What Your Security Controls Aren’t Telling You: Gaps, Drift and New Threats
Optimizing Your Security Controls
Organizations of all sizes no longer have a choice but to make some level of investment in cybersecurity. With any investment needing to payoff and keep critical data secure, having confidence that your security controls are up to the task to defend against a threat actor is a must. And just because you have security controls in place doesn’t mean your security is under control. With variables such as, constantly changing environments, new and evolving threats and controls left in default, it’s hard to keep track.
There are key strategies to strengthen organizational security posture, focusing on identifying and addressing configuration gaps, detecting control drift, helping ensure coverage against emerging threats and understanding how attackers evade controls. Even with key strategies in place, knowing your security controls weaknesses is equally as important.
Key Challenges in Security Control Effectiveness
Security controls are an essential part of safeguarding your organization’s assets, however there are certain things they might not be telling you. Just when you thought you had everything under control and within your grasp, an attacker can make a move. Security controls can detect and block malicious activities, but they can’t always anticipate the attacker’s motives or end goal. Intention can make all the difference and that’s where having experienced resources goes a long way.
Another area where security controls need more human input is user behavior. While controls can monitor activities, they may not provide insights into why users behave a certain way, which can be crucial for understanding security risks. Thinking you're blocking ransomware, phishing or malicious content is just the start; understanding the context of alerts and how to predict future threats often requires human intelligence and strategic planning.
Without common control gaps identified, they can quickly leave your organization vulnerable to cyber threats. Weaknesses like malicious URLs, custom payloads and signature-based malware can all lead to potential threats. It’s critical to know your attack surface and see what an attacker sees, including cloud systems and development and staging environments that go into production.
Four Proven Strategies to Optimize Your Organization’s Security Controls
1. Identify and address configuration gaps
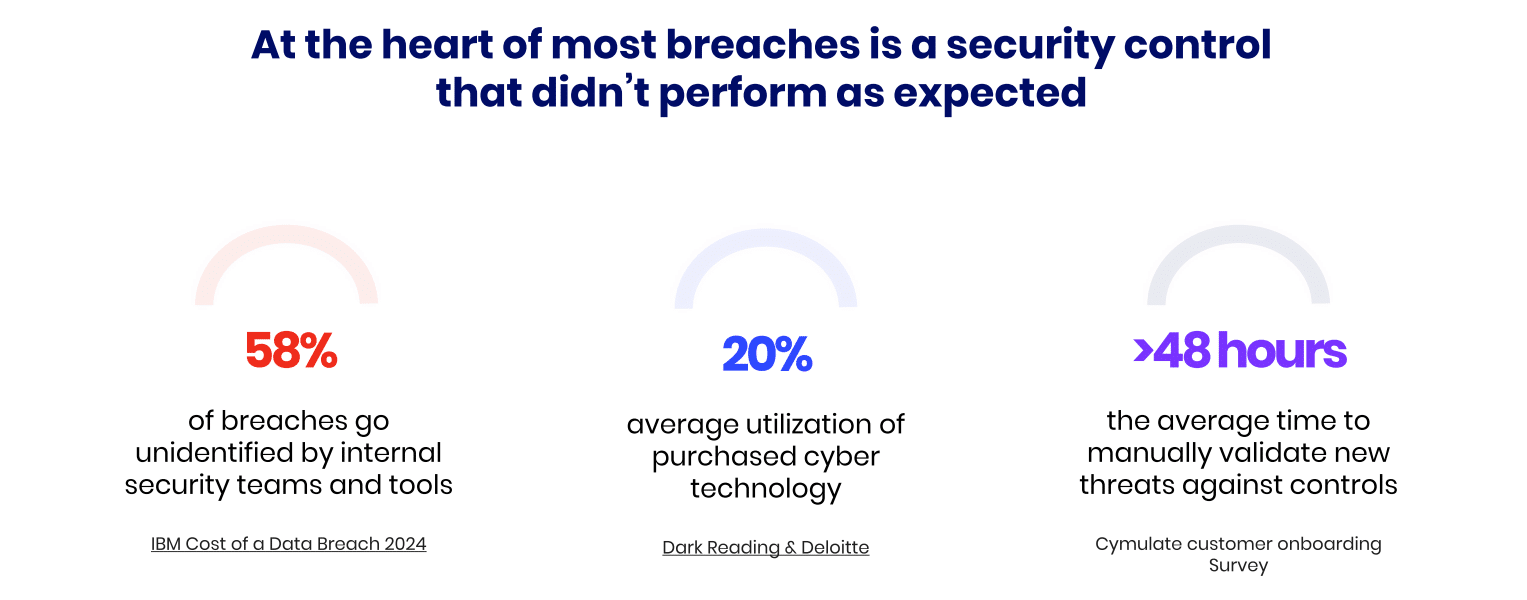
According to the IBM Cost of a Data Breach 2024 Report, 58% of breaches go unidentified by internal security teams and tools. Most breaches happen due to a security control that did not perform as expected. Most Cymulate customers report an average of 48 hours for the time it takes to manually validate new threats against controls.
Configuration gaps can act as silent vulnerabilities within your organization’s security infrastructure. Regular audits and assessments are essential to identifying weaknesses while implementing automated tools can continuously scan for misconfigurations. Prioritizing this step can help strengthen your organization’s defenses against an adversary while ensuring regulatory standard compliance.
2. Detecting control drift and prioritizing remediation
Security controls can drift from their original and optimal configuration over time due to system updates, user actions or changes in IT environments. This drift can lead to unintended vulnerabilities, however implementing continuous monitoring tools that alert you to any control drift is vital.
