Red Teaming
In cybersecurity, organizations often assemble red, blue, and purple teams to assess their security posture and resilience to cyber threats. The different colors symbolize the different responsibilities of each team:
The reasoning for the red and the blue team definitions originates from military exercises where training teams simulate enemy actions. In these exercises, the "red team" represents the attackers, while the "blue team" represents the defenders.
What is a red team?
A red team in cybersecurity is a group of offensive security testers, such as penetration testers, vulnerability assessors, and ethical hackers, who simulate cyber attacks. They aim to think like attackers and use tactics, techniques, and procedures (TTPs) seen in the real world to breach an organization's defenses. These tests are designed to challenge and verify an organization’s resilience to threats and find weaknesses in its security posture before malicious threat actors (real-world hackers) can exploit them.
What does a red team do?
A red team tests and evaluates an organization’s security defenses from an attacker’s perspective on an ongoing basis. Red team operations are more comprehensive and adversarial than routine security assessments, which often involve checking for compliance or performing standardized vulnerability scans. Their primary activities are:
- Identifying Exploitable Vulnerabilities: The primary goal of a Red Team is to uncover weaknesses in an organization’s security posture. By simulating real-world attacks, they identify vulnerabilities that malicious actors could exploit.
- Testing Security Measures: Testing security controls such as firewalls, intrusion detection systems, access controls, and other security mechanisms to ensure they function as intended.
- Simulating Real-World Attacks: Adopt the tactics, techniques, and procedures (TTPs) used by actual cyber criminals to help organizations understand if and how they would hold against real threats
- Improving Incident Response: Red Teams provide valuable insights into the effectiveness of the organization’s incident response procedures, helping, for example, blue teams refine their response strategies
In the context of identifying IoCs, the Pyramid of Pain framework offers an effective approach to prioritization. The pyramid categorizes IoCs based on how difficult they are for attackers to modify, with hashes, IP addresses, and domains at the base and TTPs at the peak. By focusing on TTPs, red teams can create significant operational challenges for adversaries, disrupting their campaigns more effectively. This strategic focus ensures that red team activities go beyond surface-level vulnerabilities and address deeper security gaps.
Methods used
Red teams employ various methods and tactics to simulate real-world cyber threats. The methods used can vary from organization to organization, depending on the needs of each specific company. The following sections outline some of the most common methods used, from the initial reconnaissance phase to the final stages of exfiltration.
1. Reconnaissance
Open Source Intelligence (OSINT): Gathering information from publicly available sources (websites, social media, public records) to identify potential attack vectors and entry points.
Network Scanning: Using tools like Nmap or Nessus to identify open ports, services, and network vulnerabilities.
Social Engineering Recon: Collecting information about employees, organizational structure, and internal processes that could be exploited in social engineering attacks.
2. Social Engineering
Phishing: Crafting deceptive emails or messages to trick employees into revealing credentials, clicking malicious links, or downloading malware.
Pretexting: Creating a fabricated scenario to manipulate someone into disclosing sensitive information or performing an action.
Baiting: Leaving physical devices (like USB drives) with malware in public or easily accessible areas to see if someone will plug them into their computer.
3. Exploitation
Vulnerability Exploitation: Identifying and exploiting known or unknown software, application, or system vulnerabilities to gain unauthorized access.
Credential Theft: Using methods like password spraying, brute-forcing, or exploiting weak passwords to gain access to accounts and systems.
Zero-Day Exploits: Utilizing unknown or unpatched vulnerabilities to compromise systems. Zero-day attacks are highly effective and challenging to defend against since the exploit is unknown to the vendor or the organization.
4. Lateral Movement
Pass-the-Hash and Pass-the-Ticket Attacks: These methods involve using stolen credentials or tokens to move laterally within the network. In a Pass-the-Hash attack, the attacker captures a user's hashed password and reuses it to authenticate as that user without needing to know the actual password. Similarly, in a Pass-the-Ticket attack, the attacker steals a Kerberos ticket to access resources within the network. Both techniques allow attackers to access additional systems and escalate their privileges without cracking the original password.
Pivoting: After gaining initial access to a network, Red Teams often use pivoting techniques to move from one compromised system to another, using the compromised system as a gateway to other parts of the network. This allows attackers to expand their foothold and access more sensitive areas of the network.
