Hybrid Cloud Security
As organizations increasingly adopt hybrid cloud solutions, balancing flexibility, scalability, and security has become a top priority. A hybrid cloud environment combines on-premises infrastructure with public and private cloud services, offering a customizable solution for managing workloads, storing data, and supporting application demands. However, with this added flexibility comes a unique set of security challenges.
Hybrid cloud setups require a security approach that protects assets across diverse environments while maintaining visibility and control over data, applications and resources.
What is Hybrid Cloud Security?
Hybrid cloud security is the practice of protecting data, applications, and infrastructure in a cloud environment that integrates private and public cloud resources. Unlike traditional IT security, hybrid cloud security requires solutions that address the unique demands of both on-premises infrastructure and cloud environments.
In a hybrid setup, sensitive data or mission-critical applications may reside in a private cloud or on-premises for tighter control. In contrast, less sensitive workloads can be deployed in the public cloud for scalability and cost savings. This flexibility enhances efficiency, but it also introduces complex security challenges.
Hybrid cloud security ensures that data remains secure regardless of where it is stored or accessed. This includes securing communication and data flow between private and public clouds, implementing unified access control, and monitoring for potential threats. Effective hybrid cloud security relies on a blend of tools and practices, such as encryption, identity and access management (IAM) and real-time threat detection.
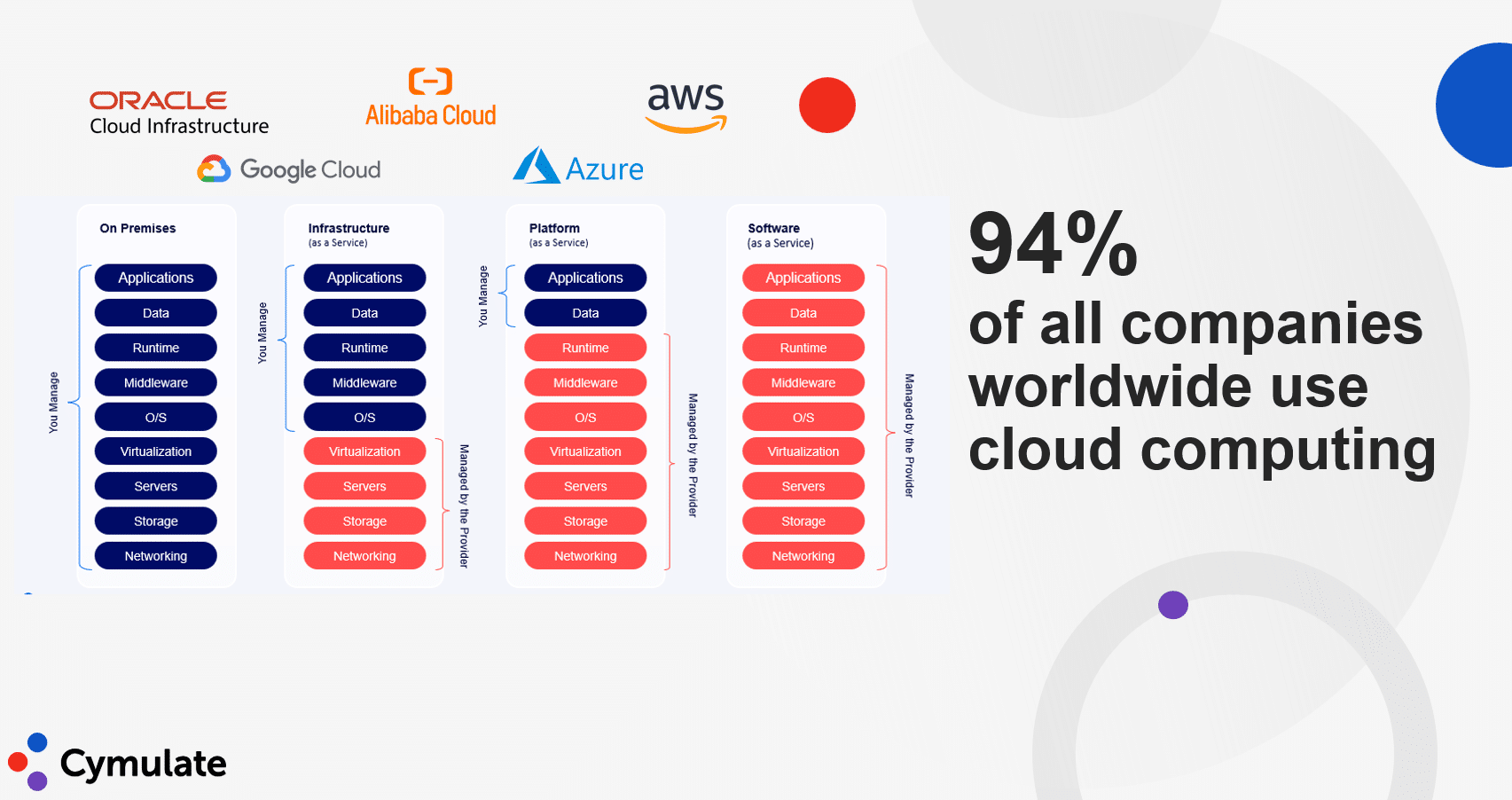
Key Components of Hybrid Cloud Security
Hybrid cloud security is built on several foundational components that protect data, ensure compliance and secure access across environments.
1. Data protection
Data protection is essential for securing sensitive information within hybrid environments. Encryption is a primary measure, ensuring data is encrypted at rest and in transit. This prevents unauthorized access, even if data is intercepted or stored in a public cloud. Data Loss Prevention (DLP) tools are also crucial, preventing unauthorized sharing or downloading of sensitive information. Secure storage solutions that adhere to strict access controls are essential for hybrid cloud security, particularly when handling regulated data.
2. Identity and access management (IAM)
