A massive amount of financial, personal, and medical data is exchanged over the internet every millisecond. Stealing or holding companies’ digital assets for ransom has become a lucrative option for opportunistic cybercriminals. Customers are tired of hearing that their information may have been stolen in a breach.
Given the inevitability of cyberattacks, how can you best protect your assets? The answer lies in proactively attacking your cybersecurity before hackers do; this is where continuous security validation comes into play.
What is Continuous Security Validation?
Continuous Security Validation is a cybersecurity method of consistently verifying that a company’s already-enabled security controls work as effectively as possible.
With an average of 35 security controls per company at any given time, confirming that all are updated and utilized exclusively by the proper people, and without granting access to hackers, is no easy feat to accomplish manually.
Security posture drifts due to a myriad of reasons – primarily due to the dynamic nature of information systems, but weak passwords, misconfigured admin access, and third-party vendor updates with unforeseen vulnerabilities can affect security posture as well.
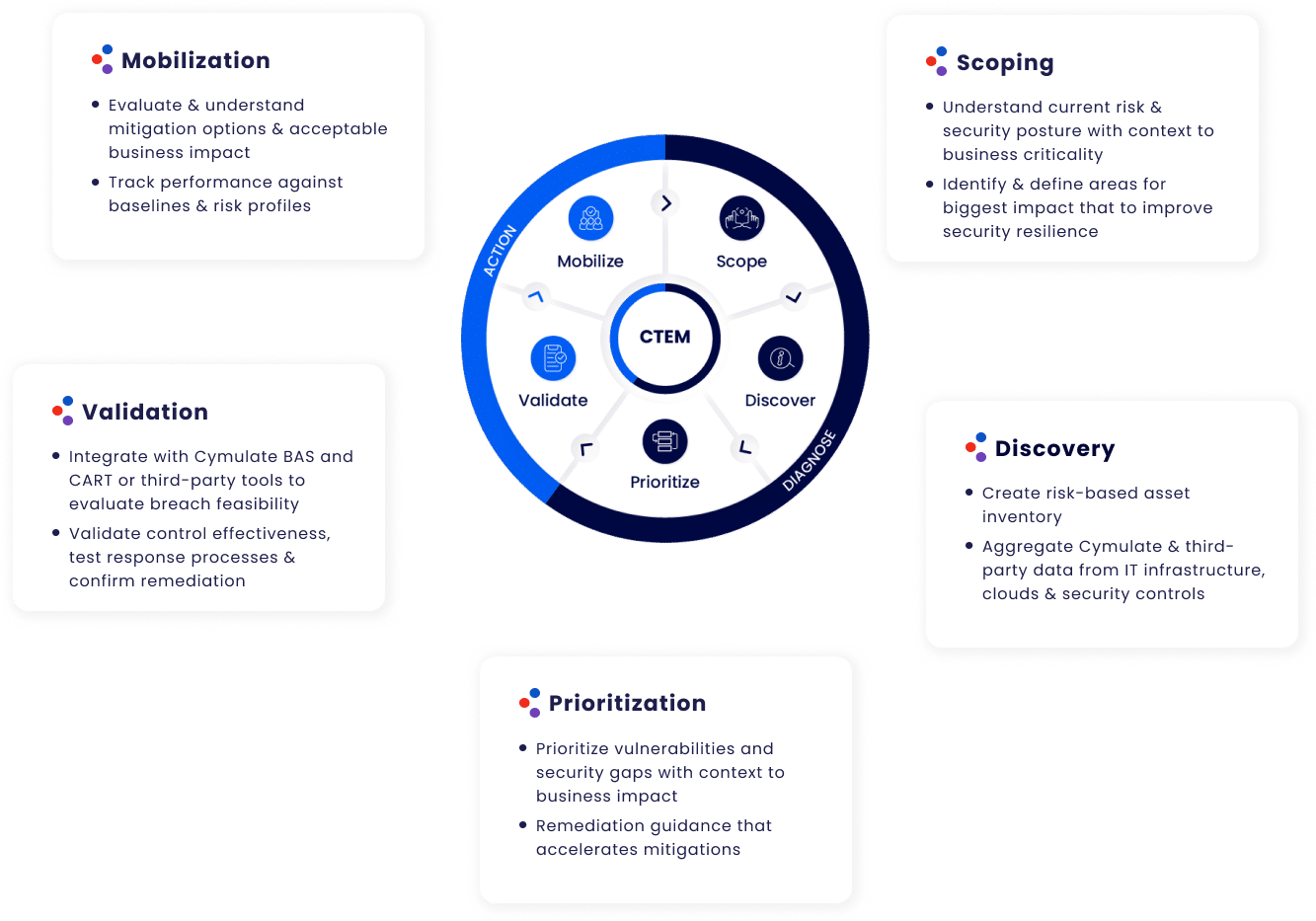
As the name suggests, Continuous Security Validation is not a traditional point-in-time assessment of the security posture, such as costly once or twice year penetration testing exercise, but rather a consistent and rigorous process that scans for weaknesses that could potentially be exploited by malicious actors. It’s a persistent, offensive method that approaches attack surface, security controls, and lateral movement paths from an attackers’ standpoint, using many of the same tactics to find vulnerabilities and escalation routes.
