CYMULATE EXPOSURE MANAGEMENT PLATFORM
AI-powered CTEM with the full context of threat validation
Sharpen resilience to cyber threats with exposure management technology that integrates discovery and validation for targeted defense optimization.
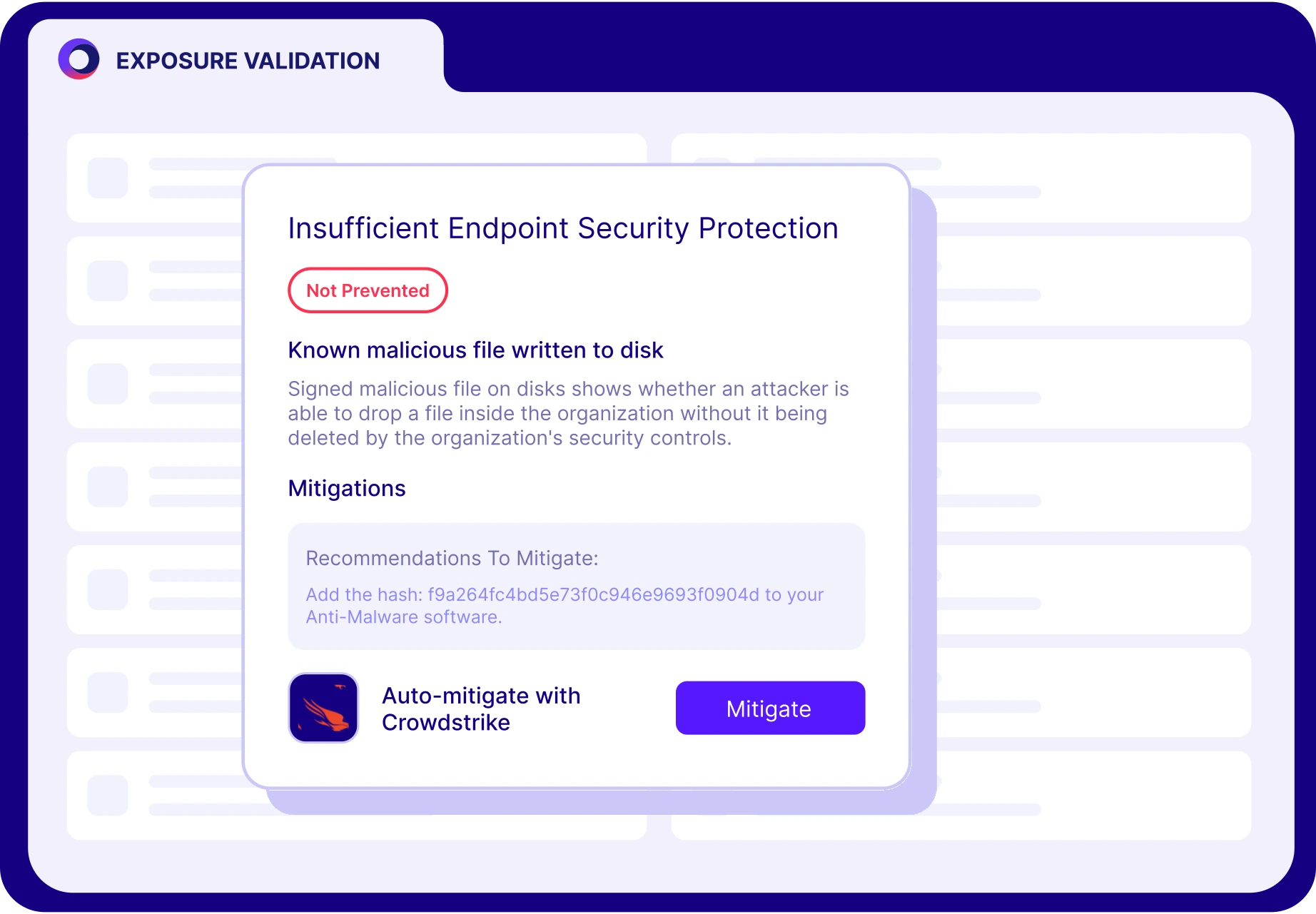
Find and fix security gaps that can be exploited
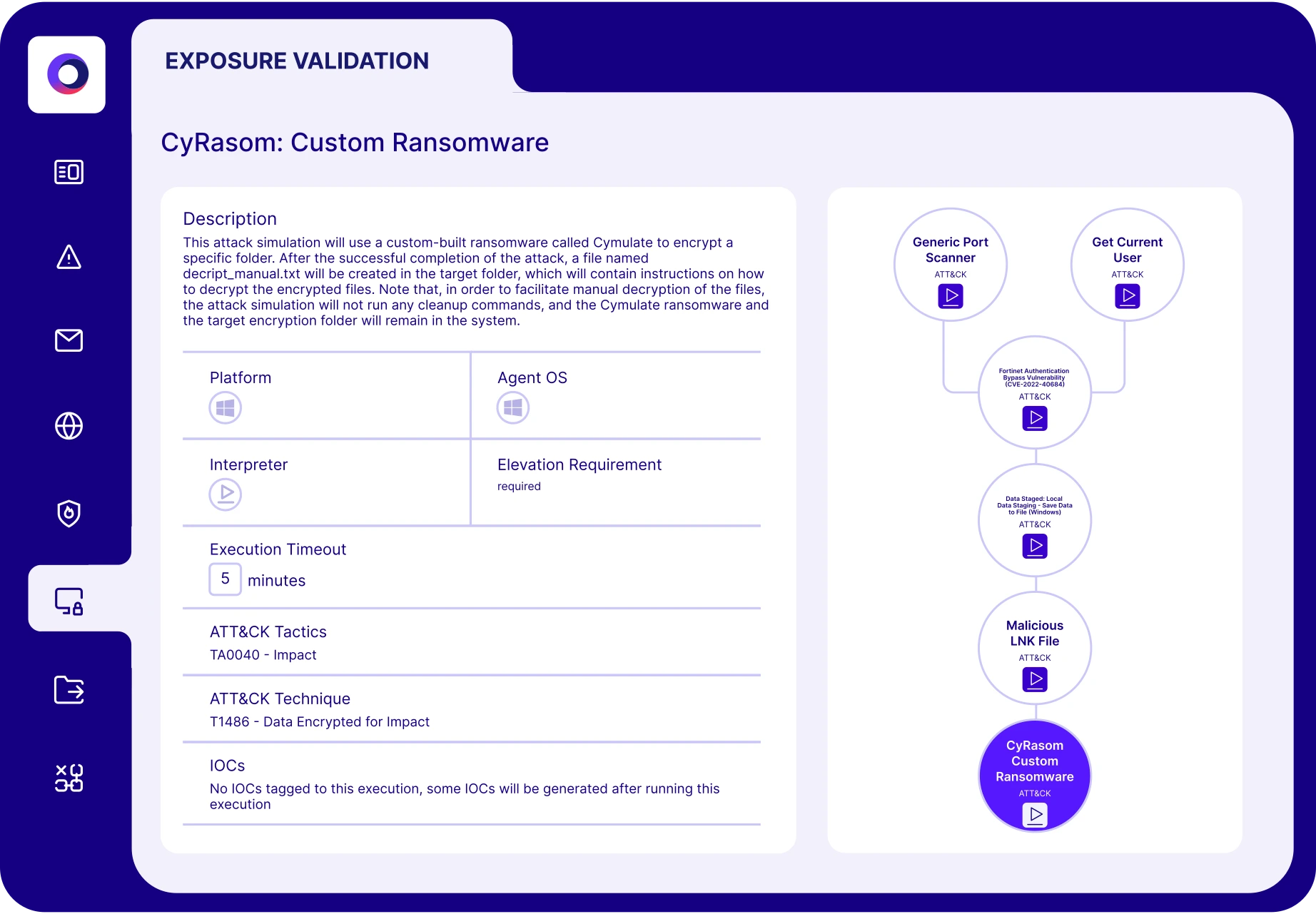
Validate Threats
Prove exploitability
Optimize Resilience
Tune security controls
Accelerate CTEM
Collaborate across teams
The Cymulate Difference
Cymulate automates threat validation and integrates exposure data to prove risk and optimize resilience. Fueled by market-leading attack simulation, Cymulate applies AI to make offensive testing easy, scalable and continuous.
Continuous
validation
Advanced offensive testing made easy with automation and AI.
