10 Strategies for Effective Cybersecurity Risk Mitigation
As digital infrastructures expand and threat actors grow more sophisticated, organizations must move beyond reactive defense and adopt proactive, risk-informed strategies to protect their critical assets.
Cybersecurity risk mitigation refers to the systematic identification, evaluation and reduction of risks that could negatively impact an organization's information systems. The goal is to minimize exposure to cyber threats and ensure operational continuity, regulatory compliance and business resilience.
Effective cyber risk mitigation isn’t optional—it’s essential for protecting brand reputation, customer trust, and the bottom line.
The Importance of Cyber Risk Mitigation in Today’s Threat Landscape
Cybercriminals are leveraging AI-driven malware, ransomware-as-a-service models and increasingly targeting supply chains and cloud environments. The days of relying on annual assessments or static defenses are long gone.
Organizations like yours face mounting pressure not only from threat actors but also from compliance bodies. Standards like NIST, ISO 27001, HIPAA and PCI-DSS demand comprehensive cyber risk mitigation plans as part of broader governance and security programs.
Moreover, risk assessment in cybersecurity must evolve into a continuous, data-driven practice. Without real-time visibility into your security posture, it's nearly impossible to keep pace with emerging threats or confidently make risk-based decisions. With that in mind, we’re offering 10 ways your organization can approach, consider and implement effective cybersecurity risk mitigation strategies to keep your critical systems safe.
10 Strategies for Effective Cybersecurity Risk Mitigation
1. Conduct Continuous Risk Assessments
Periodic assessments are no longer enough. Organizations must adopt continuous risk assessment practices to identify new vulnerabilities, evolving attack surfaces and misconfigurations as they emerge.
Tip: Use automated tools to scan networks and assets regularly. Integrate threat modeling and business impact analysis to prioritize critical risks.
2. Implement Layered Security Controls (Defense in Depth)
A single security solution won’t suffice. A Defense in Depth strategy uses overlapping layers of protection across endpoints, networks, applications, and identities.
Example: Combine firewalls, endpoint detection and response (EDR), network segmentation and multi-factor authentication (MFA) for robust coverage.
3. Prioritize Threat Intelligence and Threat Hunting
Actionable threat intelligence enables security teams to understand attacker tactics, techniques, and procedures (TTPs). Threat hunting takes a proactive approach to uncover hidden threats already inside your environment.
Tip: Subscribe to real-time threat intelligence feeds and implement threat hunting playbooks based on MITRE ATT&CK techniques.
Learn more: Exposure Validation from Cymulate
4. Regularly Validate Security Controls with Automated Testing
Security controls can degrade over time or fail silently. Regular validation ensures your defenses are operating as intended.
Solution: Use automated Breach and Attack Simulation (BAS) to safely test how your environment would respond to real-world attack scenarios.
See how: Threat Validation from Cymulate
5. Patch Management and Vulnerability Prioritization
Unpatched systems are one of the most exploited attack vectors. But with thousands of vulnerabilities disclosed each year, not all are equally critical.
Approach: Implement a risk-based vulnerability management strategy that prioritizes vulnerabilities based on exploitability, asset value and business impact.
6. Employee Training and Phishing Simulations
Human error remains the leading cause of data breaches. Ongoing security awareness training empowers employees to recognize and respond to social engineering attacks.
Tip: Conduct regular phishing simulations and track improvements over time to build a security-first culture.
7. Enforce Strong Access Controls and Least Privilege
Limit access to systems and data based on user roles and responsibilities. The principle of least privilege minimizes the potential damage from compromised credentials.
Example: Implement Just-in-Time (JIT) access and regularly review privilege escalations.
8. Backup Critical Data and Validate Recovery Plans
Backups are a last line of defense, especially in the event of ransomware. But they’re only effective if tested.
Strategy: Maintain offline, encrypted backups and regularly perform disaster recovery drills to ensure data restoration processes work under pressure.
9. Monitor Third-Party and Supply Chain Risks
Vulnerabilities in partner systems or software vendors can introduce significant exposure.
Actionable Step: Implement a third-party risk management program to assess and monitor vendor security practices and include them in incident response plans.
