Cybersecurity Risk Rating: What It Is and Why It Matters
A cybersecurity risk rating turns a messy security picture into a single, defensible signal. Boards want a number. Regulators expect evidence. Insurers and partners ask for proof. At the same time, attack surfaces sprawl across cloud, SaaS and third-party vendors that change by the hour. Without a clear rating, it’s hard to decide where to focus, what to fix first and how to show progress.
Risk ratings solve that problem by translating technical exposure into a score or grade that anyone can understand.
Used well, they align security work with business goals, support compliance reviews and set targets tied to your risk appetite. Used poorly, they become static snapshots that miss what attackers can actually exploit.
Key highlights
- A cybersecurity risk rating provides an objective, data-driven measurement of an organization’s cybersecurity posture, condensing technical security performance into a single score or grade. These cybersecurity ratings act as a “credit score” for cyber risk, enabling stakeholders to quickly grasp exposure levels.
- With the average cost of a data breach hitting $4.88 million in 2024 (up 10% from the prior year), organizations need easy-to-understand benchmarks to gauge risk. Accurate cyber risk scorecard ratings bridge technical IT threats with business priorities, support compliance mandates (NIST, ISO 27001, DORA, SEC disclosures) and help executives quantify cyber risk in financial terms.
- Cybersecurity risk ratings drive objective measurement and continuous monitoring. Security teams use these risk scorecards for resource prioritization (focusing on high-risk gaps first), vendor and partner assurance (98% of organizations have at least one breached third-party vendor), cyber insurance readiness (insurers use ratings for underwriting decisions), and board communication of security ROI.
- Cymulate’s dynamic approach to cybersecurity risk rating: Not all ratings are equal. Traditional external ratings can become stale snapshots; Cymulate goes further by continuously validating security controls against real threats. Security Posture Management tools from Cymulate move beyond static scores to deliver validated, actionable insights, reducing critical exposures by 52% through exploitability validation and boosting your cyber resilience over time.
What are cybersecurity risk ratings?
A cybersecurity risk rating is an objective, data-driven measurement of an organization’s security performance. In plain terms, it’s a score (numeric or letter grade) that indicates your overall cyber risk level at a glance.
Cybersecurity rating services aggregate various security signals, from exposed vulnerabilities to past breaches and boil them down into a single risk score or grade that anyone (even non-technical stakeholders) can understand. Think of it like a credit score for your organization’s cyber health.
These ratings are also called security ratings or cyber risk scores, and they serve as a common language between technical teams and business leadership.
A high rating (or an “A” grade) suggests strong security practices and lower risk, whereas a poor rating (say a “C” or below, or a low numerical score) flags significant vulnerabilities or gaps. The purpose of using standardized cybersecurity scoring levels is to provide a clear, consistent benchmark to evaluate and compare security postures across different companies.

Why accurate cybersecurity risk ratings matter
Cyber threats are no longer abstract IT problems, they carry real business consequences. Data breaches are growing in frequency and cost, putting pressure on organizations to quantify and manage cyber risk proactively. In 2023 alone, there were 3,205 publicly reported data compromises, a 78% increase over the prior year.
The global average cost of a breach reached $4.88 million in 2024, up 10% year-over-year. With such stakes, stakeholders from regulators to board members are demanding easy-to-understand benchmarks to gauge if their risk is under control.
Accurate cybersecurity risk ratings address this need by translating complex security telemetry into a digestible score. Here’s why these ratings have become so crucial:
- Bridge technical risk with business priorities: A well-calibrated rating ties cyber risk to business impact. It provides a common KPI that both IT teams and executives can monitor.
- Support compliance and regulatory mandates: Organizations face mounting compliance requirements (NIST CSF, ISO 27001, the EU’s DORA, SEC cybersecurity disclosures, etc.) that require demonstrating effective risk management. Risk ratings serve as evidence of a risk-based approach.
- Enable board and executive understanding in financial terms: Corporate boards increasingly recognize cyber risk as business risk, but they often struggle with technical jargon. A single cyber risk score (especially one that can be mapped to financial exposure) is immensely helpful for board reporting.
- Improve communication with external stakeholders: A common risk rating builds trust and transparency with partners, customers, cyber insurers, and other stakeholders.
- Provide benchmarks and accountability: Risk ratings offer a yardstick to measure improvement over time and against industry peers. They let you benchmark your security posture (e.g. “Are we above or below the industry average?”) and track progress. Over time, an improving rating can validate that security investments are paying off, which is powerful for justifying budgets and demonstrating ROI.
Benefits of using cyber risk ratings
Implementing cybersecurity ratings into your risk management program can yield numerous benefits. These ratings are more than just numbers, when used properly, they become tools for strategy and communication. Key benefits include:
- Objective measurement of security posture: Cyber risk ratings provide an objective, standardized score of your security performance, as opposed to subjective opinions or fragmented metrics. This objectivity helps cut through internal biases. For example, BitSight’s rating algorithm analyzes over 25 risk vectors from externally observed data to produce a daily score.
- Resource prioritization and risk-based focus: A good rating system highlights where your biggest risk exposures lie, so you can prioritize resources effectively. Rather than patching thousands of vulns arbitrarily, teams can focus on issues that significantly impact the score (and thus risk). This risk-based vulnerability management approach ensures limited budgets address the most dangerous gaps first. It’s been shown that organizations using continuous validation can reduce critical exposures by over 50% through focusing on exploitable weaknesses.
