How to Stay Ahead of IoT Security Issues
From connected medical equipment in smart hospitals to telemetry sensors in industrial plants, Internet of Things (IoT) devices are now deeply embedded in enterprise infrastructure.
But this surge in connectivity has come with a corresponding rise in cyber risk, driven by increased attack surfaces, complex IT/OT convergence and persistent visibility challenges.
Understanding and mitigating IoT security issues is essential for any cybersecurity professional tasked with protecting critical environments. We'll break down the most pressing IoT security concerns and provide actionable strategies to proactively address them.
IT, OT and IoT Security: Defining the Landscape
First, let’s level-set on some terminology.
IT (Information Technology) refers to the digital backbone of most organizations - networks, endpoints and data systems.
OT (Operational Technology) governs industrial operations - machinery, control systems and critical infrastructure.
IoT (Internet of Things) sits at the intersection, introducing connected devices that often bridge both IT and OT realms.
This convergence has created hybrid ecosystems where traditional controls, like endpoint detection or static firewalls, often fall short. IoT devices are typically lightweight, decentralized and built with different priorities than traditional IT hardware. That makes managing and securing them particularly complex, especially when they operate within critical environments like hospitals or power grids.
Top IoT Security Issues and Solutions
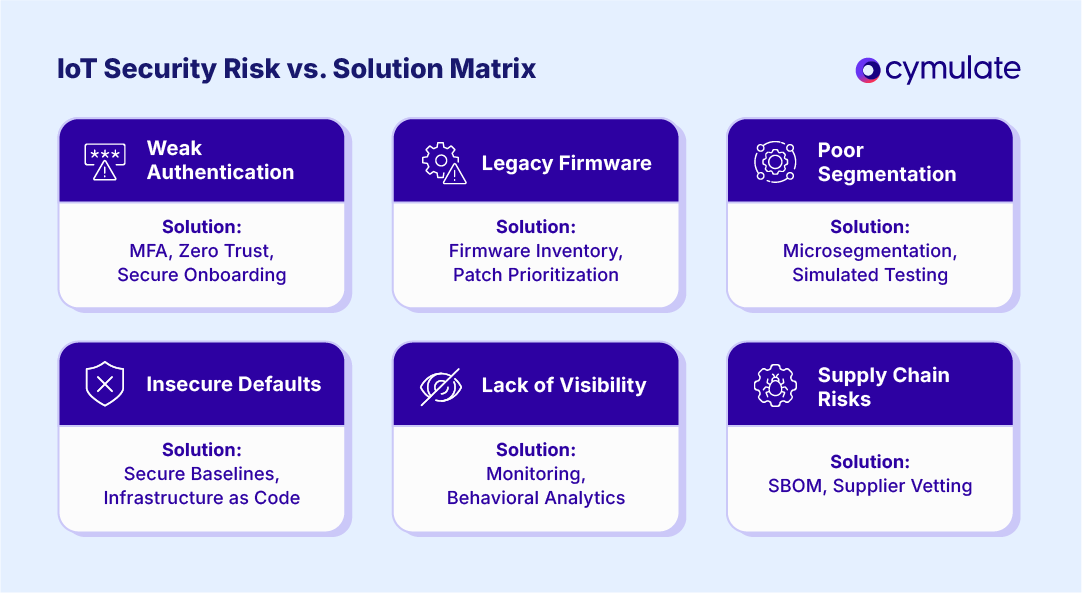
Weak Authentication and Authorization
Many IoT devices lack strong authentication mechanisms, relying on hardcoded credentials or limited role-based access. This makes them low-hanging fruit for attackers who can use default passwords or exploit exposed APIs.
Solutions:
- Enforce multi-factor authentication (MFA) where possible.
- Eliminate default credentials and mandate secure onboarding practices.
- Implement zero-trust architecture with identity-aware access controls.
Unpatched or Legacy Firmware
IoT devices often run on outdated firmware and may not receive regular security updates due to vendor limitations or operational constraints. These vulnerabilities become long-term liabilities.
Solutions:
- Maintain an up-to-date inventory of device firmware versions.
- Leverage vulnerability management tools that include firmware checks.
- Prioritize patching based on exploitability and asset criticality.
Poor Network Segmentation
Without proper segmentation, a compromised IoT device can become a gateway for lateral movement across the network, bridging IT and OT systems and enabling deeper infiltration.
Solutions:
- Segment IoT networks from corporate and OT systems using firewalls or VLANs.
- Implement microsegmentation and enforce east-west traffic controls.
- Use simulated attacks to test segmentation effectiveness.
