Cybersecurity Posture: How to Assess, Measure and Improve It

Cyber threats are growing in scale, sophistication and speed. As attack surfaces expand across cloud, hybrid and on-premises environments, organizations can’t rely on traditional defense. The need for measurable resilience has grown immensely. That resilience begins with a strong cybersecurity posture: the collective strength, readiness and adaptability of an organization’s defenses.
A mature posture enables enterprises to withstand, recover from and adapt to evolving attacks. In this guide, we’ll explore what this means, why it matters, how to assess it and how to continuously improve and validate it so you’ll maintain long-term threat resilience.
Key highlights:
- Cybersecurity posture refers to the overall strength and readiness of an organization’s defenses against cyber threats.
- A cybersecurity posture assessment identifies vulnerabilities, evaluates control effectiveness and measures resilience.
- Continuous validation and automation help enterprises improve cybersecurity posture and maintain compliance.
- The Cymulate Exposure Management Platform enables organizations to harden security posture through continuous testing and validation.
What is cybersecurity posture?
Cybersecurity posture is the overall strength and preparedness of an organization’s security controls, processes and people to prevent, detect and respond to cyberattacks. It reflects how well your systems, networks and data are protected from evolving threats and how quickly you can recover when incidents occur thanks to overall threat resilience.
A strong cybersecurity posture provides visibility into risks, ensures layered defenses and minimizes dwell time for adversaries. By continuously validating and optimizing posture, organizations can harden security posture against sophisticated, multi-vector attacks and reduce the risk of operational disruptions.
Importance of security posture in cybersecurity
In today’s interconnected threat landscape, posture is not optional. It’s a fundamental part of any strategy, with 72% of cyber leaders saying risks are rising according to the World Economic Forum. A strong security posture is directly tied to an organization's ability to prevent breaches, comply with regulations and maintain business continuity. It determines how resilient, compliant and trustworthy the organization is from a cybersecurity point of view.
- Cyber threats are escalating: Attackers now exploit every weakness across hybrid and cloud infrastructures. Without proactive validation of controls and data security posture, organizations remain exposed to misconfigurations, privilege abuse and shadow IT.
- Stakeholders demand accountability: Boards and investors expect clear evidence of preparedness. A weak posture can erode confidence, while validated resilience with proven capabilities helps build trust among stakeholders and confidence within your organization.
- Compliance pressures are mounting: Regulations such as NIS2, DORA and HIPAA require proof of ongoing risk management. Continuous exercises to validate exposures demonstrate control efficacy and compliance readiness.
- Business continuity depends on resilience: Downtime from a breach or ransomware attack has direct financial and reputational costs. Strengthening posture reduces downtime risk and improves incident response agility.
- Competitive positioning requires trust: In industries handling sensitive data, trust is a differentiator. Enterprises that validate and report on posture maturity gain an edge in customer confidence and market reputation.
What are the key components of a strong security posture in cybersecurity?
A strong cybersecurity posture is multi-dimensional. It should integrate technology, people and processes into a single cohesive defense framework. Neglecting even a single layer leaves exploitable weaknesses.
| Components of cybersecurity posture | How the components work |
| Policies | Define governance, acceptable use and escalation procedures for incident handling. |
| Asset visibility | Ensures all systems, endpoints and cloud instances are continuously inventoried and monitored. |
| Risk management | Prioritizes vulnerabilities, third-party risks and business-critical exposures. |
| Incident response | Enables quick containment, eradication and recovery to minimize breach impact. |
| Employee training | Builds a human firewall through awareness and simulated phishing. |
| Continuous monitoring | Tracks changes, detects anomalies and validates defenses in real time. |
Together these elements form the foundation of enterprise cybersecurity posture management, aligning operational defenses with business and compliance goals.
Steps of a cybersecurity posture assessment
A cybersecurity posture assessment provides a structured approach to measuring readiness. It forms the basis for continuous improvement by revealing where defenses are strong and where gaps exist.