- Vendor and partner assurance: When onboarding new vendors or reviewing partners, cybersecurity ratings offer a quick check on their security maturity. Many companies now require a minimum security rating (e.g. no lower than “B”) for critical suppliers. This helps assure third-party security in the supply chain. It’s a necessary step, considering a staggering 98% of organizations have at least one third-party vendor that has suffered a breach.
- Cyber insurance readiness: Insurers are increasingly factoring security ratings into their underwriting process. A strong rating can not only help you get insured but potentially lower premiums, as it signals lower risk. Insurers use rating data for pricing policies and deciding coverage terms.
- Board-level communication and accountability: Cyber risk ratings distill technical security status into a simple metric that boards and executives readily understand. This dramatically improves communication upward. Security leaders can set target rating levels (aligned to the organization’s risk appetite in cybersecurity) and report on progress in each board meeting.
Core factors that influence risk ratings
It’s important to understand that cyber risk ratings aren’t arbitrary, they are derived from specific, measurable factors in your IT environment and practices. Rating providers each have proprietary formulas, but generally two broad categories of factors feed into your score:
1. Technical and exposure-based factors
These relate to the direct security signals and vulnerabilities visible in your IT footprint, especially externally. Key technical factors include:
- External attack surface: What do you have exposed to the internet? Unsecured or misconfigured assets can drag down your rating. A large attack surface with weak spots indicates higher breach likelihood. Ratings like SecurityScorecard explicitly check for things like insecure open ports and DNS health as part of their scoring criteria.
- Vulnerabilities and patching cadence: The prevalence and severity of known vulnerabilities in your systems heavily influence the score. Are you patching promptly, or do you have high-criticality CVEs left unaddressed for long periods? Many rating models incorporate patch management diligence.
- Compromised systems and malware: Evidence that your environment has been breached or infected, such as bots beaconing out, spam originating from your IPs or malware callbacks will significantly hurt your rating.
- Security controls and configurations: The presence (or absence) of fundamental security controls is another factor. This can include email security (SPF/DKIM records), web security (WAF deployment, SSL configurations), endpoint protection, intrusion detection systems, etc. If external scans show you lack basic protections or have misconfigurations (e.g. allowing weak SSL ciphers), your score may drop.
- Cloud security posture: As companies move to cloud infrastructure, ratings increasingly consider cloud-related exposures. Misconfigured cloud services (like open S3 buckets or publicly accessible databases) are common breach vectors and will negatively impact risk ratings. Cloud asset discovery and cloud safety posture checks (ensuring secure configurations) are part of modern rating methodologies.
2. Organizational and contextual factors
These factors go beyond just the raw technical findings to include the context of your security program and environment:
- Policy and process robustness: How strong are your security policies and practices? For example, do you have a regular patching cadence and vulnerability management process, or is it ad-hoc? Consistent, documented security processes can positively influence certain ratings (especially those that incorporate questionnaire data or internal assessments).
- Third-party and supply chain risk: Some rating systems consider the risk posed by your vendors or partners, effectively extending the evaluation beyond your own network. If one of your major third-parties has a poor security rating or known breaches, it may indirectly affect how risky you are perceived (since attackers could exploit weaker links in the chain).
- Incident history and breach records: A company that has suffered multiple recent breaches or data leaks will be rated riskier. Ratings firms often track public breach disclosures. Frequent incidents suggest systemic issues and will weigh down your score.
- Threat intelligence inputs: Advanced rating platforms incorporate threat intelligence to gauge if your organization (or industry) is being targeted by emerging threats. For example, monitoring hacker forums for chatter about your company or detecting targeted phishing campaigns against your domain could inform the risk level.
- Industry benchmarking and peer context: Some scoring methodologies adjust or compare your rating against industry averages. For instance, being a financial institution might inherently come with higher threat levels, so context is important. A score of 700 might be average in one sector but above-average in another. Ratings providers often provide industry-specific insights, and some (like FortifyData) adhere to principles to ensure fairness across industries.
Cybersecurity risk ratings synthesize technical exposure factors (the holes in your defenses) with organizational factors (how well you manage risk). A spike in any of these areas, say a slew of critical vulns, or a major breach will push your rating down (meaning higher risk).
How are cybersecurity risk ratings calculated?
Every cybersecurity rating provider has its own secret sauce for calculating scores, which is why the same organization can have different ratings across platforms. In general, though, these scores are calculated by aggregating the core factors discussed above, weighting them based on severity and then mapping the result to a standardized scale. The process typically looks like this:
- Data Collection: The rating service continuously collects data on the organization. This may include scanning external assets (websites, IP ranges, cloud instances), ingesting threat intelligence, monitoring breach databases, etc.
- Finding and Issue Analysis: The raw data is translated into findings e.g., “Detected outdated software version X” or “Employee email/password found in a credential dump.” Each finding typically maps to a category (vector) and is assigned a severity score. For instance, an exposed critical vulnerability might be scored as a high-severity issue in the “Application Security” category, whereas an expired certificate could be medium severity in “Network Security.”
- Scoring Algorithm & Weighting: The rating provider applies a proprietary algorithm to weigh and combine these findings into an overall score or grade. Certain factors may have a heavier weight if they statistically correlate more with breaches. (In fact, third-party validation has shown that some ratings strongly correlate with breach likelihood.) Providers also normalize scores to fit their scale.