Living off the Land (LotL): Living Off the Land attacks involves using the existing tools and processes within a network to carry out an attack. Red Teams may use built-in tools like PowerShell, Windows Management Instrumentation (WMI), or other legitimate software to conduct malicious activities
5. Exfiltration
Data Encryption and Exfiltration: Encrypting stolen data to prevent detection during exfiltration. This makes the data look like normal encrypted traffic, making it harder for security teams to detect the breach.
Steganography: Hiding data within other files, such as images or documents, to conceal the exfiltration process. This can help avoid detection by security monitoring tools.
Using Legitimate Channels: Exfiltrating data through legitimate channels like email, cloud storage, or DNS requests further complicating detection efforts.
Red Team vs Blue Team
While the red team plays the role of the offender or attacker, the blue team defends against the attack from the red team.
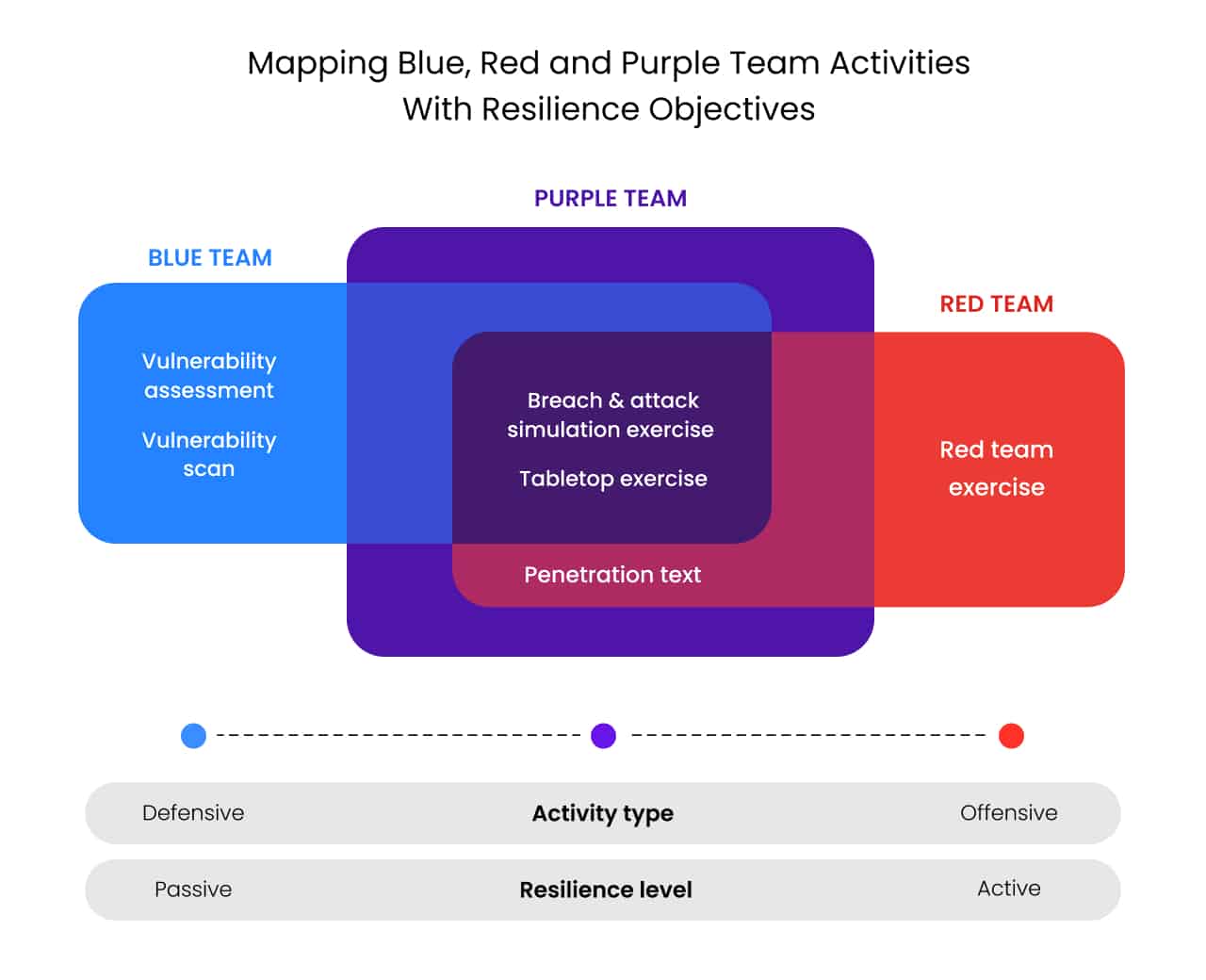
For example, a red team might simulate a cyber attack in which they attempt to breach security measures, exfiltrate sensitive data, or disrupt services. The blue team is then responsible for defending against these simulated attacks. They focus on detecting, responding to, and mitigating any attempted breaches. This involves monitoring network traffic, analyzing security logs, deploying patches, and refining defense strategies to prevent future incidents.