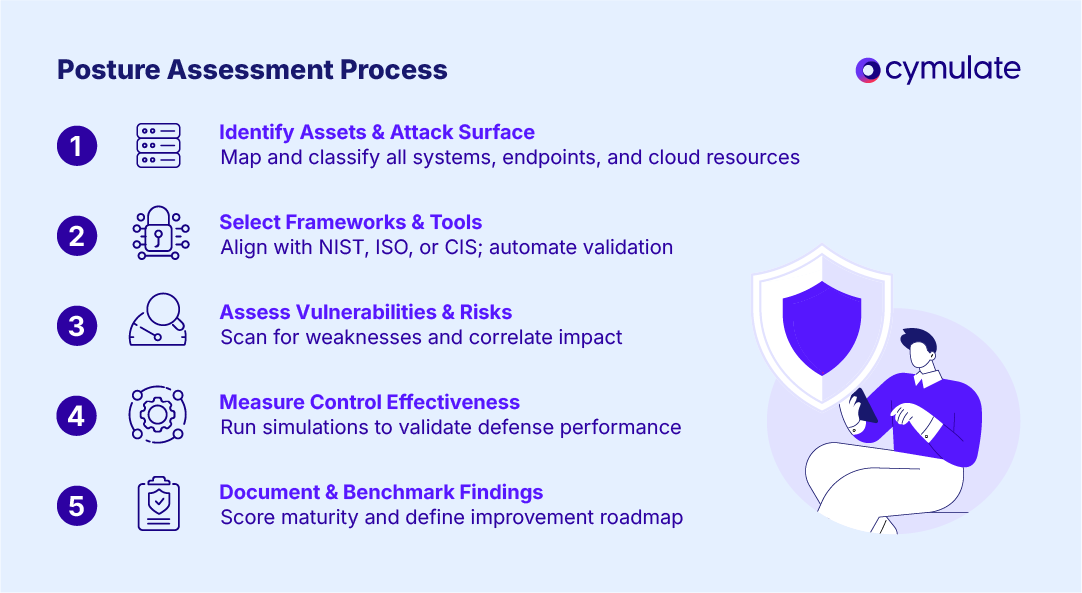
1. Identify assets and attack surface
Begin by cataloguing all digital assets. This includes on-premises systems, endpoints, IoT devices and cloud resources. A complete inventory enables accurate scoping of what needs protection.
- Map all applications, APIs and data repositories.
- Detect unmanaged devices and shadow assets.
- Classify assets by criticality and exposure level.
This discovery phase helps validate security posture by ensuring no asset is overlooked.
2. Select frameworks and tools
Use recognized frameworks such as NIST CSF, ISO 27001 or CIS Controls to guide posture measurement. Select automated tools that provide continuous validation and coverage across environments.
- Map controls to framework requirements.
- Choose assessment platforms capable of baselining maturity.
- Integrate results with SIEM, SOAR or exposure management systems.
A structured framework approach ensures posture data is standardized, comparable and actionable.
3. Assess vulnerabilities and risks
Identify and quantify weaknesses across endpoints, networks and cloud configurations.
- Scan for known vulnerabilities (CVEs) and misconfigurations.
- Correlate vulnerabilities with exploitability and business impact.
- Track inherited risks from vendors and third parties.
This phase reveals the true attack surface, which is the foundation for prioritized remediation.
4. Measure control effectiveness
Evaluate how well existing security controls detect and block threats in real-world scenarios.
- Run breach and attack simulations.
- Compare results with expected outcomes.
- Identify defensive blind spots with redundant tools.
This step ensures continuous validation and provides data to guide security posture assessment improvements.
5. Document and benchmark findings
Consolidate results into a comprehensive report that benchmarks your maturity against industry peers and compliance baselines.
- Highlight gaps and recommended actions.
- Score maturity across people, process and technology.
- Create an improvement roadmap tied to business objectives.
