What is Cyber Asset Attack Surface Management (CAASM)?
Cyber Asset Attack Surface Management (CAASM) is an security practice that gives organizations a unified, real-time view of all their digital assets, internal and external, in order to manage risk exposures proactively.
CAASM bridges the gap between traditional IT asset management and modern security needs by aggregating data across all assets and security tools into one consolidated inventory.
This visibility is crucial in dynamic IT environments, where cloud services, remote work, and shadow IT have expanded the attack surface beyond what conventional asset inventories can handle.
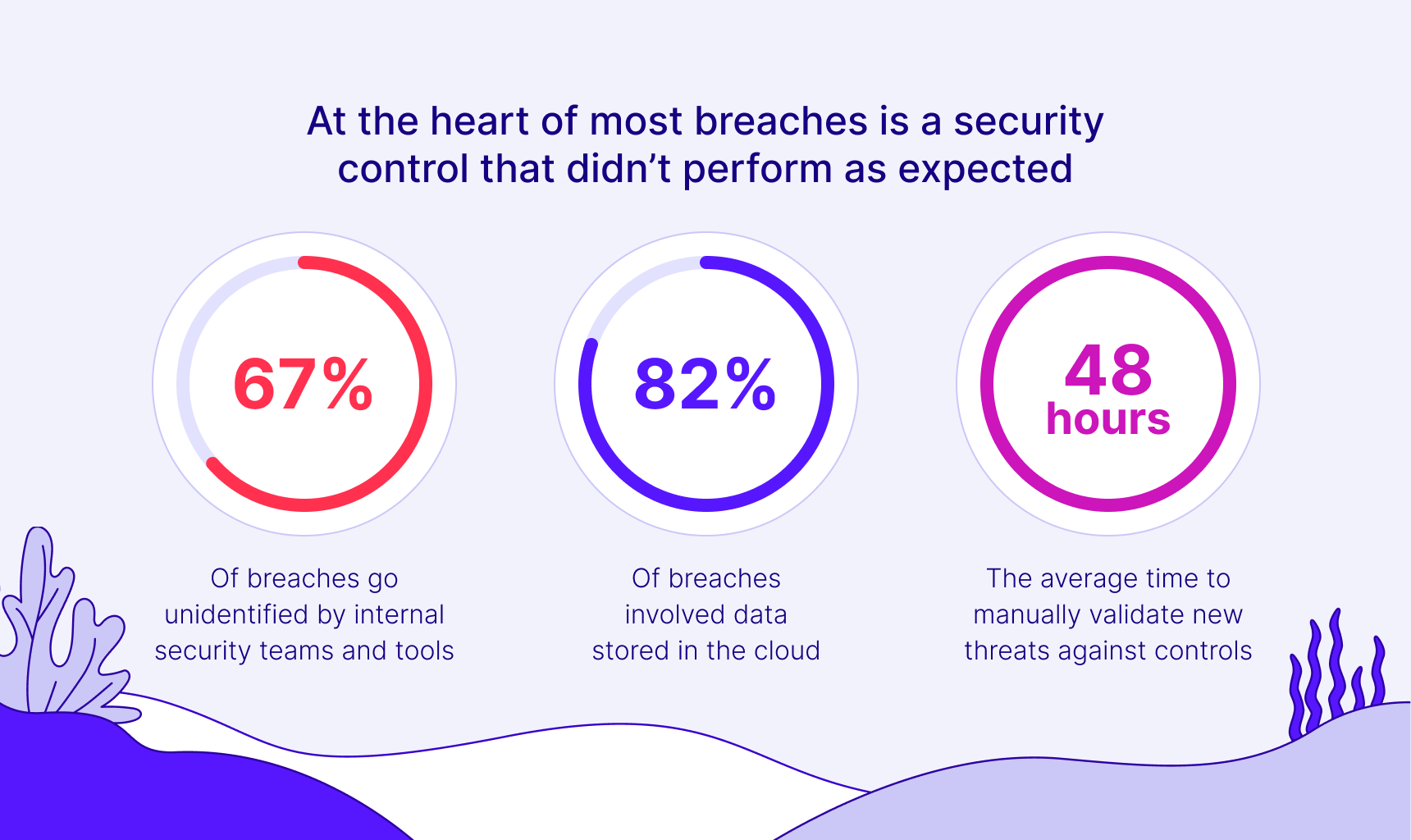
The importance of CAASM has grown as organizations recognize their visibility gaps: nearly half of security professionals admit they lack visibility into all users, devices, applications, and services on their networks.
