Cymulate Exposure Validation
Optimize your threat resilience by continuously testing your defenses across the full kill chain using the latest adversarial techniques.
Optimize Security by Validating Controls Against Real Threats
Validate the effectiveness of your security controls and test your defenses against the latest threat activity to ensure your security posture is optimized, before an attack occurs.
Validate threats
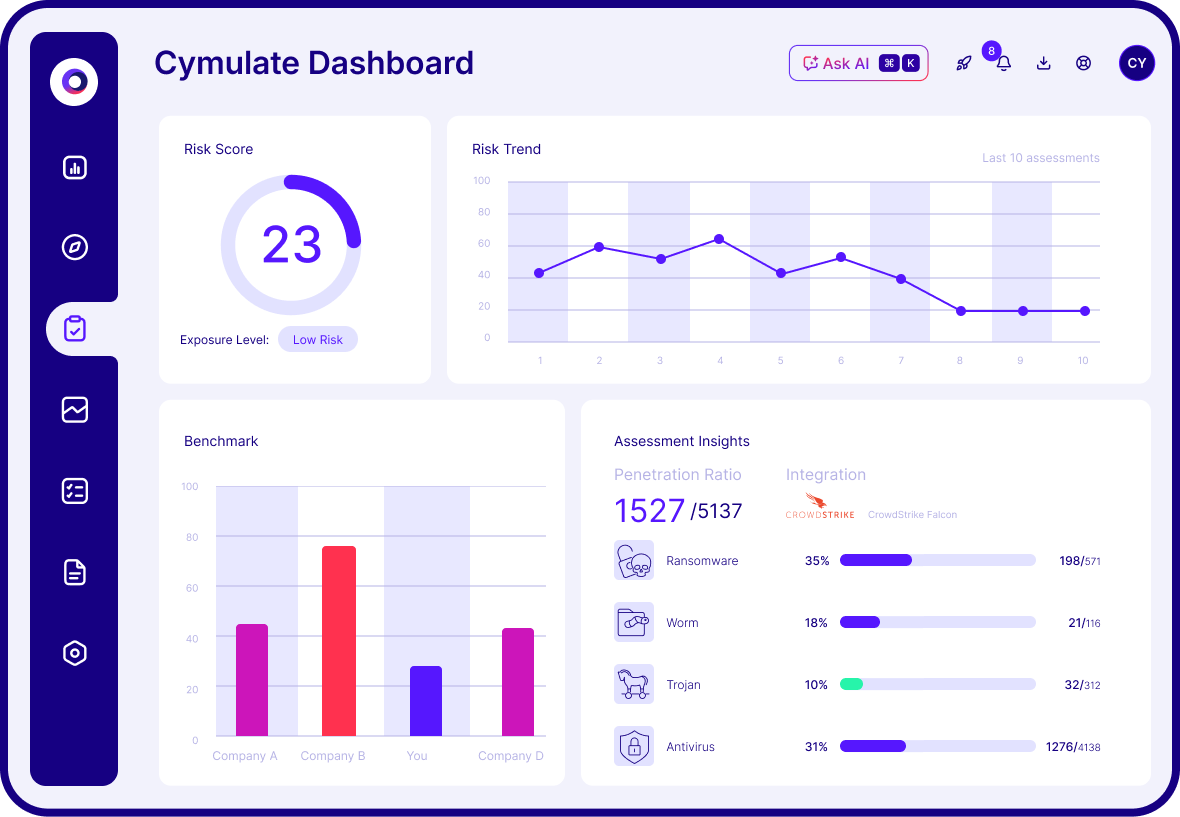
Know your threat exposure and mitigate your risk.


Optimize defenses
Improve threat resilience by strengthening your controls.


Measure resilience
Demonstrate progress and drive informed decision-making.


See Cymulate Exposure Validation in Action
Exposure Validation Benefits and Outcomes
Through automated testing and actionable insights, Cymulate Exposure Validation enables you to prove resilience against advanced threats, optimize security controls to close gaps and reduce risk, accelerate detection engineering, and measure and baseline your security posture.
<1 Hour
Test new threats
Automate continuous validation of threats with daily updates of new attacks and campaigns.
30%
Increase in threat prevention
Optimize threat prevention by finding your weaknesses and updating security controls.
3X
Increase in threat detection
Build, test and tune new threat detections in hours, not weeks with rules specific to your SIEM, EDR and XDR.