Benchmarking turns posturing data into measurable progress metrics for executive visibility.
Top cybersecurity posture management challenges
While most organizations recognize that posture is important, managing it at scale is complex. 76% of CISOs feel at risk of a material cyberattack in the next 12 months, but 58% said their organization is unprepared, per a Proofpoint survey.
There can be difficulties around complexity and limited resources. All of these factors can contribute to challenges that hinder continuous visibility and improvement. The following are challenges your organization must consider and plan around:
Limited visibility across assets and environments
Incomplete inventories create blind spots that attackers can exploit. Many environments are vast and may be difficult or cumbersome to inventory, but without a complete accounting there can be problems. You can’t secure something if you don’t know it exists.
Consequences:
- Unknown cloud instances or endpoints
- Shadow IT or rogue credentials
- Unmonitored third-party integrations
Manual processes and fragmented toolsets
Disjointed toolsets create data silos and inconsistent posture views. Additionally, when processes are implemented manually they can be inconsistently applied across an environment as well as leave open the possibility of human error.
Consequences:
- Redundant assessments and wasted effort
- Lack of centralized insight for risk prioritization
- Inconsistent compliance reporting
Cloud misconfigurations and hybrid complexity
Cloud environments evolve rapidly, making security posture drift inevitable. In hybrid environments, a mix of requirements between cloud and on-premises infrastructure can cause unforeseen issues. Misconfigurations can lead to easy targets for threat actors.
Consequences:
- Misconfigured storage buckets or IAM policies
- Overexposed APIs and containers
- Difficulty correlating findings across hybrid setups
Keeping up with evolving threats and attack surfaces
Modern adversaries evolve faster than most organizations can adapt. The continuous emergence of new exploits, zero-days and sophisticated attack paths force security teams into a constant state of reaction rather than prevention. This makes organizational resilience even more difficult.
Consequences:
- Lagging response to new threat vectors
- Incomplete patch cycles
- Difficulty maintaining validated resilience
Regulatory and compliance pressures
As the global regulatory landscape expands, security teams face mounting complexity in proving and maintaining compliance. New mandates and overlapping frameworks require organizations to demonstrate not just implementation, but continuous validation of security controls.
Consequences:
- Manual reporting consumes valuable resources
- Non-compliance risks financial penalties
- Audit fatigue due to repetitive validation cycles
Benefits of cybersecurity posture improvement
Investing in posture improvement delivers measurable gains across security, compliance and business performance. By enhancing security posture through continuous validation, automation and optimization, organizations can reduce risk exposure, strengthen governance and improve trust across stakeholders.
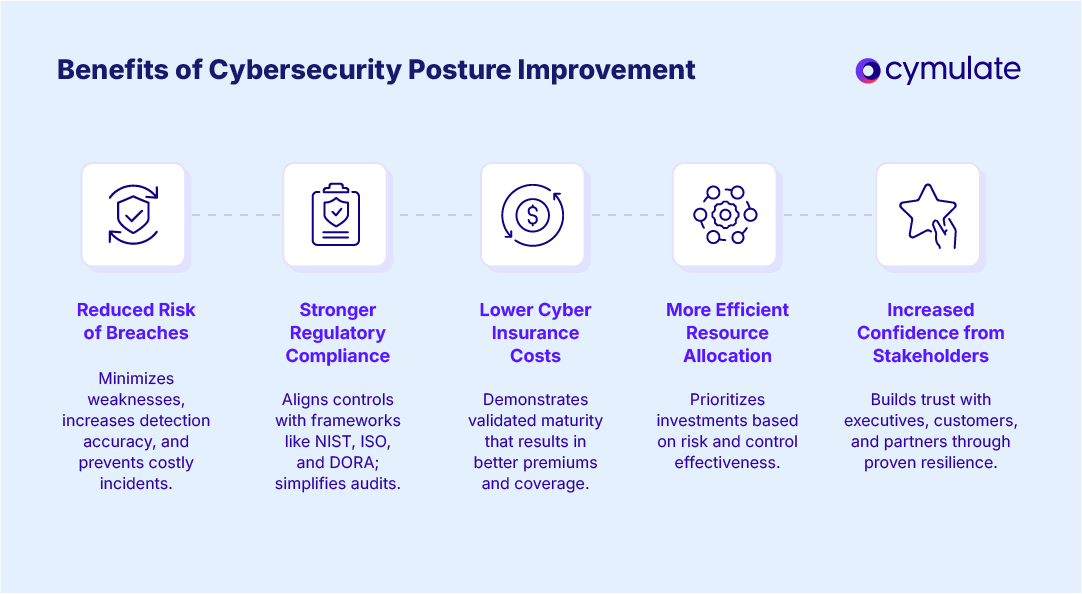
- Reduced risk of breaches: A stronger posture minimizes exploitable weaknesses, increases detection accuracy and shortens response times. Continuous validation identifies configuration drift and unpatched vulnerabilities before attackers can exploit them, preventing incidents that lead to data loss or downtime.
