Mean Time to Remediate (MTTR)
What is Mean Time to Remediate (MTTR) in Cybersecurity?
Mean Time to Remediate (MTTR) is a key cybersecurity metric that measures how quickly an organization can identify, contain and fix a security issue after it’s detected. In simple terms, MTTR is the average time it takes to neutralize a threat or vulnerability from the moment it’s discovered to the point of full remediation.
This concept originates from IT incident management, where MTTR historically stood for “Mean Time to Repair,” the time to restore a system after failure.
In a cyber context, MTTR is often defined as Mean Time to Respond or Resolve, emphasizing the complete response lifecycle from detection through resolution.
It’s important to clarify terminology because teams may also track related metrics: for example, Mean Time to Detect (MTTD) measures how quickly you discover threats, whereas MTTR measures how quickly you respond and remediate after detection.
MTTR: Definition & Purpose
MTTR in cybersecurity is the average time required to fully resolve a security incident or vulnerability. It includes all steps from initial alert, through investigation, containment and applying a fix or mitigation, until normal operations are restored.
For example, if a malware infection is detected, MTTR would encompass the time it takes for the security team to analyze the alert, isolate affected systems, eradicate the malware and confirm that systems are secure again.
This metric is typically calculated by summing the response durations for all incidents in a period and dividing by the number of incidents, yielding an average “time to remediate” per incident.
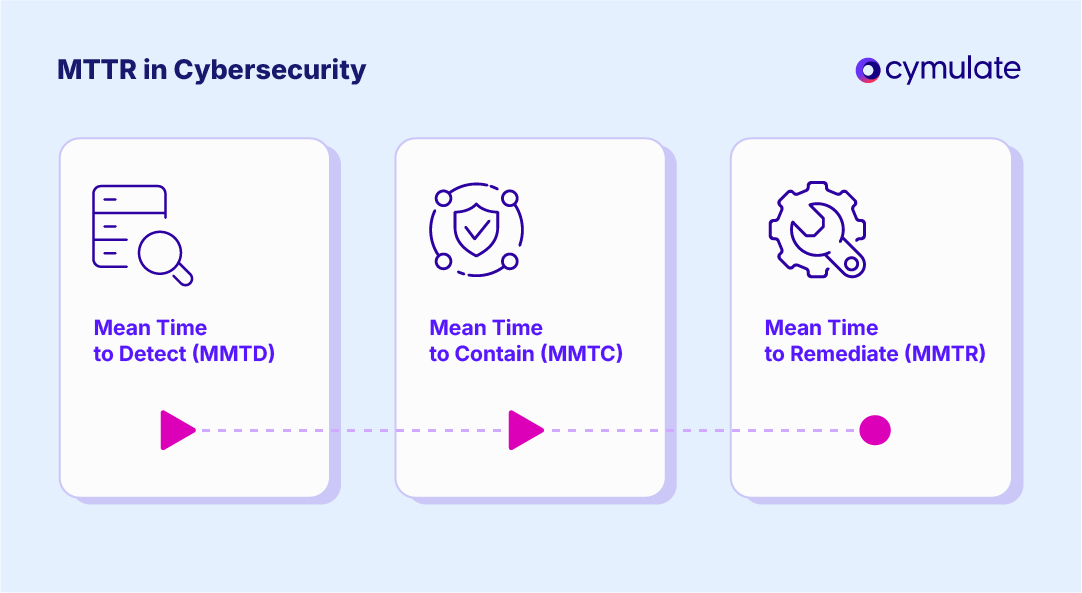
Main Purpose
The purpose of MTTR is to gauge the efficiency of an organization’s incident response and remediation processes. A low MTTR indicates that the security and IT teams can address threats quickly, limiting the window of opportunity for attackers.
Conversely, a high MTTR suggests delays or bottlenecks in response, which can translate to longer dwell time (the duration an adversary remains in your environment) and greater risk of damage.
It’s worth noting that MTTR is sometimes defined in different ways. In IT service management, the “R” in MTTR might stand for repair, restore or recover, focusing on system uptime. In cybersecurity operations, MTTR often stands for respond or remediate, emphasizing security incident resolution. Despite the slight nuances, the core idea is similar, MTTR measures responsiveness.
