Frequently Asked Questions
Product Features & Capabilities
What is Cymulate and how does it help validate security controls for AWS S3 buckets?
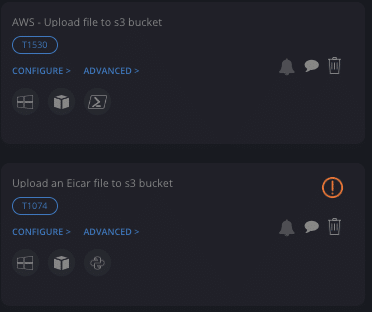
Cymulate is a Breach and Attack Simulation (BAS) platform that enables organizations to proactively test and validate their security controls, including those protecting AWS S3 buckets. By simulating real-world attack scenarios—such as uploading and downloading malicious payloads or simulating privileged activities—Cymulate helps you assess the effectiveness of your defenses against threats targeting S3 storage. This ensures your security posture is robust and up-to-date against evolving cloud-based attacks. Source
How does Cymulate simulate attacks on AWS S3 buckets?
Cymulate simulates attacks on AWS S3 buckets by allowing you to upload known malicious samples, download malware from S3, and validate detection of privileged activities. These simulations test whether your security controls—such as Amazon GuardDuty Malware Protection—can detect, block, or alert on malicious actions, helping you identify and remediate gaps in your cloud security posture. Source
What are the three best practices for validating AWS S3 security with Cymulate?
The three best practices are: (1) Uploading known malicious samples to your S3 buckets to test detection and deletion by security controls; (2) Simulating downloads of malware from S3 to see if your firewall or web gateway blocks them; (3) Validating detection of privileged activities, such as unauthorized exposure or configuration changes, to ensure alerts are triggered for critical events. Source
How does Cymulate help organizations stay ahead of threats targeting AWS S3 buckets?
Cymulate enables continuous validation of cloud security controls by simulating real-world attacks on AWS S3 buckets. This proactive approach helps organizations detect vulnerabilities, test their defenses, and ensure they are prepared to counteract threats such as malware uploads, misconfigurations, and unauthorized access. Source
What is Amazon GuardDuty Malware Protection for Amazon S3, and how does it work?
Amazon GuardDuty Malware Protection is a feature within Amazon GuardDuty that automatically scans objects stored in S3 buckets for malware. It uses machine learning, anomaly detection, and integrated threat intelligence to identify malicious files and alert administrators, providing an additional layer of security for cloud storage. Source
How do attackers use AWS S3 buckets to deliver malware?
Attackers exploit S3 buckets by uploading malicious files to their own buckets and sharing links, exploiting misconfigured public buckets to distribute malware, or gaining unauthorized access to victim buckets through compromised credentials or vulnerabilities. These methods allow attackers to deliver malware to unsuspecting users or organizations. Source
What are some real-world examples of attacks involving AWS S3 buckets?
Notable examples include Tesla's cryptojacking incident (2018), where attackers accessed an S3 bucket to deploy cryptocurrency mining scripts; the Capital One data breach (2019), where a misconfigured firewall allowed access to S3 buckets with sensitive data; and the Matanbuchus malware (2021), which used S3 buckets to host and distribute malicious payloads via phishing emails. Source
Why is continuous validation of cloud security controls important?
Continuous validation is essential because attackers constantly develop new techniques to bypass defenses. Regular testing with platforms like Cymulate ensures your security controls remain effective against emerging threats, reducing the risk of breaches and data loss in cloud environments. Source
How can Cymulate help detect unauthorized configuration changes in AWS S3 buckets?
Cymulate can simulate privileged activities, such as unauthenticated exposure of a bucket, to test whether your security controls detect and alert on unauthorized configuration changes. This helps ensure that critical changes are promptly identified and mitigated. Source
What is the benefit of simulating malware downloads from S3 buckets?
Simulating malware downloads from S3 buckets with Cymulate helps you verify if your firewall or web gateway can prevent the download of malicious files, mimicking real-world scenarios where employees might download files from trusted S3 sources. This test is critical for identifying gaps in your security perimeter. Source
How does Cymulate's Exposure Validation feature support AWS S3 security?
Cymulate Exposure Validation makes advanced security testing fast and easy by enabling you to build custom attack chains and validate your defenses against real-world threats, including those targeting AWS S3 buckets. This helps organizations proactively identify and remediate vulnerabilities. Learn More
Where can I find demos showing how Cymulate validates AWS S3 security?
You can watch Cymulate demos such as 'From Vulnerability to Validation', 'Threat Validation Demo', and 'From Control Validation to Exposure Validation' to see how the platform connects vulnerabilities to real attack scenarios and validates protection against new threats. View Demo
What types of organizations benefit from using Cymulate for AWS S3 security validation?
