The Pyramid of Pain in Cybersecurity Threat Analysis
Understanding the Pyramid of Pain and how to outsmart threat actors
With organizations facing more cyber threats today than ever before, in addition to having mass attack surfaces, companies must find ways to stay ahead, stay vigilant and stay secure. One way of tackling that is by understanding the Pyramid of Pain. Security expert, David Bianco developed this concept in 2013, that illustrates how different types of indicators of compromise (IoCs) could potentially impact an organization’s threat detection and mitigation.
Key Highlights
- The Pyramid of Pain is a cybersecurity framework by David Bianco that shows how different types of indicators of compromise (IoCs) impact the difficulty of detecting and disrupting threat actors.
- Each layer of the pyramid, from hash values and IP addresses to tactics, techniques, and procedures (TTPs), represents a different level of challenge for attackers, with higher levels causing greater disruption when defenders respond effectively.
- Applying the Pyramid helps security teams prioritize detection and response, focusing efforts where they most hinder adversaries and improve organizational resilience.
- Continuous validation through red teaming, simulations, and integrated monitoring ensures defenses remain adaptive against evolving threats.
- Cymulate’s Exposure Management and Breach & Attack Simulation (BAS) platform empowers organizations to operationalize the Pyramid of Pain, continuously testing and optimizing defenses to outsmart threat actors and stay ahead of emerging risks.
The 6 levels of indicators in the Pyramid of Pain
There are six levels of IoCs defined within the Pyramid of Pain that are from the bottom to the top, the least painful to the most painful. In this instance, “painful” is defined by how challenging or difficult it would be for an attacker to take these levels on.
At the base of the pyramid are simple indicators like hash values and IP addresses, which attackers can easily change. As you move up, it gets harder for them to alter domain names, network and host artifacts, tools, and finally their tactics, techniques, and procedures (TTPs).
By integrating the Pyramid of Pain into threat mitigation strategies, security teams can improve early detection, response capabilities, and overall cybersecurity resilience.
The six levels of IoCs are:
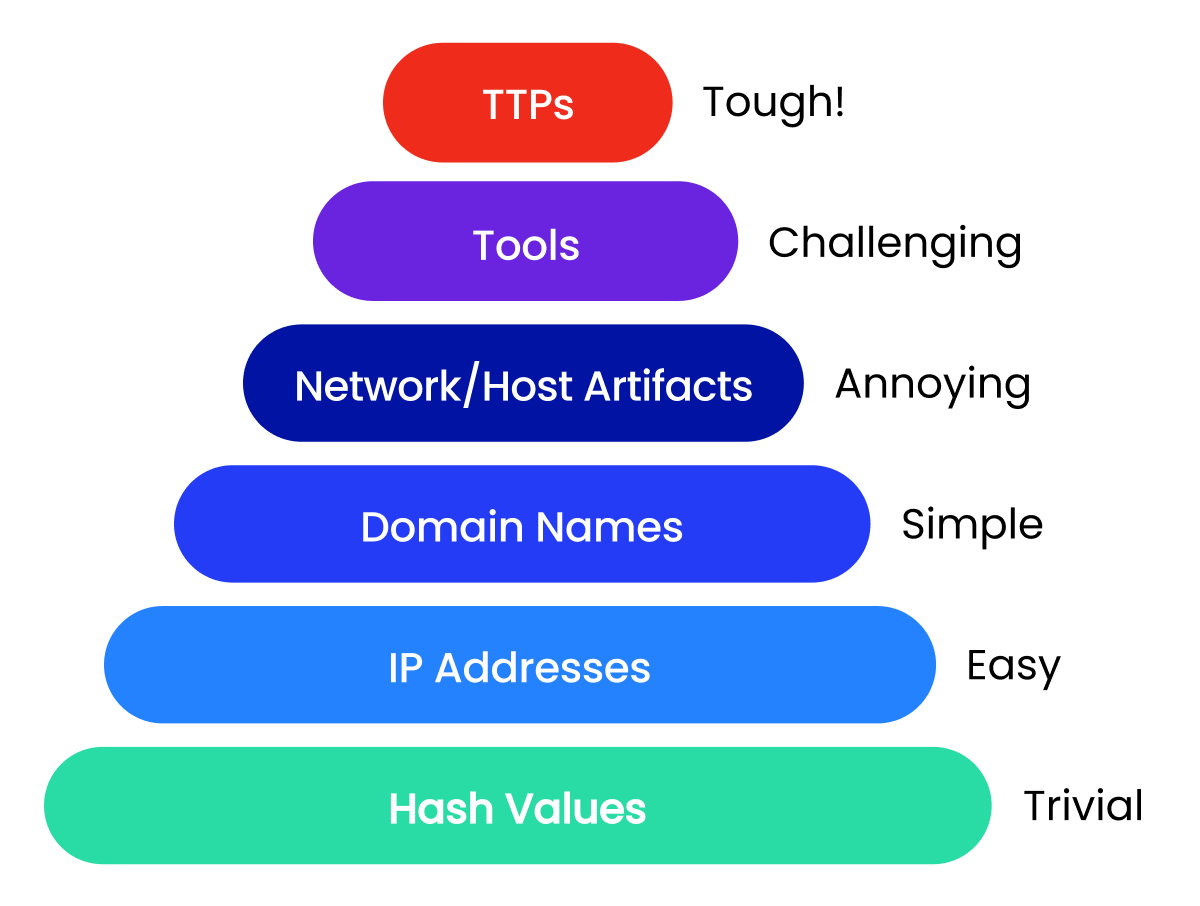
1. Hash Values
At the base of the pyramid, and therefore one of the easier and more vulnerable targets to a threat actor, are a type of software or file “signature” digital fingerprint. Hash values are the output of a complex cryptographic hash function, such as, SHA-a and MD5; between these two functions, they can nearly guarantee that two different files will not have the same hash value.
