BYOVD (Bring Your Own Vulnerable Driver) attacks are cyber security attacks that exploit vulnerabilities in drivers, leveraging new techniques that allow them to evade traditional protections and maximize disruption. This clever technique, described in detail in the September 2023 Cymulate Threat Research Lab Update Webinar, abuses legitimate but flawed driver software to disable security controls and encrypt systems.
How Do BYOVD Attacks Work?
BYOVD attacks aim to avoid defenses and bypass security. Running this technique involves loading vulnerable legitimate drivers to obfuscate against or even remove security control systems. To appreciate why this tactic is so effective, it helps to understand how drivers – and specifically kernel-mode drivers – work in Windows.
Drivers run at ring 0, the most privileged level of the operating system. This grants them direct access to critical memory, CPU, I/O operations, and other fundamental resources. Drivers underpin most core OS functions, security tools included. However, flaws in certain drivers allow attackers to abuse their privileges. It isn’t uncommon to see vulnerabilities in drivers that are installed and leveraged by threat actors to perform attacks; but in the case of BYOVD, the attack is designed to load a vulnerable driver to further the attack.
Modern security relies on kernel-level components like OS integrity checking, EDR, and behavioral monitoring, but many of these defenses run as drivers themselves or rely on drivers to function. By loading a vulnerable driver, attackers can exploit its bugs to corrupt, crash, or disable protective drivers and other ring 0 security tools. This blinds defenses at the lowest level, clearing the way for unimpeded encryption and exfiltration.