Unified Identity and Access Management (IAM) is vital in hybrid environments to control access consistently. IAM solutions enforce least-privilege access, limiting user permissions based on roles and responsibilities. Multi-factor authentication (MFA) further strengthens access control by requiring verification beyond a simple password. Unified IAM allows seamless access control across private and public cloud resources, reducing risks associated with access mismanagement.
3. Threat detection and response
Hybrid cloud environments require continuous threat monitoring to detect and respond to suspicious activities. Advanced threat detection tools use behavioral analytics to spot anomalies and flag potential risks in real time. Automated incident response capabilities then allow for rapid containment of threats, minimizing potential damage. Effective threat detection and response ensure that hybrid cloud environments are constantly monitored for evolving threats.
4. Compliance and governance
Hybrid cloud environments must adhere to industry-specific regulatory requirements such as GDPR, HIPAA, and CCPA. Compliance frameworks and governance policies ensure that security measures align with regulatory standards, mitigating risks and maintaining audit readiness. In hybrid setups, compliance often involves managing data residency, privacy and security measures across both private and public cloud segments. Governance frameworks help maintain control and provide a structured approach to ensuring that all security policies are met.
Hybrid Cloud Security Architecture
A robust hybrid cloud security architecture secures data flow, segments environments, and applies layered security controls across on-premises and cloud resources.
- Data flow management: Encrypting data in transit and at rest ensures secure data transfer between private and public clouds. Secure APIs and VPNs further protect data exchanges, maintaining data integrity and preventing unauthorized access.
- Environment segmentation: Microsegmentation divides the network into isolated segments, restricting lateral movement and limiting breaches to specific areas. Each segment can have tailored policies based on data sensitivity.
- Layered security controls: Multiple layers of defense, including firewalls, IDS/IPS, and encryption, address various threat vectors, enhancing the overall security of the hybrid environment.
Adaptability and flexibility: The architecture can scale security measures based on business needs, integrate new tools, and adapt to regulatory changes.
