Vulnerability Assessment vs. Penetration Testing: Key Differences and When to Use Each
With more cyber threats than ever before, protecting your organization’s assets and sensitive data has never been more critical. Businesses must take measures to implement robust security to safeguard their systems. Among the vast array of modern tools available are two essential components of any comprehensive security strategy: vulnerability assessment and penetration testing.
What is a Vulnerability Assessment?
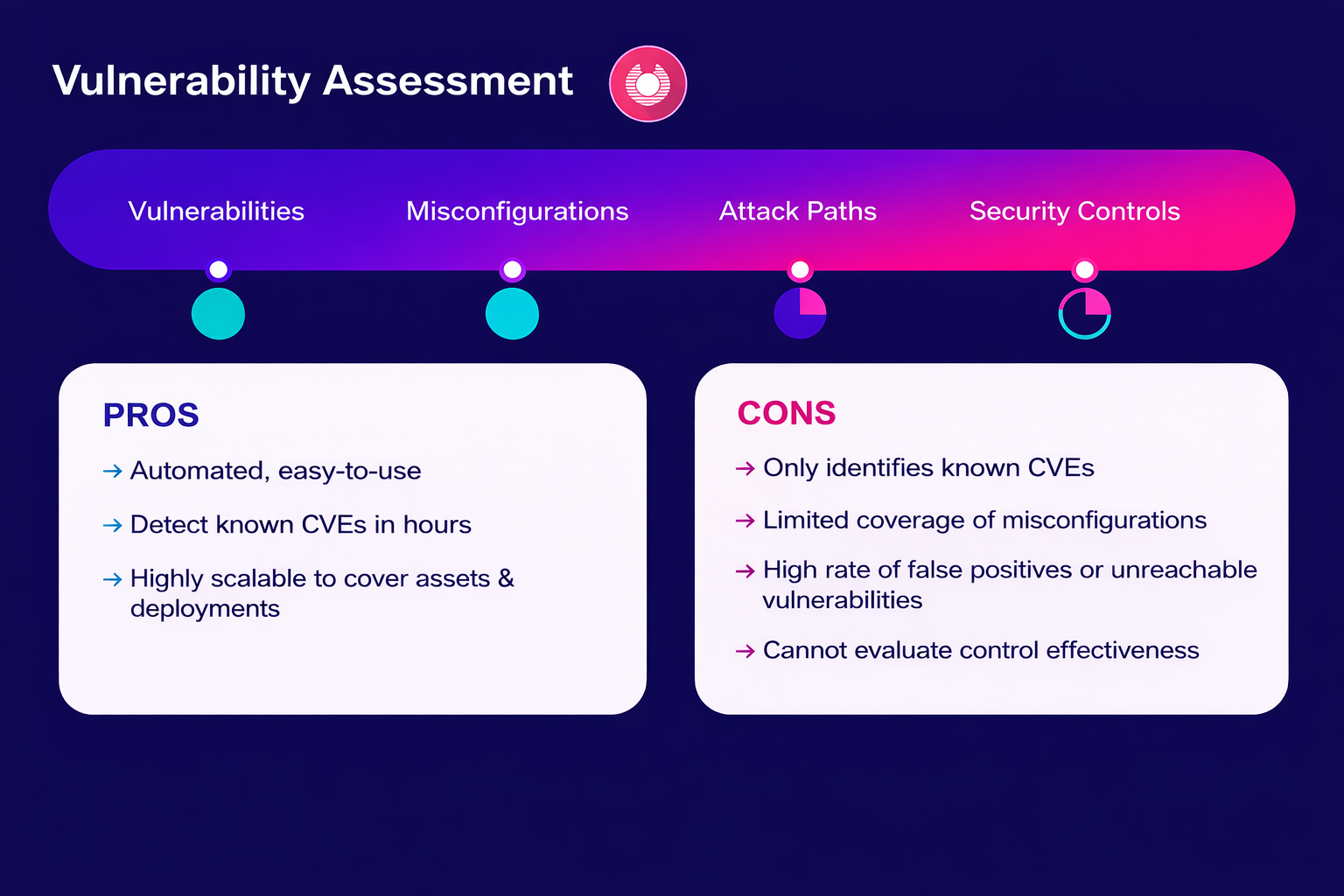
Definition: A vulnerability assessment is a systematic process of identifying, evaluating, and prioritizing potential vulnerabilities in a system. This could involve software, hardware, networks, or any other component of an IT infrastructure.
