How to Perform a Cloud Risk Assessment: A Comprehensive Guide
When safeguarding your organization’s sensitive and valuable data has become a prominent and high-profile role within a security team, there is no question that conducting regular cloud risk assessments must take place. As organizations increasingly rely on cloud and multi-cloud environments to store and process business-critical data, a cloud risk assessment can make the difference between being compromised or help mitigate risks ahead of an attack.
What Is a Cloud Risk Assessment?
Understanding the risks involved in using cloud services and how to implement measures to mitigate those risks is a critical component of the intention of conducting a cloud risk assessment. A cloud risk assessment is used to identify, evaluate and prioritize potential threats and vulnerabilities within a cloud computing environment. A cloud risk assessment can help an organization identify vulnerabilities, analyze for evidence, plan for the future and comply with regulations.
This thorough assessment helps organizations evaluate risks from a different perspective, allowing them to see what’s at stake from both the infrastructure and service levels to ensure data security, regulatory compliance, reputation and business continuity. Without this important step in place, a business risks losing costly data, allowing unauthorized access and misconfigured cloud environments.

Why You Shouldn’t Skip a Cloud Risk Assessment
The need to help ensure that cloud environments are secure, compliant and resilient has become paramount as businesses increasingly rely on cloud computing services to store data, run applications and move towards digital transformation. An assessment offers several essential benefits for an organization, from helping them secure their cloud environments, proactively mitigate potential risks and align cloud strategies with business objectives.
Conducting cloud risk assessments have become a critical component of a security team’s go-to tool for several reasons.
- Security and data protection: Cloud services are known to handle large amounts of sensitive business data, including everything from personally identifiable information (PII), personal health information (PHI), financial records and intellectual property. A risk assessment helps identify security vulnerabilities, such as weakened encryption, data leakage or unauthorized access, avoiding potential data breaches and reducing potential security incidents. The visibility that a risk assessment brings to the table can also identify potential security gaps in a cloud infrastructure, allowing an organization to strengthen its defenses against evolving threats.
- Regulatory compliance: Many industries must comply with a variety of regulations and laws, for example, GDPR, HIPAA or PCI-DSS when it comes to data storage and processing. A cloud risk assessment ensures that your organization’s cloud provider and configurations meet the regulated compliance standards, and you can avoid any costly fines or reputational damage. The other area where this comes into play is in cross-border data transfers, where businesses must ensure that data stored in the cloud aligns with jurisdiction-specific regulations.
- Business continuity and disaster recovery: Cloud service outages or disruptions can cause a business significant financial loss, loss of trust and reputational damage. A cloud risk assessment can evaluate the potential risks of downtime, service disruptions or data loss and ensure that proper disaster recovery and business continuity plans are in place by identifying them early. This process also helps identify whether the business has adequate back-ups in and redundancy measures, like multi-region or multi-cloud strategies ready to go.
- Risk of data loss and integrity challenges: Reputation is everything to an organization, and as such, the risk of losing invaluable data in a cloud environment where it could be corrupted, deleted or modified either unintentionally or maliciously could cause irreparable damage. A cloud risk assessment evaluates data management and protection practices, including back-ups, versioning and access controls to help ensure data integrity. This process can help identify and establish back-up policies, data retention strategies and safeguards against data loss.
Being able to assess an organization’s cloud environment, whether it be on or off-premises, across multiple providers is absolutely critical to having a proactive risk management approach. The benefits above add up to being regulation ready, improved incident response with pre-identified threat scenarios, positioning your organization on the offensive and equally as important, financially more sound by putting cost-saving measures in place, by avoiding cloud service misconfigurations and potential breaches. Even with all of these worthwhile technological, financial and time-saving benefits, the cloud environment can still come with its risks.
What Makes Cloud Environments Prone to Risks?
With every technology advancement comes pros and cons, risks and rewards. The cloud environment is the perfect example of that with its ability to hold vast amounts of data accessible anywhere in the world, and at the very same time that accessibility could be the very thing that causes an environmental structure to break down. Due to its environment and infrastructure, the cloud is inherently predisposed to certain risks.
