Network Penetration Testing
Hackers always find new ways to infiltrate systems, exploit vulnerabilities and cause havoc—from stealing sensitive data to disrupting critical operations. For IT security professionals, this reality makes it clear: traditional defenses are not enough!
This is where network penetration testing comes in. Think of it as a "stress test" for your network’s defenses, designed to uncover weaknesses before cybercriminals do.
By simulating real-world attack scenarios, network penetration testing offers a deep dive into how your infrastructure can withstand an adversary’s tactics, techniques and procedures (TTPs).
It is more than just identifying vulnerabilities—it is about understanding how those vulnerabilities could be exploited and how to mitigate them before they become a problem.
What is Network Penetration Testing?
Network penetration testing is a worthwhile cybersecurity practice used by organizations to proactively identify vulnerabilities within their network infrastructure.
This method involves simulating real-world attacks to assess the security posture of an organization's network, uncover weaknesses, and evaluate how those weaknesses might be exploited by malicious actors.
The Network Penetration Testing Process – Step by Step
Network penetration testing follows a structured approach to ensure thorough examination of the network’s defenses. The process typically includes the following stages:
1. Reconnaissance – gathering information about the network
The first phase of a network penetration test is reconnaissance, which involves collecting as much information as possible about the target network. This step can be broken down into passive and active techniques.
- Passive reconnaissance involves gathering publicly available information without directly interacting with the target network. This might include things like looking up domain names, examining WHOIS data, reviewing DNS records, or using search engines to find relevant information about the organization. For example, an attacker may use tools like Shodan to gather information about devices connected to the internet without directly scanning the network.
- Active reconnaissance is a more direct approach where the tester actively scans the network. This could involve identifying live hosts, mapping the network's architecture, and probing services that are exposed to the internet. For instance, tools like Nmap or Netcat can be used to find open ports, which could give attackers potential access points into the network.
2. Scanning – identifying open ports, services, and network architecture
Once reconnaissance is complete, the next step is scanning, where specialized tools are used to identify open ports, services running on those ports, and the general architecture of the network. This helps testers understand the attack surface and where vulnerabilities may exist.
During this phase, port scanning tools like Nmap or Nessus are often used to detect which services are running on which ports. For example, port 80 might indicate a web server, while port 443 could be indicative of HTTPS traffic. By scanning these ports, testers can identify potential weaknesses in services that are accessible from outside the network.
Another critical aspect of this phase is service identification. If a tester identifies a running service, they’ll attempt to determine its version to check for known vulnerabilities. For example, if a web server is running Apache 2.4, the tester may cross-reference this version with databases like CVE (Common Vulnerabilities and Exposures) to check for any known exploits.
3. Exploitation – simulating attacks to expose vulnerabilities
Exploitation is where the tester simulates real-world attacks to attempt to breach the network using the vulnerabilities discovered during scanning. This phase is designed to determine whether the identified weaknesses can be exploited in a way that leads to unauthorized access or control of the system.
If a SQL injection vulnerability is discovered on a web application, the tester might attempt to inject malicious SQL code to retrieve or manipulate data from the database. Alternatively, privilege escalation can be tested, where the tester attempts to gain higher-level access to the system after an initial foothold is gained.
Another example of exploitation could involve attacking an outdated software vulnerability. For instance, if a network service is running an outdated version of OpenSSL, the tester might attempt to exploit the Heartbleed bug (a well-known vulnerability in older OpenSSL versions) to extract sensitive data.
The goal here is not to cause harm, but to demonstrate how a real attacker might exploit vulnerabilities and to assess the severity of the risks involved.
4. Reporting – summarizing findings and recommendations
After the testing phases, the results are compiled into a comprehensive report. This report summarizes the findings from the reconnaissance, scanning, and exploitation stages and provides recommendations for remediation. The goal is to ensure that the organization understands the vulnerabilities in their network and knows how to address them.
- The report typically includes a detailed description of each identified vulnerability, the methods used to exploit them, and their potential impact on the organization. Such as, a vulnerability might be described as a critical SQL injection flaw on a public-facing web application, and the report will explain how it could lead to data loss or unauthorized access.
- Remediation recommendations are an essential part of the report. For example, if the tester identifies an exposed FTP service with weak credentials, the report might suggest changing default login credentials, encrypting traffic, or disabling the service if it's not necessary.
These findings help IT teams prioritize fixes based on risk level and take steps to improve the organization’s overall security posture.
How Often Should Network Penetration Testing Be Performed?
The frequency of network penetration testing depends on several factors, including the complexity of the network, regulatory requirements, and the organization's risk tolerance. While some organizations may test their networks annually, others, particularly those in high-risk sectors or those handling sensitive data, may need to conduct penetration tests more frequently.
Networks that undergo significant changes or experience security incidents should be tested more often to ensure that new vulnerabilities are identified before they can be exploited. In addition to periodic testing, continuous security validation can be highly beneficial.
Automated tools and platforms, such as Cymulate, allow for ongoing assessments, ensuring that organizations are not only prepared for scheduled tests but can also respond swiftly to emerging threats.
