Cloud Security Validation: Best Practices & Key Insights
Cloud security threats evolve rapidly, and misconfigurations can expose critical workloads. To ensure resilience, organizations must validate security controls across all layers of the cloud architecture. This guide outlines key best practices for continuous cloud security validation.
Before we look at cloud security, let us recall the principle of security validation as defined by Cymulate.
The Principle of Security Validation
Security Validation is a fundamental principle in cybersecurity aimed at ensuring that systems, applications, and processes are secure and operate as intended.
Based on our principle, the goal is to ensure that the applications and workloads running in a cloud environment are secure and that the controls used to secure the different layers of the cloud architecture operate as intended to stop cloud-based threats.
Why Organizations Invest in Cloud Transformation
Organizations are making significant investments in moving applications and workloads to the cloud, enabling them to scale their operations to the needs of their business. Cloud transformation offers organizations:
- Scalability and flexibility based on business demand
- Innovation and agility leveraging advanced technologies
- Operational and cost efficiency by reducing complexity and capital expenditure
- Competitive advantage for faster deployment of new products and services
However, this new cloud frontier and the very dynamic nature of cloud platforms can make it difficult to optimize cloud security and get it right the first time and equally difficult to maintain cloud security at an acceptable level of risk over time.
In addition, cloud platforms can be used for a variety of different purposes – from running applications in secure containers, hosting virtual machines as endpoint devices, or using cloud for data storage and backup.
This makes continuous validation of cloud security controls an essential best practice to ensure that the controls defending our cloud applications and workloads are operating as intended. And depending on how the cloud platform is being used determines the type of security controls needed to protect whatever is hosted on it.
Securing Different Layers of Cloud Architecture
The diagram below highlights different types of security controls used across the different layers of a cloud architecture.
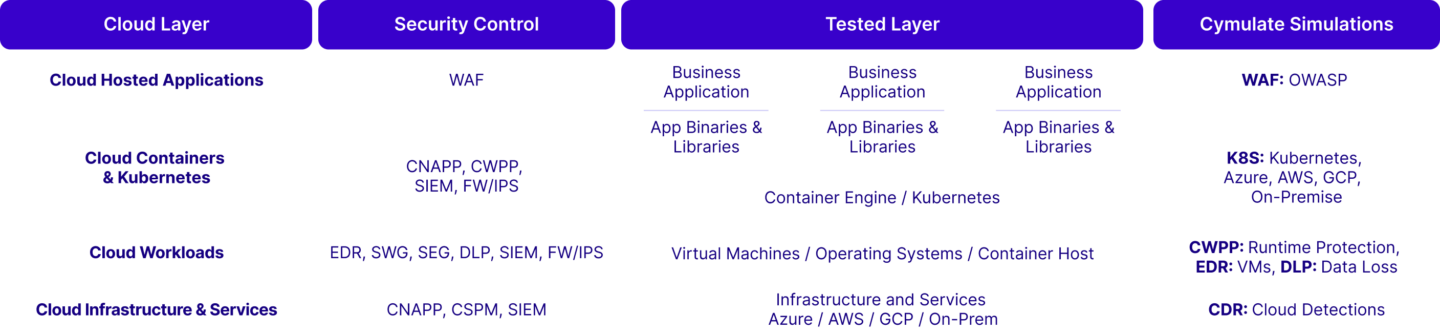
Cloud Hosted Applications
When it comes to applications hosted in the cloud, Web Application Firewalls (WAFs) (which can also be hosted in the cloud or delivered as part of the content delivery network) are used to protect the application the same way we would for the application running on-premises.
The Cymulate Web App Firewall validation is used to test and validate that the application security control (the WAF) is operating as intended. During the WAF assessments, Cymulate sends thousands of payloads from the OWASP top 10 list and based on the HTTP/S response received by the Cymulate attack server, determines whether the payload was blocked or penetrated.
Cloud Containers & Kubernetes
Testing the effectiveness of container security is essential for ensuring the security of cloud applications and workloads. Continuous validation helps identify threats specific to containers, such as unauthorized access, data breaches, and runtime attacks, ensuring robust protection across your cloud environment.
