What is Attack Surface Management (ASM)

Attack Surface Management (ASM) is the ongoing process of identifying, monitoring, and reducing potential points of entry that attackers (hackers) could exploit in a network or system. It helps organizations proactively address vulnerabilities and enhance their cybersecurity posture. The difference between ASM and asset discovery is that it adopts an attacker’s perspective to cover all exposed assets, including on the Internet and in discoverable assets in supply chains.
What is an Attack Surface?
An attack surface refers to the total sum of all possible points, such as software, hardware, web applications, physicals devices and so on where an unauthorized user (the "attacker") can try to enter or extract data. It encompasses all the vulnerabilities within a system that can be exploited to gain access to secure information or cause harm.
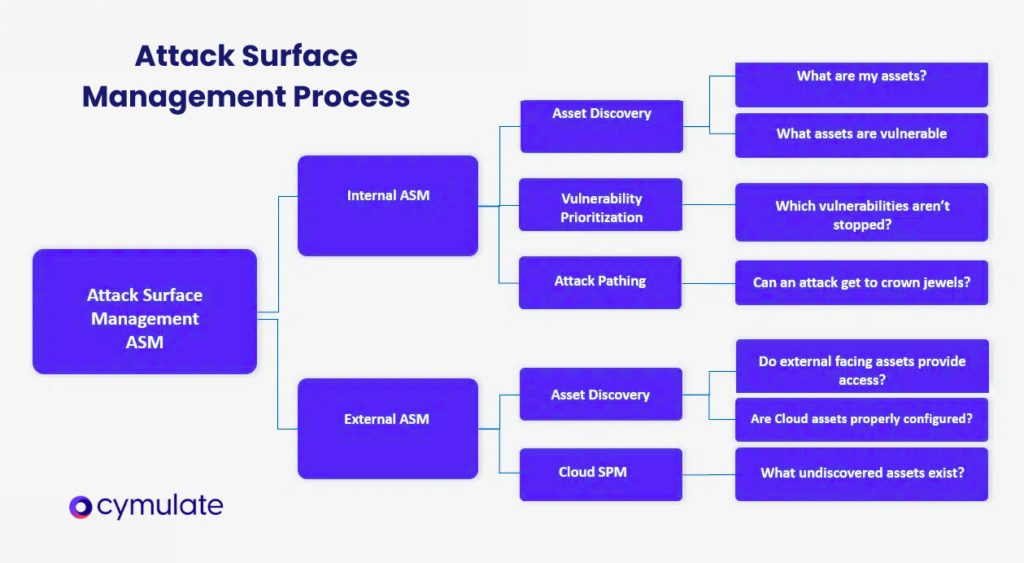
External attack surface management
External attack surface management (EASM) is a crucial aspect of attack surface management that helps organizations identify and mitigate risks associated with their external-facing assets, such as domains, IP ranges, websites, and cloud resources.
By continuously assessing these assets for vulnerabilities, an EASM solution, also known as an attack surface management solution, generates prioritized issues for the security team to remediate and reduce the external attack surface.
In addition to external attack surface management, internal attack surface management is also important for organizations seeking to move to the cloud and secure their digital infrastructure. However, external attack surface management specifically focuses on assets that are accessible from the public Internet, making it a vital component of a robust external attack surface management solution.
How does Attack Surface Management work?
The goal of ASM is to ensure that all assets, secure or insecure, known or unknown, are exhaustively listed and that the list is continuously updated so that asset monitoring can be comprehensive.
Exposed assets uncovered through ASM include:
- Shadow and orphaned IT – covers a wide range of data and practices, ranging from employees’ unapproved use of hardware or software to forgotten previous versions that have not been fully deactivated and could enable an intruder to gain an initial foothold.
- Active or inactive assets – Though classic asset discovery procedures rarely miss active assets, inactive ones might be forgotten in successive deployments
- Managed and unmanaged devices – including employee-owned vulnerable devices (BYOVD)
- Rogue assets – generated by malicious actors to impersonate your domains
- Hardware – including all devices, listed or unlisted, inherited through an M&A, email servers, data storage centers, and more
- Software – including unknown open-source software, public code repositories such as Github, APIs, web and mobile applications, and more
- SaaS-related and vendor-managed assets
- Leaked credentials
- Other
Many of these assets can appear anytime on the Internet and are completely ignored by traditional firewalls or EDR services. In other words, ASM discovers assets on the external asset surface typically ignored by defensive tool arrays.