Main goal: The goal of conducting a vulnerability assessment is to identify weaknesses before they can be exploited by malicious threat actors. By assessing risks, teams can prioritize vulnerabilities, make recommendations for mitigation and lastly, provide continuous improvement to ensure new threats and weaknesses are addressed in a timely manner.
The Vulnerability Assessment Process
- Planning and scoping: Define the scope of the assessment, set objectives and goals and gather information about the system, network architecture and security measures in place.
- Scanning and identification: Utilize automated tools to scan systems and networks for known vulnerabilities and manually review configurations, code and systems where necessary to detect issues missed by automated tools.
- Analysis and assessment: Analyze data collected from the scan to identify vulnerabilities, then assess the severity using industry standards such as, Common Vulnerability Scoring System (CVSS) to prioritize remediation efforts and resources.
- Reporting: Document findings, including identified vulnerabilities, their risk levels and potential consequences for exploitation and provide recommendations for remediation.
- Remediation and Monitoring: Implement mitigations or solutions for high-risk vulnerabilities, such as applying patches, updating software and changing configurations. Continuously monitor system for new vulnerabilities and regularly re-assess systems especially after any threat intelligence.
Challenges: Conducting a comprehensive assessment requires time, skilled resources and often expensive tools that smaller organizations will typically have to either outsource or struggle to allocate funds for. Vulnerability scanning tools are only as good as the skilled user, as they can produce false positives or negatives. Vulnerability assessments can quickly become outdated and unable to keep pace with fast moving threats, leaving teams behind.
What is penetration testing?
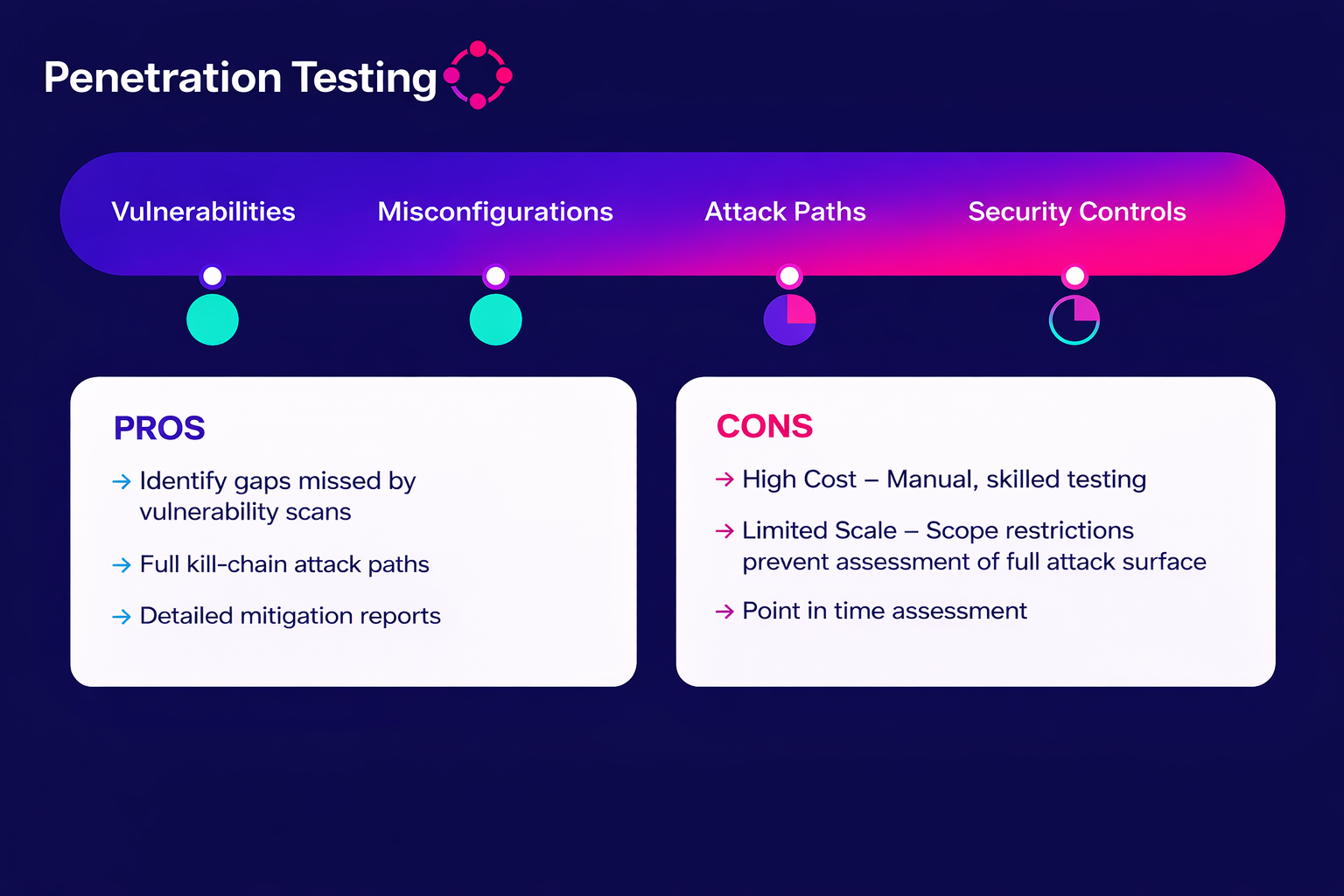
Penetration testing, also known as pen testing or “ethical hacking,” is an intentional, systematic process of evaluating an organization’s cybersecurity status by simulating real-world cyber attacks against a computer system, network or web application to identify vulnerabilities that malicious actors could exploit.