- Stronger regulatory compliance: Consistent posture validation aligns security controls with frameworks like NIST, ISO and DORA. Automated evidence collection and reporting streamline audits, reduce manual workload and help maintain ongoing compliance with ever-changing regulatory standards.
- Lower cyber insurance costs: Insurers reward organizations with demonstrably mature and validated security practices. Improving posture lowers perceived risk, which can translate into reduced premiums, faster policy approvals and better coverage terms from underwriters.
- More efficient resource allocation: Clear visibility into vulnerabilities and control effectiveness enables security leaders to prioritize investments where they matter most. This data-driven focus eliminates redundancy, reduces tool sprawl and directs resources toward mitigating high-impact risks.
- Increased confidence from stakeholders: Demonstrating measurable resilience builds trust with boards, customers and partners. A continuously validated posture shows that the organization takes proactive steps to protect sensitive data and maintain operational continuity, strengthening its reputation and competitive standing.
How to improve cybersecurity posture: A roadmap
Improving posture is a continuous journey, not a one-time task. It’s critical to follow a proven roadmap for ensuring your threat resilience is always up to the test. These steps help organizations optimize security posture and sustain resilience over time.
1. Assess your current security posture
Start by evaluating your existing controls, policies and gaps.
- Use automated assessments to reduce subjectivity.
- Benchmark against industry peers and frameworks.
- Build a baseline to measure progress.
2. Identify vulnerabilities and prioritize risks
Quantify exposure across all layers of infrastructure.
- Rank risks based on exploitability and business impact.
- Eliminate redundant tools and processes.
- Align remediation priorities with strategic goals.
3. Align with frameworks and compliance standards
Ensure your posture aligns with recognized security and regulatory frameworks.
- Map controls to NIST CSF or ISO 27001.
- Use continuous validation to maintain compliance readiness.
- Integrate with audit reporting tools for transparency.
4. Implement remediation and automation measures
Automate detection and response processes wherever possible.
- Deploy automated patching and misconfiguration correction.
- Integrate exposure management and SOAR solutions.
- Improve mean time to remediate (MTTR) for critical issues.
5. Continuously monitor and refine posture
Security posture is dynamic; treat it as a living metric.
- Schedule regular validation and testing cycles.
- Track metrics like mean time to detect/respond.
- Adjust controls and policies as your attack surface evolves.
Best practices for enterprise cybersecurity posture management
Enterprise environment requires scalable and automated approaches to posture management that integrate cloud, endpoint and identity data.
- Continuously assess and update posture: Continuous assessments ensure that security controls remain effective against emerging threats. This way your organization maintains technological, business and regulatory alignment with the evolving threat landscape and data security posture standards.
- Implement CSPM tools: Cloud security posture management solutions automatically discover and monitor cloud assets and correct cloud misconfigurations. The tools also identify excessive permissions and compliance violations in real time.
