How to Measure and Strengthen Your Cybersecurity Program
In the dynamic landscape of cybersecurity, the old approach of reactive defense—scrambling to address vulnerabilities only after they've been exploited—is increasingly seen as inadequate. The need for a shift in strategy has never been more pronounced, as highlighted in the Cymulate 2024 State of Exposure Management & Security Validation report. This shift towards a proactive cybersecurity stance is not just a trend but a necessary evolution in how security leaders approach ever-growing cyber threats.
Drawing from a rich dataset encompassing attack surface assessments, simulated attack scenarios and campaigns, and automated red teaming, the report sheds light on the practices of over 500 global Cymulate customers. It emphasizes a transition from reactive to proactive cybersecurity measures, focusing on identifying and closing security gaps before malicious actors can exploit them.
The following examples demonstrate why it's essential to take a proactive approach and stay ahead of vulnerabilities and post-exploitation threats.
Log4J: 2 Years Later and Still a Threat
One of the most telling examples of the persistent threat landscape is that the Log4j vulnerability, also known as Log4Shell (CVE: 2021-44228), was the most assessed in 2023. Last year alone, Cymulate released 15 new threat assessments related to Log4Shell, reflecting the ongoing need to stay vigilant and prepared against these enduring vulnerabilities.
First disclosed in December 2021, this critical vulnerability in the ubiquitous Apache logging library left countless Java-based applications susceptible to remote code execution. The incident disrupted the holiday season for numerous IT and security teams and remains a significant risk even years after its discovery. Its widespread impact and the ease with which it can be exploited made it a prime target for threat actors, prompting a flurry of urgent patching efforts worldwide. Despite the passage of time, unpatched systems continue to offer fertile ground for cybercriminals. The persistence of this vulnerability underscores a vital lesson: threats evolve, but they seldom disappear.
On average, 75% of web application firewalls (WAFs) demonstrated their ability to block exploits of the Log4Shell vulnerability. For the 2023 threats targeting Log4shell, endpoint security and web gateway protection showed security effectiveness from 62% to 89% to protect against post-exploit threat activity in these campaigns.
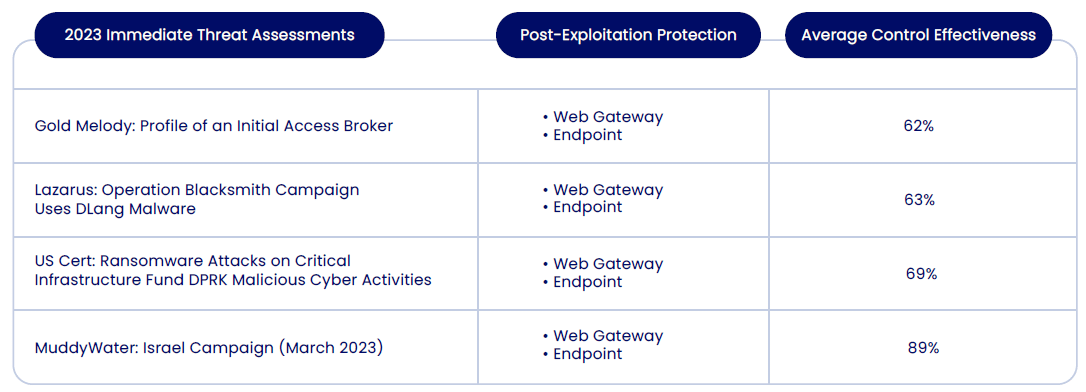
These numbers highlight the importance of continuous improvement and updates in security solutions. Additionally, organizations should not only rely on a single type of security measure but should implement a layered security approach. Regularly testing, patching, and configuring security tools are crucial to enhancing their effectiveness.
MuddyWater: Israel Campaign (March 2023): The Importance of “Assume Breach”
While protecting against vulnerability exploitation is essential, ensuring your organization’s controls can protect you from post-exploitation activity in case of a breach is just as important. Cymulate customers that ran the MuddyWater: Israel Campaign assessment, which tests their web gateway and endpoint solutions against post-exploit threat activity of the Log4Shell vulnerability, were 89% effective in protecting their organizations with those controls.
The Iranian hacker group MuddyWater, known for its sophisticated cyber operations, exploited the Log4Shell vulnerability to enhance its cyber espionage capabilities. This vulnerability allowed MuddyWater to infiltrate and persist within target networks. By exploiting this flaw, they could deploy malicious payloads, maintain a stealthy presence, and extract sensitive information, aligning with their espionage and system compromise objectives.
This incident accentuates the importance of adopting an "assume breach" mindset in cybersecurity: organizations should operate under the assumption that their defenses have already been compromised. This shift advocates for a more proactive and resilient security posture, focusing on detection, response, and recovery capabilities rather than solely on prevention.
One key method organizations use to enhance threat detection is through Sigma rules, a standardized approach for writing security detection rules that work across SIEM and log management platforms. By leveraging Sigma rules, security teams can quickly translate known attack patterns—such as those used by MuddyWater—into actionable threat detection logic, improving their ability to spot and mitigate post-exploitation activities.
It emphasizes the need for continuous monitoring, incident response planning, regular security assessments, and user training to detect and mitigate threats swiftly, thereby reducing the dwell time of attackers and limiting the potential damage they can inflict. In the context of the Log4Shell exploitation, such an approach would entail rapid identification of strange activities, immediate containment of the threat, and swift remediation of the exploited vulnerabilities, illustrating the indispensable role of resilience and preparedness in modern cybersecurity strategies.
The Cymulate Approach to Cyber Resilience
Cymulate offers a comprehensive view of an organization's defensive capabilities, focusing on comprehensive, customizable, and real-time cybersecurity assessments on-prem and in the cloud. Simulating a range of cyber threats to test and optimize an organization's security posture ensures preparedness against potential attacks and evolving threats—like those targeting Log4Shell.
This proactive approach to cybersecurity, emphasized by adopting exposure management and security validation practices, is a testament to the evolving understanding of what it means to be secure in a digital age. It shifts from the conventional, reactive find-fix routines to a strategic, “assume breach” mindset, where threats are anticipated and factored into the organization’s defensive strategy, ensuring continuous preparedness and the ability to neutralize threats proactively.
By adopting a proactive posture, organizations can enhance their security resilience, reduce their attack surface, and better allocate their resources. It transforms the narrative from one of constant emergency responses to a more controlled, predictable, and effective security strategy. This improves security posture and aligns cybersecurity efforts more closely with the organization's broader business objectives.
The 2024 State of Exposure Management & Security Validation report is more than just an aggregation of data; it's a call for a paradigm shift in cybersecurity practices. The continued relevance of vulnerabilities like Log4Shell is a stark reminder of the cyber threats in the wild. However, through proactive exposure management and rigorous security validation, organizations can anticipate and disarm these threats before they strike. This proactive cybersecurity approach is not merely a strategic advantage—it's an essential cornerstone of modern cyber defense strategies.