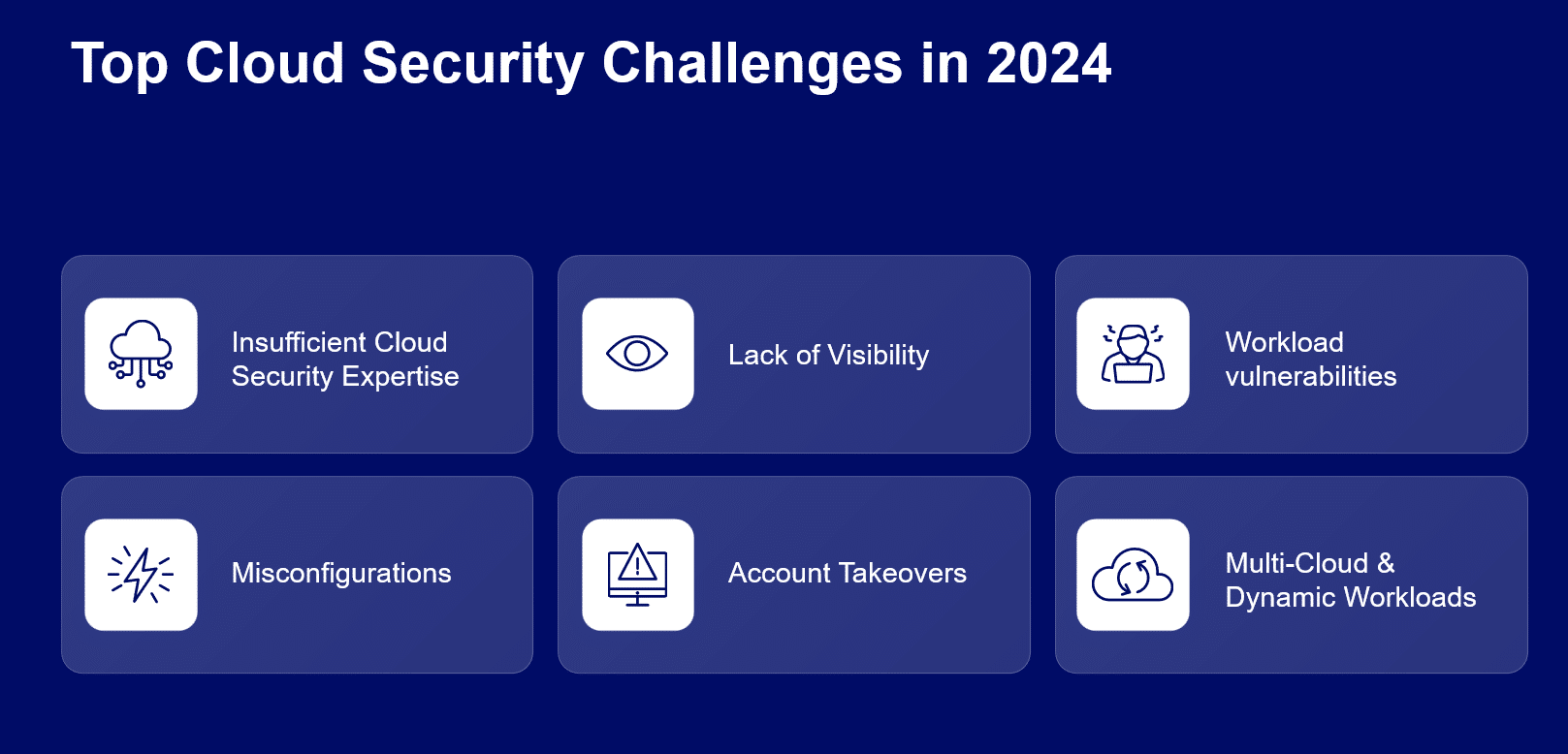
Main challenges in a hybrid cloud environment
Securing a hybrid cloud environment is complex and introduces several unique challenges organizations must address to protect their data and applications effectively.
1. Visibility
Due to their inherent differences, achieving full visibility across private and public cloud environments can be challenging. Maintaining consistent monitoring and control with multiple platforms and providers becomes difficult, increasing the risk of undetected threats. Lack of visibility can lead to blind spots, where suspicious activities or vulnerabilities go unnoticed.
2. Compliance
Hybrid environments must often meet regulatory requirements that differ by location, data type, and industry standards. Ensuring compliance across different environments is complex, as each platform may have unique data handling and storage standards. Failure to comply with regulations like GDPR, DORA or HIPAA can result in severe penalties, making this a critical area of focus.
