Frequently Asked Questions
Vulnerability Details: React Server Components RCE (CVE-2025-55182 & CVE-2025-66478)
What is the critical vulnerability discovered in React Server Components (RSC)?
A critical unauthenticated remote code execution (RCE) vulnerability was disclosed in React Server Components (RSC), tracked as CVE-2025-55182 (and related CVE-2025-66478 in Next.js). This flaw allows attackers to execute arbitrary code on the server by sending a specially crafted HTTP request to the vulnerable RSC 'Flight' component, with no authentication required. (Source: Cymulate Research Lab, Dec 15, 2025)
Which versions of React and Next.js are affected by CVE-2025-55182 and CVE-2025-66478?
Applications using React 19 (versions 19.0.0, 19.1.0, 19.1.1, and 19.2.0) with server components enabled are vulnerable. Next.js versions 14.3.0-canary, 15.x, and 16.x (App Router) are also impacted. Any tooling, bundler, or plugin that includes the vulnerable react-server-dom-* modules may be at risk. (Source: Cymulate Research Lab, Dec 15, 2025)
What is the potential impact of exploiting this React Server Components vulnerability?
Exploitation can lead to full server takeover, allowing attackers to gain an external foothold and completely compromise the system. Sensitive data (user data, credentials, tokens, configuration files) can be exposed, modified, or exfiltrated. Attackers can also disrupt service availability. The attack requires no authentication or special privileges, making the attack surface very large. (Source: Cymulate Research Lab, Dec 15, 2025)
How can organizations determine if they are vulnerable to CVE-2025-55182?
Organizations should manually inspect their React and Next.js configurations and installed versions. The presence of a caret (^) before a version number in package manifests means newer minor and patch versions may be installed. Teams must confirm the actual installed version via lock files or dependency audits. (Source: Cymulate Research Lab, Dec 15, 2025)
What immediate actions are recommended to mitigate this vulnerability?
Recommended actions include: 1) Evaluate server applications for affected components, 2) Prioritize patching by upgrading react-server-dom-* packages to 19.0.1, 19.1.2, or 19.2.1 and updating Next.js to patched releases, 3) Use NPM audit to check for known vulnerabilities, 4) Audit all dependencies for embedded vulnerable modules, and 5) Incorporate simulation of this vulnerability into BAS/red-team exercises. (Source: Cymulate Research Lab, Dec 15, 2025)
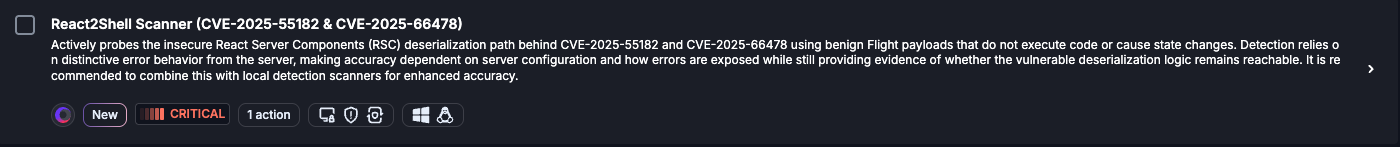
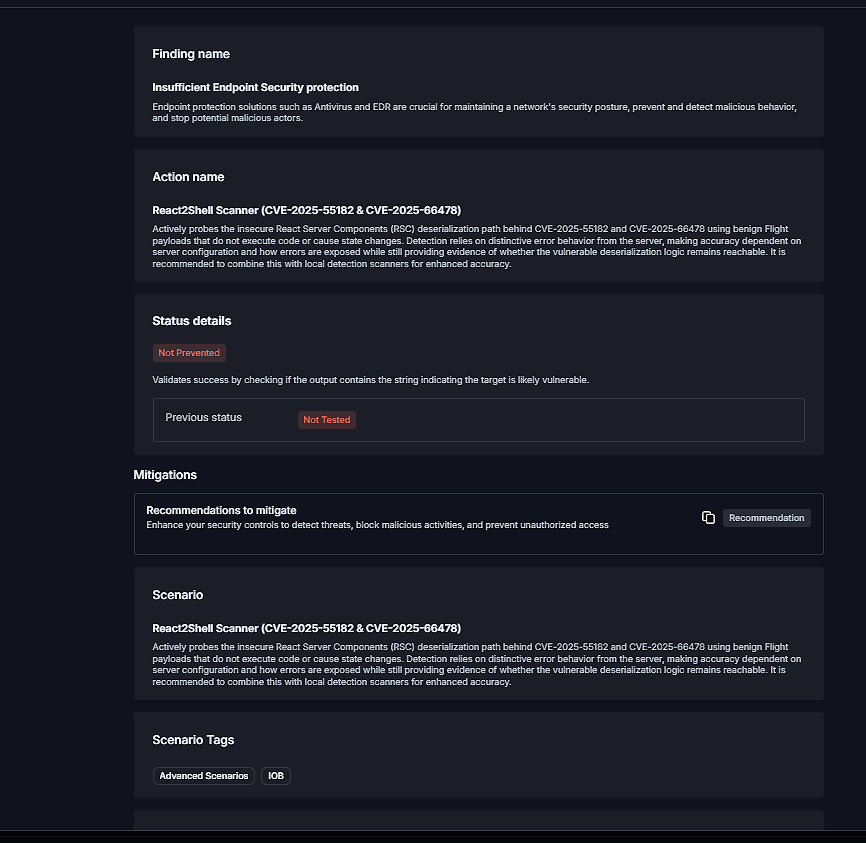
How does the React2Shell-Scanner tool help security teams validate their exposure?