We distinguish MTTR from related metrics like MTTD (Mean Time to Detect) and MTTC (Mean Time to Contain) because those isolate specific phases of incident management. MTTD measures detection speed, while MTTR (remediate) covers the entire response cycle after detection.
Both are critical: MTTD plus MTTR together essentially form the total “incident lifecycle.” Leading organizations monitor all of these to get a full picture of their security performance.
How MTTR Improves Security Operations
Mean Time to Remediate (MTTR) is a vital cybersecurity metric because it directly reflects an organization’s ability to reduce risk. The quicker a threat is contained and eliminated, the less damage it can cause.
A low MTTR shows strong security posture, while a high MTTR often indicates weaknesses in processes, visibility or staffing. Here are some specific reasons why MTTR matters:
1. Limits the Impact of Breaches
The longer a threat remains in your environment, the more opportunity it has to escalate. Research shows the average breach takes over 9 months to detect and contain.
That extended dwell time gives attackers a significant advantage. By reducing MTTR, companies can shorten this timeline, limiting damage and potentially avoiding full-scale data breaches altogether.
2. Reduces Window of Exploitation
A high MTTR means critical vulnerabilities remain open for longer periods, giving attackers more time to exploit them.
A clear example is the Equifax breach, where a known Apache Struts flaw remained unpatched for two months. This delay led to the exposure of personal data of 147 million people. Quick remediation could have prevented such a catastrophic event.
3. Controls Financial and Operational Damage
The faster a threat is contained, the less it costs the business. High MTTR correlates with greater expenses in recovery, legal actions and reputational damage.
In contrast, companies that resolve incidents quickly often avoid major financial losses and maintain operational continuity. Speed equals savings.
4. Indicates Maturity of Security Operations
MTTR serves as a reflection of the security team’s agility and coordination. A low MTTR suggests efficient communication, strong tooling and clear incident response protocols.
A consistently high MTTR may reveal gaps in staffing, process inefficiencies, or lack of authority to act quickly. Security leaders use MTTR to assess operational performance and validate investments in detection and response capabilities.
5. Meets Compliance and Builds Trust
Industries with strict regulations require prompt incident handling and breach notification. A strong grip on MTTR helps organizations stay compliant and avoid penalties.
It also strengthens customer confidence by showing that the business is capable of addressing threats before they cause harm to user data or services.
6. Reinforces Proactive Risk Management
In vulnerability management, some organizations take 60 to 150 days to patch known issues. This extended period leaves systems vulnerable.
Leading security teams aggressively work to cut that time down by prioritizing high-risk flaws and streamlining remediation processes. Each hour saved reduces the opportunity for attackers and limits the scope of incidents.
It’s no surprise then that 71% of security leaders now consider continuous threat exposure management essential to improve metrics like MTTR going forward.
Challenges in Reducing MTTR
Reducing Mean Time to Remediate (MTTR) is not easy. Many organizations face persistent operational challenges that slow down detection, response, and containment. Below are the most common barriers that contribute to high MTTR.
Manual Triage and Response
A heavy reliance on manual processes can significantly delay incident response. Analysts often must sort through alerts, investigate step by step and coordinate fixes manually. This consumes time and introduces human error. Critical alerts may be missed or handled out of order.
The problem worsens with the ongoing cybersecurity skills shortage. Many teams are understaffed, and manual workflows cannot keep up with growing threat volumes. Without automation, analysts address issues sequentially, slowing down containment.
In contrast, automating repetitive tasks like isolating endpoints or pushing patches can greatly reduce MTTR. According to Cymulate, automated security validation can test 230 times more threats than manual methods in the same timeframe.
Alert Fatigue
Security Operations Center (SOC) teams face a flood of alerts from tools like SIEMs, EDR and IDS/IPS. Many alerts are false positives or low priority, causing analysts to suffer from alert fatigue.
This fatigue leads to slower responses or missed alerts, directly increasing MTTR. Overwhelmed analysts may delay responding or even ignore alerts, allowing real threats to go unnoticed.