- Continuous Updates: Unlike one-time assessments, leading rating platforms update scores frequently, some daily or in real-time. The dynamic nature of cyber risk means your score can change with any significant event: applying patches might raise your score, while a new critical CVE disclosure could lower it. Continuous monitoring ensures the rating reflects your current posture (though some providers only update when new scans or data is available). It’s important to know how frequently a vendor updates their data; stale data can lead to misleading scores.
Crucially, static external ratings can sometimes be misleading without validation. A rating might flag many vulnerabilities, making your score look bad, but perhaps most of those vulns aren’t actually exploitable due to compensating controls or are on isolated systems.
This is where a Cymulate takes a different approach: rather than scoring purely from outside observation, Cymulate performs active security validation (simulated attacks) to test what vulnerabilities are truly exploitable and how effective your controls are.
This validated, dynamic rating approach can provide more actionable insight than a passive scan-based score. In other words, a high static risk rating doesn’t guarantee you’re safe and a low rating might overstate risk if issues are theoretical. Blending external ratings with continuous validation is the best practice to get an accurate picture.
To illustrate how different vendors score organizations, here’s a comparison of some popular cybersecurity risk rating platforms and their scoring methodologies:
| Vendor | Scoring Scale | Data Sources Focus | Example Use Case |
| BitSight | Numeric 250–900 (credit-score style); currently achievable range ~300–820 (higher = better) | External internet-facing data only. Collects signals on 25+ risk vectors (botnets, open ports, patching, breaches, etc.); no internal data required. | Continuous third-party risk monitoring and benchmarking of security performance across industry peers. Often used by risk managers and underwriters for an outside-in view. |
| SecurityScorecard | Letter grades A–F (with an underlying score of 0–100 behind each grade) (A = best, F = worst) | External open-source intelligence and proprietary sensors across 10 factor categories (Network Security, DNS health, Patching Cadence, Endpoint security, IP reputation, Application security, etc.). Data refreshed continuously as new info is collected. | Third-party vendor assessments and supply chain risk management. Also used for cyber insurance assessments and as a KPI for communicating security posture to executives (easy A-F format). |
| Panorays | Numeric 0–100 Cyber Posture Rating (0 = highest risk, 100 = best) for external risk; plus separate letter grades for overall vendor risk factoring in questionnaires. | Combines external attack surface analysis with internal questionnaire responses and business context. Performs “hundreds of tests” non-intrusively on external assets; also considers human/social factors and policy evidence via its Smart Questionnaire. | Third-party cyber risk management with context. Ideal for supply chain risk where you need a more 360° view (external technical risk + internal controls of vendors). Used in vendor onboarding and ongoing monitoring, with ability to engage third-parties to improve. |
Table: Comparison of cybersecurity risk rating scales and approaches for BitSight, SecurityScorecard, and Panorays. Each vendor uses a different scoring methodology, numeric vs. letter grade, external vs. combined data, tailored to various use cases in cyber risk management.
As shown above, methodologies differ notably. BitSight and SecurityScorecard are purely outside-in, while Panorays blends outside-in with inside-out inputs. One vendor’s “B” grade might correspond to another vendor’s “750” score, making direct comparison tricky.
Buyers should be aware of these differences and choose a platform that aligns with their needs (e.g. broad external visibility vs. contextual depth). In any case, understanding how the score is calculated (factors, refresh frequency, data sources) is critical so you can trust and effectively use the rating.
How do rating methodologies differ?
When evaluating cybersecurity rating solutions, it’s important to recognize that not all ratings are created equal. Key differences in methodologies include:
| Vendor | Scoring Scale | Data Sources Focus | Example Use Case |
| BitSight | Numeric scale, 250–900 (higher = better) | Externally observable data (compromised systems, configurations, events) via public sources, AI-enhanced mapping, human curation | Continuous monitoring of external cyber hygiene for own organization or third-party vendors; alerting on changes and correlating scores with breach risk |
| SecurityScorecard | Numeric 0–100 with A–F letter grades overlay | External data: asset misconfiguration, DNS, patching, leaked info, endpoint, malware, etc.; uses machine learning, size normalization, statistical calibration | Daily scoring of external attack surface; fair benchmarking across company sizes; external third-party risk assessment |
| Panorays | Numeric 0–100 Cyber Posture Rating | External attack surface assessment (network, app, human/social layers) plus questionnaire inputs and context; AI-based asset discovery; non-intrusive probing | Third-party risk management: combines external posture with responses and business context for rapid vendor risk evaluation |
Key takeaways & buyer challenges
- No universal standard: Vendors differ widely in methodology, so a “B” from one provider is not equivalent to a “B” from another.
- Trade-offs between simplicity and nuance: Letter grades are digestible, but numeric scales capture subtle improvements.
- Transparency matters: Without visibility into inputs and validation, it’s difficult to justify scores to boards or regulators.
- Context is critical: A raw score without industry or geography adjustment can give misleading impressions.
Main challenge for buyers: comparing vendors is not an apples-to-apples exercise. Organizations often triangulate by:
- Using multiple rating providers.
- Mapping vendor scores into a common risk language (e.g., high/medium/low).
- Focusing on trends over time rather than absolute numbers.
The bottom line: when comparing cybersecurity risk rating platforms, recognize that a single “score” can be derived in very different ways. It’s wise not to rely on one rating alone. In fact, many organizations use multiple ratings, or pair an external rating with internal security posture management tools to get a comprehensive picture.