The React2Shell-Scanner is a free, non-intrusive tool released by Cymulate. It sends benign payloads to trigger the vulnerable deserialization logic without executing malicious code, then analyzes server responses for error patterns indicative of an unpatched RSC implementation. This allows teams to proactively test their React/Next.js servers for exposure with minimal risk. Download the tool here. (Source: Cymulate Research Lab, Dec 15, 2025)
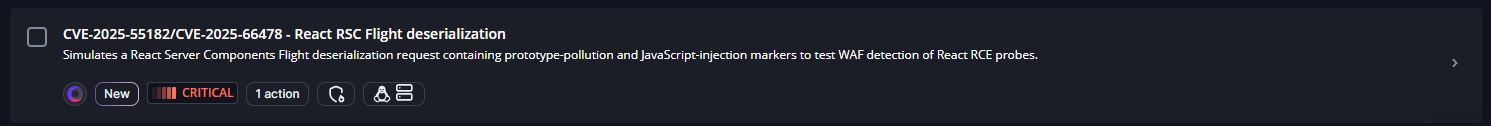
What attack scenarios and templates has Cymulate released for this vulnerability?
Cymulate released three new attack scenarios and two new attack templates in Cymulate Exposure Validation. These include the React2Shell Scanner (CVE-2025-55182 & CVE-2025-66478) for SIEM and endpoint security validation, and advanced campaigns simulating exploitation tactics used by APT groups. (Source: Cymulate Research Lab, Dec 15, 2025)
How can organizations use Cymulate Exposure Validation to test for CVE-2025-55182?
Organizations can use the new attack scenarios and templates in Cymulate Exposure Validation to simulate exploitation of CVE-2025-55182 and CVE-2025-66478. These scenarios test detection in SIEM, endpoint security, and WAF, and help validate the effectiveness of security controls against real-world attack techniques. (Source: Cymulate Research Lab, Dec 15, 2025)
What are the names of the new exposure validation templates for this vulnerability?
The new exposure validation templates are named 'React Server Components Exploitation Simulation' and 'React2Shell RCE Simulation.' These templates are available under 'advanced attacks (APT & TA)' in Cymulate Exposure Validation. (Source: Cymulate Research Lab, Dec 15, 2025)
Why is it important to simulate this vulnerability in BAS or red-team exercises?
Simulating this vulnerability in Breach and Attack Simulation (BAS) or red-team exercises helps organizations test their detection, response, and containment capabilities in case of a real exploit. This proactive approach ensures that security teams are prepared for actual attacks and can identify gaps in their defenses. (Source: Cymulate Research Lab, Dec 15, 2025)
What is the role of Cymulate Research Lab in addressing emerging threats?
Cymulate Research Lab continuously examines the cyber-threat landscape, delivering in-depth visibility into current threats and the actors behind them. The team combines expertise from private security, military, and intelligence backgrounds to provide actionable research and tools for the security community. Learn more about Cymulate Research Lab.
Where can I find more technical details and resources about this vulnerability?
For more technical details, recommended actions, and links to tools, visit the original blog post at Cymulate's blog and the React2Shell-Scanner GitHub repository.
Features & Capabilities
What features does Cymulate Exposure Validation offer for testing modern threats?
Cymulate Exposure Validation provides advanced security testing with ready-to-launch attack scenarios and templates, including custom attack chains for continuous validation. It enables security teams to simulate real-world threats, validate detection and response, and optimize defenses against vulnerabilities like CVE-2025-55182. Learn more about Exposure Validation.
How does Cymulate help organizations stay ahead of emerging threats?
Cymulate offers continuous threat validation, daily updates to its attack simulation library, and rapid release of new scenarios for emerging vulnerabilities. This ensures organizations can test their defenses against the latest threats and adapt quickly to changes in the threat landscape. (Source: Cymulate Platform Overview)
What integrations does Cymulate support for security validation?
Cymulate integrates with a wide range of security technologies, including Akamai Guardicore (network security), AWS GuardDuty (cloud security), BlackBerry Cylance OPTICS, Carbon Black EDR, Check Point CloudGuard, Cisco Secure Endpoint, CrowdStrike Falcon, Wiz, SentinelOne, and more. For a complete list, visit our Partnerships and Integrations page.