Some estimates even suggest many enterprises can only see about 60-70% of their IT assets with legacy approaches. Such blind spots translate to security gaps. CAASM matters now because it addresses this visibility deficit, helping security teams identify unknown or unmanaged assets and close coverage gaps.
What Exactly is CAASM?
Cyber Asset Attack Surface Management (CAASM) is a technology and methodology for achieving comprehensive asset visibility and security insight across an organization’s entire IT environment. It compiles and analyzes data from disparate sources, including on-premise devices, cloud resources, software applications, user accounts, and more, to give security teams a 360-degree view of their attack surface.
CAASM emerged to fill a critical gap between external attack surface management (EASM) and internal asset management systems.
Traditional IT asset management tools (like CMDBs) maintain inventories for purposes like tracking hardware/software lifecycles or financial management, but they often lack the security context (vulnerabilities, threats, control status) that security teams need.
On the other side, External Attack Surface Management tools focus on discovering internet-facing assets from an outsider perspective, but ignore internal infrastructure. CAASM was conceived as a bridge between these: it leverages the data from existing IT and security tools to present one consolidated, queryable asset inventory tailored for security use cases.
According to Gartner’s definition, CAASM solutions use API integrations to collect asset data from sources like configuration databases, vulnerability scanners, endpoint agents, cloud platforms, identity management systems, and more, then normalize and deduplicate that data into a single view of “all assets” across internal and external environments.
This comprehensive inventory becomes the foundation for security analysis: the CAASM platform can then identify missing assets, uncover discrepancies (e.g. an asset known to one system but invisible to another), and highlight vulnerabilities or misconfigurations associated with each asset.
Why CAASM Matters
Implementing CAASM has become a priority because traditional asset management and vulnerability management approaches struggle to keep up with modern challenges.
Distributed IT Assets
One major challenge is the dynamic, distributed nature of IT assets. With the rise of multi-cloud infrastructure, BYOD and remote work, IoT and OT devices, and third-party SaaS adoption, the inventory of assets to protect is constantly growing and changing.
Legacy asset inventories (often spreadsheets or static CMDB entries) are frequently out-of-date almost as soon as they’re created.
This leads to security teams making decisions based on incomplete data, leaving unknown assets (“shadow IT”) unmonitored and unpatched. It’s no surprise that unknown or unmanaged assets are a common source of security incidents.
For example, an abandoned cloud server or an employee’s personal device could be missed by vulnerability scans and become an easy entry point for attackers. CAASM directly addresses this by continuously aggregating and updating asset information from all corners of the environment, so nothing falls through the cracks.
Security Tool Coverage Gaps
Another reason CAASM matters is the elimination of security tool coverage gaps. Enterprises typically use dozens of security tools (EDR, anti-malware, cloud security, DLP, etc.), and not every asset is covered by every tool. A fundamental CAASM use case is to quickly answer questions like: “Do we have any devices that are not enrolled in our endpoint protection?” or “Which cloud databases lack encryption or backups?”
Without CAASM, getting these answers might require manually correlating data from multiple dashboards. CAASM solutions let you query the unified asset dataset to find such gaps instantly. This helps reveal misalignments (e.g. a server that the IT inventory shows as active but doesn’t appear in patch management logs, indicating it’s not being updated).
Identifying these blind spots significantly reduces risk because it directs attention to assets that would otherwise be overlooked. In fact, 47% of security professionals report lacking full visibility into their assets and users, highlighting how common these blind spots are. CAASM brings those blind spots into the light.
Core Capabilities of CAASM Solutions
To achieve its goals, a CAASM solution offers several core capabilities and features that set it apart from standard asset management or scanning tools. Key capabilities include:
Data Aggregation from Existing Tools
CAASM platforms integrate via APIs with the myriad tools and databases an organization already uses, such as CMDBs, cloud management consoles, vulnerability scanners, EDR agents, identity/IAM systems, network inventories, ticketing systems, etc, and pull in asset data from all these sources into one place.
This often involves normalizing different data formats and reconciling records (e.g. merging an asset’s info from CMDB with data from a scanner). The result is a comprehensive, automated asset inventory without manual data entry.
Comprehensive Asset Visibility (Including Shadow IT)
CAASM tools provide a unified view of “every asset”, from on-prem servers and IoT devices to cloud VMs and containers, to SaaS accounts, including assets that may be unmanaged or not officially approved (shadow IT).