Fragmented Tools and Siloed Data
Many enterprises use dozens of security tools that rarely integrate well. According to Panaseer, large organizations use an average of 76 security tools. This results in fragmented visibility, where data and alerts are spread across multiple consoles.
Analysts waste time jumping between systems, piecing together information from different sources. Key context may exist in one tool (like a vulnerability scanner) while detection comes from another (like an EDR), delaying investigation.
Siloed data between teams, such as network, cloud, and endpoint security, makes collaboration harder. Without a unified view, teams struggle to quickly answer questions like “What systems are affected?” This fragmentation keeps MTTR high.
Static or Infrequent Testing
Many organizations rely on periodic assessments, such as quarterly scans or annual pen tests. While useful, these point-in-time checks mean that new vulnerabilities can linger until the next scheduled test.
If a threat appears right after a monthly scan, it may go undetected for weeks. This inflates MTTR and creates feast-or-famine cycles, where teams are overloaded post-scan, then relatively inactive until the next.
Such testing does not reflect the dynamic threat landscape. Without continuous validation, security teams are always behind. Cymulate found that 61% of security leaders cannot promptly identify or remediate cloud exposures. Only 9% test daily, and over a third take up to 24 hours just to validate a single cloud issue.
Best Practices to Reduce MTTR
Improving Mean Time to Remediate (MTTR) requires more than just speed. It demands refined processes, the right technologies and strong coordination. Below are best practices that security teams can adopt to reduce MTTR effectively.
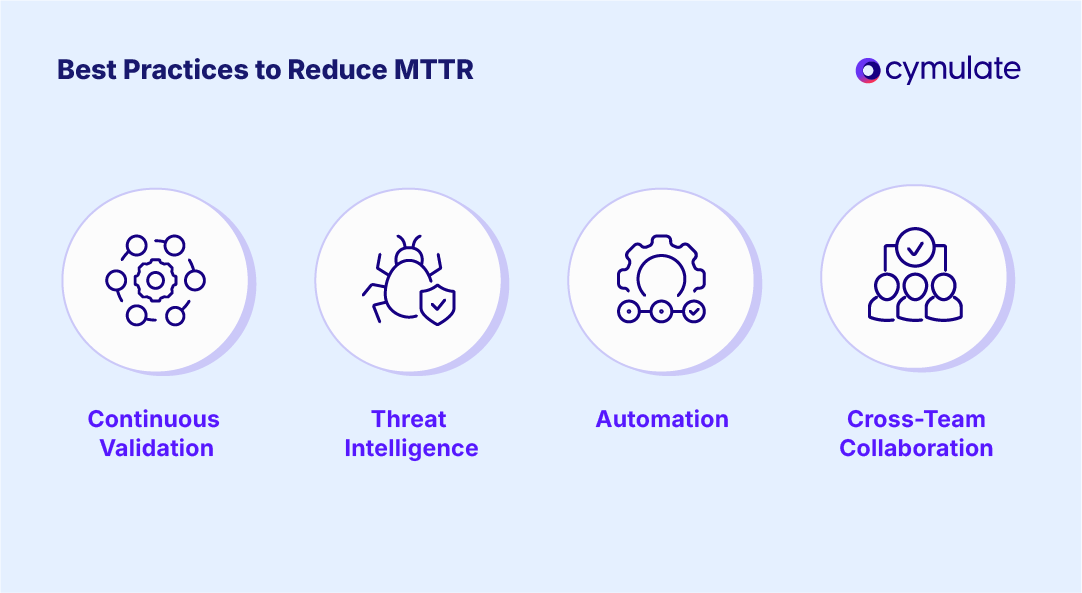
1. Implement Continuous Security Validation
Avoid relying solely on annual pen tests or occasional scans. Adopt continuous threat exposure management by regularly validating your defenses using tools like automated attack simulations, Breach and Attack Simulation (BAS), and structured runbooks.
This approach identifies vulnerabilities early, reducing the time they remain unaddressed. As Cymulate emphasizes, continuous testing shortens both MTTD and MTTR, helping teams detect and remediate issues before they escalate. Continuous testing also cultivates a culture of readiness, ensuring faster and more natural responses during actual incidents.