2. IP Addresses
The next level up from the bottom is Internet Protocol (IP) Addresses, which uniquely identify a computer, or any other device connected to the internet. Blocking IP addresses can help be a preventative measure, however, they remain an easy target for threat actors to break through and change, making them less effective long-term.
3. Domain Names
In the middle of the pyramid, Domain Names offer more intricacies, with its ability to block malicious domains can be much more effective than blocking IP addresses. Yet, attackers can still have the upper hand here with the ease of registering different domains or using domain generation algorithms (DGAs).
4. Network/Host Artifacts
In the upper portion of the pyramid, threat actors should have a more challenging time against Network/Host Artifacts. Every byte that goes through a network as a result of an adversary’s interaction could be an artifact, and those pieces can be distinguished as signs of malicious activity, catching an attacker much earlier in their endeavor and with greater disruptions. Network artifacts are produced as the result of some network activity or interference, where as host artifacts are produced from activity on a host machine.
5. Tools
With a variety of tools in place, threat actors often have various software tools and platforms at their disposal to carry out their targets, such as, backdoors and password crackers. This would allow them to move laterally, extract data and exploit organizational vulnerabilities. However, this would require the attacker to have replace or develop new tools that can beat the secure organization, making it a costly and time-consuming mission.
6. Tactics, Techniques and Procedures (TTPs)
At the top of the pyramid, the most difficult point of entry for a threat actor sits the tactics, techniques and procedures (TTPs). The TTPs are critical in understanding and defending against the slyest attacker, involving recognizing the methods and strategies used by them, not just the specific tools or indicators. This is the most effective long-term approach, as it addresses the underlying methods used in attacks, rather than pieces of signatures or artifacts.
Using the Pyramid to outsmart an attacker
Implementing the Pyramid of Pain into cybersecurity strategies is crucial for enhancing threat detection, incident response, and overall defense capabilities. This approach focuses on targeting areas that significantly disrupt adversaries, thereby strengthening defenses against complex cyber attacks. The indicators are only one form of threat detection in cybersecurity.
Staying on top of an organization’s behavioral threat analysis, signature-based detection, heuristic-based detection, machine learning and AI-based detections can be the difference between a reputational and data breach nightmare and a good nights’ sleep.
Keeping an eye on where things fall within this pyramid framework allows the cybersecurity teams to focus their efforts more effectively against potential dangers in their environment.
Ways to use the Pyramid to Validate your Security Controls
The Pyramid of Pain is an effective framework for validating your security controls by assessing how well they detect and respond to various threats:
File Hashes (Bottom Layer)
Validation: Test if your security system can detect and block known malicious file hashes.
Challenge: Since attackers can easily change the hash by altering the file, ensure your system is updated with the latest threat intelligence feeds.
IP Addresses and Domain Names
Validation: Implement IP and domain blacklists to see if your system can block communications with known malicious servers.
Challenge: Attackers frequently change IP addresses and domains. Validate if your system can quickly update and respond to these changes.
Network/Host Artifacts
Validation: Check if your security controls can identify patterns in network traffic or host configurations indicative of malicious activity.
Challenge: This requires more sophisticated detection mechanisms. Conduct regular penetration tests and simulations to ensure your controls can identify these artifacts.
Tools
Validation: Detect and block the use of specific malicious tools and utilities commonly used by attackers.
Challenge: Attackers can switch tools or modify existing ones. Ensure your controls can adapt and detect new or altered tools.
Tactics, Techniques, and Procedures (TTPs)
Validation: Assess if your security measures can identify and disrupt the specific methods attackers use, such as, phishing attempts or lateral movement within a network.
Challenge: This involves behavioral analysis and requires a deep understanding of attacker methodologies. Regularly update your detection rules and conduct threat hunting exercises to refine your capabilities.
Practice makes a better prepared organization
- Conduct Red Team Exercises: Simulate attacks that use various IoCs across all layers of the Pyramid of Pain. Evaluate how well your security controls detect and respond to each type of indicator.
- Regular Updates: Ensure your threat intelligence feeds, detection rules, and response strategies are regularly updated to address new and evolving threats.
- Continuous Monitoring: Implement continuous monitoring and logging to detect anomalies and potential indicators of compromise in real-time.
- Integration of Security Tools: Use a combination of security tools that cover different layers of the pyramid. For example, antivirus software for file hashes, intrusion detection systems for network artifacts, and behavioral analytics for TTPs.
- Training and Awareness: Train your security team to recognize and respond to indicators at all levels of the pyramid. Awareness and education can significantly improve your overall security posture.