These controls prevent or detect malicious activities within containerized environments and Kubernetes platforms, ensuring the security of applications and workloads inside containers. These controls include:
1. Cloud-native Security Controls
- Azure Defender for Cloud
- AWS GuardDuty
- Google Cloud Command Center
2. Cloud Workload Protection Platform (CWPP)
3. Cloud-Native Application Protection Platform (CNAPP)
4. Security Information and Event Management (SIEM)
5. Firewall (FW) / Intrusion Prevention Systems (IPS)
Cymulate enables you to test your container security controls using cloud-native malicious scenarios and privileged activities, such as container escaping, secrets listing, clear history, and other persistent and evasive techniques. Cymulate container security assessments focus on Kubernetes environments and are available for Azure, AWS, and Google Cloud-managed Kubernetes and on-premises deployments. Assessments are available for both pre and post-exploitation:
- Pre-Exploitation: Simulates an attacker executing malicious actions from within a container or Kubernetes platform. This type of assessment includes test cases such as attempts to escape from the pod to the host to evaluate if such actions are detected and prevented by the cloud security controls.
- Scanners: Test common Kubernetes misconfigurations on Azure, AWS, and Google Cloud.
- Advanced Scenarios: Simulate advanced attack scenarios to assess your Kubernetes security posture.
- Post-Exploitation: Assumes an attacker has escaped the container and runs malicious activities on the host. This type of assessment includes test cases such as connection to command-and-control servers, file encryption, and deployment of crypto mining operations.
Cloud Workloads
Cloud platforms are used to host different types of workloads including compute workloads like virtual machines (endpoints), data centric workloads like file / data storage, databases, and big data / data lakes, and application workloads like web apps and enterprise SaaS applications to name a few.
Cymulate tests the security robustness of cloud workloads running on EC2 instances, Azure VMs, and GCP compute instances by simulating common attack scenarios like crypto mining operations on a cloud workload, cloud data exfiltration from a data centric workload, and attacks targeting cloud-hosted applications.
We test and validate different types of cloud workloads using the different assessments for key security controls like:
- Windows Virtual Machines (VMs) hosted on a cloud platform would use our Endpoint Security Validation solution to test that the endpoint security controls can stop known malicious file samples and behaviors the same way we would for a physical Windows endpoint.
- File and Data Storage hosted in a cloud storage bucket would use our Data Exfiltration Validation solution to test that the data loss controls can stop data from leaving the cloud environment.
- Enterprise SaaS Application hosted in a cloud container would use our WAF Validation solution to test that the WAF security controls can stop malicious activity targeting the application.
Cloud Infrastructure & Services
When threat actors obtain access to cloud infrastructure and services, we need to be able to detect their presence through the existence of events in the SIEM platform. To validate that the SIEM can detect potential threat activity, we adopt an “assume breach” post-exploitation approach that simulates an attacker who has already gained credentials and access to the cloud environment.
Rather than looking for outright malicious activities, we test the effectiveness of your SIEM configuration by simulating high-privileged activities that a threat actor would typically execute during a cloud breach. This exercise aims to gauge which activities trigger SIEM events and whether those events correctly lead to alerts.
- Post-exploitation: Execution of malicious behavior test cases involving simulating cloud infrastructure high-privileged activities including data exfiltration through unauthenticated S3 buckets, unauthorized user additions, or exposure of sensitive ports.
Cymulate cloud security assessments evaluate the effectiveness of SIEM solutions in correlation with cloud logs, CSPM, and CNAPP security controls.
Recommended Frequency: Weekly
The goal of these best practices is to thoroughly test the effectiveness of an organization's cloud security controls and policies by simulating a wide variety of cloud-based threats and malicious, high-privileged behaviors.
Due to the very dynamic nature of cloud environments, it is highly recommended that these validation tests be run weekly or whenever changes are made to the cloud environment.
Cloud security is a strategic component of your security program and one that requires multiple forms of attack simulation to continuously test and validate that your security controls are operating effectively to protect your cloud applications and workloads.
For more information, download our solution brief and schedule a demo of our cloud security assessments.