3. Data management
Data management is complicated in hybrid clouds, as data frequently moves between private and public environments. Securing data in transit and ensuring proper encryption across platforms is essential. Additionally, organizations must ensure that sensitive data complies with residency requirements, which can vary by country or region.
4. Resource misconfiguration
Misconfigurations are a leading cause of vulnerabilities in hybrid environments, often resulting from human error or inconsistent configurations across platforms. A misconfigured access control or unprotected API can expose sensitive resources, creating significant security risks. Regular configuration reviews and automated monitoring tools can help identify and correct these issues before they lead to security breaches.
Building a Strong Hybrid Cloud Security Posture
A strong hybrid cloud security posture requires more than just technology—it demands a strategic approach tailored to the complexities of managing both private and public cloud environments. By addressing these unique cloud security challenges with proven best practices, organizations can safeguard their assets, reduce risks, and ensure seamless operations across the hybrid cloud. Below are four critical strategies to help secure your hybrid cloud infrastructure effectively.
- Zero-trust approach: Adopting a zero-trust approach is essential in hybrid cloud environments, where resources are distributed across diverse locations. Zero trust is based on the principle of “never trust, always verify,” meaning all access requests are rigorously validated before access is granted.
This approach enforces least privilege access, ensuring users have only the permissions necessary to perform their tasks. Implementing multi-factor authentication (MFA) and single sign-on (SSO) for all applications and data access strengthens the zero-trust framework. This reduces the risk of unauthorized access, especially from compromised credentials or insider threats. - Regular vulnerability assessments: Conducting cloud risk assessments is crucial to identifying security gaps and potential risks. Hybrid environments can be particularly susceptible to vulnerabilities due to the different configurations across on-premises and cloud platforms. Regular scanning, both automated and manual, helps detect misconfigurations, unpatched software and weak access controls.
- Consistent security policies: Inconsistent security policies across environments can lead to misconfigurations and compliance issues. To prevent this, organizations should establish unified security policies that apply consistently across private and public cloud resources. Unified policies make managing access, enforcing encryption, and regulating data handling easier, regardless of where data or workloads reside.
- Security automation: Automation is a powerful tool in hybrid cloud security, helping to streamline and enhance security operations. Automated monitoring tools provide real-time insights into network activity, immediately flagging any anomalies or suspicious behavior. Automated incident response systems can contain and address threats faster than manual methods, minimizing potential damage.
Automation also supports patch management, ensuring that software and applications across environments remain up-to-date and secure. By integrating security automation, organizations improve their ability to quickly detect, respond to and recover from incidents, maintaining a strong security posture.
Tools for Hybrid Cloud Security
- Cloud security posture management (CSPM): CSPM tools help organizations maintain secure configurations in their cloud environments by identifying misconfigurations, compliance issues, and potential risks. By continuously scanning cloud assets, CSPM solutions detect vulnerabilities and provide remediation guidance, keeping the environment secure and compliant.
- Workload protection platforms: These platforms protect applications and data across hybrid cloud environments. They monitor workloads for unusual activity, prevent unauthorized access, and enforce security policies, ensuring that workloads remain secure across all environments.
- Identity and access management (IAM): Unified IAM solutions are essential in hybrid clouds, where access control must be consistent across platforms. IAM tools enforce least-privilege access, support multi-factor authentication and centralize user management, reducing the risk of unauthorized access and streamlining security operations.
By integrating CSPM, workload protection, and IAM tools, organizations can effectively secure hybrid cloud environments, ensuring that both cloud-based and on-premises assets are protected against evolving threats.
How Cymulate Can Help
Cymulate enhances hybrid cloud security through cloud security validation and exposure management, offering continuous visibility, control validation and risk-based mitigation across cloud and on-prem environments.
- Asset identification and misconfiguration detection: Cymulate exposure validation platform scans for assets and misconfigurations in cloud and hybrid environments.
- Prioritized mitigation: Cymulate exposure analytics prioritizes mitigation efforts based on breach feasibility and business impact, helping security teams focus on high-risk areas.
- Targeted remediation: With actionable insights, Cymulate enables focused remediation based on risk and operational context, enhancing security across hybrid environments.