Evolving Vulnerability Management to Continuous Threat Exposure Management

Vulnerability management (VM), a cornerstone of cybersecurity since the 1990s, has been steadily evolving. The introduction of the Common Vulnerabilities and Exposures (CVE) system in 1999 standardized the identification and sharing of vulnerabilities. Next, the Exploit Prediction Scoring System (EPSS) added predictive intelligence to vulnerability prioritization.
Now, the industry stands at its next significant milestone: the shift to continuous threat exposure management (CTEM). This enables organizations to move beyond static scanning to continuously validate vulnerabilities with a threat-based approach, effectively prioritize and quickly remediate.
Key blog highlights:
- Explore the persistent challenges VM teams encounter, and the critical role threat validation plays in strengthening their processes
- Discover how the Cymulate Exposure Management Platform integrates threat validation into vulnerability prioritization and demonstrates how attackers exploit weaknesses within your unique environment
- Uncover the practical steps organizations can take to transform a traditional VM program into a continuous, threat-informed CTEM program
- See how the Cymulate Exposure Management Platform automates threat validation to assess and prioritize real-world risk across your assets and vulnerabilities
Challenges with traditional vulnerability management
VM teams continue to face day-to-day challenges and must balance limited resources against an ever-growing backlog of vulnerabilities. They must also navigate extensive compliance demands and reporting obligations. With thousands of new CVEs emerging every month, organizations struggle to identify and prioritize which vulnerabilities are critical and truly matter in their environment.
According to a survey by Ponemon Institute, approximately 60% of breaches involve unpatched vulnerabilities, underscoring the critical need for smarter prioritization and more dynamic approaches to managing risk, such as threat-based validation.
The hard truth is that not every vulnerability can or should be patched immediately. Security teams must make daily trade-offs, deciding which patches are truly critical and which can safely wait. Yet, without context on how each vulnerability interacts with real-world attack paths and security controls, these decisions are little more than educated guesses. Wouldn’t it be nice to know which vulnerabilities are truly critical in your environment and pose a business risk? Or understand how some vulnerabilities are not truly critical since you already have existing security policies in place that provide mitigation of an attack that exploits the vulnerability?
As the attack surface expands with the evolution of cloud, SaaS, identities, supply chain and AI, the reactive “find, prioritize, fix” model no longer suffices. Plus, adversaries continue to mature. Organizations now require a continuous, context-driven strategy that validates, proves and prioritizes exposures based on actual exploitability and true operational risk to maintain threat resilience.
Your solution is CTEM
The Cymulate Exposure Management Platform introduces automated threat-based exposure validation as the critical missing piece in many solutions that claim to deliver full CTEM. It provides organizations with data-driven evidence, combining threat intelligence and business context to reveal how attackers could exploit vulnerabilities by bypassing specific security controls and policies.
By correlating ingested vulnerability data with tested and validated prevention and detection coverage (formerly known as breach and attack simulation), threat intelligence and business context, Cymulate calculates true severity risk scores. This enables organizations to effectively prioritize and focus remediation efforts on exposures that are truly exploitable within their environment.
Security teams are able to understand if their existing defenses already mitigate vulnerabilities, which allows them to focus their patching efforts on those that require immediate action versus those that can be safely deferred. For those truly exploitable security gaps that cannot be patched immediately, teams gain insights into security policies that can be implemented to improve prevention and detection as a form of mitigation, referred to as virtual patches.
The result is a data-driven, continuous cycle of discovery, validation, prioritization and remediation, which is a strategic evolution from reactive vulnerability patching to proactive, risk-based exposure management. Security teams are empowered to proactively and continuously demonstrate and enhance their threat resilience.
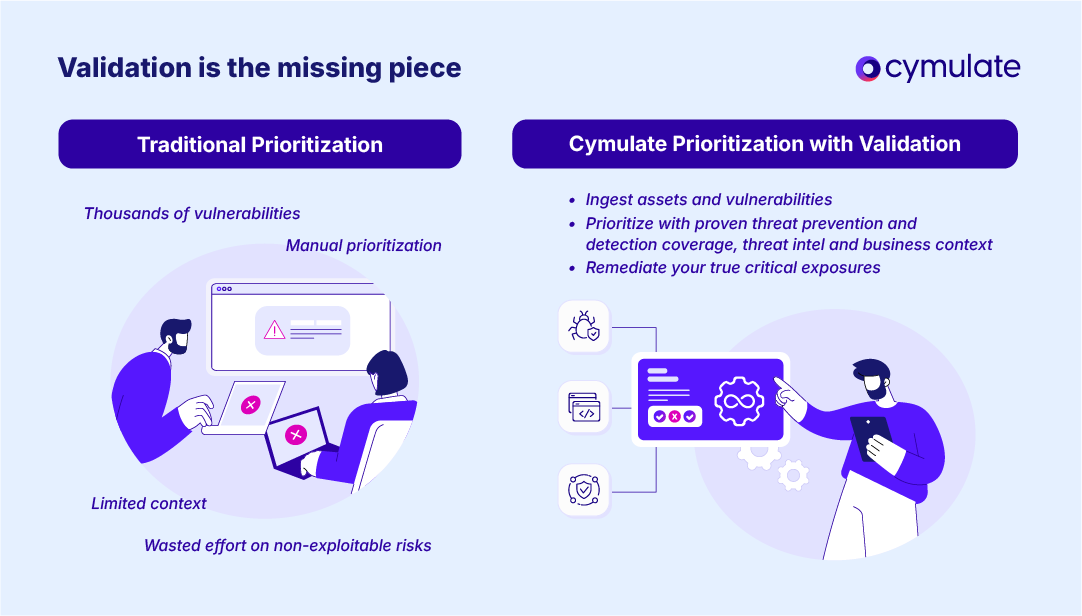
Vulnerability management vs. CTEM: What’s the difference?