If you do compare vendors, translate their outputs to a common risk language (e.g., high/medium/low risk) rather than the raw numbers or letters, and focus on trends over absolute values.
How to measure cyber risk
When people ask “how to measure cyber risk,” they’re essentially looking to quantify two things: the likelihood of a cyber attack and the impact it would have. Measuring cyber risk means putting numbers (or at least structured ratings) around those uncertainties so that you can make informed decisions, much like measuring financial or operational risk.
Measuring cyber risk means quantifying how likely an organization is to face an attack and what the potential impact would be. In practice, cyber risk is often expressed as a combination of probability (chance of an incident in a given timeframe) and impact (the damage or loss if it occurs). One simple formula often used is:
Cyber Risk=Likelihood of ThreatImpact (Loss).
The challenge lies in determining those likelihoods and impacts with some rigor. Here’s a step-by-step approach to measure cyber risk effectively:
Step 1: Define scope and critical assets
Before crunching numbers, identify what you’re measuring risk to. Catalog your critical assets, systems, data, applications, business processes, that, if compromised, would have a significant impact.
Understand their value to the organization (financial value, sensitivity, role in operations). For example, a customer database with personal data or a critical manufacturing control system might be high on the list. Defining scope ensures your risk measurement focuses on what truly matters, rather than every trivial asset.
Step 2: Choose your measurement approach
There are several methodologies to quantify cyber risk, ranging from qualitative to quantitative. Common approaches include:
- Qualitative assessments: Using expert judgment and categories (e.g. high/medium/low risk) for likelihood and impact. Frameworks like risk matrices or heat maps fall here. While not numeric, they provide an ordered sense of risk severity. Qualitative methods are easier to start with but can be subjective.
- Quantitative models: These involve assigning numerical values to frequency and impact, sometimes using historical incident data or simulations. One example is Cyber Risk Quantification (CRQ) frameworks (like FAIR, Factor Analysis of Information Risk). CRQ uses models to estimate monetary loss distributions for different scenarios. It translates technical risk into financial terms.
- Security risk ratings: Using cybersecurity risk ratings (numeric scores or letter grades) from platforms as a measure of risk. Services like BitSight or SecurityScorecard provide an outside-in risk score based on your security posture data. These ratings effectively quantify aspects of likelihood, a lower score implies a higher probability of incident based on observed weaknesses.
- Validation-driven metrics: Incorporating validated assessment results, such as breach and attack simulation outcomes. For instance, running controlled attack simulations (with Cymulate) can reveal how your systems respond, did an attack succeed? How far could it go? This provides empirical data on which vulnerabilities are truly dangerous. Such validation can be turned into risk metrics.
Many organizations use a hybrid of these: e.g., qualitatively rank top risks, use ratings for continuous monitoring and quantitatively estimate financial impact for the worst scenarios.
Step 3: Collect data and metrics
Once your approach is set, gather the relevant data points that will feed your risk measurement. Key cyber risk metrics to collect include:
- Exploitability of vulnerabilities: Don’t just list vulnerabilities, gauge how many are exploitable and whether they’ve been tried in the wild. For example, using penetration testing or breach simulation results to identify which critical vulns could actually lead to compromise. Tracking the count of exploitable critical vulnerabilities gives a more risk-oriented view than total vulns.
- Mean Time to Detect (MTTD): How fast can your team detect a security incident or intrusion? This metric measures the average time between the start of an attack and when your security team becomes aware of it. Alongside it, Mean Time to Respond (MTTR) is crucial, how quickly you contain and remediate an incident after detection. Both MTTD and MTTR are core vulnerability management metrics and incident management KPIs that correlate with risk exposure.
- Security control effectiveness: Metrics on how well your defenses are performing. For example, what percentage of phishing test emails do users click (security awareness effectiveness)? What fraction of simulated attacks did your EDR (endpoint detection & response) stop? Cymulate, for instance, can produce an exposure score or control efficacy score by testing your controls against threats. If key controls like email filtering or IDS are only catching, say, 60% of attacks in simulations, that quantifiably increases risk.
- Third-party risk exposure: Data on your vendors’ security postures. How many of your critical suppliers have a high risk rating or recent breaches? If you use a cyber risk scorecard for vendors, track how many fall below your acceptable threshold. You might measure the percentage of vendors rated “high risk” and require mitigation plans for them. Given the near ubiquity of third-party breaches (98% orgs impacted), this metric is a big part of overall cyber risk.
- Incident frequency and loss data: Track how often security incidents (of various severities) are occurring within your environment and what impact (downtime, financial loss) they caused. If you have data on past incidents or near-misses, use it to statistically estimate frequency and impact.
- Business impact estimates: For each critical asset or scenario, work with business stakeholders to estimate the potential impact in financial or operational terms. This includes direct costs (e.g. revenue loss, remediation cost, regulatory fines) and indirect costs (reputation damage, customer churn). If measuring risk in the quantitative CRQ way, these impact values (often in dollars) are a key input. Even for qualitative measurement, labeling an asset “High impact” versus “Low impact” requires understanding what high impact means, which should be defined (e.g. High = more than \$1M loss or shutdown of critical operations).
Automation is helpful, many modern platforms provide dashboards that continuously update metrics like average patch time, number of critical findings, etc., feeding into an overall risk score or trend.
