Security administrators, responders, and threat hunters are constantly required to tune their endpoint detection and response (EDR) solution to detect and prevent the latest attack tactics and techniques being employed by threat actors across the globe.
In a race against time, where adversaries can gain access to a network and achieve lateral movement in just over an hour (average of 62 minutes for eCrime threat actors according to the CrowdStrike 2024 Global Threat Report), accelerating defensive actions to detect threats is critical to avoid becoming their next breach victim.
The Cymulate platform provides a comprehensive assessment of endpoint security controls against thousands of signature-based and behavior-based attack scenarios. These attack simulations cover a broad range of the latest malware, ransomware, worms, trojans, and rootkits that threat actors use to gain access and control of endpoint devices. The assessment also provides attack scenarios for other threat activities including DLL side-loading and malicious code injection.
Identifying Endpoint Security Weaknesses
Once the endpoint security assessment has completed, security teams analyze the findings to identify simulated attack scenarios that were not detected or not prevented by their EDR solution.
These attack scenarios highlight potential weaknesses in endpoint security controls that will require security admins to configure and fine-tune their EDR systems with the right detection rules to detect an actual “real” attack.
As with most things in the world of cybersecurity, time is of the essence. Given the speed at which threat actors can break out across a network, the sooner new detection rules can be configured into an EDR system the better.
Accelerating Defensive Actions with EDR Mitigation Rules
To help accelerate the implementation of mitigation actions, the Cymulate platform goes beyond simply notifying security teams that they have a weakness in their endpoint security controls.
The Cymulate platform informs security administrators of actions they should take to improve detections in the form of generic EDR mitigation rules. These generic rules provide the guidance needed for a security admin to create new detection rules in their EDR system to detect those types of attacks they are currently missing.
For each of the test scenarios in the endpoint security assessment findings, we provide security admins with EDR mitigation rules written using our generic security detection query language.
Leveraging Security Detection Rules
Cymulate has established a generic security detection query language to write generic EDR mitigation rules that help security admins understand how to engineer detection rules in their EDR solution to detect certain types of attacks.
The versatility of these rules means they can be adapted to fit any EDR solution, albeit with some translation due to variations in terminology across different EDR platforms.
The mitigation rules include the necessary fields and values that will be required to codify a new detection rule in an EDR system. The generic query language includes the following fields:
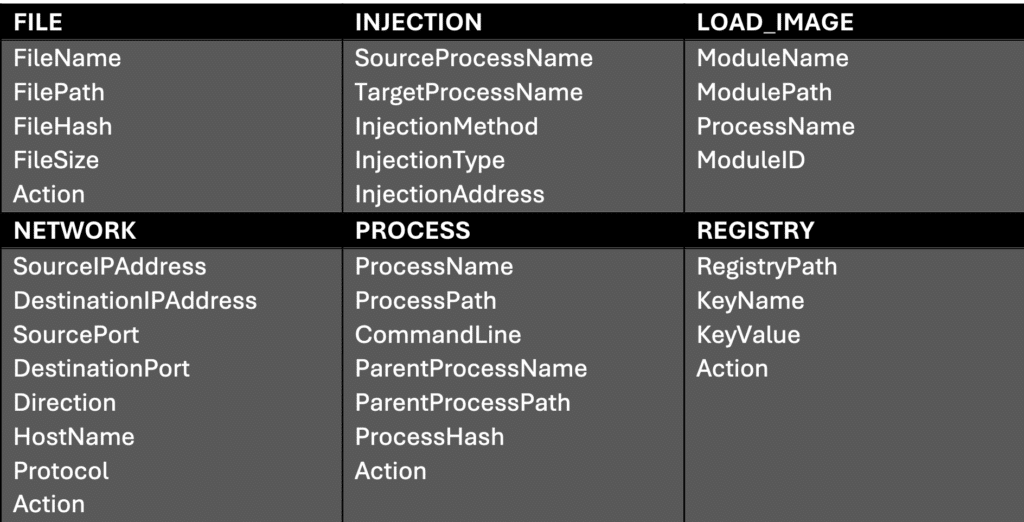
Translating EDR Mitigation Rules
Security administrators can take EDR mitigation rules from the findings overview in the Cymulate platform and translate them to the specific syntax required for their EDR system.
Each rule is assigned an accuracy level (very low, low, medium, high and very high), that indicates the potential for the rule to generate false positives in the EDR system.
Security admins should use the accuracy level as a guide to determine if further customization of the rule is required to effectively detect an attack. Security admins with the right knowledge may also use the detection rule as the basis for creating a prevention rule to block the attack, although we recommend you proceed with caution here. Start with a detection rule and monitor the detections for false positives before considering creating a prevention rule. This approach is crucial for ensuring that the rules effectively enhance detection and prevention capabilities without overwhelming the EDR system with false positives.
Example Detection Rule
Consider the following example of an EDR mitigation rule to see how the rule would easily translate into a detection rule for an EDR system.
After running an endpoint security assessment and simulating a malicious attack, we see in the findings overview that the endpoint security control was unable to prevent (or even detect) the malicious behavior.