These risks arise from both technical and organizational factors, including shared responsibilities, third-party providers, public cloud environments prone to misconfigurations, hybrid or multi-cloud environments. Here are some key factors that make the cloud environment susceptible to risks:
- Complex cloud architectures: The cloud environment is a complex, dynamic architecture, including multiple services and interconnected systems. This complexity increases the potential for misconfigurations, vulnerabilities, exposed endpoints and security gaps. While the dynamic nature of the cloud environment could be seen as a positive, it also makes it difficult to keep up with security policies and access controls that can’t often keep the same pace.
- Emerging threats: AI, machine learning and serverless functions are all examples of new cloud technologies that pose new challenges for cloud providers. They must keep up with patching as new attack vectors emerge and continually assess and update their security postures to mitigate new risks.
- Multi-tenancy and shared resources: Public clouds use multi-tenancy, meaning that multiple customers share the same underlying physical resources, like servers and storage. While this increases efficiencies this also introduces risk of vulnerability or misconfiguration that could lead to data leakage or unauthorized access between tenants. In multi-tenant environments, resources and workloads from different customers need to be securely isolated. An isolation failure, such as in the container technology can lead to a data breach.
- Third-party dependencies and vendor risk: Relying on third-parties for cloud support is part of the norm now, however any breakdown in service can be completely disruptive and have severe impacts to a customer’s own security posture if something were to come undone with the vendor. There is a big risk in relying on a single cloud vendor, making it difficult and/or costly to migrate to another provider. This can create operational risks if the cloud provider faces financial or technical challenges.
How to Perform a Cloud Risk Assessment
- Define the scope and objectives: Identify cloud assets and services in the first step, including listing all cloud-based assets, applications and services, as well as infrastructure (IaaS), platforms (PaaS), software (SaaS) and any hybrid cloud configurations. This step will also account for defining any assessment goals and identifying key stakeholders.
- Define risk criteria: This step defines all the areas of risk, including security, compliance, operational, vendor, privacy and performance risks. This takes into consideration all potential vulnerabilities in the respective areas, like GDPR, HIPAA or PCI-DSS and the collaborations that must take place between them and how each will define their individual levels of risk tolerance.
- Identify threats and vulnerabilities: Identifying potential threats, such as cyberattacks, data breaches and insider threats is a critical step. Here you can assess for common cloud risks like misconfigurations, DDoS attacks and unauthorized access. Make use of threat intelligence tools to identify potential attack vectors.
- Evaluate risks: Review security measures implemented by the cloud provider including certifications (e.g., ISO 27001, SOC 2), encryption protocols and security best practices. Perform risk scoring using a risk matrix to prioritize the most critical risks based on impact and likelihood.
- Develop mitigation plans: In the next to last step, putting risk mitigation measures into place and continuously monitoring their effective is mission critical. This should be on a scale from risk mitigation (high-risk), risk acceptation (lower-risk), risk transfer (where risks can be transferred through cyber insurance or by outsourcing certain responsibilities), and lastly risk avoidance (best to avoid the risk altogether).
- Continuous monitoring and validation: Continuous monitoring is a must to ensure any third-parties are operating as intended. Use automated tools to help with monitoring and incident response. Conduct regular assessments to validate that mitigation efforts remain effective.
What to Look for in a Successful Cloud Risk Assessment
A comprehensive cloud risk assessment should address areas that help create a secure, compliant and resilient cloud environment that aligns with an organization’s goals and ensures long-term success. To achieve this, an assessment should include the following:
- Security risks: This includes data breach risks, misconfigurations, identity and access management (IAM) and access controls, insider threats and security patch management.
- Compliance and regulatory alignment: Ensure the organization complies with relevant regulations and standards, that cloud systems meet industry regulations and audit requirements. Remember to inquire about data retention and deletion – does the cloud provider have clear policies that align with regulatory requirements?
- Operational risks: Know your cloud provider’s uptime guarantee (e.g., 99.9% SLA) and does your organization require higher availability? Always have a contingency plan in place for disaster recovery and know your downtime and outages. Knowing your cloud providers scalability and vendor lock-in options puts you a step ahead.
- Cloud architecture and configuration risks: Are virtual networks properly segmented to prevent unauthorized access to sensitive workloads? Check for cloud service configuration, segmentation and isolation to avoid lateral movement in case of a breach and cross-contamination.
- Vendor risks: Evaluate third-party cloud providers for potential vulnerabilities, exit strategy and transition plan in the instance of a shutdown of cloud services or needing to do a data migration.
