Attack Surface Reduction
Minimize Attack Vectors, Strengthen Control Validation, and Quantify Cyber Risk Reduction
Attack Surface Reduction (ASR) is the practice of minimizing potential entry points that attackers could exploit in an organization’s IT environment. In simple terms, it means reducing the number of ways an attacker can break in by limiting common initial access points and removing unnecessary exposure.
Attack surface includes all possible points of attack such as hardware, software, cloud services and even human elements. By shrinking this footprint, ASR leaves attackers with fewer paths to exploit, which significantly lowers the risk of compromise.
ASR is not limited to securing endpoints or networks alone. It also includes protecting identities, applications, configurations, and cloud resources.
Attack Surface Management (ASM) focuses on discovering and monitoring assets and exposures to show what exists. ASR, in contrast, focuses on reducing and securing those exposures to prevent potential attacks. In other words, ASM helps you see what’s out there, while ASR helps you lock it down.
Vulnerability management aims to find and patch known flaws in systems. ASR, on the other hand, is more preventive in nature. It focuses on eliminating or restricting areas of exposure before attackers can reach those vulnerabilities.
Both approaches work together. You still need to patch critical issues, but reducing the attack surface limits the number of ways attackers can get to them.
The Different Types of Attack Surfaces
An organization's attack surface includes all the possible ways an attacker could gain access to its systems. To reduce it effectively, you must address three core areas: digital systems, human behavior and third-party connections.
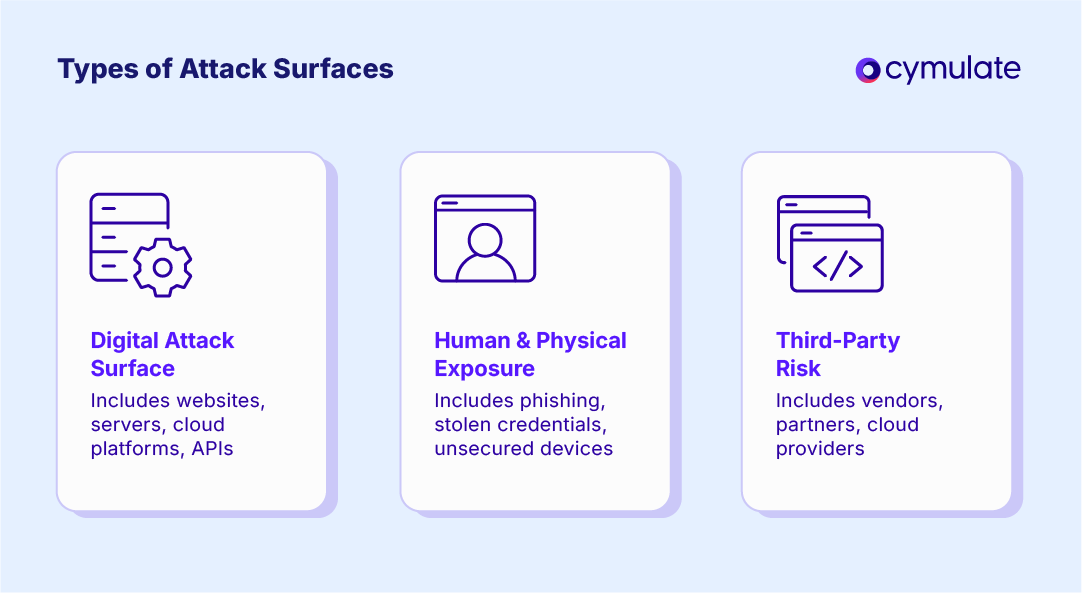
Digital Attack Surface
The digital attack surface includes all technology assets such as websites, servers, cloud platforms, databases and APIs. These systems are often vulnerable due to misconfigurations, unpatched software or open ports. An outdated server or exposed cloud storage can serve as an entry point.
To reduce this surface, organizations need to keep software updated, disable unused services and secure applications. Tools like web application firewalls (WAFs) and platforms such as Cymulate help test how well these systems can withstand real-world attacks.
Human and Physical Exposure
Humans are a frequent target in attacks. Risks here include stolen credentials, phishing, poor security habits and unsecured devices. An attacker who obtains valid login details can operate like an insider.
Organizations should use multi-factor authentication, educate users on threats like phishing and secure both digital and physical environments. Cymulate can help test the impact of compromised credentials and help identify where access controls need tightening.
Third-Party and Supply Chain Risk
Connections to vendors, partners and cloud providers also increase the attack surface. A third party with network access or excessive permissions could expose internal systems.
To reduce this risk, companies should perform regular security assessments, restrict third-party access and monitor their external ecosystem. Cymulate can help identify exposures from third-party platforms and acquisitions, allowing organizations to isolate or remediate those risks.
Complete Risk Reduction
Each layer of the attack surface presents unique challenges. Attackers often look for the easiest path in. A strong attack surface reduction strategy must address all components, technical systems, user behavior and third-party access.
Platforms like Cymulate help test defenses across these areas. By understanding and minimizing every exposure point, organizations can improve their security posture and reduce the likelihood of a successful attack.
How Attack Surface Reduction Works
Attack surface reduction combines technical controls with strategic policies to eliminate unnecessary exposures and strengthen what remains accessible. Security teams apply a variety of methods to reduce the attack surface.
Hardening Configurations and Systems
This involves securing operating systems, applications, cloud platforms and user devices by applying best practices and disabling unsafe defaults. Actions include turning off default passwords, enforcing encryption and removing risky features.