Insecure Default Configurations
Many IoT devices ship with insecure defaults such as open ports, unnecessary services or permissive settings. These are rarely hardened before deployment.
Solutions:
- Conduct configuration audits against secure baselines.
- Disable unused services and lock down communication ports.
- Automate secure provisioning through infrastructure-as-code approaches.
Lack of Visibility and Monitoring
A fundamental challenge in IoT security is visibility. Without clear insight into connected devices and their behaviors, threat detection becomes reactive rather than proactive.
Solutions:
- Deploy network monitoring solutions with deep packet inspection for IoT protocols.
- Maintain a dynamic asset inventory across IT, OT and IoT environments.
- Use behavioral analytics to detect anomalies in device communication.
Supply Chain and Third-Party Risks
IoT devices often rely on third-party components or firmware, introducing opaque dependencies that attackers can exploit via the supply chain.
Solutions:
- Vet suppliers with security assessments and contract clauses.
- Monitor software bills of materials (SBOMs) for vulnerabilities.
- Use validation tools to test real-world exploit paths stemming from third-party devices.
Industry Use Cases: IoT Security in Practice
Healthcare
Hospitals rely on IoT for everything from patient monitoring to automated medication delivery. Yet many of these devices - such as infusion pumps or telemetry monitors - run legacy software, lack encryption, and are difficult to patch.
Risks:
- Patient data exposure.
- Disruption of life-critical services.
- HIPAA and HITECH compliance violations.
Finance
IoT-enabled systems in finance include smart ATMs, surveillance cameras, and branch-level IoT for environmental controls. If unsecured, these can offer entry points into sensitive financial networks.
Risks:
- Transaction fraud.
- Regulatory exposure under GLBA or PCI DSS.
- Use of IoT as a pivot into banking infrastructure.
Manufacturing
Industrial IoT (IIoT) devices, such as sensors and actuators, are integral to modern manufacturing but often operate with minimal security.
Risks:
- Bridging attacks from IT to OT.
- Tampering with operational processes.
- IP theft or operational disruption.
Retail
Retailers use IoT for inventory tracking, customer analytics and smart POS systems. These devices handle sensitive consumer data and financial transactions.
Risks:
- Exposure of payment data.
- Lateral movement from exposed IoT to corporate networks.
- Violation of consumer privacy laws like GDPR or CCPA.
Energy & Utilities
Smart meters, remote pressure sensors and grid automation systems are now common across the energy sector, introducing critical IoT exposure.
Risks:
- National infrastructure threats.
- Service disruption from targeted attacks.
- NERC CIP or other regulatory non-compliance.
Transportation & Logistics
Fleet management, cargo tracking, and vehicle telemetry systems are now largely IoT-driven. When compromised, attackers can disrupt supply chains or exfiltrate location-sensitive data.
Risks:
- Operational disruption.
- Physical safety threats.
- Exposure of sensitive routing or cargo data.
Building a Proactive Defense with Cymulate
Addressing IoT security concerns requires more than monitoring—it demands proactive validation of defenses across hybrid environments. Cymulate helps enterprises do just that by continuously simulating real-world attacks and validating the effectiveness of security controls in IT, OT and IoT infrastructures.
With the Cymulate Exposure Validation platform, organizations can:
- Validate Exposure Continuously: Run automated attack simulations to identify and close gaps in access controls, segmentation and detection.
- Test Device Access Controls: Ensure identity and access policies are enforced consistently across IoT endpoints.
- Measure Segmentation Effectiveness: Simulate east-west movement to test isolation between IoT and critical assets.
- Map Exploit Paths: Understand how attackers might pivot from an IoT foothold through IT or OT networks.
This approach aligns with modern exposure management strategies and supports cyber resilience goals by turning passive defenses into active safeguards. By incorporating Cymulate’s platform, security teams gain actionable insight into their true exposure—allowing for faster remediation and smarter investment in IoT security.
Explore Cymulate’s Threat Exposure Validation Report and Exposure Prioritization Brief for deeper insights into quantifying and reducing cyber risk.
Make Sense of IoT Security Risks with Cymulate
As IoT continues to reshape enterprise infrastructure, the complexity and stakes of securing connected environments will only grow. Weak authentication, legacy firmware, poor segmentation and limited visibility are no longer peripheral concerns. They are core vulnerabilities.
Cybersecurity leaders must adopt a proactive, validation-driven strategy that accounts for the realities of IT, OT and IoT convergence. By integrating platforms like Cymulate into their defense stack, organizations can stay ahead of IoT security issues and build essential resilience.