While advanced EDR/XDR solutions may detect this form of manipulation of the OS, not all platforms provide that functionality; leading to a gap in defenses that groups like Cuba can take advantage of.
Meet the Cuba Ransomware Group, a Specialist in BYOVD Attacks
To understand the gravity of the BYOVD attacks, it is important to recognize the increasing danger posed by threat actors like Cuba ransomware. Suspected of emerging from Russia, Cuba ransomware has rapidly gained notoriety for ransoming and extorting major financial corporations worldwide.
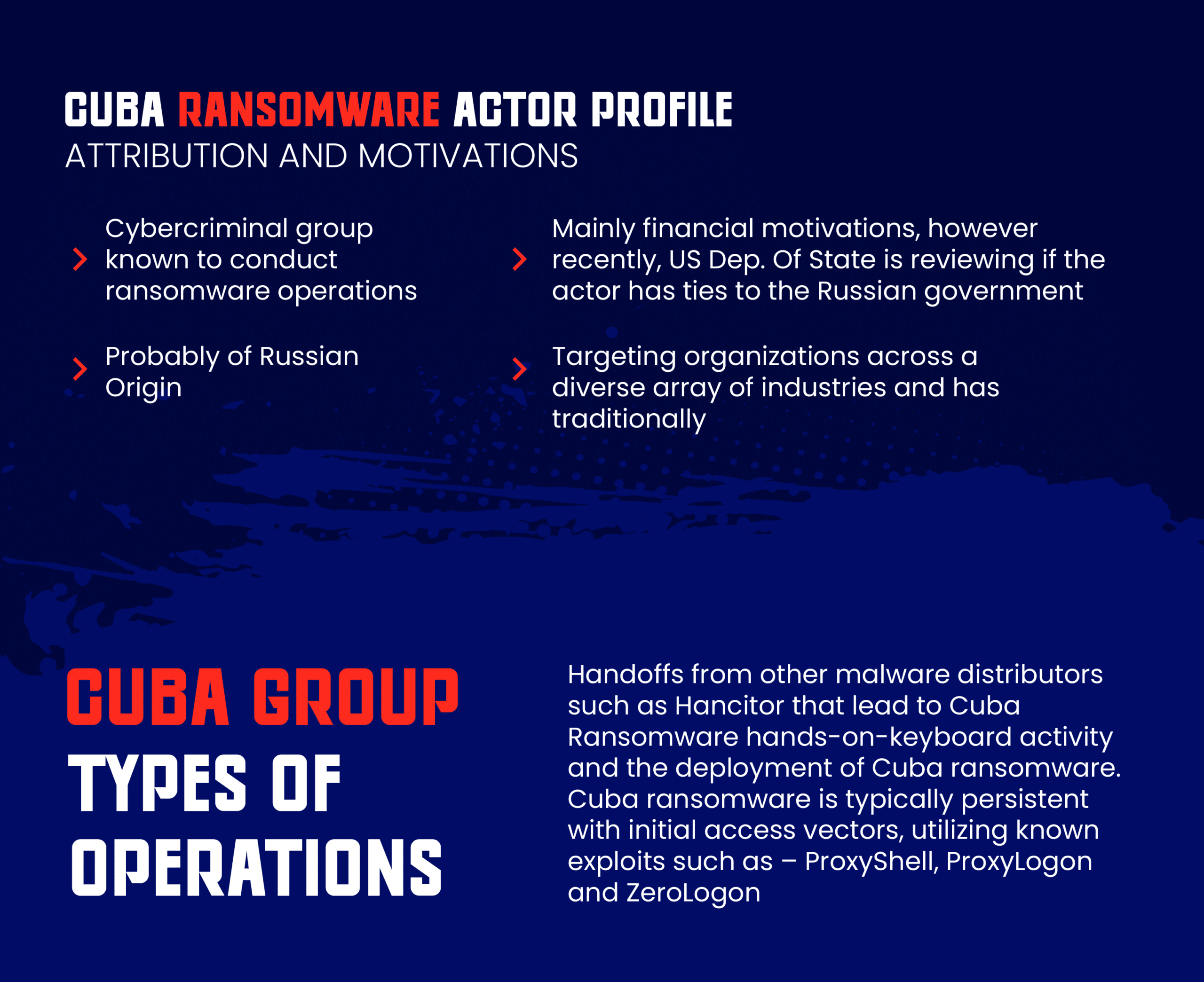
Since it was identified in 2019, the Cuba ransomware group has inflicted over $50 million in damages and displays a high degree of technical sophistication. Like other modern ransomware attackers, Cuba ransomware maintains an established infrastructure for initial compromise, lateral movement, data exfiltration, and money laundering.
Their attack playbook relies heavily on exploiting common vulnerabilities like ProxyShell in Microsoft Exchange Servers, and also on using initial access brokers to further expand the breadth of environments they can engage in.
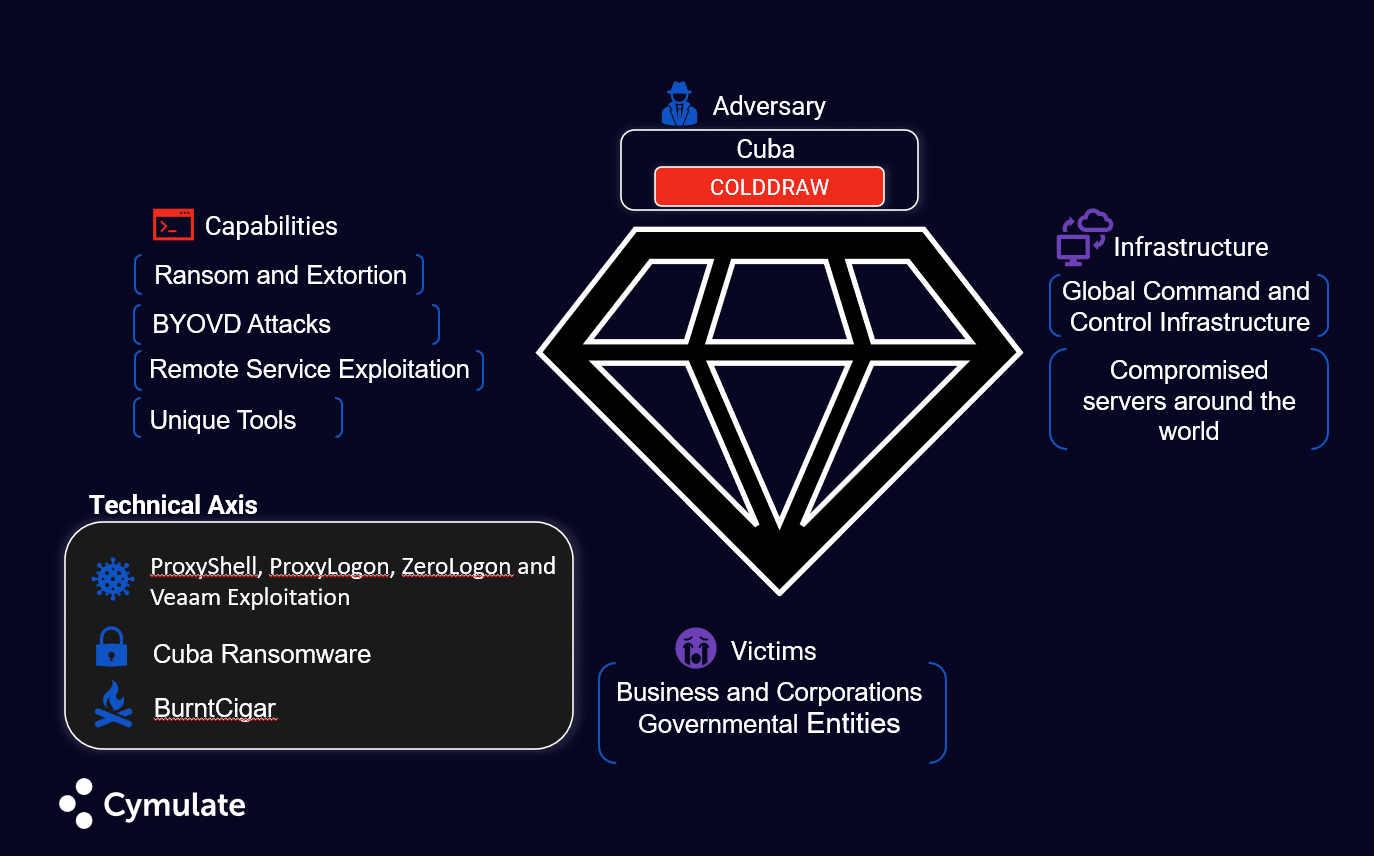
In addition to server exploits, Cuba ransomware’s arsenal includes unique tools like “BurntCigar” malware and, more to the point, the BYOVD attack analyzed below.