This broad visibility ensures that even rogue assets or forgotten systems are brought to attention. For instance, a CAASM solution might flag an unknown device on the network or an unregistered cloud instance that was spun up outside of IT’s knowledge.
Queryable, Living Inventory
Unlike static spreadsheets, CAASM maintains a living inventory that is continuously updated and can be queried in real time. Security teams can ask complex questions by searching the inventory (often via a query language or simple filters).
For example, one can query “show all Windows servers missing EDR agent” or “list all databases containing sensitive data that are exposed to the internet.” The CAASM tool will return results by correlating data from its aggregated sources.
This ability to query assets and get immediate answers greatly accelerates tasks like incident investigation, audit preparation, or exposure analysis.
Identify Security Gaps and Discrepancies
A fundamental capability is automatically finding where there are gaps in security controls or inconsistent configurations. CAASM will cross-reference data to spot issues such as devices that aren’t being scanned by vulnerability tools, or software that is installed but not in the patch management system.
It can also highlight discrepancy between sources (e.g. an asset in Active Directory that’s not in the CMDB, indicating inventory drift). By alerting on these findings, CAASM helps remediate coverage gaps before an attacker can take advantage.
Vulnerability and Risk Context
Most CAASM solutions ingest vulnerability scan results and link them to asset records. They often integrate with CVE databases or threat intelligence to add context.
This enables the platform to prioritize vulnerabilities based on asset context, for example, a critical vulnerability on a public-facing server is flagged as higher risk than the same on an isolated workstation.
Some CAASM tools incorporate risk scoring (EPSS, CVSS, etc.) to sort assets by risk level. The end goal is to not just list assets, but help security teams focus on the most exposed or critical ones.
Continuous Monitoring & Alerting
CAASM isn’t a one-time inventory; it continuously monitors for changes. New asset discovered? It gets added and an alert can notify the team. Software patch released? The platform can note which assets are now unpatched.
This continuous monitoring means the attack surface map stays up-to-date as the environment evolves. Alerts or dashboards can inform teams of significant changes (e.g. a new server appears without any security tool installed on it). This real-time awareness is essential for prompt risk mitigation.
Reporting and Compliance Support
Because CAASM maintains a historical record of assets and security metrics, it can generate reports needed for audits or compliance. For example, it can provide an audit trail of assets and their security controls to demonstrate adherence to frameworks like SOC 2, PCI DSS, or internal policies.
Security teams can quickly produce evidence like “all critical systems are being scanned for vulns and backed up” or identify compliance gaps if any exist. This not only eases audit preparation but also strengthens overall governance of asset security.
CAASM vs. EASM (How It Differs from External ASM)
| Aspect | CAASM (Internal & External) | EASM (External-Facing Only) |
| Scope | All cyber assets (internal and external), e.g. endpoints, servers, cloud instances, apps, user accounts. | External-facing assets (public websites, IPs, domains, cloud services, APIs, etc.). |
| Approach | Aggregates data via API from internal tools (CMDB, EDR, vuln scanner, IAM, etc.) to build a consolidated inventory. Passive data collection and correlation. | Actively discovers assets via internet scanning, DNS querying, web crawling, etc., from an attacker’s outside perspective. |
| Primary Purpose | Unified asset visibility and security context for all assets; identify internal coverage gaps, correlate vulnerabilities, query inventory for risk management. | Discover unknown exposures and shadow IT; provide an “outside-in” view of what an attacker sees, find externally visible vulnerabilities. |
| Key Benefit | Comprehensive, single source of truth for enterprise asset risk. Enables internal teams to prioritize and remediate issues on any asset (internal or external) with full context. | Uncovers assets and weaknesses that might be unaccounted for by internal inventories. Serves as an early warning for exposed infrastructure and misconfigurations on the perimeter. |
| Dependency | Depends on existing internal data sources (does not replace CMDB, etc., but builds on them), thus adoption is tied to integrating with current tools. | Operates independently of internal systems, discovers assets even if you have no prior record of them. Generally easier to deploy (no integrations needed), often offered as a service. |
(As shown above, CAASM and EASM address different angles of attack surface management. They work best in tandem: EASM finds and feeds unknown external asset data into the security program, while CAASM consolidates all asset data (internal + external) and drives remediation and risk reduction across the board.)
