What Is Detection Engineering?
Detection Engineering Explained: A Structured Approach to Threat Detection
Detection engineering is a specialized cybersecurity discipline focused on the structured process of designing, implementing, testing and maintaining detection logic that identifies malicious activity in an environment.
In essence, it involves building reliable detection systems (rules, analytics, and alerts) that catch threats in real time before they can cause damage while also minimizing false alarms.
This practice aligns security teams around continuously developing and tuning high-fidelity detection logic – the queries, signatures, and algorithms that recognize adversary behaviors – so that Security Operations Centers (SOCs) can respond to threats swiftly and confidently.
Why Detection Engineering Matters More Than Ever
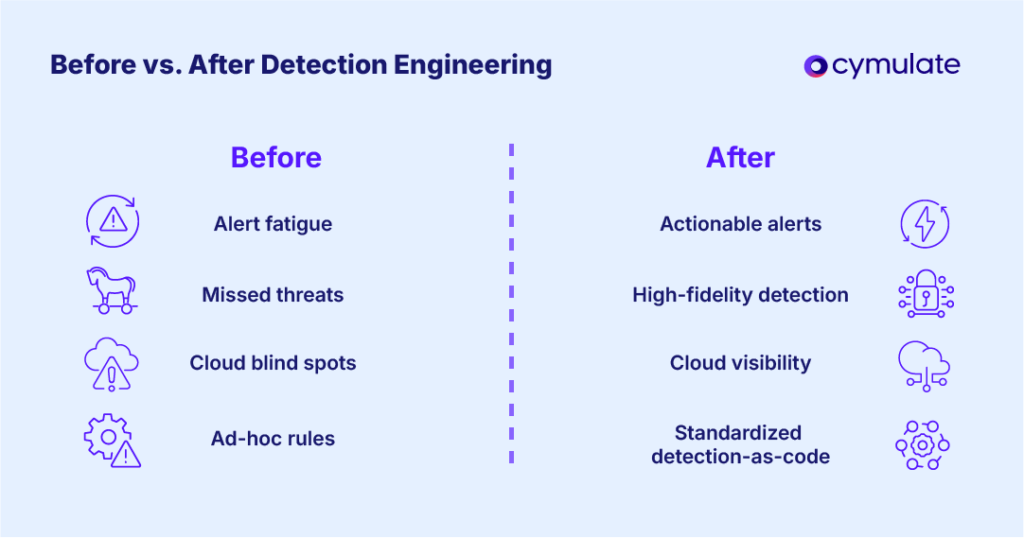
Traditional, ad-hoc detection methods struggle to keep up in current environments. Modern SOCs often complain of “drowning in alerts” or missing critical threats – symptoms of alert fatigue and detection gaps in complex environments.
Detection engineering has emerged as a practical threat detection engineering approach to address these challenges by systematically improving how threats are detected across on-premises and cloud systems.
In cloud and hybrid environments, security telemetry comes from dynamic sources (cloud APIs, containers, serverless functions, etc.), requiring structured engineering to data pipelines, log management and analytics.
By applying detection engineering principles, security teams can adapt to new attacker tactics in these fast-moving environments, ensuring they have visibility into cloud control planes, ephemeral workloads, and automated processes that were previously blind spots.
Objectives of Detection Engineering for High-Fidelity Detection
The core objective of detection engineering is to achieve high-fidelity, actionable threat detection. This means developing detections that accurately identify true malicious behavior (high signal) with minimal false positives (low noise), so analysts can trust and act on alerts.
A high-fidelity detection capability improves the signal-to-noise ratio and helps reduce wasted effort on benign events.
Detection engineering programs commonly align their content with frameworks like MITRE ATT&CK to ensure comprehensive coverage of adversary tactics, techniques and procedures (TTPs).
Every detection is designed with context and intelligence so that it’s immediately actionable – for example, an alert might map to a specific MITRE ATT&CK technique and include details on the affected host/user, enabling quick triage.
By mapping detection rules to MITRE ATT&CK, teams can perform gap analysis to identify which techniques are not yet covered and prioritize developing those detections. Ultimately, detection engineering’s goal is a threat-informed defense: the SOC knows what threats matter, has detections for them and can catch attackers early in the kill chain with confidence.
