What Is Petya and NotPetya Ransomware?
In June 2017, a devastating ransomware strain—first believed to be a variant of Petya and later known as NotPetya—caused widespread disruption worldwide. This ransomware encrypts Windows systems, rendering them inoperable and demanding ransom payments.
How Do Petya and NotPetya Spread?
Petya ransomware encrypts the master boot records of infected Windows computers, making affected machines unusable.
Open-source reports indicate that after opening the attached file, the infected machine communicates with the 182.165.29.78 IP address. Following opening a communication channel between the infected machine and the malicious C&C, a screenshot appears which displays that a scan of the hard disk is in progress (CHKDSK).
It is believed that this is when the distribution of the ransomware within the network begins using several communication protocols such as SMBv1, and a number of additional protocols and lists 139, 445, and 135.
The ransomware scans the computer folders and encrypts most of the useful files and data.
After encryption, the ransomware displays a message that requires the user to pay hundreds of dollars for the de-encryption of the data. Victims have a specific amount of time to pay. If payment is not made by the deadline, the ransom increases.
How Cymulate Helps Mitigate Ransomware Risk
Organizations utilize Cymulate’s Ransomware Resilience Assessment to ensure they are prepared for attacks such as the Petya ransomware. The platform's broad range of assessments test for breach feasibility, as well as what would occur if a ransomware attack successfully penetrated an organization. Additionally, attack simulations of new and emerging ransomware payloads are added daily to the platform so organizations can immediately assess their security against the latest threats.
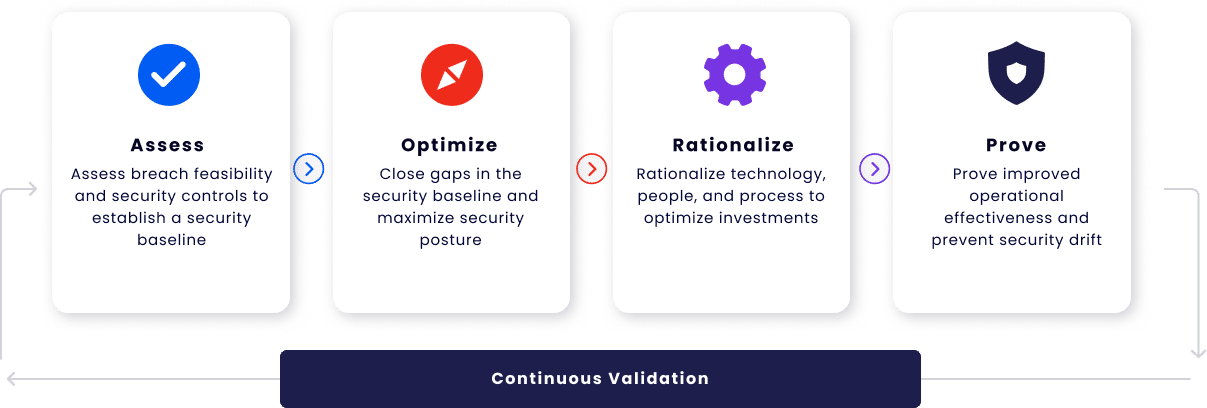
The results of each assessment are used to identify any weak points in the organization's cybersecurity posture. The platform also provides remediation guidance so organizations can close gaps and optimize protection against ransomware attacks.