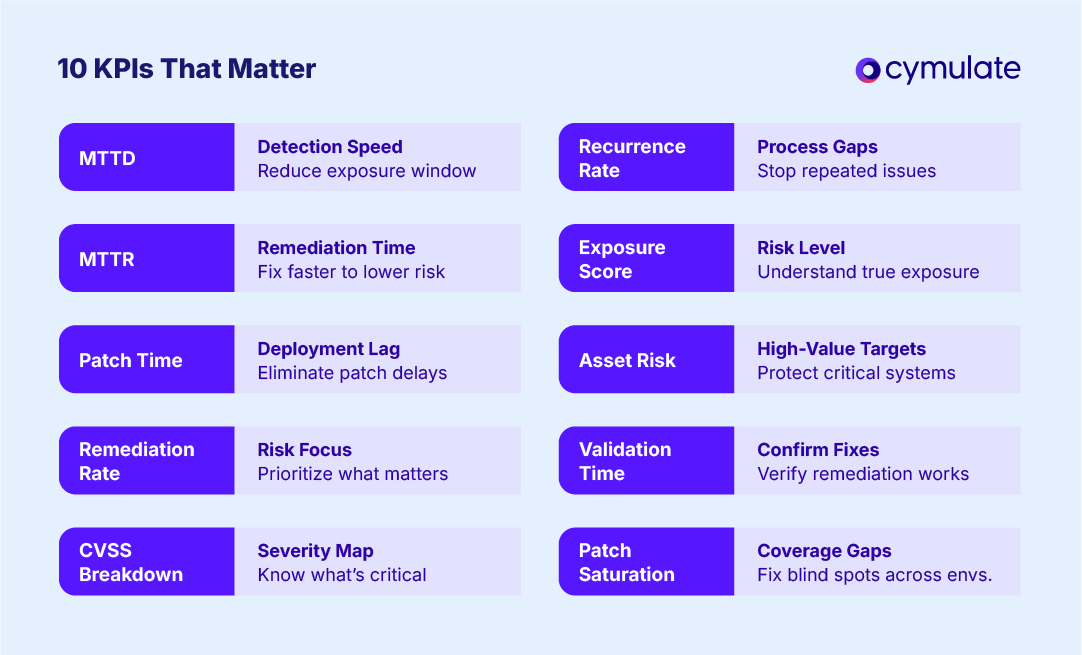
Example metrics for cyber risk measurement: “10 KPIs That Matter” such as MTTD (Mean Time to Detect) indicating detection speed, MTTR (Mean Time to Remediate) indicating response time, Exposure Score to understand true risk level, Validation Time to confirm fixes and others. Tracking these vulnerability management metrics helps quantify and reduce cyber risk over time.
Step 4: Calculate and interpret risk
With data in hand, you can calculate your cyber risk and derive insights:
- Quantify likelihood and impact: If following a model like FAIR or using ratings, you might calculate an annualized likelihood (e.g. “20% chance of a major breach this year”) and an impact (e.g. “\$5 million loss”). Multiply for an expected risk value (e.g. \$1M annual risk). Or, if using ratings, map your rating to a likelihood band (for instance, an “A” rating might correspond to <5% annual breach probability based on historical correlations). The key is to turn raw metrics into a risk estimate or level that is understandable.
- Create a risk heat map or scorecard: Many organizations present cyber risks in a heat map: likelihood on one axis, impact on another, with risks plotted (high-high being the critical ones). Alternatively, use a risk scorecard approach: list top risks (e.g. “Ransomware attack on ERP system”) with their likelihood, impact, and a composite risk rating. The measurements from previous steps feed into these.
- Compare against benchmarks and thresholds: Interpret your results by comparing to industry data or your own risk appetite. For example, if the average security rating in your industry is 750 and you’re at 600, that’s a concern to address.
- Derive actionable insights: The ultimate point of measuring risk is to know where to act. If your risk quantification shows “Credential theft leading to data breach” is a top risk scenario, you might invest in stronger authentication and monitoring. If a particular third-party poses outsized risk, you might audit or replace them. Risk measurement should highlight these priorities. Furthermore, track the metric trends: is your MTTD improving after a new detection tool? Is your overall risk score decreasing after a major patch effort? Use those insights to adjust strategy and demonstrate progress.
You move from vague fear of cyber threats to a structured risk picture with these steps. It allows you to answer questions like “How much cyber risk do we have and where?” and “Are our risk levels improving or worsening?” which is incredibly valuable for decision-makers.
Regularly refresh your measurements (many organizations do this quarterly or even continuously with automated security ratings and exposure management tools). This keeps your risk quantification current, so you can proactively manage cyber risk rather than reactively responding after incidents.
What are the common use cases for security risk ratings?
Cybersecurity risk ratings have a variety of practical use cases across enterprise security and risk management. Some of the most common scenarios where security ratings add value include:
- Third-Party Risk Management (TPRM): Ratings help evaluate vendors before onboarding and enable continuous monitoring of supplier security health to manage supply chain risk at scale.
- Continuous Security Performance Monitoring: Organizations track their own ratings over time to measure posture, verify improvements, and maintain a real-time view of cyber health.
- Board Reporting and Cyber Risk KPI: Ratings serve as simple, business-friendly KPIs for executives and boards, supporting peer benchmarking and demonstrating program effectiveness.
- Mergers & Acquisitions (M&A) Due Diligence: Acquirers use ratings to quickly assess target companies’ security maturity, spot red flags, and prioritize post-merger remediation.