Why Are BYOVD Attacks so Effective at Evading Defenses
What makes BYOVD attacks so insidious is their reuse of signed, legitimate drivers. Windows, in most default configurations, requires all drivers to be digitally signed by the vendor or Microsoft. This aims to prevent the loading of malicious unsigned drivers. BYOVD turns this security feature against itself by abusing properly signed but flawed drivers. Though more difficult to employ, even revoked driver signatures may still load in Windows. This means blacklisting vulnerable driver hashes is often ineffective.
Key Mitigation Strategies
How can organizations protect themselves from BYOVD attacks by threat groups like Cuba ransomware?
The most direct mitigation is upgrading end-of-life operating systems like Windows 7 and Server 2008 which are most vulnerable to BYOVD. However, if there is no possibility to rapidly evolve from relying on legacy infrastructure, applying the following best practices can help reduce exposure:
- Perform regular audits of kernel drivers and apply their vendor patches
- Harden administrative privileges required to load drivers
- Implement kernel protection tools that prevent unauthorized driver loading
- Monitor driver load events via Windows Event Logs
- Use behavioral monitoring to detect driver-based termination of security processes
For monitoring, make sure to collect event logs and telemetry from legacy servers, endpoints, and any other available devices. Tools like Sysmon and WEF are invaluable for gaining kernel visibility on servers. Feed this data into a capable SIEM to baseline normal driver, load patterns, and alert on anomalies.
Containment is also key, so you should isolate systems exhibiting suspicious kernel activity to prevent lateral movement. With BYOVD attacks, this may require fail-safe physical controls since software defenses are already compromised. An application control solution can also help prevent unauthorized kernel code execution.
Simulating BYOVD attacks
For proof of value, advanced attack simulation platforms like Cymulate can safely model BYOVD and other advanced ransomware behaviors. Running simulations helps validate detection, prevention, and response capabilities before a real attack. Running attack simulations to detect rootkit-type activities can be done with Cymulate BAS (Breach & Attack Simulation) in a production-safe way.
Red teams can load vulnerable drivers, terminate security processes, and encrypt files in a sandboxed environment to experience the attack’s progression firsthand with advanced scenarios. Detailed post-execution reports assess performance in alerting on suspicious and malicious activity and stopping simulated ransomware at each stage. Simulation arms security teams with data to demonstrate inherent risks to leadership and prompt action on remediation recommendations.
Core Practices to Combat Evolving Ransomware Threats
While ransomware groups continue evolving, the core principles of good security hygiene still apply. This includes prompt patching, least privilege, segmentation, backups, and recovery planning. For critical legacy systems, compensate with rigorous monitoring and containment capabilities. Verify these controls through continuous red teaming and attack simulation. With robust defenses augmented by threat intelligence and testing, organizations can protect themselves against even sophisticated kernel-level attacks.
For a full overview of BYODV attacks, check out the September 2023 Cymulate Threat Research Lab Update webinar that also covers topics such as:
- Securing legacy infrastructure against modern threats
- Using threat intelligence to improve ransomware defenses
- The rise of kernel-level threats
- Collaborative cybersecurity between business and IT
- An in-depth analysis of the Cuba ransomware group