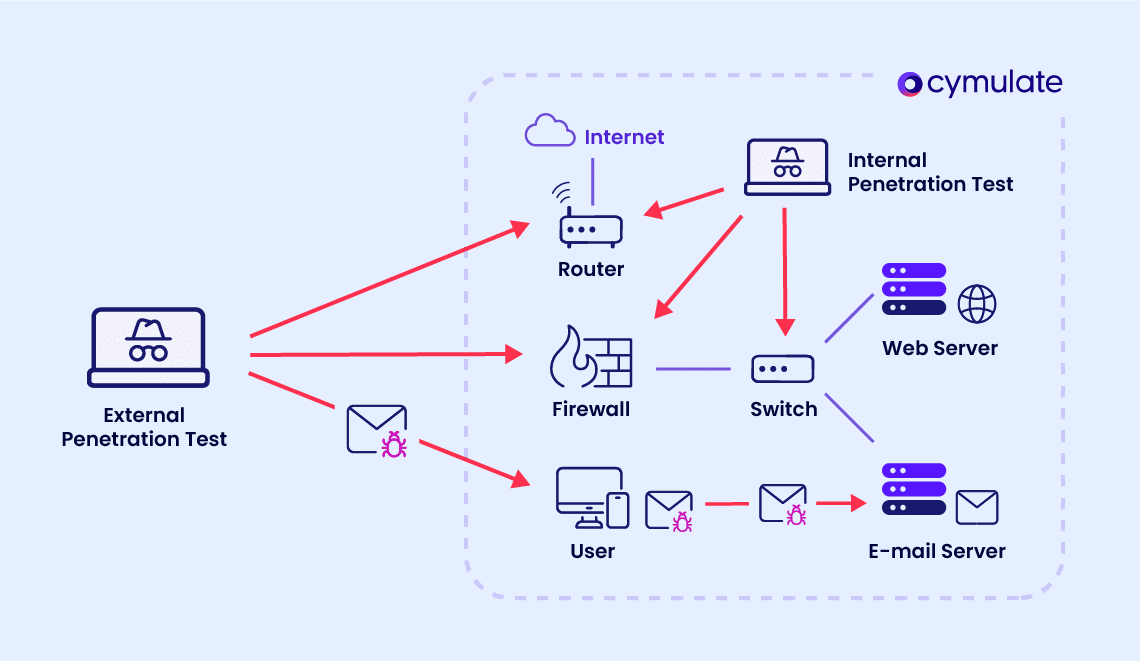
External Network Penetration Testing
External network penetration testing focuses on evaluating an organization’s perimeter defenses against attacks originating from outside the network.
By simulating how external threat actors might attempt to breach the system, this type of testing is crucial for assessing the robustness of firewalls, intrusion detection systems, and other external security measures.
External penetration testing helps identify weak points in public-facing systems such as web servers, DNS configurations, or email servers, which are often targeted by cybercriminals.
Regular external testing ensures that the network is protected from a wide range of external threats, including DDoS attacks, phishing, and SQL injection.
Internal Network Penetration Testing
Internal network penetration testing takes a different approach. It assesses vulnerabilities that may be exploited by insiders or attackers who have already breached the network’s perimeter defenses.
This test simulates the risks posed by malicious or negligent employees, compromised user credentials, or physical access to network systems.
Internal testing is essential for identifying weaknesses in network segmentation, access control policies, and overall internal security practices.
Given the prevalence of insider threats, conducting internal penetration tests is just as important as external assessments. It helps organizations ensure that even if attackers manage to gain internal access, they cannot move laterally across the network and escalate privileges undetected.
Automated Network Penetration Testing
Automated network penetration testing is an emerging trend that offers several advantages over traditional manual testing. With automated tools, organizations can run penetration tests more frequently and at a lower cost, allowing for continuous security validation.
Automated testing tools can scan networks for known vulnerabilities, run exploitation scenarios, and generate reports, all with minimal human intervention.
However, there are limitations to automation. While automated tools can cover a broad range of known vulnerabilities, they may miss sophisticated attack vectors or fail to identify vulnerabilities that require manual expertise. For this reason, a hybrid approach that combines both automated and manual penetration testing is often recommended.
Network Penetration Testing Tools
There are numerous tools available for conducting network penetration testing. These tools vary in their focus and functionality, with some specializing in network scanning, others in exploitation, and others in reporting. Some of the most widely used tools include:
- Nmap: A network scanning tool that helps identify live hosts, open ports, and services on a network.
- Metasploit: An exploitation framework that simulates attacks to test vulnerabilities.
- Wireshark: A packet analyzer used to examine network traffic for signs of malicious activity.
- Nessus: A vulnerability scanner that detects weaknesses in the network, including missing patches and misconfigurations.
The Cymulate platform serves as an all-in-one solution, combining network penetration testing, security validation and exposure management into a unified system. Cymulate provides automated, continuous testing to ensure that vulnerabilities are detected early, while its reporting tools allow for real-time insights and actionable recommendations.
Cymulate: Continuous Security Validation and Exposure Management for Nework Penetration Testing
Cymulate provides network pen testing with continuous validation of the efficacy of security policies. For companies with a complex infrastructure, security teams ensure that there is no opportunity for lateral movement between networks. The platform continuously discovers discrepancies and provides remediation guidance so security teams can reduce risk by closing gaps and preventing security drift.
By using Cymulate, organizations can continuously assess their security posture and manage the exposure of their assets to cyber threats. Unlike traditional penetration testing, which is often a one-off process, Cymulate ensures ongoing testing and validation across cloud, on-premises, and hybrid environments.