- Cyber Insurance Underwriting: Insurers rely on ratings to price policies and evaluate applicants’ risk, while organizations use strong ratings to secure better terms or lower premiums.
- Regulatory and Compliance Oversight: Regulators and firms use ratings to show adherence to frameworks and continuous monitoring requirements (e.g., NIST, NYDFS, EU directives).
- Benchmarking and Peer Comparison: Ratings provide standardized comparisons against industry peers, helping organizations gauge relative performance and showcase trustworthiness.
- Prioritizing and Tracking Security Improvements: Sub-scores highlight weak areas (e.g., patching, DNS), guiding remediation and validating progress through measurable rating changes.
Nonetheless, the convenience and communicative power of a single score make cybersecurity ratings a versatile tool in the risk management toolbox, from third-party risk management to internal security performance monitoring and beyond.
Challenges with traditional risk ratings
While cyber risk ratings are useful, the traditional implementations of these ratings come with limitations and challenges. Understanding these shortcomings can help you avoid pitfalls and choose a more effective approach. Key challenges include:
- One-time snapshots become outdated: Ratings based on static scans quickly lose relevance in dynamic environments. Continuous monitoring is needed.
- External-only visibility: Outside-in scans miss internal controls, human factors and compensating measures, giving an incomplete risk picture.
- Exploitability not validated: Scores often count theoretical vulnerabilities equally, regardless of whether they’re actually exploitable or mitigated.
- Lack of business context: Ratings don’t reflect criticality of assets, industry-specific risks or organizational priorities, making them a blunt tool.
- False positives & misattribution: Errors in data mapping or outdated findings can unfairly lower scores, requiring disputes and corrections.
- Gaming & variability: Organizations may chase higher scores instead of real security. Different providers weigh factors differently, creating inconsistent results.
These challenges don’t mean that risk ratings are not valuable, rather, they highlight that traditional cyber risk management using ratings alone can fall short. The solution is to use ratings wisely: as one input among many, and ideally combine static ratings with more continuous, validated assessment (like breach simulations, red teaming, etc.) to get a true sense of security posture.
This is precisely why the industry is moving toward Continuous Threat Exposure Management (CTEM) and extended security posture management, which leverage ratings but also test and verify security in real time.
Beware of treating a cybersecurity rating as a silver bullet. Use it as a tool, not an absolute truth. Keep it up-to-date, supplement it with internal knowledge and remain aware of its blind spots. By doing so, you can gain the benefits of ratings while mitigating their inherent limitations.
How to improve security posture using ratings
If you have a cyber risk rating in place (or plan to get one), the real question becomes: How do you use that rating to actually improve your security posture? A rating by itself doesn’t fix anything, it’s how you respond to it that matters. Here are practical ways to leverage risk ratings for tangible security improvements:
- Continuous monitoring & remediation: Treat ratings as living metrics. Set alerts for score changes and act quickly on critical issues to strengthen posture over time.
- Prioritize vulnerabilities & controls: Use factor-level scores (e.g., patching, application security) to direct resources toward the weakest areas, making improvements data-driven.
- Track progress & set goals: Turn ratings into measurable objectives (e.g., improve from 720 to 800). Use them to motivate teams and demonstrate accountability to leadership.
- Leverage reports for ROI & budget optimization: Show score improvements after security investments, benchmark against peers and use reports to justify further funding.
- Integrate into governance: Include ratings in risk dashboards and set thresholds that trigger management reviews or board notifications if ratings fall below target.
- Combine with other security tools: Align ratings with internal risk registers, red team findings and other assessments for a holistic view of risk.
Security posture improvement via ratings is about closing the loop: Measure, identify gaps, fix them and then measure again to confirm improvement. It’s a continuous cycle.
Ratings give you a quantifiable target and immediate feedback on changes, which can greatly enhance a traditional security program that might otherwise lack clear metrics of success.
How to choose a cybersecurity risk rating platform
If you’re considering adopting a cybersecurity risk rating solution, it’s important to choose one that fits your organization’s needs and provides reliable value. Here are key factors and practical tips for selecting the right cybersecurity risk rating platform:
- Data breadth & depth: Check if the platform only scans external-facing data or also incorporates internal assessments. Broad external datasets (e.g., BitSight, SecurityScorecard) suit third-party risk, while deeper validation (e.g., Cymulate) fits internal posture. Ensure coverage includes cloud, IoT and modern assets.
- Accuracy & validation: Look for independent studies, third-party validations and customer references that prove ratings correlate with real risk (e.g., breach likelihood). Ask how the vendor minimizes false positives and whether analysts curate data.
- Transparency & reporting: The platform should let you drill into score components, view detailed issue descriptions and generate reports tailored to executives, boards or technical teams. Clear remediation guidance is key.
- Update frequency & alerts: Continuous monitoring requires daily or real-time updates plus alerts when scores drop or new issues emerge. Avoid platforms that refresh monthly without notifications.
- Historical data & trends: Access to long-term (12+ months) historical ratings helps track patterns and prove improvements. Graphical trend analysis makes it easier to spot recurring issues or seasonal fluctuations.
- Customization & context: Some platforms let you adjust factor weightings, tag critical assets or segment subsidiaries. Tailoring ratings to your environment adds relevance.
- Integration with workflows: Ensure compatibility with GRC, ticketing (e.g., Jira, ServiceNow), or vendor risk systems. Integration enables automated follow-ups (e.g., questionnaires when vendor scores drop).