60%
Increase in team efficiency
Automate and streamline the most critical and resource-heavy tasks in modern SecOps.
Supported by Award-Winning Technology
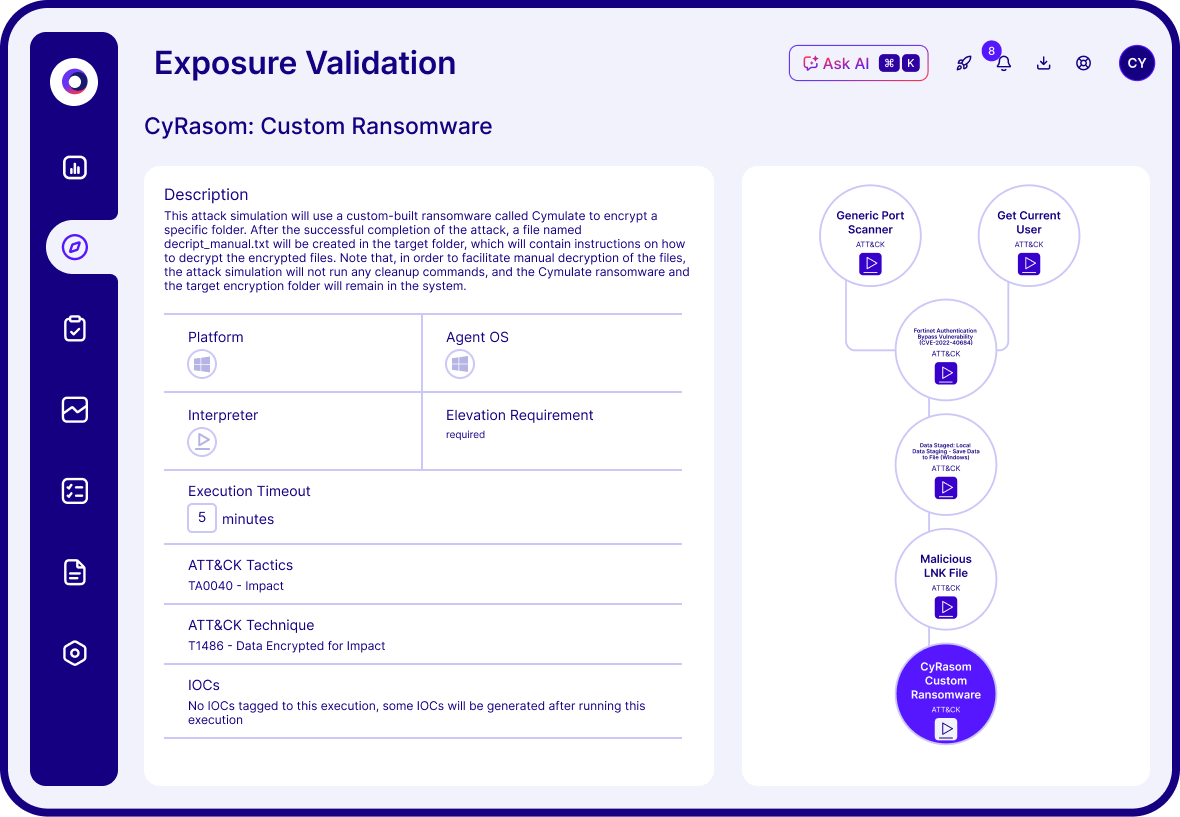
Powered by breach and attack simulation (BAS) and continuous automated red teaming (CART), Cymulate Exposure Validation delivers empirical proof of threat resilience through live, offensive testing.
Breach and Attack Simulation
BAS automates real-world attack scenarios to evaluate your security posture and verify defenses against the latest emergent threats and threat actors.
Continuous Automated Red Teaming
CART automates scalable security validation using real-world techniques to test for lateral movement and critical asset exposure.
Test, Tune and Optimize Your Cloud Architecture
Cymulate provides both pre- and post-exploitation simulations to test and validate the threat detection and runtime security controls for different layers of your cloud architecture.
What our customers say about us
Organizations across all industries choose Cymulate for automated cybersecurity validation, proactively confirming that defenses are robust and reliable-before an attack occurs.
