Top 5 Must-Have Features in an Exposure Management Platform

Security teams are under growing pressure to reduce risk faster and prove resilience continuously. Attack surfaces expand with every new cloud workload, SaaS connection and identity entitlement. Traditional vulnerability management, point-in-time assessments and siloed security tooling cannot keep pace with dynamic threats, nor modern business operations.
Gartner predicts that “by 2028, organizations enriching SOC data with exposure information will enhance threat evaluation and accelerate incident response, reducing the frequency and impact of cyberattacks by 50%.”
There’s a clear reality taking shape: if your organization can unify and validate exposure data, you’ll withstand more of what comes your way.
Done correctly, exposure management gives security teams the ability to understand not just where they are vulnerable but what is exploitable, what matters most to the business and what to fix first.
Selecting the right exposure management platform now directly impacts security performance. Yet with dozens of vendors claiming “exposure management” it’s important to look beyond buzzwords. Here, you’ll find five features that define a true exposure management platform, why each one matters and how security teams can use them to advance toward a continuous threat exposure management (CTEM) platform.
In this blog, you’ll discover:
- How modern exposure management platforms must unify discovery, validation and prioritization, not just generate lists of vulnerabilities
- Why validation and proof of exploitation are the defining capabilities that separate true exposure management from traditional scanning
- How contextual risk scoring and integrated workflows accelerate remediation and enable continuous SecOps improvement
- How Cymulate delivers must-have exposure management features in one unified CTEM platform to operationalize continuous resilience
Exposure Management Features That Actually Matter
Exposure management has become a crowded category of technology. Vendors with scanning tools, asset discovery products, cloud posture solutions and even traditional vulnerability management providers have all adopted language around exposure management. But terminology doesn’t equate to capability by itself.
Real, unified exposure management requires more than discovering assets or inventorying vulnerabilities. A security program only matures and is effective when an exposure management solution:
- Aggregates data from multiple sources
- Validates which exposures are actively exploitable
- Prioritizes risk based on business context
- Enables remediation workflows across defensive teams
- Continuously retests benchmarks and resilience
This level of validation, correlation and operationalization goes well beyond what traditional scanning or posture management tools offer. These five features separate true exposure management platforms from repurposed point solutions.
#1. Unified, multisource discovery
The foundation of exposure management is complete visibility and that requires aggregating exposure data from every environment a business relies on, not just IT-managed assets.
A mature exposure management platform must unify discovery across the following places: on-premises infrastructure, cloud environments (IaaS, PaaS and SaaS), identity and access systems, endpoints and workloads, network infrastructure and applications (as well as APIs).
This approach requires native connectors and integrations with existing security tooling, including: vulnerability management solutions, endpoint/XDR platforms, cloud security tools, identity providers (IdP, IGA, PAM), network scanners, application security tools and CMDB/asset inventory platforms.
When unified, these data sources provide a multidimensional map of exposure. This spans vulnerabilities, misconfigurations, excessive permissions, exploitable paths and unmonitored attack surface areas.
Why this matters
Silos create blind spots. If vulnerability data sits in one system, identity risks in another and cloud exposures in yet another, it’s impossible for security teams to cross-correlate signals to identify attack paths or root causes. Cross-environment visibility enables teams to:
- Detect exposures that span cloud-to-identity-to-endpoint chains
- Validate real attack paths, not isolated control failures
- Reduce investigation time by consolidating data into a single view
The Cymulate Exposure Management Platform unifies these data sources into a single, continuously-refreshed exposure inventory, mapped directly to attack paths and exploitability.
#2. Native validation and proof of exploitation
Discovery alone is not exposure management. The critical differentiator? Validation, or, the ability to simulate attacker behavior and determine what can truly be exploited.
Modern environments generate more risk signals than any team can manually interpret. Without validation, teams end up chasing “possible vulnerabilities” instead of focusing on weaknesses with actual impact potential.
A mature exposure management platform should deliver:
- Native attack-path validation using real-world TTPs
- Automated proof of exploitation showing whether an attacker could reach critical assets
- Continuous security control validation to confirm defensive effectiveness
- Impact modeling to quantify potential blast radius
- False positive elimination by validating only what is operationally exploitable
The value in validation is providing proof instead of assumptions. The Cymulate Threat Exposure Validation Report 2025 found that of surveyed organizations using continuous validation:
- 47% saw improved mean time to detection
- 40% saw increased threat resilience against the latest immediate threats
- 37% saw continuous validation and tuning of security controls
Why this matters
Validation creates a direct path between exposures and defensive controls. It enables teams to answer questions such as:
- Does a critical CVE actually lead to a compromise in my environment?
- Can attackers pivot from my cloud environment into internal systems?
- Which identity permissions enable lateral movement?
- Do my SIEM, EDR and network detections trigger when they should?
Validation elevates exposure management from information gathering to operational security improvement.
Cymulate delivers automated and safe exploit simulations that validate end-to-end attack paths, turning theoretical risks into measurable, actionable priorities.
#3. Contextual risk prioritization
Once exposures are discovered and validated, the next challenge is prioritization. Traditional risk scoring (based on CVSS or static severity ratings) fails to capture real-world exploitability or business impact.
Your exposure management platform much elevate exposures in context, combining factors such as:
- Exploitability (validated through active testing)
- Asset criticality (business function, sensitivity, operational dependency)
- Threat intelligence (known exploits in the wild, adversary targeting patterns)
- Environmental factors (network position, privilege levels, compensating controls)
- Blast radius (potential lateral movement or privilege escalation pathways)
When these elements are correlated, practitioners receive a true risk score, not a theoretical one.