Key Benefits
A robust detection engineering practice delivers several important benefits for security teams:
- Reduced Alert Fatigue and Noise: Structured detection engineering reduces false positives and redundant alerts by continually tuning detection rules, fine-tuning thresholds, and enriching alerts with context. This prevents analyst overload, resulting in fewer but more meaningful alerts.
- Actionable alerts and faster response: High-quality, contextual alerts enable quicker investigation and containment, significantly reducing Mean Time To Detect (MTTD) and Mean Time to Respond (MTTR). Early threat identification allows teams to address incidents swiftly, minimizing their impact.
- Enabling proactive threat hunting: Effective detection automation frees security teams to focus on proactive threat hunting, investigating sophisticated threats beyond automated detection. Findings from threat hunting then inform detection rule improvements, continually enhancing coverage.
- Improved SOC efficiency and focus: A mature detection engineering program boosts SOC productivity by minimizing attention to benign alerts and enhancing incident response workflows. Detection-as-code standardizes detection practices, enabling scalability, consistency and cost-effective resource allocation.
- Continuous adaptation to evolving threats: Detection engineering promotes ongoing adaptation to evolving attacker techniques through continuous rule updates. This adaptation is informed by threat intelligence and frameworks like MITRE ATT&CK. This agile approach ensures security monitoring remains effective, especially in rapidly changing cloud or DevOps environments.
How Detection Engineering Works: Lifecycle and Core Components
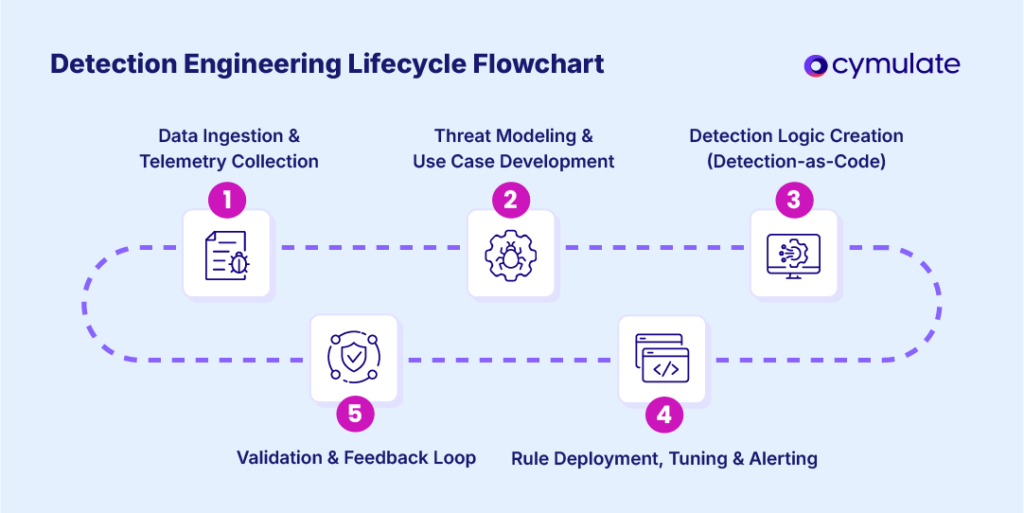
Detection engineering involves a structured, ongoing lifecycle with clear steps and continuous improvement:
Data ingestion and telemetry collection
Effective detection begins by collecting and centralizing logs and telemetry from endpoints, servers, networks, cloud services and applications.
Logs are enriched with contextual data (e.g., asset importance, user roles, threat intelligence) and stored in a centralized platform (like Splunk or ELK) for analysis, ensuring comprehensive visibility.
Threat modeling and use case development
Teams identify and prioritize threats relevant to their organization using frameworks like MITRE ATT&CK, performing gap analysis to uncover detection blind spots.
This produces prioritized detection use cases and clear analytic requirements that target actual attacker behaviors.
Detection logic creation (Detection-as-Code)
Engineers develop detection rules and analytics using standardized, platform-agnostic formats (like Sigma or YARA) and manage them through software engineering practices (version control, testing, CI/CD pipelines). Rules are tested against historical data to validate effectiveness before deployment, ensuring reusability and scalability.
