Risk Exposure
The cybersecurity landscape is in a constant state of flux. New threats emerge daily, targeting vulnerabilities in your IT infrastructure and those of your vendors and partners. As a cybersecurity leader, you can mitigate these risks by adopting a proactive approach to cyber risk exposure management.
What is Cyber Risk Exposure?
Cyber risk exposure is the sum of the vulnerabilities and risks associated with your organization’s digital footprint, including on-premises and cloud systems, applications, data, networks, and remote devices. It represents the potential for loss or damage resulting from cyber threats (including data breaches, system failures, and ransomware attacks).
If you understand your cyber risk exposure, you can:
- Prioritize security efforts: Identify the most critical vulnerabilities and allocate resources accordingly.
- Make informed decisions: Evaluate the potential impact of different security measures and choose the most effective ones.
- Comply with regulations: Adhere to industry standards and government regulations, such as GDPR and HIPAA.
- Protect brand reputation: Mitigate the risk of negative publicity and customer loss.
Different Types of Cyber Risk
Cyber risks come in many forms, each posing unique threats to business operations, finances, compliance, and reputation. Understanding these risks is essential for strengthening cybersecurity defenses and ensuring long-term resilience.
Operational risk
Cyber attacks directly threaten business operations, causing system outages, data corruption, or complete shutdowns. When critical systems fail, production stops, customer service breaks down, and revenue drops.
Ransomware presents one of the most severe operational threats, as attackers encrypt essential files and systems, forcing businesses to choose between paying hefty ransoms or rebuilding from backups.
Supply chain attacks, like the 2019 SolarWinds attack, can also cause widespread operational disruption. Here, hackers infiltrated SolarWinds, a widely used network management software provider, and inserted malicious code into software updates distributed to over 30,000 organizations. This code granted attackers remote access, enabling them to steal data, disrupt operations, and launch further attacks.
Financial risk
Security incidents inflict both immediate and long-term financial damage. Companies face substantial costs for incident response, forensics, and system recovery. Legal settlements and regulatory fines often follow.
However, the secondary costs typically exceed initial damages through lost revenue during outages, decreased productivity, and higher insurance premiums. And it's worth noting cyber insurance premiums have skyrocketed in recent years, making it increasingly difficult for organizations to afford coverage. In 2021 and 2022, premiums surged significantly, with rates doubling in some cases. While premiums have stabilized somewhat, they remain at record highs.
Compliance risk
Modern privacy laws and industry regulations demand robust data security. Failure to protect sensitive data can lead to costly investigations, fines, and mandated security overhauls. Regulations like GDPR and CCPA impose strict data handling requirements, while industry standards add complexity. Organizations must demonstrate compliance by documenting security practices and conducting regular audits or reap the consequences.
Reputational risk
Security failures can shatter stakeholder trust overnight. When customer data is exposed, the resulting media coverage and public backlash often trigger immediate customer losses and declining sales. Even minor breaches can damage carefully built brand reputations, while major incidents can forever tarnish a company's image. The cost of rebuilding trust through improved security, customer outreach and brand rehabilitation often exceeds the direct costs of the breach itself.
How to Analyze and Measure Your Risk Exposure
Understanding your organization's cyber risk requires a systematic approach. This involves combining quantitative metrics and qualitative assessments to create a comprehensive risk picture. Let's break this down.
Risk assessment fundamentals
Start by identifying critical assets and their potential vulnerabilities. Map out how these assets connect to core business operations and what threats could compromise them. For example, customer databases face risks from SQL injection attacks or unauthorized access, while payment processing systems are vulnerable to man-in-the-middle attacks and fraudulent transactions.
This inventory becomes the foundation for measuring exposure. Consider both obvious assets like customer databases and less apparent ones like vendor relationships or intellectual property.
Measuring probability and impact
Each identified risk needs two key measurements: likelihood of occurrence and potential impact. Calculate probability by analyzing threat intelligence, historical incidents, and industry patterns. Measure impact across multiple dimensions - financial losses, operational disruption and reputational damage. For example, a ransomware attack might have a medium probability but catastrophic impact, while a minor data leak could be highly probable but have limited consequences.
Tools and Technologies
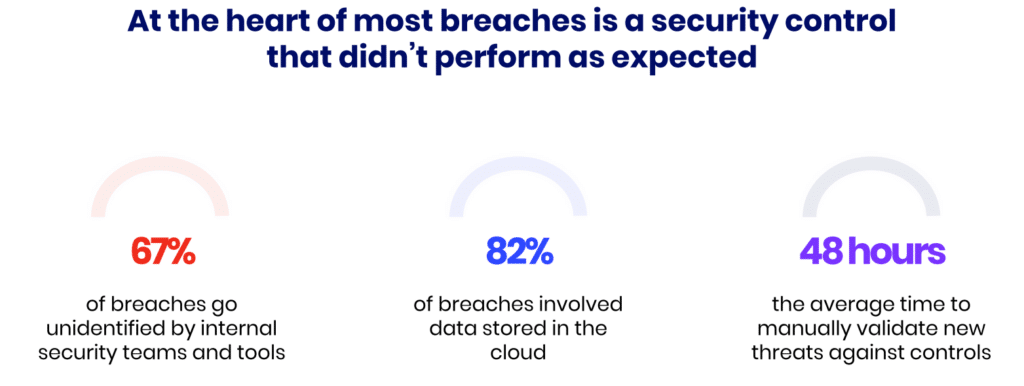
Modern risk assessment platforms automate much of the risk exposure analysis. These tools continuously scan for vulnerabilities, measure security control effectiveness, and track risk metrics in real-time. However, it's essential to regularly validate that these tools and security controls are performing as expected to ensure comprehensive protection against evolving threats.
