Kubernetes Security Best Practices: Insights from Real-World Attack Simulations
Securing Kubernetes in production environments is more than a checkbox exercise. It’s a continuous battle against sophisticated attack vectors.
Research from Cymulate underscores a stark truth: native cloud provider defenses fall short when it comes to detecting and preventing real-world Kubernetes threats.
It’s time to understand hard-earned lessons from simulated adversarial campaigns against Kubernetes clusters across AWS, Azure, and GCP. Our goal is simple: equip Kubernetes architects, DevSecOps engineers and platform security teams with actionable best practices that go beyond native tools and help secure containerized infrastructure at scale.
View Full Research: Native Cloud Defenses vs Kubernetes Attacks
What is Kubernetes and Why Does Its Security Matter?
Kubernetes (K8s) is the de facto orchestration platform for deploying and managing containerized applications. Its flexibility and power make it ideal for modern microservices architectures.
However, this complexity also introduces a broad attack surface: from misconfigured role-based access control (RBAC) policies and unmonitored workloads to privilege escalation paths and unsecured secrets.
In production, even a single misstep can lead to data exfiltration, lateral movement or full cluster compromise. Kubernetes security isn’t just about hardening configurations. It’s about operational resilience against active threats.
Why Kubernetes Security Still Fails Across Major Cloud Providers
Over the past few years, Kubernetes clusters have been increasingly targeted by sophisticated attacks, including RBAC backdoor exploits, the Scarleteel campaign, AWS infrastructure breaches and crypto mining operations using Dero and Monero. These attacks often exploit common misconfigurations such as overly permissive access controls and exposed API servers.
In the RBAC backdoor case, a misconfigured API server allowed unauthenticated access, enabling attackers to gather information and escalate privileges. These incidents reveal the advanced tactics used by threat actors to steal credentials and persist in cloud environments.
They underscore the urgent need for organizations to secure their Kubernetes deployments by addressing misconfigurations, enforcing least-privilege access, and performing continuous security validation.
Proactive defense and adherence to Kubernetes security best practices are essential to reducing risk in cloud-native infrastructure.
Cymulate’s research rigorously tested Kubernetes attack detection across native cloud security services: AWS GuardDuty, Azure Cloud Defender and Google Security Command Center. The results are sobering—fewer than 50% of Kubernetes-specific attack techniques were detected across these platforms.
Red team simulations emulated MITRE ATT&CK TTPs, including persistence, privilege escalation, defense evasion and container escape techniques. The verdict? Native tools provide limited coverage, and security teams need a defense-in-depth approach that includes runtime protection, policy enforcement and breach simulation.
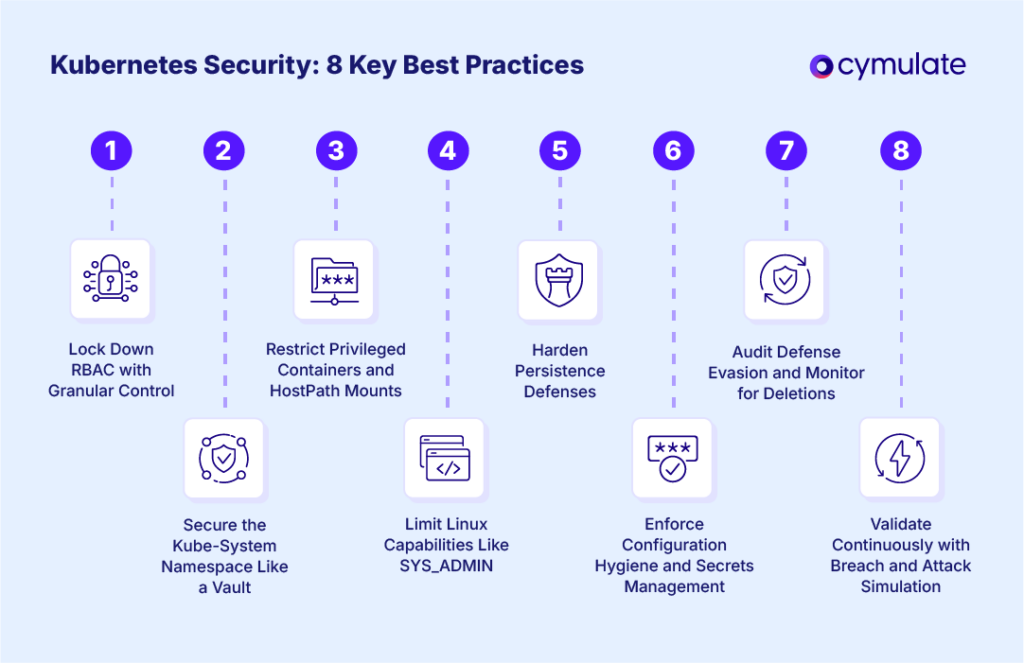
1. Lock Down RBAC with Granular Control
Key Insight: Cymulate successfully exploited excessive permissions by binding ClusterRole to system:anonymous, which was undetected in 2 of 3 cloud platforms.