Exposure Validation FAQs
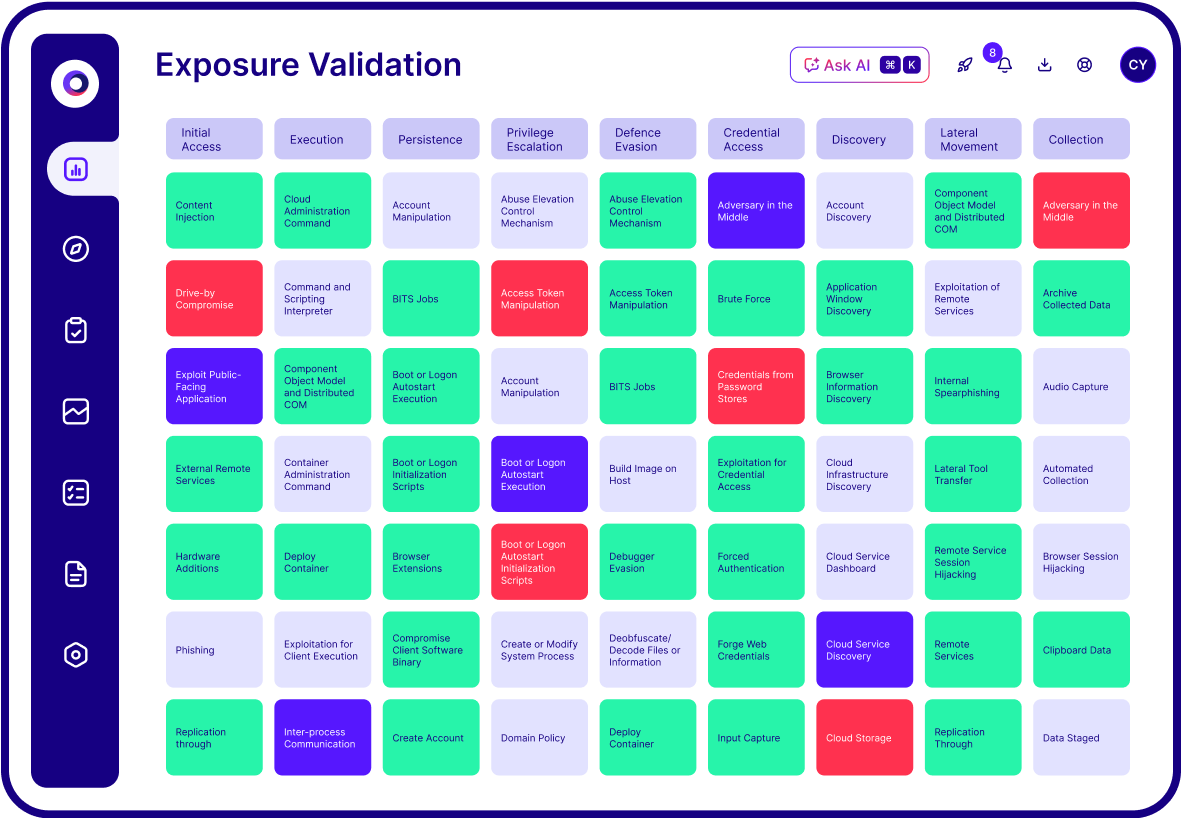
Exposure validation enhances threat detection by continuously testing whether security controls are functioning as intended against real-world attack techniques. By simulating adversarial behaviors in a safe environment, organizations can verify if threats are detected by their existing tools, such as EDR, SIEM and XDR systems. This proactive approach helps identify blind spots, misconfigurations and detection gaps, enabling security teams to fine-tune alerts, improve rule sets and ensure earlier, more accurate threat identification.
Cymulate drives exposure management by aggregating exposures from vulnerability scanners and discovery tools, correlating them with business context and validated threats. This ensures teams can focus on what truly matters, significantly improving threat resilience and operational efficiency.