Common red teaming problems
While the tasks performed by a red team are essential to any cyber security posture assessment, they might not be enough to maintain a resilient cyber defense in the constantly evolving cyber threat landscape. Some of the challenges facing red teams are:
- Lack of resources and limited capacity
- Continuously growing threat landscape
- Communication gaps with blue teams and other parts of the cyber defense company infrastructure
- Inability to extensively validate each security defense
Red Teaming Tools
There is a wealth of pen testing and red teaming tools out there, both paid and open source, to help
you test your infrastructure, including
- MITRE Caldera is an automated adversary emulation tool designed to test defenses against the latest cyber threats. Caldera provides modular TTPs based on MITRE ATT&CK and can automate complex attack chains, making it a powerful addition for those who need to simulate realistic, multi-step attacks. However, users require technical expertise to fully leverage its potential, and the tool provides limited guidance on addressing identified weaknesses.
- Red Canary Atomic Red Team is another popular option, providing a library of simple, atomic tests that emulate a range of known adversarial behaviors. Its straightforward framework allows security teams to test specific TTPs across different platforms with less setup, making it ideal for assessing individual components of a security posture. Yet, as with Caldera, it lacks comprehensive remediation guidance, requiring analysts to devise their own solutions for any detected vulnerabilities.
- The Metasploit Framework remains one of the most widely used tools for penetration testing and red teaming. It offers extensive exploitation and post-exploitation capabilities. It is highly adaptable, with a vast repository of exploit modules that can be customized to suit various testing needs. However, Metasploit demands substantial technical knowledge, and, like many red teaming tools, it does not prioritize vulnerabilities or offer specific remediation steps.
Red team tools often lack the latest cyber threat intelligence, which means they can only challenge controls against known threats. Alternatively, red team testers must conduct research in advance to incorporate the latest threat intelligence in their testing. New malware variants emerge daily, requiring you to ensure that your controls can identify the newest attacks’ Indicators of Compromise (IoCs), stealth techniques, and behaviors.
Due to these variables, it is challenging for CISOs and IT teams to make meaningful evaluations of security control effectiveness across attack vectors for accurate security risk assessment. A lack of remediation guidance further complicates the prioritization of resources for mitigating identified weaknesses.
Without end-to-end automation, red teaming exercises are difficult to repeat consistently, hard to perform on a large scale, and challenging to execute with a broad scope. For instance, after running an exercise and fine-tuning controls, you would want to repeat the same barrage of tests to ensure the adjusted controls work.
Automated Red Teaming
Given red teams' challenges, many organizations looking to strengthen their security posture are turning to automated security control validation. Automated security control validation involves the continuous testing and validation of security controls to ensure they are functioning as intended and that they are effective against the latest emerging threats.
One of the primary advantages of automated security control validation is the ability to conduct ongoing, dynamic testing without the need for constant manual intervention. This approach allows security teams to run simulations of advanced threats, attack techniques, and specific adversary behaviors continuously, providing a near-real-time assessment of vulnerabilities. Unlike traditional red teaming, which may only happen periodically due to resource and time constraints, automation enables continuous testing, helping security teams to quickly identify any changes in control effectiveness as new threats emerge or as the IT environment evolves.
Bottom Line
- Red teams, by adopting real-world attack tactics, help organizations proactively identify and remediate vulnerabilities, testing controls across a variety of adversarial techniques.
- Common red teaming methods include reconnaissance, social engineering, exploitation, lateral movement, and exfiltration, each designed to assess different aspects of an organization’s security defenses.
- Despite their benefits, red teams face challenges like limited resources, a continuously expanding threat landscape, and difficulties in consistent validation, which can make it hard to fully assess and strengthen defenses.
- Automated red teaming through security control validation offers a scalable, continuous testing approach, providing near-real-time insights into vulnerabilities and helping prioritize remediation based on risk, making it a valuable enhancement to traditional red team efforts.