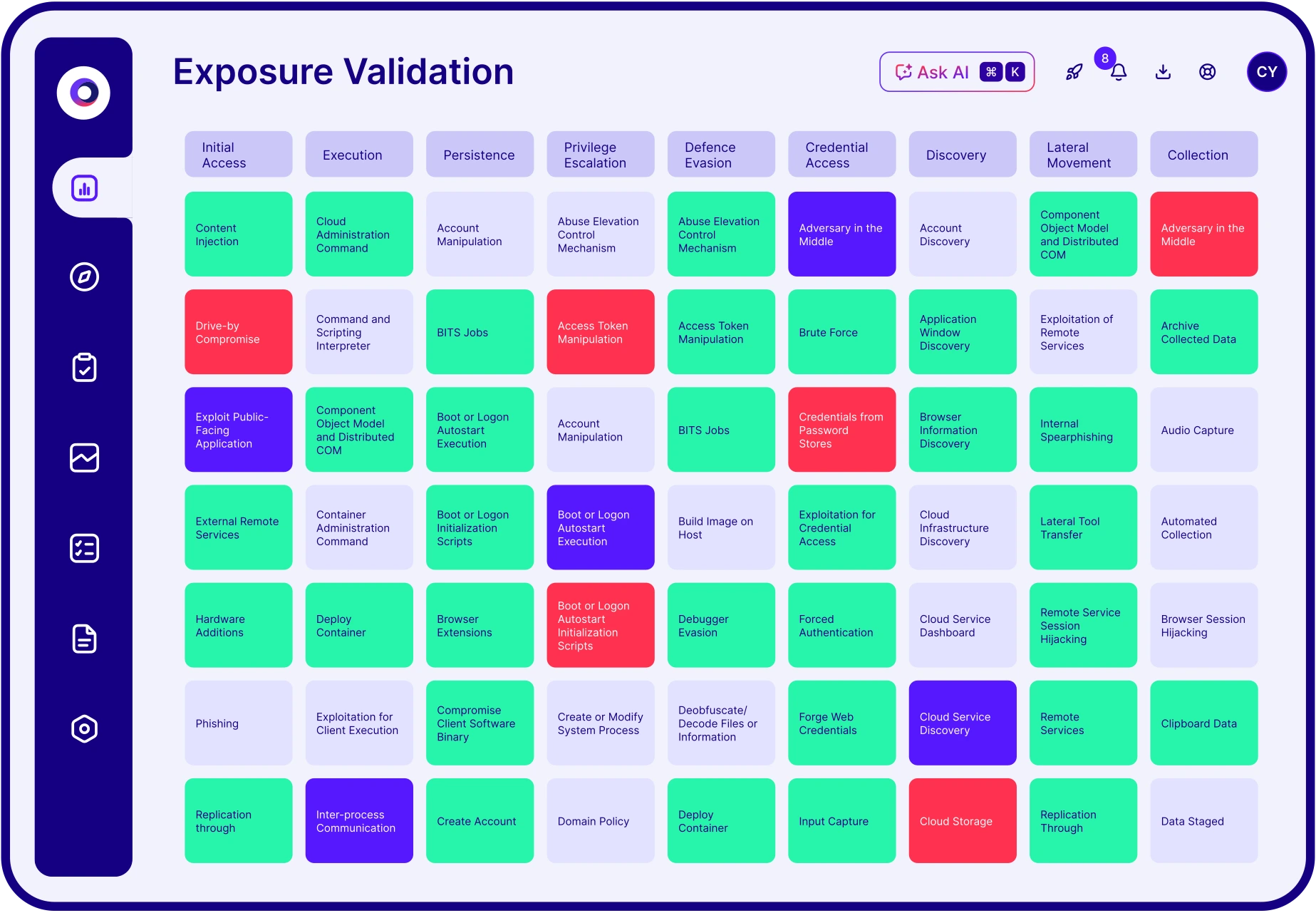
Kill chain
coverage
Attack lifecycle simulation from access to exfiltration.
Advanced
testing
Build and scale custom attack simulations for any environment.
Easy
integrations
Map complex attacks to controls and exposures.
Other solutions lack threat validation.
We put the “T” in CTEM.