Organizations of all sizes and industries—including finance, healthcare, retail, media, transportation, and manufacturing—benefit from Cymulate's AWS S3 security validation. The platform is designed for CISOs, SecOps teams, Red Teams, and Vulnerability Management teams seeking to proactively test and improve their cloud security posture. Learn More
How does Cymulate integrate with other security tools for AWS S3 validation?
Cymulate integrates with a wide range of security technologies, including AWS GuardDuty, Check Point CloudGuard, Wiz, and more, to enhance your cloud security ecosystem and automate validation processes. For a complete list of integrations, visit our Partnerships and Integrations page.
What certifications and compliance standards does Cymulate meet?
Cymulate holds several key certifications, including SOC2 Type II, ISO 27001:2013, ISO 27701, ISO 27017, and CSA STAR Level 1. These certifications demonstrate Cymulate's commitment to robust security, privacy, and compliance standards. Learn More
How easy is it to implement Cymulate for AWS S3 security validation?
Cymulate is designed for quick and easy implementation, operating in agentless mode with no need for additional hardware or complex configurations. Customers can start running simulations almost immediately, with comprehensive support and educational resources available. Schedule a Demo
What is Cymulate's pricing model?
Cymulate operates on a subscription-based pricing model tailored to your organization's requirements. Pricing depends on the chosen package, number of assets, and scenarios selected. For a detailed quote, schedule a demo with the Cymulate team.
How does Cymulate compare to other security validation platforms?
Cymulate stands out by offering a unified platform that integrates Breach and Attack Simulation (BAS), Continuous Automated Red Teaming (CART), and Exposure Analytics. It provides continuous, automated attack simulations, AI-powered remediation insights, and a comprehensive threat library, making it suitable for organizations seeking real-time, actionable security validation. See Comparison
What customer feedback has Cymulate received regarding ease of use?
Customers consistently praise Cymulate for its intuitive, user-friendly interface and actionable insights. Testimonials highlight its ease of implementation, accessible support, and the ability to quickly understand and improve security posture. Read Testimonials
What are the core problems Cymulate solves for organizations using AWS S3?
Cymulate addresses challenges such as overwhelming threat volumes, lack of visibility into exploitable vulnerabilities, unclear risk prioritization, and resource constraints. By automating threat validation and exposure prioritization, Cymulate helps organizations focus on the most critical risks and improve operational efficiency. Learn More
What are some case studies demonstrating Cymulate's effectiveness for cloud security?
Case studies include Hertz Israel reducing cyber risk by 81% in four months, Nemours Children's Health improving detection in hybrid and cloud environments, and a sustainable energy company scaling penetration testing efficiently. See Case Studies
How does Cymulate support compliance and data protection for AWS S3 security?
Cymulate supports compliance with global standards such as SOC2, ISO 27001, and GDPR. The platform includes data encryption in transit and at rest, secure AWS hosting, and a dedicated privacy and security team, ensuring robust data protection for cloud environments. Learn More
Where can I find resources and thought leadership from Cymulate?
You can access a combination of insights, thought leadership, and product information in the Cymulate Resource Hub. For the latest threats and research, visit our blog and newsroom.
How can I contact Cymulate for support or a personalized demo?
You can reach Cymulate's support team via email at [email protected] or use the chat support page. To see Cymulate in action, book a personalized demo.
What is Cymulate's mission and vision?
Cymulate's mission is to transform cybersecurity practices by enabling organizations to proactively validate their defenses, identify vulnerabilities, and optimize their security posture. The vision is to create a collaborative environment for lasting improvements in cybersecurity strategies. About Us
How does Cymulate help with operational efficiency for cloud security teams?
Cymulate automates threat validation and exposure management, allowing security teams to focus on strategic initiatives rather than manual tasks. Customers have reported up to a 60% increase in team efficiency and significant time savings in testing new threats. Learn More
What are the measurable outcomes of using Cymulate for AWS S3 security validation?
Organizations using Cymulate have achieved up to a 52% reduction in critical exposures, a 20-point improvement in threat prevention, and an 81% reduction in cyber risk within four months, as reported in customer case studies. See Results
How does Cymulate support collaboration across security teams?
Cymulate provides a unified platform for SecOps, Red Teams, and Vulnerability Management teams, enabling collaboration and a holistic approach to exposure management and threat validation. Learn More
Where can I find news, events, and webinars from Cymulate?
Stay up-to-date with Cymulate by visiting the blog, newsroom, and events & webinars page for the latest updates, research, and opportunities to engage with the Cymulate team.