Effective vulnerability management is crucial for protecting your organization from cyber threats. Attack surface management (ASM) provides a comprehensive approach to vulnerability management by automating asset discovery, risk assessment, and vulnerability assessment processes.
ASM tools analyze the attack surface in real-time, covering all of an organization’s assets beyond traditional security controls like mapping, firewall, and endpoint protection. To build an effective vulnerability management program, organizations need to understand their attack surface, prioritize remediation efforts, and build a robust inventory of assets, all of which are crucial for the success of security operations.
Why do you need Attack Surface Management (ASM)?
The combination of technological development, such as increased reliance on external services, abrupt societal change, such as the massive move to work from home during the COVID-19 pandemic, and the acceleration of the threat landscape expansion is creating a perfect mix for turning unknown assets into ticking cyber threat time bombs.
While security teams still often focus on reducing attack surfaces, without an adversarial-based discovery process such as ASM, the reduced surface fails to include unknown assets. On the other hand, cyber attackers have no qualms about using advanced reconnaissance tools that will uncover those overlooked exposed assets.
In today's ever-evolving cybersecurity landscape, it is crucial for organizations to adopt robust attack surface management (ASM) practices. While asset discovery procedures may effectively identify active assets, there remains a significant security risk associated with inactive assets, including cloud assets, that often go unnoticed during successive deployments. These forgotten assets can become vulnerable entry points for malicious actors, including IoT devices, which are increasingly being used in business environments. Therefore, understanding and implementing ASM is essential in mitigating these potential threats.
ASM goes beyond traditional asset management by encompassing both managed and unmanaged devices. This includes employee-owned devices brought into the workplace, also known as BYOD (Bring Your Own Device). Such devices can introduce additional security challenges if not properly monitored and secured.
Main functions of ASM tools
Robust ASM tools provide a full range of services that include:
- Discovery – the reconnaissance phase (AKA recon) during which the ASM tool impersonates attackers by scanning multiple sources for intelligence that could later be exploited, including domains and sub-domains (for application and infrastructure vulnerabilities, web misconfigurations, and open ports,) organizational, employee, and technical information that can be used in a social engineering attack or to gain illicit network access and initial foothold, and other exploitable intelligence that an attacker may take advantage of.
- Findings classification – there are different ways of classifying uncovered assets and the degree of severity of the exposure they generate. Cymulate’s ASM uses the following classification categories: Network-level – Firewall policies and “network-level” protocols findings
- Server level – Everything that can be considered infrastructure.
- Operating System, built-in administrative capabilities, HTTP servers such as IIS and Apache
- Service level – Services that are installed on top of the “infrastructure” |
- Application level – Web application and other custom applications scanners
- Data level – Privacy-related and sensitive information disclosure findings
- Policy level (Insights) – Missing security controls rather than misconfiguration
- Report generation – Once the uncovered assets have been classified, the ASM tool generates a report listing all uncovered assets, categorized and correlated with the type of risk they generate.
Key Takeaways
Attack surface management is crucial in today's cyber threat landscape, where attackers are constantly scanning and targeting vulnerable assets, including an organization’s digital assets. With mergers or acquisitions, it is important for IT and security teams to identify rogue assets that threat actors may use to target the company.
In the realm of cybersecurity, attack surface management (ASM) is a critical aspect that organizations must prioritize. To effectively manage their security posture, companies often rely on tools like Cymulate's ASM tools, which provide valuable insights into an organization's overall security standing.
These ASM tools leverage threat intelligence feeds to generate security ratings and risk scores, enabling businesses to assess the potential vulnerabilities within their systems. By combining informational data, such as the number and type of assets, with risk data related to findings, organizations gain a comprehensive understanding of their attack surface, including both open-source and proprietary assets. This includes viewing ASM results per findings to identify and address possible attack vectors and reduce the risk of data breaches.