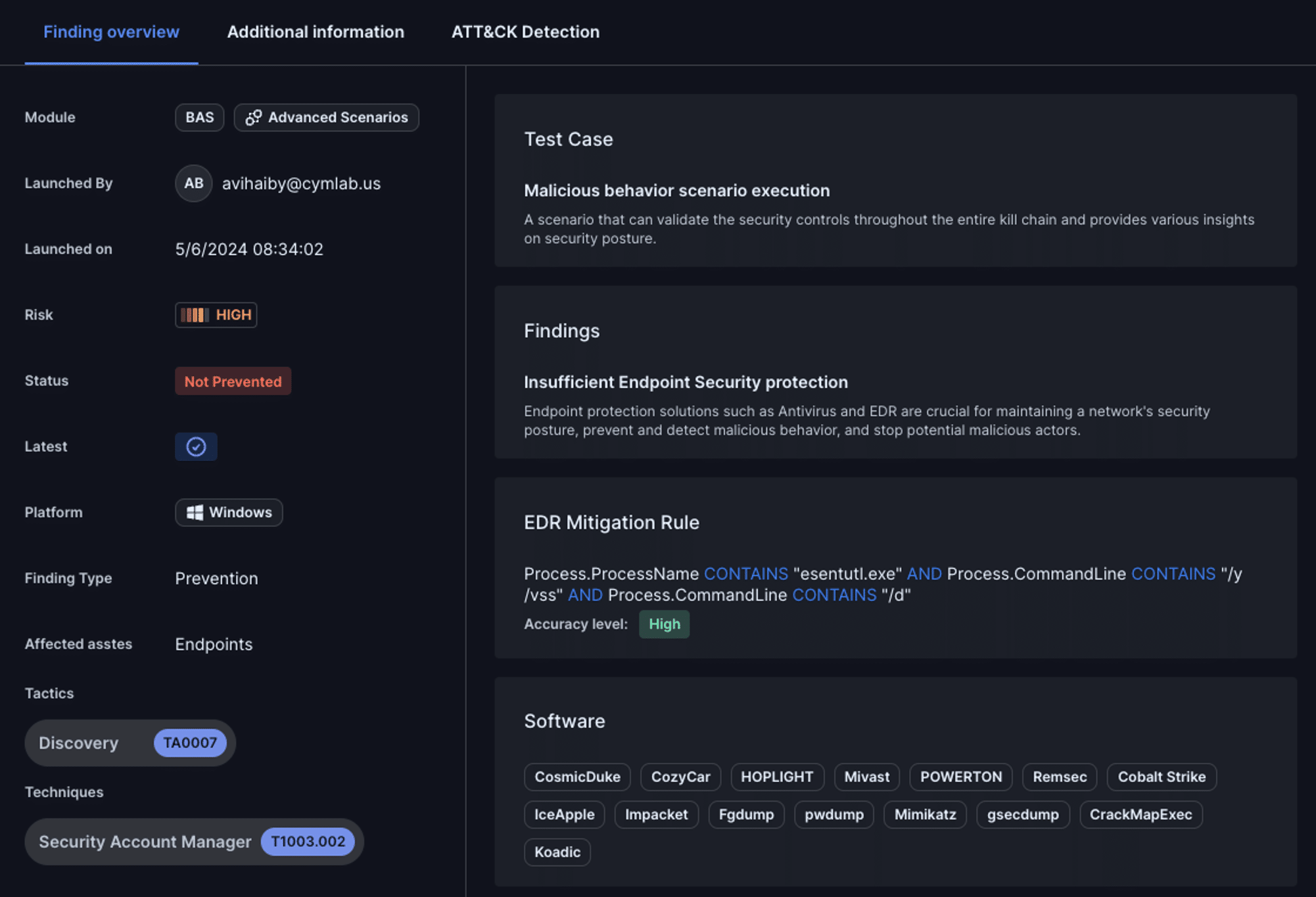
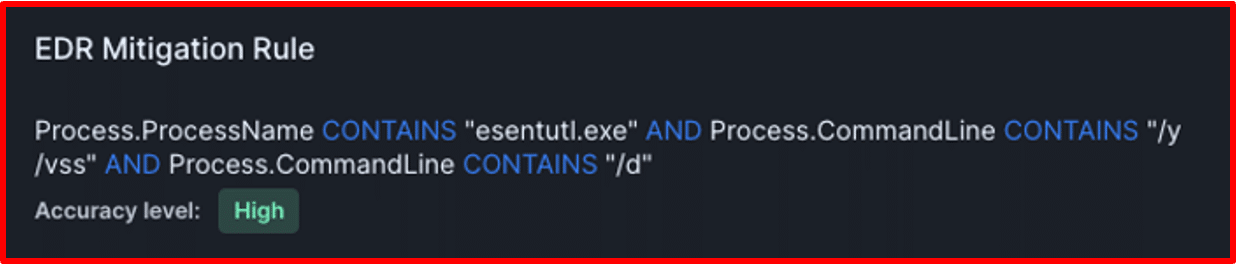
EDR Mitigation Rules are Strategic Assets to Accelerate Defensive Actions
Cymulate EDR mitigation rules are a strategic asset offered by the Cymulate platform. The generically coded rules help organizations accelerate the implementation of risk mitigation actions, enabling them to be more cyber resilient in detecting attacks on their endpoints.
For more information, you can schedule a demo to see how our endpoint security assessments can validate the efficacy of your endpoint security controls and how our EDR mitigation rules can help you configure new detection rules in your EDR system.