- Integrate ASPM practices: Application security posture management extends visibility into software supply chains, CI/CD pipelines and third-party dependencies. By integrating ASPM tools into DevSecOps workflows, organizations can detect code-level vulnerabilities earlier.
- Automate exposure management: Automation centralizes visibility across assets and accelerates the identification and prioritization of high-risk exposures. Automated validation and remediation reduce manual workload, improve response consistency and ensure exposure data is continuously updated as environments evolve.
- Benchmark against peers: Regularly benchmarking cybersecurity posture maturity against industry peers provides valuable performance insights. It highlights strengths, uncovers weaknesses and fosters accountability across teams. Tracking maturity trends over time allows organizations to set measurable goals.
Boost your cybersecurity posture levels with Cymulate
In the Threat Exposure Validation Impact Report 2025 from Cymulate, 95% of security leaders say testing the threat prevention and detection capabilities of their security controls is important. A critical part of how organizations can ensure their capabilities are strong is through adhering to the methods of extended security posture management we’ve discussed across this guide.
The Cymulate Exposure Management Platform can help you reach your goals and improve your posture. Proving validated threats and providing automated remediation is more here than security posture management solutions alone can provide.
Features of the platform include:
- Validation made easy with automation and AI: Cymulate provides the best of adversarial exposure validation with automated offensive security testing to prove the current state of threat resilience. This is powered by breach and attack (BAS) and continuous automated red teaming (CART) technologies.
- Exposure prioritization to focus on the exploitable: Validated exposure scoring will stack rank exposures based on proof and evidence of threat prevention and/or threat detection.
- Optimize threat resilience with actionable and automated mitigation: Guided remediation, custom detection rules and an option for automated security control updates for immediate prevention of new threats are included.
- Evidence-based metrics of threat prevention and detection: Heatmaps of MITRE ATT&CK threat coverage and dashboards for executives, team leaders and control owners are critical tools for improving cybersecurity posture.
What differentiates Cymulate from the rest?
- Continuous threat validation with best-in-class exposure validation with a single platform to optimize controls, scale offensive testing and provide essential exposure insights.
- Simple automation with advanced testing for any blue or red teamer to run and customize with templates, best practices and AI assistant to scale offensive testing.
- Put the T in Continuous Threat Exposure Management (CTEM) and make threat validation a continuous process with collaboration across security operations, threat intel and vulnerability management teams.
Book a demo today to discover how the Cymulate Exposure Management Platform can help your organization strengthen its cybersecurity posture.
Frequently asked questions
A security posture assessment is a structured evaluation of an organization’s security readiness, resilience and maturity. It identifies vulnerabilities, measures control effectiveness and benchmarks overall risk exposure against best practices and compliance standards.
During an assessment, teams catalog assets, test security controls and map findings to frameworks like NIST or ISO. The outcome provides a measurable baseline and a roadmap for continuous improvement.
You should perform a cybersecurity posture assessment at least annually, but quarterly or continuous validation is recommended for dynamic, hybrid environments. The faster you attack surface changes, the more frequent assessments should be.
Regular assessments detect posture drift early and prevent configuration or control gaps from growing into exploitable weaknesses. Automation helps maintain ongoing assurance without disrupting daily operations.
Cybersecurity posture measures your current defensive strength and readiness, while cybersecurity maturity reflects how advanced and optimized your security processes are. Posture is the “snapshot,” maturity is the “progress curve.”
Mature organizations have advanced visibility, automation and validation processes that sustain strong posture over time. Maturity drives continuous posture optimization through data-driven decision-making.
Automation enhances enterprise cybersecurity posture management by enabling continuous monitoring, faster remediation and real-time exposure validation. It eliminates manual effort and ensures consistency across complex hybrid environments.
Automated platforms detect posture drift, validate controls and streamline compliance reporting. The result is a dynamic, self-improving defense system that scales with evolving threats.