10. Develop and Test an Incident Response Plan Regularly
An untested incident response (IR) plan is only marginally better than none. Your IR plan should outline clear roles, escalation paths, and playbooks for various attack scenarios.
Best Practice: Conduct tabletop exercises and red team engagements more than once a year to keep your team prepared.
Cymulate’s Role in Risk Mitigation
Cybersecurity risk mitigation strategies are only as effective as their implementation—and verification. That’s where Cymulate can make a major difference.
Cymulate combines the best of automated security validation with a focus on threat exposure to continuously test and optimize your security. Integrate Cymulate into your exposure management program to focus on the exploitable.
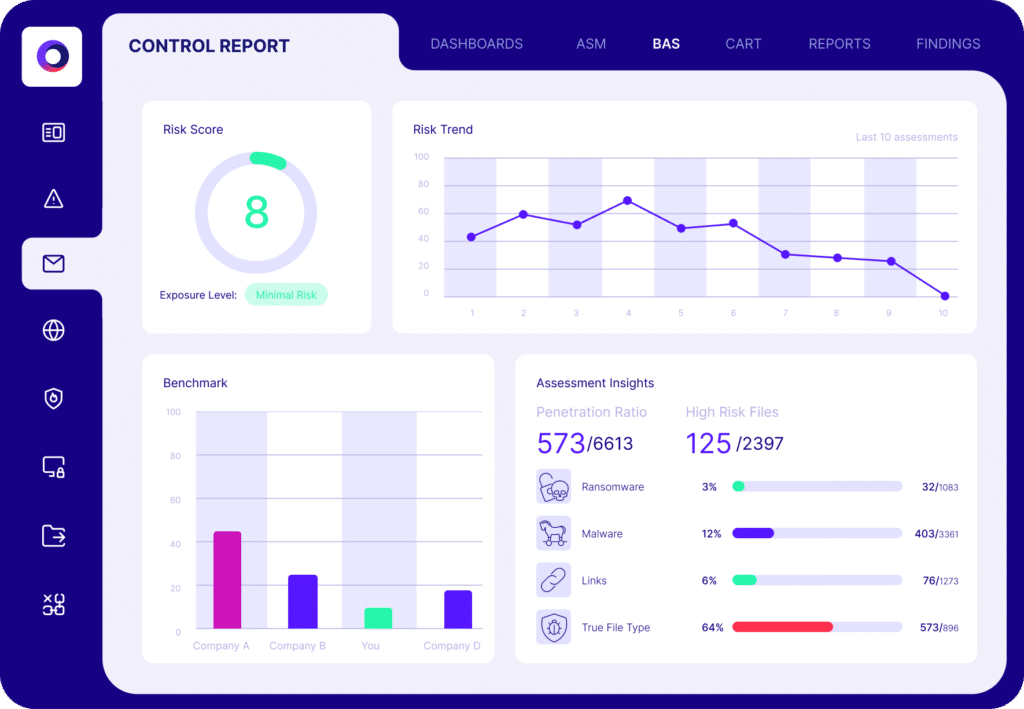
Organizations can move from periodic assessments to exposure validation thanks to Cymulate, helping security leaders:
- Identify and prioritize exposures through automated Breach and Attack Simulation (BAS)
- Validate the effectiveness of security controls in real-time
- Support risk-informed decision-making by mapping findings to business impact
- Enhance cyber resilience with attack path mapping and exposure analytics
By integrating Cymulate Exposure Validation and Immediate Threat Intelligence solutions, organizations gain clear visibility into their current security posture and can take action before attackers do.
Key Takeaways
- Cybersecurity risk mitigation must be proactive, not reactive.
- The modern threat landscape demands continuous assessment, validation and adaptation.
- Layered defenses, strong access policies, threat intelligence and employee training are key pillars.
- Automated tools like Cymulate provide real-time insights and validation to support decision-making and reduce cyber exposure.
- Building a comprehensive cyber risk mitigation plan strengthens your compliance posture and boosts resilience.
Ready to Proactively Manage Cyber Risk?
Traditional cybersecurity approaches can’t keep pace with modern threats. Cymulate empowers you to validate defenses, uncover exposures and reduce cyber risk with confidence.
Start your risk-informed journey with Cymulate’s proactive security solutions by booking a demo today.