- Independent reviews & feedback: Use Gartner, G2, or peer insights to gauge usability, support and data freshness. Strong vendor support is crucial for resolving disputes or clarifying findings.
- Cost & licensing model: Pricing varies - by number of monitored vendors, company size, or access tiers. Align spend with expected ROI: higher costs may be justified if risk reduction and efficiency gains are clear.
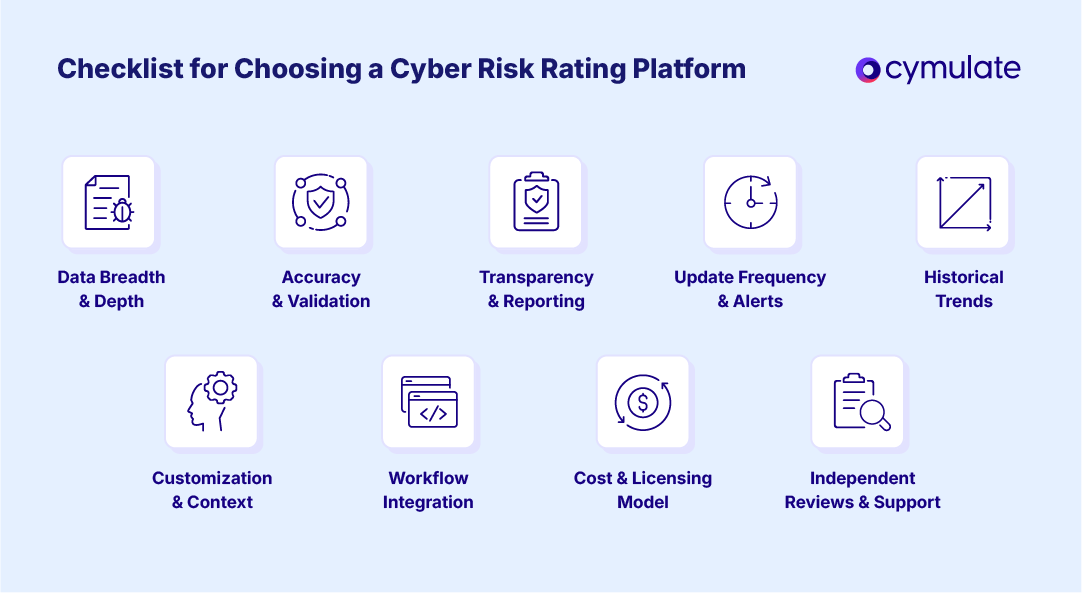
Make a checklist of these factors and evaluate each platform against it. It can also be helpful to run a proof-of-concept: get a trial, see how many issues it finds and gauge if those findings are things you didn’t know (value-add) or just duplicating existing scanners. See if the score reacts when you fix something, that feedback loop is crucial.
Remember, the best platform for you depends on your specific objectives: Is it to manage third-party risk broadly? To continuously validate your own security? To communicate with the board? Some platforms specialize more in one area than others.
Cymulate, for example, shines in validated, continuous testing (dynamic ratings in context), whereas a platform like BitSight excels in breadth of external monitoring. Some organizations even use multiple tools, one for vendor risk, one for internal validation.
Consider the future: As your program matures, you may want a platform that goes beyond just a rating, perhaps offering modules for security posture management solution capabilities like attack simulation, exposure analysis or risk quantification. Choosing a provider that’s innovating and expanding (versus a stagnant one) can ensure your investment grows with you.
Best practices for using cybersecurity ratings
Once you have cybersecurity ratings in place, following best practices will ensure you get the most value out of them while avoiding missteps. Here are some actionable best practices:
1. Integrate into governance
Don’t treat ratings as an isolated metric. Place them in the same context as financial and operational risks by adding them to enterprise dashboards and regular risk reports.
Assign clear ownership, whether a CISO, risk officer or dedicated team so someone is accountable for monitoring changes, coordinating responses, and ensuring that remediation tasks are followed through. This elevates the score from a novelty to a board-level risk indicator.
2. Set thresholds tied to risk appetite
Define upfront what “acceptable” vs. “unacceptable” looks like for your organization. For example, a target score of 750/900 might be labeled Low Risk, while anything below 700 could trigger immediate escalation and CIO oversight.
Extend the same logic to vendors: require critical suppliers to maintain at least a “B” grade, with corrective action plans required if they fall lower. By setting these thresholds, ratings become actionable triggers, not just reference numbers.
3. Monitor continuously & validate data
Establish a process where security teams check dashboards, alerts and factor-level scores regularly, daily or weekly depending on risk appetite. Assign responsibility for verifying accuracy, correcting false positives and requesting rescans where necessary.
This ensures that outdated or misattributed assets don’t harm your score unfairly and that true risks are addressed quickly. Proactive monitoring keeps the rating a live indicator rather than a stale snapshot.
4. Supplement, don’t replace, security reviews
Ratings are valuable but incomplete. They flag external-facing risks but miss internal issues, misconfigurations or human factors.
Use them as conversation starters with vendors or internal teams. For example, a poor vendor rating could trigger an audit rather than automatic disqualification.
A strong internal rating shouldn’t replace penetration tests, compliance audits, or red-team exercises. Think of ratings as a first line of insight, not the final word.