The goal of pen testing is to find exploitable weaknesses within systems, networks, applications or processes that an adversary could use to gain unauthorized access. Other goals of pen testing include assessing risk exposure, testing defense mechanisms, simulating real-world attacks, providing regulatory compliance and actionable remediation.
Penetration testing is highly effective, but comes with significant challenges. Time constraints can cause testers to miss subtle vulnerabilities and complex interconnected systems make thorough testing difficult and costly.
How to conduct a penetration test and vulnerability assessment
To run effective vulnerability assessments and penetration tests, security teams must understand the workflows behind them. Automated scanners and manual testers use different tactics to expose weaknesses. The following breakdown shows exactly how each methodology works in the field.
The vulnerability assessment process
A systematic vulnerability assessment follows a structured, five-phase approach designed to identify, evaluate and remediate security weaknesses. Here's how the process typically unfolds:
- Planning and scoping: Define the scope of the assessment, set objectives and goals and gather information about the system, network architecture and security measures in place.
- Scanning and identification: Utilize automated tools to scan systems and networks for known vulnerabilities and manually review configurations, code and systems where necessary to detect issues missed by automated tools.
- Analysis and assessment: Analyze data collected from the scan to identify vulnerabilities, then assess the severity using industry standards such as Common Vulnerability Scoring System (CVSS) to prioritize remediation efforts and resources.
- Reporting: Document findings, including identified vulnerabilities, their risk levels and potential consequences for exploitation and provide recommendations for remediation.
- Remediation and Monitoring: Implement mitigations or solutions for high-risk vulnerabilities, such as applying patches, updating software and changing configurations. Continuously monitor the system for new vulnerabilities and regularly re-assess systems, especially after any threat intelligence.
The penetration testing process
Penetration testing is a more intensive, hands-on approach than vulnerability assessment. Rather than simply identifying weaknesses, penetration testers simulate real-world attack scenarios to demonstrate how those vulnerabilities could actually be exploited. The process consists of six distinct phases:
- Planning and scoping: Define the goals of the penetration test, whether it’s to identify vulnerabilities, test specific network segments or simulate an attack. Determine which systems, applications, networks and assets will be tested and gain organizational permission to conduct the tests.
- Information gathering: Collect both public and non-public data, including domain names, IP addresses, employee details and organizational structure for public data. For non-publicly available information, look for more technical details about the system’s configuration and weaknesses, including network mapping and port scanning.
- Assessment: Leverage automated tools to scan for known vulnerabilities and misconfigurations, then manually review and analyze results to identify issues that may require repeat testing.
- Exploitation: Identify the vulnerabilities that you will try to exploit and gain unauthorized access, elevate privileges or bypass security controls. Use techniques such as SQL injection, buffer overflows or social engineering. Once access is achieved, identify which data can be accessed or exfiltrated and which systems could be compromised. Test for potential backdoor access and privilege escalation.
- Reporting: Document the findings, include a summary of exploited vulnerabilities, the risk level of each and the methods used. Include recommendations for improving security posture, such as strengthening network segmentation, changing configurations and employee training.