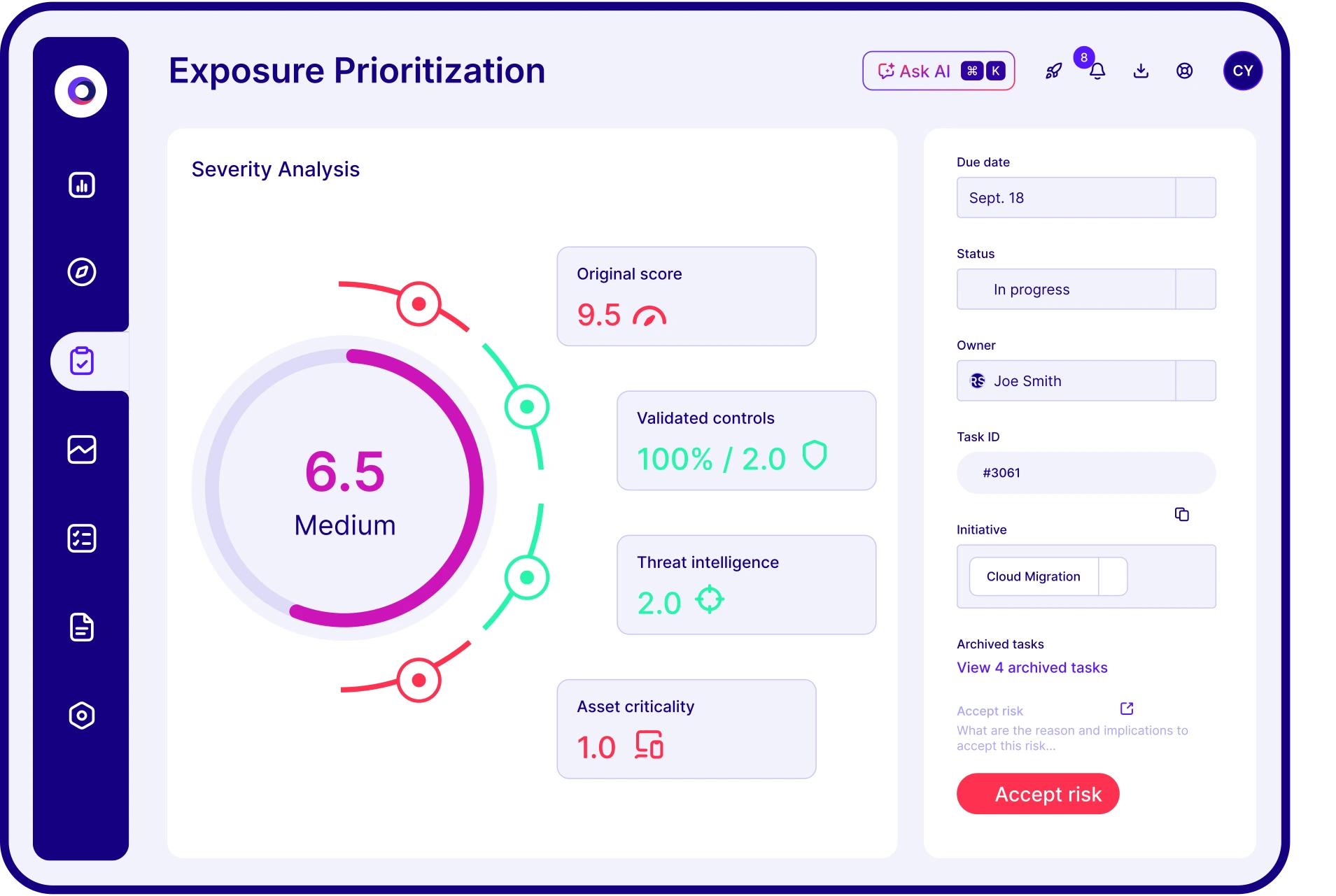
By identifying and closing security gaps before adversaries can exploit them, exposure validation is an integral part of a strategy around reducing cyber risk. By validating exposures in the context of an organization’s unique environment across endpoints, identities, networks and configurations, security teams can prioritize and remediate critical weaknesses based on validated impact.
This risk-based approach ensures resources are focused on the most exploitable paths, minimizing the attack surface and significantly lowering the likelihood and potential impact of a breach.
Exposure management is a broad strategy that encompasses identifying, assessing, prioritizing and mitigating security exposures across an organization. Exposure validation is a key component within that strategy, focusing specifically on confirming whether detected exposures are exploitable and if defenses effectively respond to them.
While exposure management is ongoing and strategic, exposure validation is tactical and evidence-based, providing the actionable insight needed to support informed risk decisions.
In red and purple teaming exercises, exposure validation is used to measure the effectiveness of both offensive and defensive operations.
- During red teaming, it confirms whether simulated attacks succeed in bypassing defenses and reaching critical assets.
- In purple teaming, exposure validation plays a collaborative role, validating whether the blue team detects and responds to attacks in real-time.
Measurable feedback is provided to both teams. Exposure validation helps close detection gaps and ensures that improvements are based on verified performance rather than assumptions.