and telemetry to recognized frameworks (NIST, ISO, CSA CCM) to ensure consistency and auditability. Framework alignment helps standardize how risk is measured across teams and clouds.
Use framework mappings to drive programmatic improvements and to demonstrate progress to auditors and executives.
- Maintain a framework-to-control matrix and automate evidence collection
- Use maturity metrics to prioritize capability investments
Support cloud enterprise security providers with Cymulate
Cymulate offers a robust and comprehensive platform that significantly enhances cloud security through its validation capabilities. Cloud security validation enables you to optimize your controls for cloud security management and better protect the systems and data hosted in your cloud platforms.
The platform offers thousands of cloud attack scenarios to simulate high-privilege actions with an “assume breach” mindset, identifying exploitable vulnerabilities across AWS, Azure and GCP.
These scenarios simulate real-world attacks, such as identity-based attacks, API vulnerabilities and lateral movement attempts, allowing organizations to validate the effectiveness of their security controls. The full suite of test cases is completely production-safe and will not harm your cloud environment.
Book a demo today and see how Cymulate supports enterprise cloud security for your organization.
Frequently asked questions
The cloud shared responsibility model means the provider is responsible for the security of the cloud (infrastructure), while the customer is responsible for security in the cloud (data, apps, configurations, identity). Understanding this split is essential to avoid gaps where neither party is accountable.
Practically, enterprises must inventory responsibilities per service model (IaaS/PaaS/SaaS) and map internal controls to those responsibilities. Failing to do so commonly leads to misconfigurations and exposure.
Securing multi-cloud and hybrid environments is challenging because each provider exposes different services, APIs and configuration paradigms, making consistent visibility and enforcement difficult. Differences in telemetry, identity models and compliance mappings create fragmentation that attackers can exploit.
To mitigate this, centralize logging, normalize telemetry, adopt cross-cloud CSMP/CNAPP tooling and standardize configuration baselines and IaC templates to reduce divergence across environments.
Cloud security supports compliance by implementing and evidencing controls mapped to regulations (GDPR, HIPAA, PCI DSS) and by automating continuous monitoring and reporting. These controls make audit evidence repeatable and reduce the manual burden of compliance verification.
Enterprises should use policy-as-code, automated evidence collection and validation to demonstrate control effectiveness (not just control existence) thereby lowering audit risk and remediation cycles.
Common mistakes include relying solely on one class of tools (e.g., only CSPM), misconfigured IAM policies, failing to validate controls through testing and treating compliance as a checkbox rather than an ongoing program. These errors create false confidence and leave exploitable gaps.
Avoid these mistakes by integrating tools into workflows, validating controls through simulations, conducting regular entitlement reviews and measuring program effectiveness with risk and validation metrics rather than artifact counts.
AI/ML for anomaly detection, automated remediation and SOAR playbooks and continuous exposure management platforms are among the emerging technologies reshaping cloud security trends. They increase detection speed, reduce false positives and automate repetitive remediation tasks.
Adopt these technologies carefully, validating outputs and ensuring human oversight for high-risk decisions; combine them with existing controls and validation to avoid overreliance on any single capability.
Enterprises should adopt continuous validation practices (such as BAS, automated control testing and regular red/blue team exercises) to test controls under real-world conditions. Validation ensures controls operate as intended and identifies gaps that static assessments miss.
Feed validation results into a governance loop that prioritizes remediation by business impact, updates controls and IaC templates and tracks progress against maturity metrics to ensure continuous improvement.