It’s important to distinguish Cyber Asset Attack Surface Management (CAASM) from External Attack Surface Management (EASM), as these terms target different facets of exposure management.
In fact, CAASM and EASM are complementary, not competing approaches, each addressing a different perspective of an organization’s attack surface. Here’s a clear comparison of CAASM vs EASM:
Scope of Assets
CAASM covers the entire spectrum of assets both internal and external, pulling from internal data sources to include on-premises IT assets, cloud instances, endpoints, user accounts, applications, etc.
By contrast, EASM focuses solely on external-facing assets, those that are visible to an outside attacker.
EASM finds things like your public websites, domains, cloud services, IP addresses, exposed APIs, certificates, and so on, essentially anything an adversary could discover via internet scanning.
In short: EASM provides an “outside-in” view of your attack surface, whereas CAASM provides a 360° internal+external view (with a heavy emphasis on internal asset details).
Approach and Data Sources
CAASM is largely a data aggregation and correlation solution, it passively collects information via API from tools you already use (CMDB, cloud APIs, security tools, etc.) and compiles it into a unified asset inventory.
EASM, on the other hand, is more of an active discovery process, it uses external scanners, web crawlers, and other reconnaissance techniques to discover unknown assets from the outside.
An EASM service might scan IP ranges for your company to find an unregistered server or check DNS records for forgotten subdomains. EASM does not rely on your internal databases; it reveals what an attacker could find without inside knowledge. CAASM may ingest EASM findings as one of its data feeds, combining that outside view with internal records.
Primary Use Cases
EASM excels at uncovering “shadow” assets and exposures that exist beyond the firewall, e.g. an old website or a misconfigured cloud storage bucket left open.
It’s about discovering and reducing unknown external risks. CAASM’s use cases are broader internally: it helps find security coverage gaps, ensures policy compliance on assets, and gives full asset context for risk prioritization.
In practice, organizations often use EASM to feed data into CAASM. For instance, if EASM finds an unknown public-facing asset, that information can be incorporated into the CAASM inventory so that internal teams can immediately see it, tag it, and bring it under management
Output and Value
CAASM produces a single source of truth for asset risk management, it answers questions like “Do we have asset X and is it secure?” by providing context (vulnerabilities, controls, ownership) on every asset.
EASM produces an attacker’s-eye view of your perimeter, highlighting what an outsider would see as your organization’s attack surface.
One way to look at it: EASM is about discovering assets (especially those you didn’t know existed), while CAASM is about managing assets (ensuring all known assets are accounted for, secure, and prioritized appropriately).
Both together give a complete picture, EASM finds the unknowns; CAASM aggregates all knowns (plus those discoveries) and drives remediation.
7 Common Use Cases for CAASM
CAASM capabilities translate into practical use cases that help security teams address daily challenges. Some common ones include:
1. Shadow IT Discovery
One of the immediate wins from CAASM is uncovering assets unknown to IT or security. Its aggregated inventory can reveal shadow IT, e.g., unmanaged servers, unauthorized cloud databases, or personal devices, that would otherwise go unnoticed.
For instance, if an employee launches a SaaS app without approval, CAASM (with EASM data) can correlate login or network activity and trigger an investigation.
2. Attack Surface Analysis & Risk Mapping
CAASM helps map your attack surface, letting teams identify exposed assets and assess threats. For example, it can show how many assets are internet-facing or have critical vulnerabilities.
With its unified view and vulnerability data, security teams can ask, “Which assets are most at risk?” or “What attack paths exist?”, enabling prioritization of defenses.
3. Security Control Coverage & Gap Analysis
A key use case is ensuring all assets are protected by proper security controls. CAASM can quickly identify devices missing endpoint protection, lacking patches, or misconfigured (e.g., open RDP ports, unencrypted databases).
This gap analysis improves security hygiene and supports ongoing monitoring for drift, enforcing consistent security policies.
4. Compliance and Audit Readiness
CAASM automates asset tracking and control verification, critical for regulations like PCI DSS, HIPAA, and ISO 27001. It provides an audit-ready inventory with evidence of controls (e.g., encryption, vulnerability scans).
Security teams can instantly generate reports showing assets, owners, and protection measures, saving time during audits and internal reviews.
5. Incident Response & Breach Investigation Support
During incidents, CAASM speeds up triage. Analysts can instantly look up an affected asset, what it is, who owns it, software installed, known vulnerabilities, or missing patches. It also maps relationships between systems to trace lateral movement paths.