Traditional VM is reactive and periodic, focusing on a continued cycle of scanning and patching IT-managed assets. The prioritization is based mostly on CVSS scores and compliance requirements. More mature organizations may be prioritizing with business context data and attack path mapping.
CTEM, in contrast, is continuous and risk-driven, expanding the scope beyond CVEs to include exposures in cloud, identity and data environments. It introduces automated adversary exposure validation into the process. Once the exposures are correlated with real attack scenarios and business priorities, security teams are equipped to continuously execute threat-based validation, prioritize, remediate and prove threat resilience.
| Function | Vulnerability Management | Continuous Threat Exposure Management |
| Scope | IT assets and network vulnerabilities | All exposures across cloud, SaaS, identity and data |
| Discovery | Scheduled scans | Continuous monitoring and exposure discovery |
| Prioritization | CVSS scores, sometimes exploitability | Contextualized by threat, business impact and mitigations |
| Validation | Manual assessment and validation (if applicable) | Attack simulations automatically validate true exploitability of vulnerabilities in an organization’s environment based on real-time existing security controls |
| Mobilization | Patch and report | Collaborate on remediation, improve controls and measure risk reduction |
Table: Difference of VM and CTEM
5 ways security leaders can evolve to CTEM
Below are steps organizations can take to mature their vulnerability management program to CTEM.
- Evaluate your current landscape: Identify how your organization currently discovers and prioritizes exposures.
- Pinpoint and prioritize gaps: Look for blind spots in asset visibility, fragmented tools or poor collaboration between teams.
- Define a business-aligned scope: Focus on critical assets and compliance-driven areas to deliver quick wins and ROI.
- Incorporate threat validation: Test whether existing security controls already mitigate key security gaps and identify critical exposures.
- Expand to continuous validation: Automate ongoing testing to ensure resilience keeps pace with evolving threats.
Inside the Cymulate Platform: How it works
Below is an overview on how the Cymulate Exposure Management Platform ingests assets and exposures and calculates severity risk scores by correlating threat intelligence, business context and threat simulation prevention and detection results.
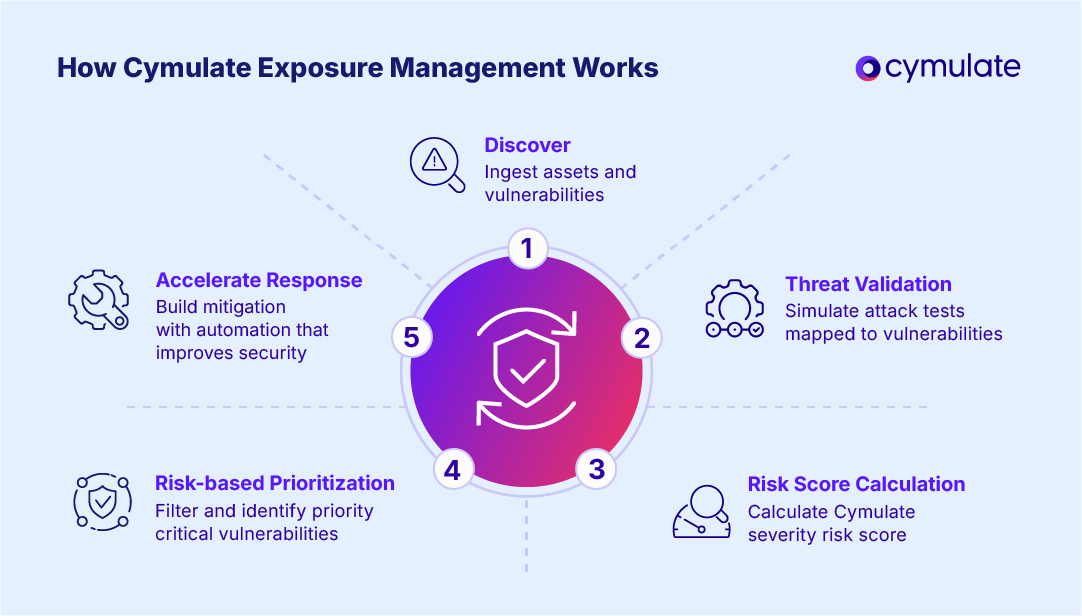
- Data ingestion: The platform connects with leading VM tools like Tenable, Qualys and Rapid7 as well as security platforms like Microsoft and CrowdStrike, aggregating exposure data from across environments and providing a consolidated view.
- Mapping to attack scenarios: Each vulnerability is automatically mapped to attack simulations in our comprehensive attack simulation library to allow organizations to test whether current defenses detect or block exploitation.
- Risk score calculation: Cymulate severity risk score unifies CVSS, threat intelligence, asset criticality and prevention/detection coverage to reflect actual operational risk.
- Prioritization dashboard: Teams leverage interactive dashboards to visualize which vulnerabilities to escalate or de-escalate, enabling effective resource allocation and improving threat resilience for systems, applications, resources and data.
- Remediation and mobilization: Cymulate automates remediation actions, from generating vendor-specific detection rules to applying patches or mitigation scripts.
From reactive to resilient
With adversaries rapidly advancing and organizations facing dynamic business needs, larger attack surfaces, more security tools, limited resources and strict regulatory compliance requirements, evolving to CTEM is essential. To thrive in today’s threat landscape, security and risk leaders need continuous confidence in their overall threat resilience.
Cymulate enables this evolution from VM to CTEM by delivering automated threat validation, effective exposure prioritization and comprehensive remediation.