- Remediation: Provide remediation steps, including technical solutions and process improvements. After the fixes are in place, retest to verify that the vulnerabilities are no longer accessible and that the system is secure.
The key differences between pen testing and vulnerability assessment
Understanding the difference between a vulnerability assessment and a penetration test is essential for choosing the right approach for your organization's security needs, since they differ in scope, methodology, and purpose.
| Security testing attribute | Vulnerability assessment | Penetration testing |
|---|---|---|
| Purpose | Broad vulnerability identification | In-depth testing |
| Methodology | Automated scanning | Manual and semi-automated |
| Depth | Surface-level vulnerabilities | Exploitation-focused |
| Frequency | Regular/continuous | Periodic (annual or bi-annual) |
| Tools Used | Scanning tools | Manual/automated exploitation tools |
| Output | Risk prioritization reports | Detailed exploitation reports |
When to use pen test and vulnerability assessment
Although a well-rounded cybersecurity strategy often includes both approaches, each offers distinct benefits and serves different purposes.
When to use vulnerability assessments
Vulnerability assessments should be your go-to method for continuous monitoring and routine vulnerability management. Use vulnerability assessments to identify weaknesses, prioritize risks and manage patches on an ongoing basis. The vulnerability assessment approach is ideal for organizations seeking regular, automated insights into their security posture.
When to use penetration testing
Penetration testing should be used when you need a deeper dive into how an attacker might exploit your environment. Conduct penetration testing to evaluate the effectiveness of your defense systems against specific attack types, or to simulate real-world attack scenarios. A hands-on penetration testing approach is essential for validating your security controls.
Using both strategies for maximum security
When analyzing the automation of vulnerability scanning vs. penetration testing, security teams must distinguish between detection and exploitation. Scanners efficiently flag potential issues. However, these automated tools can produce false positives—flagging problems that aren't actually vulnerabilities—and may miss subtle vulnerabilities that require human expertise to uncover.
Penetration testers use advanced techniques—such as SQL injection, buffer overflows, privilege escalation and social engineering—to validate real-world impact. The distinction is critical when debating vulnerability testing vs penetration testing. While vulnerability testing confirms their presence, active penetration attempts prove their danger.
Ultimately, mature organizations combine vulnerability analysis and penetration testing. Vulnerability assessments handle the routine identification and analysis of known bugs, while penetration tests verify resilience against complex threats. This dual strategy ensures the organization stays ahead of evolving cyber risks through both constant monitoring and validation.
Deciding between pentesting and vulnerability assessment
Choosing between pentesting and vulnerability assessment depends on several key factors: organization size, budget, security objectives, and compliance requirements. Here's how to evaluate each factor for your organization:
Organization size and maturity
Small to mid-sized businesses (SMBs) usually benefit more from vulnerability assessments due to resource constraints and ongoing monitoring needs. Whereas large enterprises with more complex IT infrastructures often have the resources and need for both types of evaluation and testing as well as the mature security processes in place to act on any findings.
Budget and resource availability
For organizations with limited budgets, a vulnerability assessment is best suited, as it is less resource-intensive and provides a good overview of gaps that can be prioritized and addressed over time. For organizations with greater budgets, they may conduct both a vulnerability assessment and a pen test, enabling more comprehensive coverage with continuous monitoring.
Security objectives
A vulnerability assessment is the right choice if the goal is to identify and prioritize potential risks across an environment. Conducting a pen test is an option when the goal is to validate the effectiveness of existing security controls by simulating a real-world attack.
Compliance and regulatory requirements
Depending on the industry, they may require specific types of security assessments. For example, the Payment Card Industry Data Security Standard (PCI DSS) mandates regular vulnerability scans as well as annual pen tests and organizations must comply with this mandate.