These tactics and techniques are mapped from the MITRE ATT&CK Framework – a curated knowledge resource of known behavior an attacker might use to gain access to a company’s digital assets and where they would go once they’ve infiltrated the environment. Created in 2013, the MITRE ATT&CK Framework provides a common taxonomy and lexicon to describe adversarial actions or the platforms they are known to target, making it easier for both offensive and defensive security teams to define certain behaviors and goals.
How to Use Continuous Security Validation
Reports based on these attacks allow companies to assess which areas of their security system need improving or replacing and create baselines. Baselines are priceless when looking to assess the evolution of their security performance. Getting a holistic view, knowing what they’re up against, and the ability to show the facts to both upper management and security staff to make educated decisions is the most valuable aspect of Continuous Security Validation. It gives enterprises the data and reassurance that their security posture will stand up to the latest threats and zero-day attacks. Security professionals do not have to guess whether their security controls and overall security posture could withstand an attack.
Continuous Security Validation assumes a breach is inevitable and proactively attacks itself to find weaknesses before hackers do.
When a potential vulnerability is found, the security team is notified quickly, and the vulnerability is scheduled for patching according to an attack-based patching prioritization system.
Breach and Attack Simulation role in Continuous Security Validation
Continuous Security Validation is comprised of multiple tools and processes that are repeated on a consistent basis. One of these tools is Breach and Attack Simulation.
Breach and Attack Simulation is the process of actually attacking computer security, emulating cybercriminals with production-safe automated attacks. It is essentially an automated penetration test like one mentioned earlier, but it differs by being automated and continuous. An advanced cybersecurity attack simulator assesses new attack techniques and validates security controls against them throughout the entire kill chain (including escalation paths followed by attackers from an entry point to valuable company assets).
Breach and Attack Simulations can run 24 hours a day, seven days a week, 365 days a year. The Breach and Attack Simulation model doesn’t rely on human penetration testers, or sometimes, any human at all. This means there is less chance of a human error occurring, which might leave an opening for an attacker.
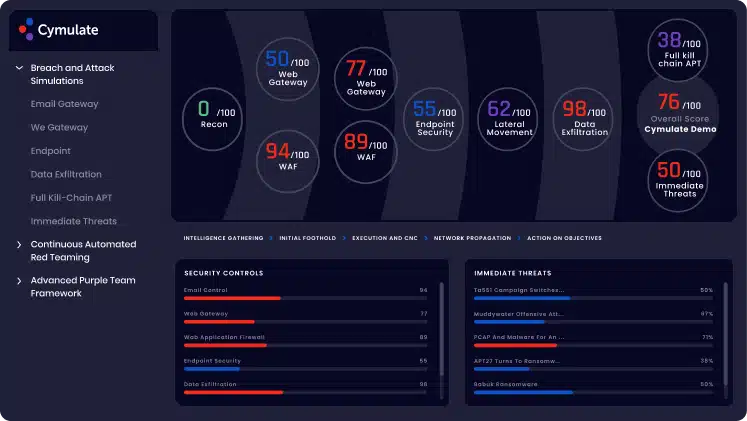
Benefits of Continuous Security Validation
1. Smarter Budget Use
Automating the validation of cybersecurity performance with Continuous Security Validation, as opposed to hiring penetration testers or multiple skilled IT specialists, saves money. With ransomware attacks hitting an all-time high, preventing the possibility of a price to pay after a data breach could save companies millions of dollars. Not only do big companies get hit by ransomware attacks, but small companies, schools, and hospitals are also just as likely to be in the attackers’ line of sight.
Companies are also given visibility into which security measures aren’t working or are superfluous. By having that information handy, enterprises can make better decisions on which security controls are redundant and wasting money.
2. Protect Customers, Clients, or Patients
When end-users choose a company to give their data to, they expect the utmost care to be taken to make sure that their data doesn’t fall into the wrong hands. With continuous security validation, businesses can have a leg up on the competition by assuring customers that their personal information is as secure as possible.
3. Protect Brand Reputation
Even with the best cybersecurity, attacks can still happen. But as opposed to a security stance without Continuous Security Validation, companies are at a disadvantage as to how it may have happened and how to prevent it in the future. They are at a loss of words when being held accountable which can damage their brand reputation in the future. By having the analysis and intelligence, companies can get ahead of scandals and PR disasters, where the cost of breach skyrockets way beyond just the incident remediation.
Key Takeaways
Continuous Security Validation is becoming a growing necessity for companies looking to adapt technologically. The automated proactive approach of constantly attacking and using findings to optimize security posture makes enterprises safer for their assets and customers.
With just a few clicks, Cymulate challenges your security controls by initiating thousands of attack simulations, showing you exactly where you’re exposed and how to fix it—24/7. Book a demo with Cymulate to see how we can help you enhance your security posture.