Rule deployment, tuning, and alerting
Detection rules are deployed into monitoring platforms (e.g., SIEMs, EDR solutions) and fine-tuned continuously based on production performance. Engineers adjust rules to minimize false positives and maximize accuracy, iteratively refining detection mechanisms and aligning alerts to actionable security events.
Validation and feedback loop
Detection content is regularly validated through red-team exercises, automated attack simulations, and real-world incidents.
Post-incident reviews provide critical feedback, guiding rule improvements. Teams continuously update detection logic, tracking performance metrics to evolve alongside changing threats.
Throughout this lifecycle, collaboration among detection engineers, threat intelligence teams, incident responders, and threat hunters ensures comprehensive and up-to-date detection coverage.
Tools and Techniques
A variety of tools and frameworks support the detection engineering process:
SIEM and log management platforms
SIEM platforms like Splunk, Microsoft Sentinel, IBM QRadar, or the open-source ELK Stack aggregate logs and execute detection rules in real-time.
Cloud-native SIEMs, such as Azure Sentinel, handle cloud telemetry effectively and offer built-in threat detection rules that engineers can extend.
Rule and signature repositories (Sigma, YARA, etc.)
Sigma provides an open, YAML-based rule format easily converted to multiple SIEM languages, promoting rule-sharing and reuse across organizations.
Similarly, YARA rules detect malware based on files or memory patterns. Managing these detections as code (using version control) facilitates collaboration and efficiency.
Behavioral analytics and UEBA
User and Entity Behavior Analytics (UEBA) tools employ heuristics and machine learning to detect anomalous behavior that static rules might miss, like unusual login patterns.
Detection engineers integrate and tune these behavioral models alongside rule-based systems to detect stealthy or novel threats.
Threat intelligence integration
Detection engineering uses threat intelligence feeds (malicious IPs, file hashes, attacker TTPs) to enrich alerts and detection rules.
This alignment ensures detections remain current against known adversaries and evolving threats, leveraging frameworks like MITRE ATT&CK.
Automation and CI/CD for detection (Detection-as-Code)
Teams increasingly use DevOps practices and automation for managing detection logic, employing CI/CD pipelines and infrastructure-as-code to deploy, test, and iterate detection rules rapidly and reliably. This reduces human error and streamlines detection development.
By combining these tools and techniques, detection engineering becomes systematic, scalable, and repeatable, leveraging community-shared rules, behavioral analytics, and robust automation frameworks.
Challenges and Shifts in Cloud Detection Engineering
Cloud-native environments introduce new complexities that reshape traditional detection engineering methods:
- API and control plane visibility: In cloud environments (AWS, Azure, GCP), critical security events often occur via APIs, invisible to traditional monitoring. Detection engineers must focus on analyzing cloud audit logs (CloudTrail, Azure Activity Logs, GCP Audit Logs) to detect suspicious activities, like unauthorized API actions or IAM changes, effectively addressing this new attack surface.
- Ephemeral and elastic resources: Cloud workloads (containers, serverless functions) can rapidly appear and disappear, complicating persistent monitoring. Engineers need to employ centralized, agentless logging (e.g., Kubernetes audit logs), real-time analytics, and cloud-native security tools (AWS GuardDuty, Azure Defender) enhanced with custom detection logic to effectively monitor short-lived, dynamic resources.
- Behavioral baselines in cloud environments: Cloud applications typically exhibit predictable behavior, enabling detection engineers to build behavioral analytics that flag abnormal activities (e.g., unusual network requests from serverless functions). However, distinguishing legitimate changes from malicious behavior requires close collaboration with DevOps teams for contextual understanding.
- Multi-cloud and log integration: Operating across multiple cloud providers and on-premises infrastructure creates fragmented logging, complicating detection efforts. Engineers must centralize and normalize logs, using cloud-native SIEMs, data lakes, or emerging standards (e.g., Open Cybersecurity Schema Framework) to correlate events across different cloud platforms and eliminate blind spots.
- Cloud-native tooling and techniques: Detection engineers utilize cloud-native security features (Azure Sentinel, AWS GuardDuty, Kubernetes monitoring tools) as a baseline, supplementing them with custom detections.
Infrastructure-as-code scanning and pre-runtime checks enhance detection capabilities. Automation, such as detection-as-code and continuous validation through simulated attacks, becomes critical for adapting to fast-moving cloud environments.