Tools That Can Help You Perform a Cloud Risk Assessment
Depending on your organization’s needs, whether it be security posture, compliance requirements or cost management, there is likely a tool available to help ensure a comprehensive approach to a cloud risk assessment. Any combination or singular use of any of these tools can help provide more visibility throughout the execution of the assessment.
Examples of tools are:
- Cloud security posture management (CSPM), which helps focus on identifying and mitigating security risks in cloud configurations, ensuring compliance with security best practices and providing continuous monitoring.
- Prisma Cloud (formerly RedLock) by Palo Alto Networks
- CloudHealth by VMware
- Cloud compliance and governance tools help organizations monitor and enforce compliance with regulatory requirements and internal policies in the cloud environment.
- AWS Config
- Google Cloud Security Command Center (SCC)
- Cloud cost management tools (for risk of financial overruns) help to determine the mismanagement of cloud costs that could introduce financial risks.
- AWS Cost Explorer
- CloudHealth by VMware
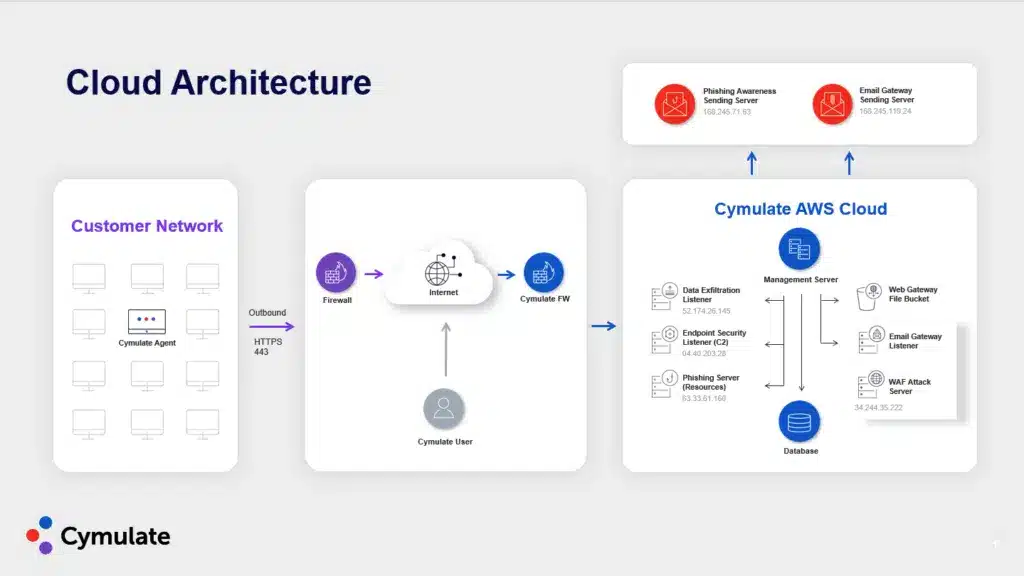
Building a Strong Cloud Security Posture With Cymulate
By now, the benefits of performing a cloud risk assessment should be in focus. Risk management is an everyday effort for security teams and on the minds of every CISO and key stakeholder. The Cymulate security and exposure validation platform is much like the cloud risk assessment in that it can bring instant relief with advanced detection and information.
By positioning your security teams in the offensive by being able to simulate real-world attacks to identify vulnerabilities before an adversary does, you are not only saving time, money and resources, but could be saving your entire business and reputation at the same time.
The Cymulate platform performs continuous security validation, provides exposure analytics, breach and attack simulation (BAS) and continuous automated red teaming (CART). With all of these consistent automated features, we can help any organization manage their multi-cloud environments.
Key Takeaways
A cloud risk assessment helps an organization proactively identify vulnerabilities, protect sensitive information, ensure compliance with regulatory requirements, and avoid financial and reputational losses that could result from security incidents or operational failures in the cloud. This is particularly critical as organizations increasingly rely on cloud environments to store and process business-critical data.
By performing a thorough risk assessment, companies can make informed decisions about which cloud services to use, how to configure them securely, and what additional safeguards they might need to put in place.
Contact Cymulate for a demo to learn how we can help your organization work with any third-party vendor and conduct a successful cloud risk assessment.