CAASM acts as a forensic asset database, improving the speed and accuracy of containment and remediation.
6. Third-Party Risk Management
Organizations can extend CAASM to track third-party assets (e.g., vendor applications or services). Even if managed externally, CAASM helps monitor vulnerabilities or misconfigurations, improving supply chain visibility.
This supports vendor risk assessments and strengthens oversight of external dependencies.
7. Continuous Vulnerability Prioritization
CAASM enhances vulnerability management by connecting flaws to asset context. It helps prioritize fixes for crown jewel assets (like domain controllers or critical databases), or filter vulnerabilities by exposure (e.g., internet-facing).
Some CAASM tools integrate threat intelligence to highlight actively exploited flaws, leading to more efficient and risk-based remediation.
Cymulate’s Approach to CAASM
Unlike traditional CAASM tools focused on asset inventory, Cymulate brings an attacker’s perspective. Its Exposure Management Platform delivers CAASM in a threat-informed, exposure-centric way, prioritizing how assets could be exploited rather than just cataloging them. This aligns CAASM with continuous security validation.
Continuous Testing Through Attack Simulations
Cymulate integrates Breach and Attack Simulation (BAS) and automated red teaming into CAASM. Instead of just showing vulnerabilities, it actively tests them.
For instance, it might simulate credential theft or lateral movement on certain endpoints. If the simulation succeeds, it proves real-world exploitability, helping teams prioritize based on validated risk, not just theoretical CVEs.
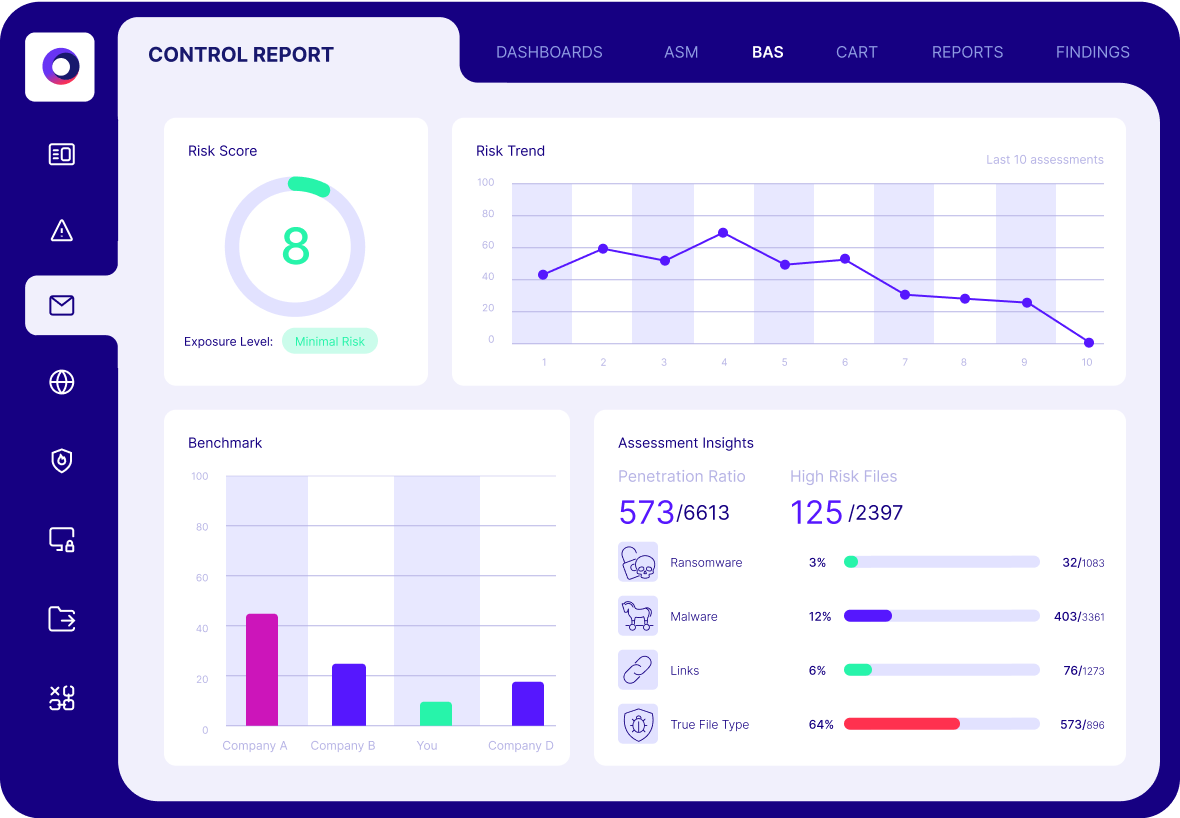
Risk-Based Prioritization with Business Context
Cymulate enhances CAASM by linking assets to business criticality and attack simulation results. Assets proven exploitable and important to the business are ranked highest, while low-impact issues are deprioritized. This approach surpasses basic severity scoring, ensuring mitigation efforts focus where they matter most.
