NIST Compliance Checklist: A Practical Guide to Cybersecurity Alignment

Threats are everywhere in digital business. As such, regulatory alignment can’t just be a best practice. It’s time for a reality check: these regulations exist to keep your business and the ecosystem at large safe.
If you’re looking to bolster your cybersecurity resilience, align with federal standards, or prepare for rigorous audits, the National Institute of Standards and Technology (NIST) Cyber Security Framework (CSF) is a cornerstone for structured improvement.
The CSF can help you build, manage and continuously validate a robust cybersecurity program.
This guide breaks down essential NIST publications, walks through the five steps to compliance, provides a detailed checklist and explains how Cymulate can empower your compliance journey.
Understanding the NIST Framework
The NIST CSF was introduced to improve critical infrastructure cybersecurity in the U.S. and has since become a global standard. Rooted in voluntary guidance, it supports organizations of all sizes in managing and mitigating cybersecurity risk.
The framework reaches beyond federal agencies and impacts defense contractors, healthcare organizations, financial institutions and any company managing sensitive or regulated data. Adopting CSF not only improves security posture but often satisfies broader compliance requirements, including those related to GDPR, HIPAA and CMMC.
Key NIST Compliance Publications
Understanding which NIST publications apply to your organization is essential. Here's a breakdown of the most referenced standards:
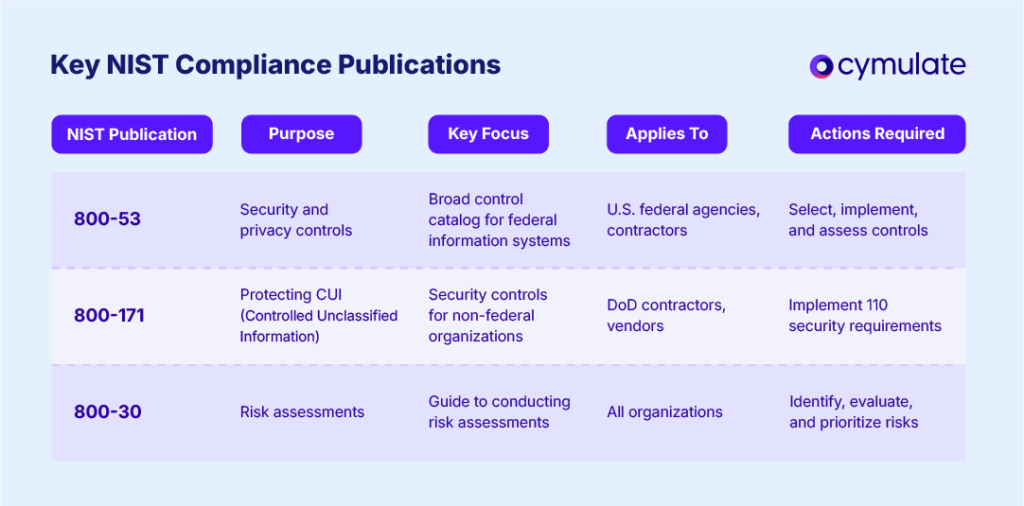
Each of these standards contributes a foundational layer to a well-rounded cybersecurity framework and should be part of your NIST compliance strategy.
The Five Steps to Achieve NIST Compliance
NIST’s Cybersecurity Framework is organized around five core functions that provide a strategic view of the lifecycle of cybersecurity risk:
1. Identify
Establish an understanding of your business environment, assets, data and associated risks. Conduct asset inventory, understand fully your governance and compliance requirements and undergo necessary risk assessments (per NIST 800-30).
2. Protect
Implement safeguards to limit or contain the impact of cybersecurity events. Get a clear handle on your access controls, cybersecurity awareness training practices, data security policies and endpoint hardening based on NIST hardening standards.
3. Detect
Develop and implement mechanisms to identify cybersecurity incidents. There are a number of ways organizations can approach this, but you’ll need to ensure your threat detection systems, security information and event management (SIEM) and continuous monitoring capabilities meet your needs.
4. Respond
Take action when a cybersecurity incident is detected. Develop and understand your incident response plans, communication protocols and mitigation strategies. Attacks and breaches can happen no matter how strong your security posture. It’s critical to have these processes in place as a result.
5. Recover
Restore capabilities and services impacted by cybersecurity incidents. To do this effectively, you’ll need to ensure your recovery planning is up to date, your backup procedures are in place and you conduct post-incident reviews to learn and plan for the future.
NIST Compliance Checklist
Use the following NIST compliance checklist to guide your program implementation. Each item is an actionable step tied to best practices and NIST guidance:
- Understand applicable NIST standards
Identify which publications (e.g., 800-53, 800-171, 800-30) apply to your organization based on industry and data handled. - Perform a gap assessment
Conduct a detailed comparison between your current controls and NIST requirements. - Define and document risk management policies
Establish formalized policies that map to the risk management framework outlined by NIST. - Manage and classify assets and data
Create a comprehensive asset inventory and classify data based on sensitivity and value. - Implement safeguards (Protect Function)
Deploy protective technologies and practices, including encryption, MFA, access controls, and secure configurations. - Deploy detection mechanisms
Integrate real-time monitoring and alerting systems for anomaly and intrusion detection. - Develop and test incident response plans
Create and regularly rehearse playbooks for breach response and communication. - Establish recovery processes
Implement systems for data backup, disaster recovery, and business continuity. - Manage third-party risk
Use a NIST third-party compliance checklist to evaluate vendors and partners. - Continuously monitor and validate security controls
Use automated testing, audits, and assessments to verify control effectiveness. - Prepare for audits
Maintain documentation and evidence to support a NIST audit checklist review. - Conduct employee training and awareness programs
Train staff on security best practices, phishing resistance, and compliance responsibilities. - Review and update compliance strategies regularly
Treat compliance as a living process that evolves with threats, technologies, and regulations.
How Cymulate Helps Organizations Stay NIST Compliant
Achieving and maintaining NIST compliance is not a one-time exercise—it requires continuous validation and improvement. That’s where the Cymulate Exposure Validation platform excels.
Here’s how Cymulate aligns with and supports the NIST CSF:
- Identify: Cymulate provides a real-time view of asset exposure through automated discovery and attack surface mapping.
- Protect: The platform validates the effectiveness of deployed security controls through simulated attacks based on NIST-compliant scenarios.
- Detect: Cymulate evaluates detection and alerting capabilities, enabling organizations to tune SIEMs and SOCs accordingly.
- Respond: By testing incident response capabilities, Cymulate ensures teams can detect, analyze and mitigate threats quickly.
- Recover: Post-exercise reports help refine recovery procedures and improve resilience.
Additionally, Cymulate supports risk quantification and compliance mapping, helping teams directly align results with NIST guidelines and compliance requirements.
Key Takeaways
Implementing a NIST-compliant cybersecurity strategy may seem daunting but the benefits greatly outweigh the downside of going through these exercises. By following a structured framework, referencing the correct publications and using tools like Cymulate to validate and enhance your controls, your organization can:
- Strengthen its cybersecurity posture
- Satisfy regulatory obligations
- Minimize the impact of cyber incidents
- Be fully prepared for audits and reviews
Security and compliance professionals don’t need to go it alone. Explore how Cymulate can support your NIST compliance journey and deliver actionable insights that drive measurable improvements.