Why this matters
Contextual prioritization prevents teams from spending endless hours or days patching low-impact exposures while possibly missing high-impact ones. This enables:
- Prioritization of exposures that are exploitable right now
- Visibility into which risks directly affect critical business assets
- Understanding of where controls are failing across detection and prevention
- Better alignment between SecOps, IT operations and leadership
Cymulate correlates exploitability data, attack paths, asset value and current threat intelligence to produce contextual, validated risk scoring that aligns with CTEM best practices.
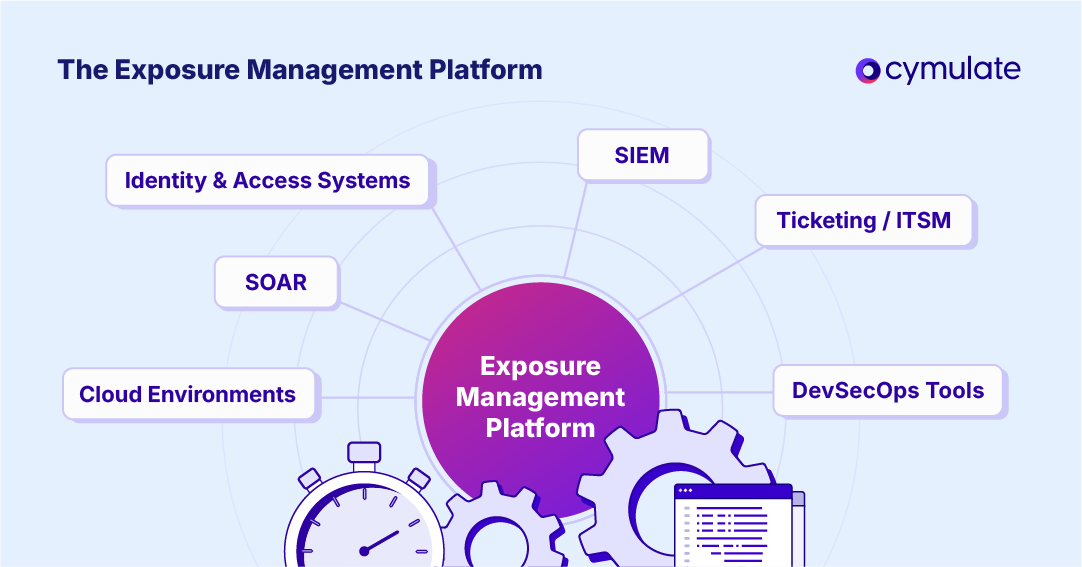
#4. Integration and workflow support
Exposure management cannot be a standalone practice. Once exposures are identified and prioritized, teams must be enabled to quickly take action. This requires end-to-end operationalization across existing SOC and SecOps workflows.
A mature exposure management platform must integrate with:
- SIEM for telemetry enrichment and detection validation
- SOAR for automated response and remediation workflows
- Ticketing systems such as Jira and ServiceNow
- IT operations tools
- Threat intelligence platforms
- DevSecOps pipelines
- Identity and cloud remediations systems
These integrations allow exposures to flow directly into the systems your teams already use to collaborate, triage and resolve issues.
Why this matters
Without workflow integration, exposure management becomes solely a dashboard. Sure, that can be useful in theory, but it’s disconnected from operations. With seamless integrations, your team can:
- Automate remediation tasks
- Enrich alerts with exposure insights
- Break down silos between red, blue and purple teams
- Establish closed-loop validation after remediation
- Reduce MTTR by streamlining communication
Integrated workflows take exposure management from an analytical function into a continuous operation pillar of your cybersecurity strategy.
Cymulate is built with open APIs, flexible orchestration and native integrations designed to unify red, blue and purple team activities across the exposure lifecycle.
#5. Continuous validation and improvement
Exposure management is not a quarterly project, nor is it an annual audit. Threat actors operate continuously. The same must apply to defenders.
A real exposure management platform must support continuous validation, meaning:
- Automated attack-path testing
- Frequent re-testing after remediation
- Scheduled simulations aligned with emerging threats
- Continuous security control insights
- Ongoing posture scoring and benchmarking
- Historical trend analysis to measure resilience improvements
The continuous loop aligns directly with the CTEM model. It’s a framework that moves organizations from reactive to proactive resilience.
Why this matters
Continuous validation ensures that:
- Fixes actually resolve root causes
- New exposures don’t reintroduce old risks
- Detections remain effective as environments evolve
- Teams can demonstrate measurable improvements to executives and auditors
Cymulate automates this cycle, enabling teams to detect, validate, prioritize and improve continuously, not just during scheduled assessments.
Choose a platform that proves, not promises
Modern cyber risk reduction requires unified visibility, validated exploitability, contextual prioritization, workflow automation and continuous improvement. Tools that only scan, only discover or only report are not exposure management platforms. They’re just point solutions that address parts of a problem, not the entire thing.
Organizations evaluating exposure management solutions should invest in platforms that deliver proof-based, unified, continuous exposure management aligned with CTEM maturity.
Cymulate offers unified exposure discovery, validation and prioritization in one platform. It's now your time to prove the threat and improve resilience continuously with Cymulate.
Want to see Cymulate in action? Sign up for a demo today.