Advanced Exposure Analytics
The platform’s Exposure Analytics module models real attack chains, such as privilege escalation or credential misuse, to uncover multi-step exposures.
It maps how attackers could move laterally from one foothold to others, showing how asset combinations (not just individual flaws) could lead to breaches.
Validation of Security Controls
Cymulate tests whether security controls (AV, EDR, firewall, DLP) are not just present but actually effective. Through simulations, it can confirm if controls detect or block real attacks. This ensures the CAASM inventory reflects not only tool deployment but true defense capability.
Automated Reporting and Integration
The platform generates automated reports showing trends in security posture (e.g., how many critical assets have exploitable flaws). It integrates with ITSM and ticketing systems to help operationalize remediation by opening tickets or suggesting fixes for exposed assets or weak controls.
Cymulate extends CAASM into what could be called “CAASM with continuous validation”. By adding the attacker’s lens, Cymulate transforms the CAASM process from a passive visibility exercise into an active, ongoing assessment of security readiness.
The unique strength of Cymulate’s approach is focusing on what’s exploitable, not just what’s visible. As Cymulate’s platform messaging puts it, it “filters out the noise, so you can focus on the exploitable”.
Benefits of CAASM with Exposure Validation
Combining CAASM with exposure validation (i.e., continuous testing of controls and exploitability) delivers significantly greater value than either approach alone. When layered together, organizations can achieve:
Real Risk Reduction (Not Just Visibility)
Standard CAASM provides visibility into assets and vulnerabilities. Adding exposure validation helps focus on truly exploitable risks, lowering the actual risk profile.
Instead of reacting to hundreds of minor issues, teams can prioritize the top 5% of assets proven exploitable via simulations. This targeted approach reduces successful attacks by closing the most dangerous gaps, transforming visibility into meaningful risk mitigation.
Proactive & Continuous Security Improvement
This combined approach enables a proactive security posture. As new assets or misconfigurations appear, they’re automatically tested and addressed.
This creates a feedback loop: CAASM finds issues, validation tests them, and security fixes them, before an incident occurs. Over time, the attack surface shrinks, and security evolves with the environment instead of reacting after breaches.
Faster Incident Response & Resilience
When incidents occur, CAASM with validation provides instant context. If a new critical vulnerability is disclosed, teams can quickly identify which assets are both affected and exploitable, based on previous tests.
This shortens response time and improves cyber resilience, since teams have rehearsed scenarios through simulated attacks and are prepared with accurate asset visibility.
Better Decision-Making for Security Investments
This approach provides measurable data on asset risk, control effectiveness, and exposure trends. CISOs can use this insight to prioritize investments, focus resources on high-risk areas, and track metrics like “mean time to remediate” or “percentage of assets without critical findings.” These metrics support stronger reporting and better alignment with business goals.
Operational Efficiency & Team Alignment
By unifying inventory, vulnerability data, and testing insights, CAASM improves coordination across IT, security, and risk teams. Everyone works from a shared, accurate source.
Automated queries and reports save time, while integrated workflows reduce friction. The result is higher productivity and better focus on strategic security tasks.
Key Takeaways
It solves the long-standing issue that “you can’t secure what you don’t know,” enabling defenders to identify blind spots that traditional tools miss.
Acting like the central nervous system of cybersecurity, CAASM continuously monitors the environment, helping teams pinpoint vulnerabilities and direct defensive efforts effectively in today’s expanding threat landscape.
The real value of CAASM is unlocked when combined with continuous exposure validation. This turns static asset data into actionable insights by identifying which assets are most exploitable.
Cymulate take this a step further by simulating attacks to test defenses, allowing teams to prioritize risk based on validated threat exposure. This proactive approach shifts security from reactive to preventive, enabling continuous improvement in an ever-evolving threat environment.



