December 2nd, 2024
Under the EDR Radar: A Deep Dive into Binary Exploitation
August 15th, 2024
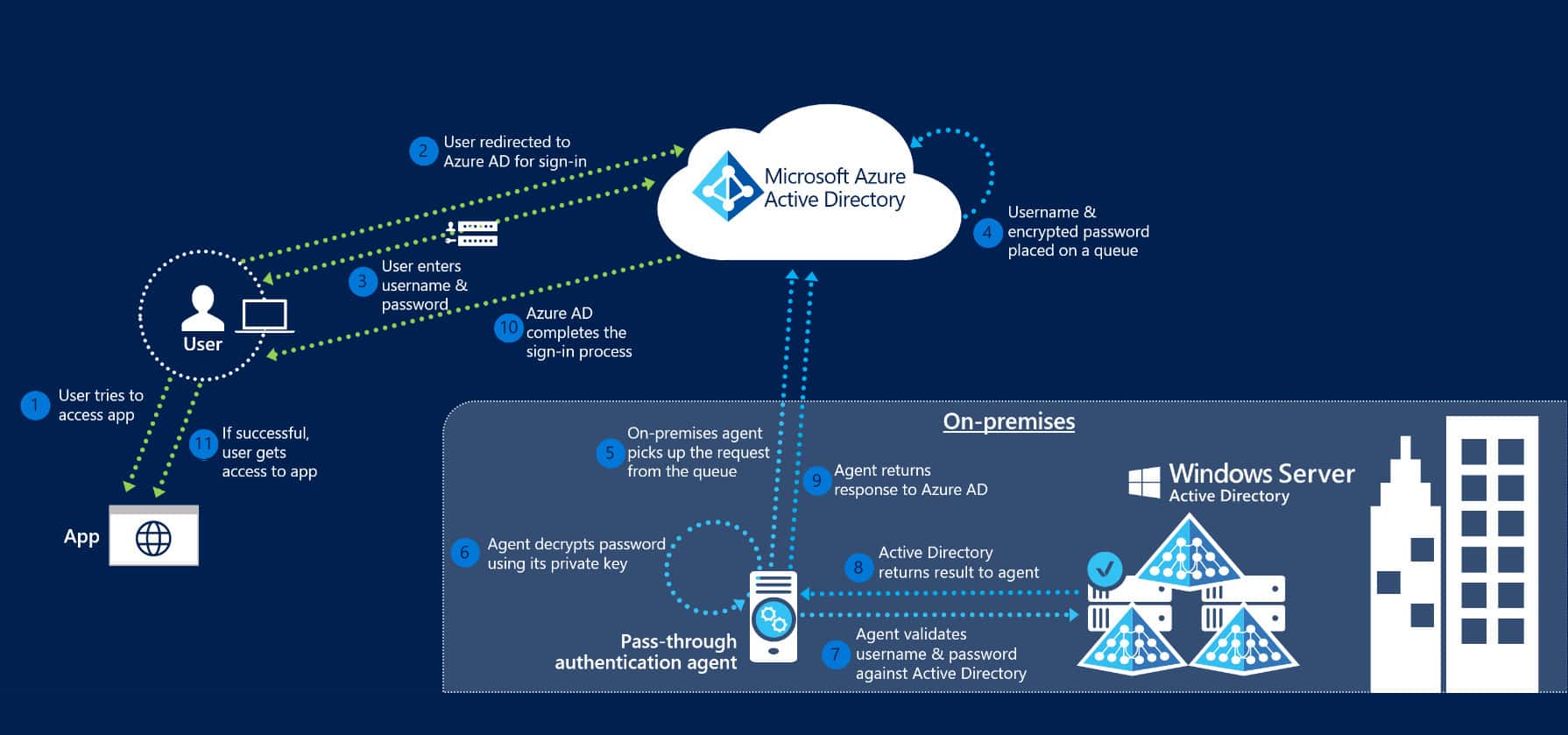
Double Agent: Exploiting Pass-through Authentication Credential Validation in Azure AD

February 14th, 2024
How Attackers Bypass EDR: Techniques & Defense Strategies

February 8th, 2024
Understanding Endpoint Defense: EDR, XDR, and Anti-Virus Explained

February 1st, 2024