Despite advancements, challenges remain, including limited log retention periods and visibility gaps (e.g., encrypted traffic). Engineers must navigate these constraints by adopting creative solutions like traffic mirroring or sensor deployment when necessary.
Limitations and Considerations of Detection Engineering
While detection engineering vastly improves an organization’s security posture, it is not a silver bullet. There are important limitations and ongoing challenges to acknowledge:
Evolving threats and detection gaps
Detection engineering must constantly adapt as attackers evolve new evasion techniques. Blind spots and unknown threats persist, highlighting the need for ongoing updates, threat hunting, and intelligence efforts alongside detection engineering.
False negatives vs. false positives
Balancing sensitivity and precision can be challenging. Over-tuning detection rules to reduce false positives may inadvertently cause false negatives (missed threats). Continuous testing helps calibrate this balance to ensure critical threats are not overlooked.
Resource and overhead
Detection engineering demands skilled staff, significant time investment, and substantial tooling infrastructure. Computational overhead from complex analytics can impact performance and incur costs. Organizations must foster the right culture and management support to sustain continuous detection improvement.
Integration and data quality issues
Effective detection relies heavily on high-quality, correctly integrated data. Problems such as missing log sources, parsing errors, or siloed security tools can undermine detections. Establishing reliable data pipelines and integrating security platforms remain persistent challenges.
Alert overload if not done right
Deploying excessive or inadequately tuned detection rules can overwhelm analysts, recreating alert fatigue. It’s critical to prioritize quality over quantity, regularly prune ineffective detections, and maintain rigorous review processes to prevent overload.
While detection engineering significantly enhances threat detection, acknowledging these limitations helps organizations proactively address challenges, maintain realistic expectations, and integrate it effectively within a broader defense-in-depth strategy.
Enhancing Detection Engineering with Continuous Validation Through Cymulate
Validating Detection Logic
Cymulate is a continuous security validation platform that helps organizations test and improve their SIEM, EDR and XDR detection and response capabilities using simulated attacks. It acts as an automated feedback loop, helping detection engineers verify whether alerts fire as expected during real-world attack scenarios.
Using breach and attack simulation and automated red teaming, Cymulate simulates full attack chains (e.g., credential dumping or cloud breaches) and checks if detections trigger, highlighting any gaps in telemetry or rule logic.
Learn More: Accelerate Detection Engineering By Cymulate
Optimizing and tuning rules
Cymulate also assists in fine-tuning detection rules by analyzing how security tools respond to simulations. If alerts are too noisy or don’t trigger at all, engineers can adjust rule logic and immediately re-test.
The Cymulate Exposure Validation Platform offers relevant IoCs, indicators of behavior, pre-built Sigma rules and EDR rules as part of its remediation guidance. This helps organizations focus on tuning logic instead of building it from scratch.
This means if a gap is found (say, no alert for a certain ransomware behavior), Cymulate might supply a Sigma rule to fill that gap, accelerating the detection engineering effort. Cymulate even offers translations of Sigma rules to vendor-specific systems, further increasing tuning efficiency and accuracy.
Supporting SOC and MSSP Models
Whether used by internal SOC teams or MSSPs managing multiple clients, Cymulate enhances detection efforts through automation. It allows for frequent, safe validation runs in production-like environments, helping security teams avoid waiting for periodic red-team exercises.
MSSPs benefit from Cymulate’s cross-platform integration, enabling consistent detection validation across diverse tech stacks. It also supports purple teaming for enhanced collaboration between red and blue teams.
Benchmarking Detection Maturity
Cymulate provides quantifiable insights into detection program effectiveness by mapping outcomes to frameworks like MITRE ATT&CK.
Cymulate can help find detection gaps with actionable threat modeling via a MITRE heatmap and guides teams directly to where new detection rules are needed, or existing ones that require improvement.
It generates heatmaps and resilience scores, tracks improvements over time, and benchmarks performance against industry peers. These reports help justify security investments and guide focus areas in detection engineering.
Cymulate strengthens detection engineering by validating that detection logic works against real threats, pinpointing gaps, and enabling rapid tuning. Automation, attack simulations and integrations create a continuous improvement cycle for threat detection. This approach is becoming a best practice for modern SOCs seeking proactive, data-driven defense readiness.