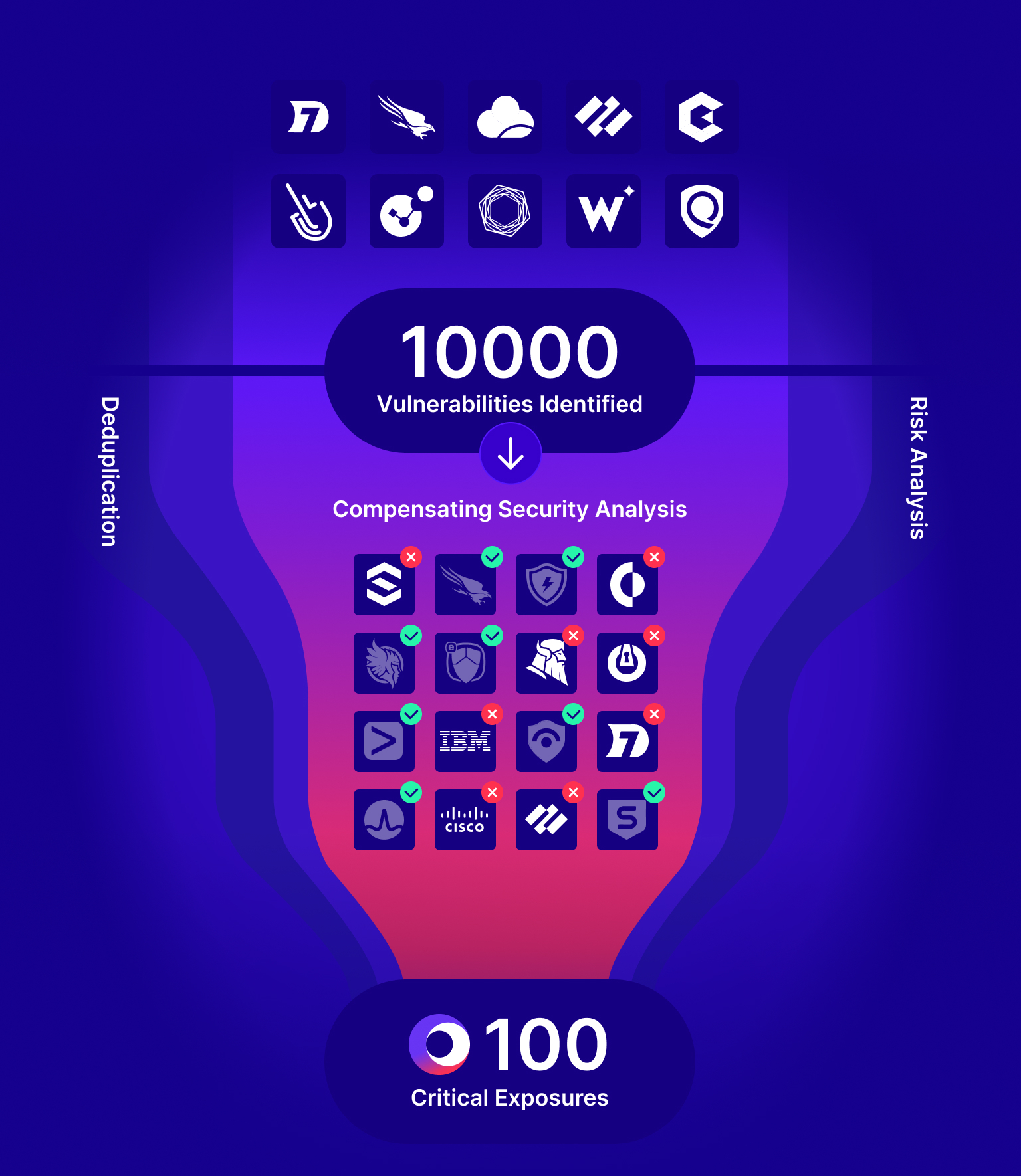
Cymulate delivers powerful impact — and measurable ROI
30%
Improvement in threat prevention
AVG. of CYMULATE CUSTOMERS
52%
Reduction in critical exposures
AVG. of CYMULATE CUSTOMERS
60%
Increase in team
efficiency
FINANCE COMPANY
What our customers say about us
Organizations across all industries choose Cymulate for automated cybersecurity validation, proactively confirming that defenses are robust and reliable – before an attack occurs.
GET A PERSONALIZED DEMO
Ready to see Cymulate in action?
“Cymulate shows us our security gaps so we know what to focus on, where to prioritize our patching, and discover where we should invest most of our efforts.”
– Vice President and Head of Cybersecurity, Investment Firm