2. Leverage Automation and Orchestration
Automation is one of the most powerful tools for lowering MTTR. Identify repetitive, manual steps in your detection and response workflows and automate them using SOAR tools or scripts.
Automation can handle tasks like quarantining machines, collecting forensics, or closing firewall ports in seconds. Automated playbooks can act immediately on indicators of compromise, saving analysts hours. According to Purplesec, continuous and automated vulnerability management significantly reduces remediation time by speeding up prioritization and patching.
3. Integrate Threat Intelligence for Prioritization
Not all threats are equal. Integrating real-time threat intelligence into your workflows helps teams focus on what matters most. By enriching alerts with context on active exploits and industry-specific threats, you can prioritize remediation effectively.
For instance, if a specific CVE is being widely exploited, teams can fast-track patching and mitigation for related systems. Threat intel feeds also help update detection tools, guide defenders on attacker tactics and lower MTTR through faster and better-informed decision-making.
Operationalizing threat intel through fusion centers or SIEM integrations enables real-time, intelligence-driven response. The key is to use threat intel actively in your playbooks, SIEM and endpoint defenses so that response actions are data-driven and not wasted on low-priority issues.
4. Foster Cross-Team Collaboration
Remediation often involves multiple departments, security analysts, IT operations, developers, and even external vendors. Tight collaboration across these groups can drastically reduce MTTR.
Make sure your incident response plan defines roles clearly and sets up fast hand-off procedures. Use shared communication channels, such as Slack or Microsoft Teams war rooms, for real-time collaboration. Many teams now adopt ChatOps to combine alerts and actions into shared conversations, speeding up response.
Integrate your ticketing system with security alerts and ensure overlapping on-call rotations between security and IT. When everyone shares the same view and can act quickly, MTTR drops substantially.
How Cymulate Helps Reduce MTTR
Cymulate’s Exposure Management Platform helps reduce Mean Time to Remediate (MTTR) by continuously testing your defenses through automated security assessments, breach and attack simulations (BAS) and guided remediation workflows.
Rather than waiting for periodic scans, Cymulate allows security teams to uncover vulnerabilities in real time. This approach significantly shortens both MTTD and MTTR.
According to the Cymulate 2025 Threat Exposure Validation Impact Report, organizations running monthly exposure validation exercises experienced a 20% reduction in breaches, while 47% of security leaders reported improved MTTD, giving responders a crucial head start.
Automation, Threat Intelligence, and Integrated Response
Cymulate enhances incident response speed through automated simulations, an extensive library of over 1 million attack techniques and daily threat intelligence updates. These simulations help teams test defenses against emerging threats and identify weaknesses before attackers do.
When issues are detected, the platform offers prioritized, actionable remediation guidance, helping security teams focus on high-risk exposures. Features like purple teaming promote collaboration between red and blue teams, ensuring coordinated response during actual incidents and reducing overall MTTR.
Cymulate also integrates seamlessly with SIEM, SOAR, EDR and IT ticketing systems, providing a unified view of your security posture.
Cymulate supports automated remediation by pushing Indicators of Compromise (IoCs) and detection rules directly into your tools. This tight integration eliminates silos, reduces manual handoffs, and enables faster response.
As a result, organizations using Cymulate consistently report improved metrics, including breach reduction and faster incident resolution, making it a valuable solution for any team focused on operationalizing continuous improvement in security operations.
Key Takeaways on MTTR and How to Optimize It
A lower MTTR means less attacker dwell time, reduced breach impact, and greater operational resilience. Achieving this requires overcoming common obstacles such as manual response workflows, alert fatigue, siloed tools and infrequent testing.
Organizations can significantly improve MTTR by adopting continuous security validation, automated response, intelligence-driven prioritization and cross-team collaboration. These best practices not only limit damage from incidents but also reinforce confidence in security operations.
Cymulate is built to help teams reduce MTTR by enabling continuous threat exposure management. Through automated breach simulations, real-time threat intelligence, prioritized remediation guidance, and deep integration with existing tools, Cymulate empowers teams to detect and resolve issues faster.
MTTR reflects how agile and effective your security response truly is. Keeping MTTR low strengthens cyber resilience and helps ensure threats are contained before they escalate.