Best Practices:
- Use RoleBinding over ClusterRoleBinding unless cluster-wide access is strictly required.
- Prohibit anonymous access and ensure default service accounts don't have elevated privileges.
- Regularly audit and version-control role bindings—integrate checks into CI/CD pipelines.
- Apply least privilege principles rigorously; validate permissions with tools like rakkess or kubectl-who-can.
2. Secure the Kube-System Namespace Like a Vault
Key Insight: Commands executed in the kube-system namespace went undetected on GCP, with only Azure alerting the activity.
Best Practices:
- Treat kube-system as a critical infrastructure zone; restrict access via strict RBAC policies.
- Enforce policies using PodSecurityAdmission, OPA/Gatekeeper or Kyverno to block non-system pods.
- Implement real-time monitoring and alerting on pod creation events in sensitive namespaces.
3. Restrict Privileged Containers and HostPath Mounts
Key Insight: Cymulate used a privileged Docker-in-Docker (DinD) pod to gain full host access—an attack vector missed by native defenses.
Best Practices:
- Ban the privileged: true setting unless necessary and explicitly reviewed.
- Audit hostPath volumes—replace with CSI drivers or other abstractions when possible.
- Apply policies via PodSecurity standards or Kyverno to block dangerous mount configurations.
4. Limit Linux Capabilities Like SYS_ADMIN
Key Insight: Containers granted SYS_ADMIN ran host-level commands without detection on 2 cloud platforms.
Best Practices:
- Use securityContext.capabilities.drop: ["ALL"] to remove all Linux capabilities by default.
- Whitelist capabilities (e.g., NET_ADMIN) only with business justification and review.
- Use PodSecurityPolicies, Kyverno, or OPA to enforce allowed capabilities per workload type.
5. Harden Persistence Defenses
Key Insight: Cymulate simulated persistence via nohup, useradd and shell scripts—undetected by GCP entirely.
Best Practices:
- Use AppArmor or SELinux profiles to block known persistence methods like nohup or cron jobs.
- Monitor for execution of binaries like useradd, passwd or wget inside containers.
- Implement runtime threat detection tools (e.g., Falco, Sysdig Secure) for suspicious process creation.
6. Enforce Configuration Hygiene and Secrets Management
Key Insight: Cymulate accessed Kubelet’s kubeconfig and found hardcoded environment tokens in pod specs.
Best Practices:
- Store credentials in Kubernetes Secrets or external vaults like HashiCorp Vault.
- Block the use of plaintext secrets in environment variables through validation policies.
- Secure access to secrets using fsGroup, read-only mounts and strict RBAC.
7. Audit Defense Evasion and Monitor for Deletions
Key Insight: Attackers cleared .bash_history and deleted Kubernetes events to evade detection. Only Azure consistently logged these actions.
Best Practices:
- Enable immutable logging via Kubernetes audit webhooks; stream logs to a centralized SIEM.
- Set up alerts for deletion events, including secrets, ConfigMaps and historical logs.
- Use runtime integrity tools (e.g., Falco, Tracee) to detect tampering with log and audit trails.
8. Validate Continuously with Breach and Attack Simulation
Key Insight: Cymulate safely emulated real-world attacks across ATT&CK stages, revealing multiple detection gaps.
Best Practices:
- Adopt continuous security validation to uncover blind spots in detection and response.
- Use breach and attack simulation (BAS) platforms to simulate TTPs like lateral movement, privilege escalation, and data exfiltration.
- Prioritize remediations based on actual detection and response performance, not assumptions.
Native Cloud Tools Are Not Enough
Cymulate’s field-tested research clearly shows that AWS, Azure, and GCP native tools provide only partial Kubernetes security coverage. Security teams cannot rely solely on GuardDuty or Cloud Defender. Instead, organizations must:
- Enforce strict configuration hygiene
. - Implement runtime and behavioral detection
. - Conduct regular adversary emulation to validate controls
.
The security of your Kubernetes environment depends not on any single tool, but on your defense-in-depth architecture and your willingness to validate assumptions.