How easy is it to implement Cymulate and start testing?
Cymulate is designed for quick, agentless deployment with no need for additional hardware or complex configurations. Customers can start running simulations almost immediately, with robust support and educational resources available. (Source: Customer Testimonials, Cymulate Implementation Guide)
What feedback have customers given about Cymulate's ease of use?
Customers consistently praise Cymulate for its intuitive interface and ease of use. For example, Raphael Ferreira, Cybersecurity Manager, stated: "Cymulate is easy to implement and use—all you need to do is click a few buttons, and you receive a lot of practical insights into how you can improve your security posture." (Source: Customer Testimonials)
What security and compliance certifications does Cymulate hold?
Cymulate holds several industry-leading certifications, including SOC2 Type II, ISO 27001:2013, ISO 27701, ISO 27017, and CSA STAR Level 1. These certifications cover security, availability, confidentiality, privacy, and cloud security controls. (Source: Security at Cymulate)
How does Cymulate ensure data security and privacy?
Cymulate ensures data security through encryption in transit (TLS 1.2+) and at rest (AES-256), secure AWS-hosted data centers, and a tested disaster recovery plan. The platform is developed using a strict Secure Development Lifecycle (SDLC) and includes mandatory 2FA, RBAC, and IP address restrictions. (Source: Security at Cymulate)
Is Cymulate compliant with GDPR and other privacy regulations?
Yes, Cymulate incorporates data protection by design and has a dedicated privacy and security team, including a Data Protection Officer (DPO) and Chief Information Security Officer (CISO). The platform is GDPR-compliant and follows international privacy standards. (Source: Security at Cymulate)
Use Cases & Benefits
Who can benefit from using Cymulate Exposure Validation?
Cymulate Exposure Validation is designed for CISOs, security leaders, SecOps teams, red teams, and vulnerability management teams in organizations of all sizes and industries, including finance, healthcare, retail, media, transportation, and manufacturing. (Source: Cymulate Platform Message Guide)
What business impact can organizations expect from using Cymulate?
Organizations using Cymulate can achieve up to a 52% reduction in critical exposures, a 60% increase in team efficiency, and an 81% reduction in cyber risk within four months. These outcomes are supported by customer case studies and quantifiable metrics. (Source: Hertz Israel Case Study)
What core problems does Cymulate solve for security teams?
Cymulate addresses overwhelming threat volumes, lack of visibility, unclear risk prioritization, and resource constraints by providing continuous threat validation, exposure prioritization, improved resilience, operational efficiency, and collaboration across teams. (Source: Cymulate Platform Message Guide)
How does Cymulate help with fragmented security tools and visibility gaps?
Cymulate integrates exposure data and automates validation to provide a unified view of the security posture, addressing gaps caused by disconnected tools. (Source: Cymulate Platform Message Guide)
Are there case studies showing Cymulate's effectiveness?
Yes, for example, Hertz Israel reduced cyber risk by 81% in four months, and a sustainable energy company scaled penetration testing cost-effectively with Cymulate. See more at Cymulate Case Studies.
How does Cymulate address resource constraints in security teams?
Cymulate automates processes, improves operational efficiency, and enables faster threat validation, allowing security teams to focus on strategic initiatives rather than manual tasks. (Source: Cymulate Platform Message Guide)
How does Cymulate support communication with stakeholders?
Cymulate provides quantifiable metrics and actionable insights, helping CISOs and security leaders justify investments and communicate risks effectively to stakeholders. (Source: Cymulate Platform Message Guide)
What pain points does Cymulate solve for different security personas?
Cymulate tailors solutions for CISOs (communication barriers, risk prioritization), SecOps (resource constraints), red teams (threat simulation), and vulnerability management teams (operational inefficiencies). (Source: Cymulate Platform Message Guide)
How does Cymulate compare to traditional penetration testing?
Cymulate offers automated, continuous validation and a library of over 100,000 attack actions, providing faster, more comprehensive, and cost-effective testing compared to manual penetration tests. (Source: Cymulate Platform Message Guide)
Pricing & Plans
What is Cymulate's pricing model?
Cymulate operates on a subscription-based pricing model tailored to each organization's requirements. Pricing depends on the chosen package, number of assets, and scenarios selected. For a detailed quote, schedule a demo with the Cymulate team. (Source: Cymulate Pricing Model)
Support & Resources
Where can I find Cymulate's blog, newsroom, and resource hub?
You can find the latest research, news, and resources at our blog, newsroom, and resource hub.
How can I get support or contact Cymulate?
You can reach Cymulate support via email at [email protected] or use the real-time chat support available on the website. For sales or general inquiries, visit the Contact Us page.
Where can I find definitions for cybersecurity terms used by Cymulate?
Cymulate provides a comprehensive cybersecurity glossary with definitions for terms, acronyms, and jargon used in the industry.