The tools and technologies you use, along with the policies you create, should align with cybersecurity frameworks like NIST or ISO 27001. These frameworks provide a structured approach to managing cybersecurity risks, covering areas such as asset management, access control, incident response, and business continuity. This ensures that your security measures are comprehensive, effective, and compliant with relevant regulations.
Calculating total exposure
Combine probability and impact measurements to quantify total risk exposure. This helps prioritize security investments and justify budgets. Track trends over time to identify emerging risks and measure your program's effectiveness. Regular reassessment is essential as both threats and business needs evolve.
Lastly, integrating risk exposure analysis into your business strategy is crucial. This ensures that security measures are aligned with business goals and that resources are allocated effectively. Remember that risk measurement isn't a one-time exercise - it requires ongoing attention and adjustment as your organization grows and changes.
Threats That Increase Risk
External threats
External threats, such as advanced persistent threats (APTs), emerging cyberattacks, and geopolitical tensions, are constantly evolving. These threats, often launched by nation-state actors, cybercriminals and hacktivists, leverage sophisticated techniques to compromise systems and steal sensitive data.
Internal threats
Internal threats often arise from within an organization, both intentionally and unintentionally. Human error, such as accidental data leaks or weak password practices, can lead to significant security breaches. Additionally, malicious insiders, like disgruntled employees or compromised accounts, can pose serious risks. Misconfigured systems and outdated technology also create vulnerabilities that can be exploited by attackers.
Industry-specific threats
Industries like healthcare, finance, and government handle sensitive data, making them prime targets for cyberattacks. These industries must comply with strict regulations and protect critical information. Strong security measures, including data encryption and regular audits, are essential to safeguard sensitive data and maintain compliance.
Decreasing Your Risk Factor
While the evolving cyber risk landscape presents significant challenges to any cybersecurity team, strategic action can significantly strengthen your defense.
- Proactive measures: Continuously scanning systems for vulnerabilities and conducting regular penetration testing helps identify and address weaknesses before they can be exploited by attackers. This proactive approach ensures that potential security gaps are identified and patched promptly.
- Employee training: Regular employee security awareness training empowers employees to recognize and avoid phishing attacks and social engineering tactics. By educating employees about best practices, organizations can reduce human error-related breaches.
- Security hygiene: Maintaining strong security hygiene is essential for protecting sensitive information. This includes keeping software and systems up-to-date with the latest security patches, encrypting data both at rest and in transit, and implementing robust access controls to limit unauthorized access to critical systems and data.
- Incident response: A well-defined incident response plan is crucial for minimizing the impact of a cyberattack. This plan should outline steps for incident detection, containment, eradication, recovery, and lessons learned. By having a proactive plan, organizations can quickly respond to incidents, limit damage and restore normal operations.
Building a Strong, Proactive Cybersecurity Strategy
A robust cybersecurity strategy is the backbone of effective defense—more than just deploying the right tools, it requires a structured, proactive approach to risk management.
- Frameworks and standards: Adopting frameworks like the NIST Cybersecurity Framework provides a structured approach to managing cybersecurity risk. By aligning with industry-recognized standards, organizations can establish a strong foundation for their security programs.
- Automation and continuous monitoring: Automation tools, like Cymulate, enable continuous validation of security controls. Automating routine tasks and monitoring systems for anomalies helps proactively identify and address potential vulnerabilities.
- Zero trust approach: A zero-trust security model limits access to systems and data, even for authorized users. By assuming a potential breach, organizations can implement stringent access controls and continuous authentication to minimize the impact of attacks.
How Cymulate Can Help Reduce Risk Expsoure
The Cymulate exposure management platform provides data-driven insights based on simulated attacks that proactively highlight high-risk security deficiencies and quantify risk. It translates technical findings into executive reports, enabling business leaders to track cybersecurity performance and risk management. This will empower you to focus on the truly exploitable by validating security controls and proving real threat exposure with the full context of security control effectiveness, active threat intelligence and business impact.
Key benefits include:
- Real-Time Exposure Management – Identify and prioritize truly exploitable vulnerabilities based on security control effectiveness, active threat intelligence, and business impact.
- Continuous Control Validation – Go beyond outdated penetration tests with automated attack simulations that assess security posture and validate existing defenses.
- Phishing Awareness & Training – Strengthen human resilience with phishing simulations and interactive training to reduce social engineering risks.
- Optimized Defense Strategies – Correlate threat assets, security controls, and mitigation efforts to enhance security posture with actionable insights.
- Proven Cyber Resilience – Demonstrate cybersecurity readiness with executive-level reporting and continuous exposure assessments.
By focusing on true exposure rather than theoretical risks, Cymulate equips organizations with the intelligence needed to make informed security decisions and strengthen defenses against real-world threats.