Once identified, prioritizing remediation based on the severity of the potential drift impact can take place. Automated response systems can help expedite this process and help ensure that security measure remain aligned with security policies.
3. Ensuring coverage against emerging threats
Gaining insights into the latest threats and adjusting your security controls accordingly using threat intelligence platforms is a must to stay a step ahead against a threat actor. This comes with comes with regularly updating all operating systems, applying patches quickly and staying on top of threat hunting exercises to identify any potential risks before they can be exploited. There’s a big cyber community to rely on to help share threat information and build your organization’s ability to anticipate emerging threats.
4. Understanding how attackers evade your controls
Understanding human behavior is a critical element to staying ahead an adversary and being able to predict their next move. Just as technology is constantly evolving, so are attackers and their techniques to bypass security controls.
To be ready, conduct red teaming and penetration testing exercises to simulate real-life potential attacks to uncover weaknesses in your defenses. Analyze the results to develop stronger strategies to counteract these tactics. Implement continuous training and education internally for security teams and all employees on the latest attack techniques, including phishing scams.
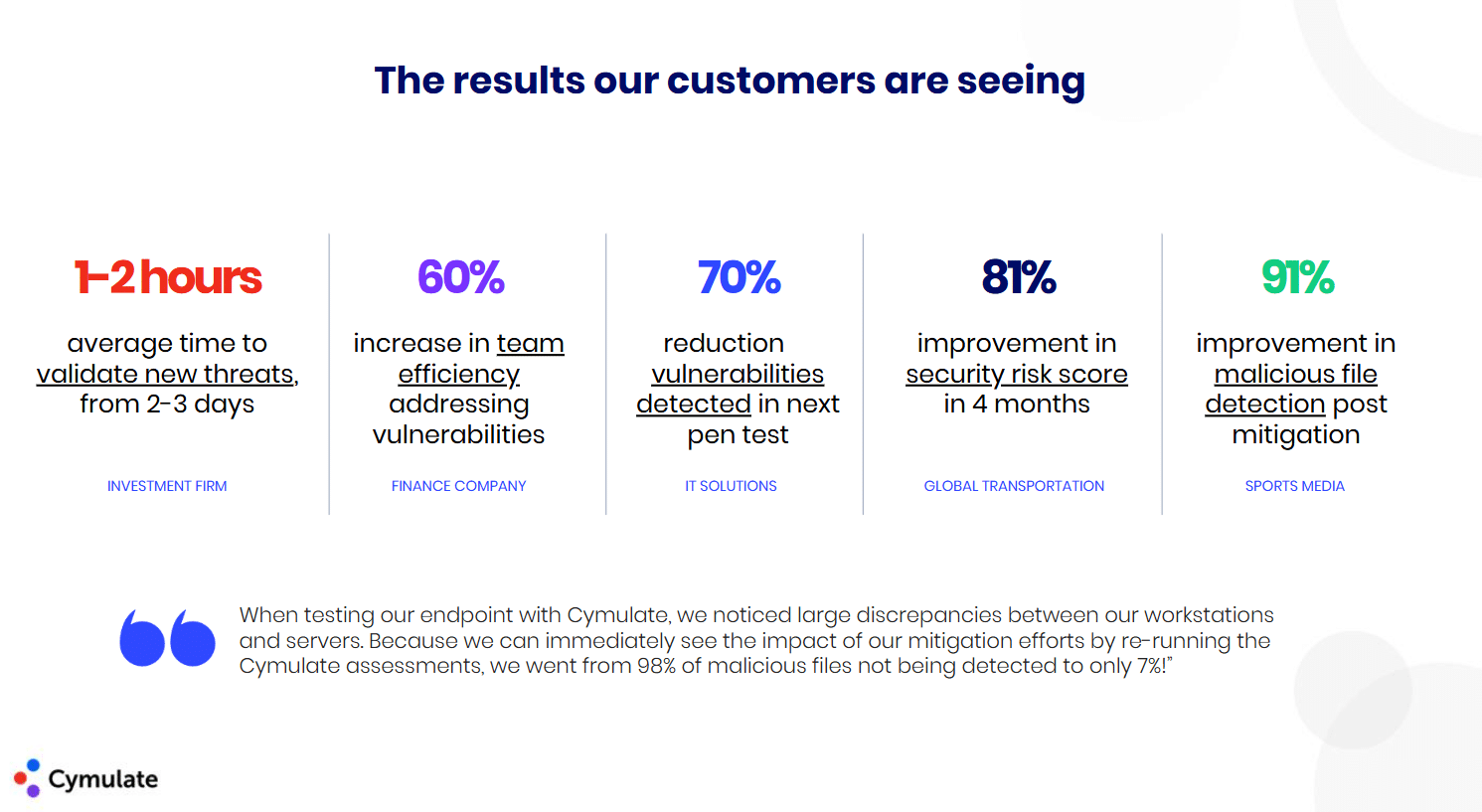
Key Takeaways for Strengthening Your Security Framework
Optimizing your organization’s security controls is an ongoing process that requires vigilance, adaptability and a proactive approach. It demands ongoing testing and assurance for proof of effectiveness at each stage. This must include ongoing security control validation automation and AI to keep up the pace new daily threats.
By implementing the four key strategies of identifying and addressing configuration gaps, detecting control drift, ensuring coverage against emerging threats and understanding how attackers evade controls, an organization is in an optimal position to build a resilient security framework.
To learn more about how Cymulate can help your organization get its security controls under control, watch this webinar.