5. Collaborate & share insights
Distribute rating results to different stakeholders to build awareness and drive collaboration. IT and security teams can act on technical issues; developers can address application security weaknesses; procurement and legal can embed security clauses into vendor contracts.
Sharing positive improvements (e.g., moving from a C to a B) also helps reinforce security culture, rewarding teams for progress and keeping morale high.
6. Leverage automation & integration
Connect ratings to the tools you already use. For example, integrate with a GRC platform so a drop in score creates a new risk record. Use ticketing systems like Jira or ServiceNow to auto-generate remediation tasks when new vulnerabilities are detected.
In third-party risk management, automate workflows so vendors with falling scores automatically receive security questionnaires or alerts. These integrations reduce manual effort, speed response and scale oversight across hundreds or thousands of entities.
7. Review multiple providers
Different rating vendors use different data sources and algorithms, which can lead to varied results. Periodically compare what at least two providers say about your organization or vendors. If both flag the same weakness, it validates the finding.
If only one does, it might be a false positive, or a blind spot in the other system. Keep an eye on industry updates as well, since providers regularly refine scoring methodologies (e.g., adjusting weightings for new threats). Understanding these changes ensures you aren’t caught off guard if your score shifts unexpectedly.
The ratings will serve as a dynamic tool that informs decision-making at all levels, from IT ops to the boardroom, rather than a checkbox or vanity metric. The goal is to use the rating to drive real improvements and maintain vigilance, thereby continuously bolstering your security posture and lowering your risk of a cyber incident.
Boost your organization’s cyber risk rating with Cymulate
Cybersecurity risk ratings help translate technical risks into business-friendly metrics, but they often remain static snapshots that don’t reflect whether defenses can withstand real-world threats. This is where Cymulate elevates the approach, moving beyond a simple score to continuous, validated, and actionable insights.
From static scores to validated security
Traditional ratings may tell you your score but not whether your systems would resist an actual breach attempt.
Cymulate Exposure Management continuously tests your environment against real-world attack scenarios, identifying exploitable vulnerabilities and verifying whether your detection and response tools work as intended. This ensures that your rating reflects proven security outcomes, not just external assumptions.
Validate, remediate, elevate
Cymulate can simulate complete attack paths across email, endpoint and lateral movement defenses. When weaknesses are uncovered, it provides direct remediation guidance.
Acting on these findings reduces real-world risk and naturally improves the external factors that feed into most cyber risk ratings. The process is simple: validate your defenses, remediate gaps and elevate both your security posture and your rating.
Dynamic internal risk scoring
Beyond third-party scores, Cymulate delivers its own dynamic internal risk scoring that updates continuously as you strengthen defenses.
These scores range from high-risk (red) to low-risk (green) and are tied directly to successful or blocked attack simulations. This allows security leaders to communicate with confidence: “Our score improved because we validated controls against threats and closed specific vulnerabilities.”
Adding context that ratings miss
Cymulate links findings to MITRE ATT&CK tactics and maps them to business impact. This helps organizations prioritize fixes that matter most rather than chasing generic score improvements. It’s a more contextual and actionable view that still contributes to raising external ratings.
Addressing traditional rating limitations
With Cymulate, organizations overcome the common challenges of ratings by gaining:
- Continuous updates with on-demand assessments.
- Fewer false positives, since only exploitable issues count.
- Contextual insights that connect vulnerabilities to real business risk.
- Improved external ratings as validated fixes address weaknesses those ratings measure.
Request a demo now to see how Cymulate helps you measure, validate and improve your cybersecurity risk rating.
FAQs
It’s the level of cyber risk an organization is willing to tolerate. Leadership sets thresholds (e.g., acceptable rating ranges), which trigger action if breached.
Vendor cybersecurity ratings are security scores for third parties (suppliers, partners, providers) based on external data. They help in third-party risk management (TPRM) by screening new vendors and monitoring existing ones.
Exposure management is a broad strategy that encompasses identifying, assessing, prioritizing and mitigating security exposures across an organization. Exposure validation is a key component within that strategy, focusing specifically on confirming whether detected exposures are exploitable and if defenses effectively respond to them.
While exposure management is ongoing and strategic, exposure validation is tactical and evidence-based, providing the actionable insight needed to support informed risk decisions.
The concept emerged in the early 2010s, led by BitSight (2011) and SecurityScorecard (2013). Initially based only on external scans, ratings evolved into more integrated platforms (e.g., Panorays, FortifyData) and are now a recognized Gartner category.
They make cyber risk quantifiable for boards and executives, guide security team priorities, lower due diligence costs, support insurance underwriting and serve as trust signals to customers.
A “good” cybersecurity risk rating means low risk:
- Letter scale (A–F): A or B is good.
- Numeric (e.g., BitSight 300–900): 740+ is strong; 800+ is excellent.
- Industry benchmarks vary, but top quartile performance is generally the goal.
Investigate the factors, dispute inaccuracies with evidence, and request corrections from the provider. Simultaneously fix any valid issues. Continuous monitoring prevents surprises.
Yes. Ratings are central to TPRM:
- Screen vendors during onboarding.
- Set minimum thresholds (e.g., critical vendors must maintain a B grade).
Monitor continuously and require corrective action if scores fall.
Ratings complement, but don’t replace, audits and questionnaires.
Track your own score as a KPI. Break it down by category (patching, app security, etc.) and assign ownership. Use it to measure progress, gamify improvements across teams, and present simplified trends to leadership.