| Decision factor | Vulnerability assessment | Penetration testing |
|---|---|---|
| Organization size | Small to mid-sized businesses | Large enterprises |
| Budget | Limited budget | Sufficient budget |
| Security objectives | Risk identification and prioritization | Validation of security controls |
| Compliance needs | Routine compliance checks | Specific regulatory mandates |
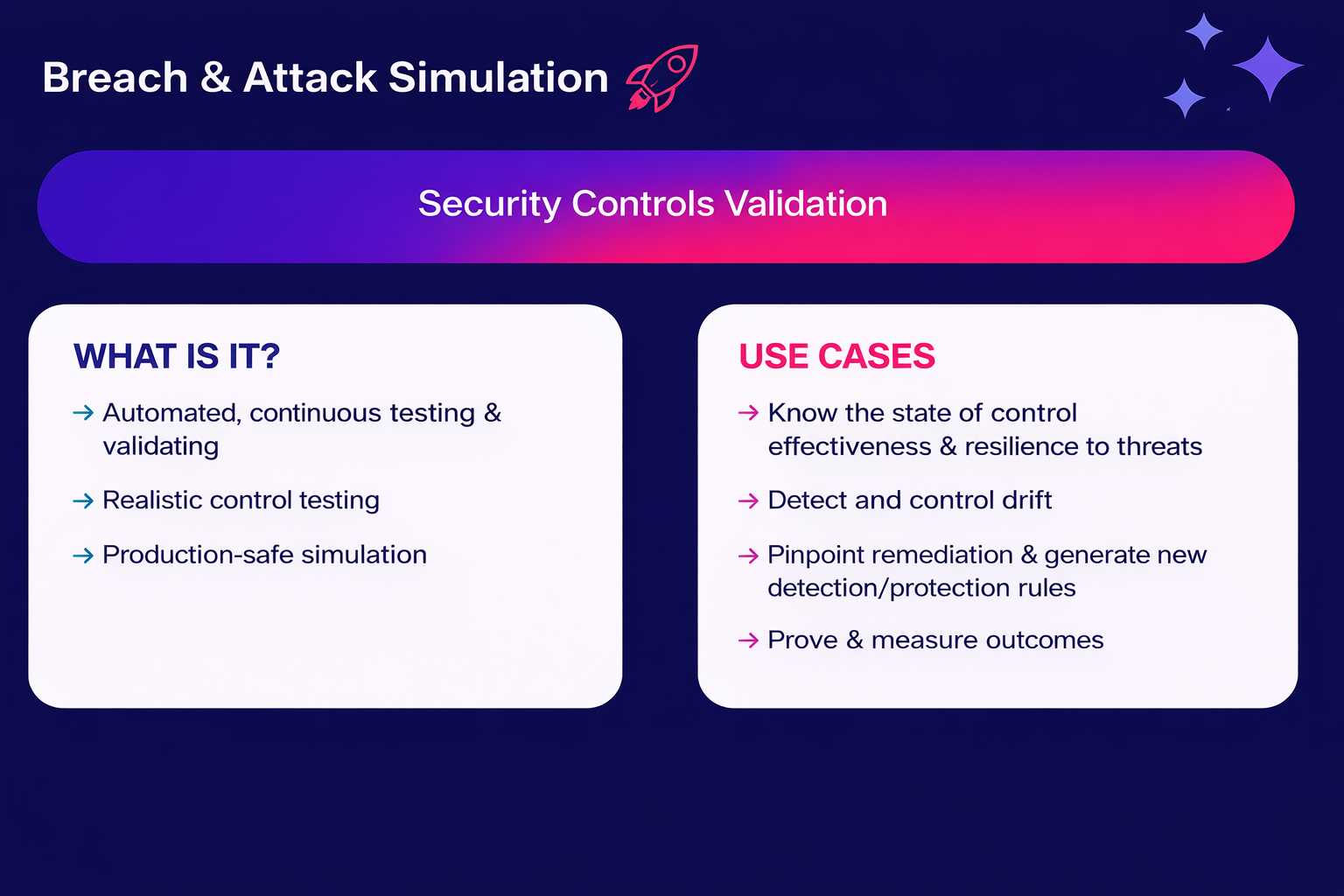
Prove your threat resilience with Cymulate Exposure Management
When you combine continuous monitoring of vulnerability assessments with deep exploitation testing in penetration tests, you get exposure management.
The Cymulate Exposure Management Platform delivers continuous validation of threat exposure, helping organizations prove threat resilience and build defenses that actually work. By automating threat-exposure validation with AI-powered testing, Cymulate enables security teams to prioritize validated threats, correlate exposures with offensive-test results and focus remediation efforts on vulnerabilities that pose real risk.
Key benefits of the Cymulate platform:
- Continuous AI-powered security testing that identifies exploitable vulnerabilities
- Focus on validated threats that actually matter, not noise from scanning tools
- Aggregate exposures from your existing vulnerability management and discovery tools
- Automated mitigation guidance and continuous validation of fixes
See Cymulate in action. Book a demo and discover how to reduce critical exposures and improve threat resilience.