Patch management is also essential, since many breaches result from unpatched vulnerabilities. Hardening even applies to user settings, such as removing local administrator rights. A hardened system gives attackers fewer chances to gain access.
Eliminating Unnecessary Services, Ports and Assets
Unused or outdated systems often expand the attack surface. Every open port, exposed service or forgotten app is a potential risk. Security teams should audit and remove unnecessary elements.
For example, disabling Remote Desktop Protocol on servers that don’t need it can block a major attack route. Publicly exposed admin interfaces are also high-risk and should be removed or restricted. Reducing to only essential services and securing them limits easy entry points.
Implementing ASR Rules and Policies
Some platforms offer predefined ASR rules to block high-risk behaviors. For instance, Microsoft Defender’s ASR rules can prevent malicious scripts in Office apps or block unauthorized downloads.
These policies limit how software behaves, making it harder for threats to exploit vulnerabilities. Organizations can also create custom rules, like disabling macros or enabling allowlisting. While these need to be balanced with usability, they can prevent entire categories of attacks.
Reducing Privilege and Access
Too many high-privilege accounts increase risk. ASR means applying the principle of least privilege: users and systems should only have the access needed to perform their tasks.
Limiting admin rights, reviewing unused accounts, and enforcing multi-factor authentication helps reduce identity-related exposures. Just-in-time access and monitoring for unusual behavior further strengthen this layer.
Disabling Lateral Movement Paths
Flat networks make it easy for attackers to move between systems once inside. Network segmentation divides systems into isolated zones. This limits the spread of attacks by requiring extra steps for each move.
For example, sensitive databases might only be reachable from certain app servers. Firewalls, access controls and disabling legacy protocols like SMBv1 can all help stop lateral movement. A segmented network reduces the overall surface by creating contained zones of exposure.
Deprecating Legacy and High-Risk Systems
Old systems often lack support and remain unpatched, making them frequent targets. Organizations should identify outdated systems and either retire, upgrade, or isolate them. Legacy devices can be restricted to segmented zones with limited access.
When removal isn’t possible, use virtual patching, strict controls and continuous monitoring. Many attacks target known flaws in legacy systems, so minimizing their use is a key step in reducing risk.
Attack Surface Reduction vs. Vulnerability Management: A Functional Comparison
| Aspect | Attack Surface Reduction (ASR) | Vulnerability Management (VM) |
| Focus | Limiting what is exposed to attack | Finding and fixing known flaws |
| Approach | Preventive (remove attack paths) | Reactive (patch existing issues) |
| Mindset | Outside-in: reduce opportunities | Inside-out: fix internal weaknesses |
| Timing | Applied early (design, deployment) | Applied after deployment or flaw discovery |
| Techniques | Disable services, limit privileges, segment networks | Scan, patch, configure securely |
| Example Action | Removing unnecessary public-facing systems | Patching Apache vulnerability on all affected servers |
| Tool Support | Attack surface discovery, ASR policy validation | Vulnerability scanners, patch management tools |
| Strength | Reduces overall exposure and prevents many attack paths | Fixes specific known threats and improves resilience |
| Limitation | Cannot address flaws in critical, needed systems | Cannot reduce exposure of unnecessary or forgotten assets |
Attack Surface Reduction (ASR) and Vulnerability Management (VM) both reduce risk, but they take different approaches. While VM focuses on fixing known weaknesses, ASR aims to eliminate or minimize exposures before they can be exploited.
Vulnerability Management: The Reactive Layer
Vulnerability management is focused on identifying and fixing flaws in systems. These include software vulnerabilities, misconfigurations or outdated components. VM tools scan defined assets, flag known issues (such as CVEs) and guide remediation through patching or configuration changes.
This approach is reactive. It assumes systems are already live and accessible, then works to fix what can be exploited. For example, if a new flaw is discovered in Apache, the VM process identifies every instance running Apache and applies the patch.
VM is essential, but it deals with an inside-out view: what’s already present and how it can be secured.
Attack Surface Reduction: The Preventive Layer
ASR takes a broader, preventive approach. Instead of focusing on each vulnerability, it looks at how to reduce exposure altogether. This involves disabling unused services, limiting internet-facing systems, tightening user privileges, and reducing attack paths.
ASR operates with an outside-in mindset: assuming an attacker is looking for a way in, how can we make it harder for them by presenting fewer targets?
For instance, instead of only patching Apache, ASR would question whether that server needs to be public or whether unused Apache modules can be removed.
Working Together: A Dual Strategy
ASR and VM are complementary, not interchangeable. ASR reduces the number of systems and services exposed, while VM ensures that remaining assets are kept up-to-date and secure. When used together, they provide comprehensive coverage.
A helpful analogy: VM is patching holes in your roof, while ASR is reducing how much roof you have. The less roof, the fewer holes to patch.
Modern exposure management integrates both. It starts with discovering all assets (including shadow IT), then feeds this into vulnerability scanning and exposure reduction efforts.
Timing also differs: ASR is preventive and applied early during system design or deployment. VM is corrective, applied after a vulnerability is discovered. Both are vital. An unpatched flaw can lead to a breach even on a reduced surface, and a fully patched environment can still be exploited if it's overly exposed.
Platforms like Cymulate support both efforts. They simulate real-world attacks to validate whether vulnerabilities are exploitable (supporting VM) and assess open services or misconfigurations (supporting ASR). This provides full visibility and confidence in both reduction and remediation.
The Role of ASR in Exposure Management
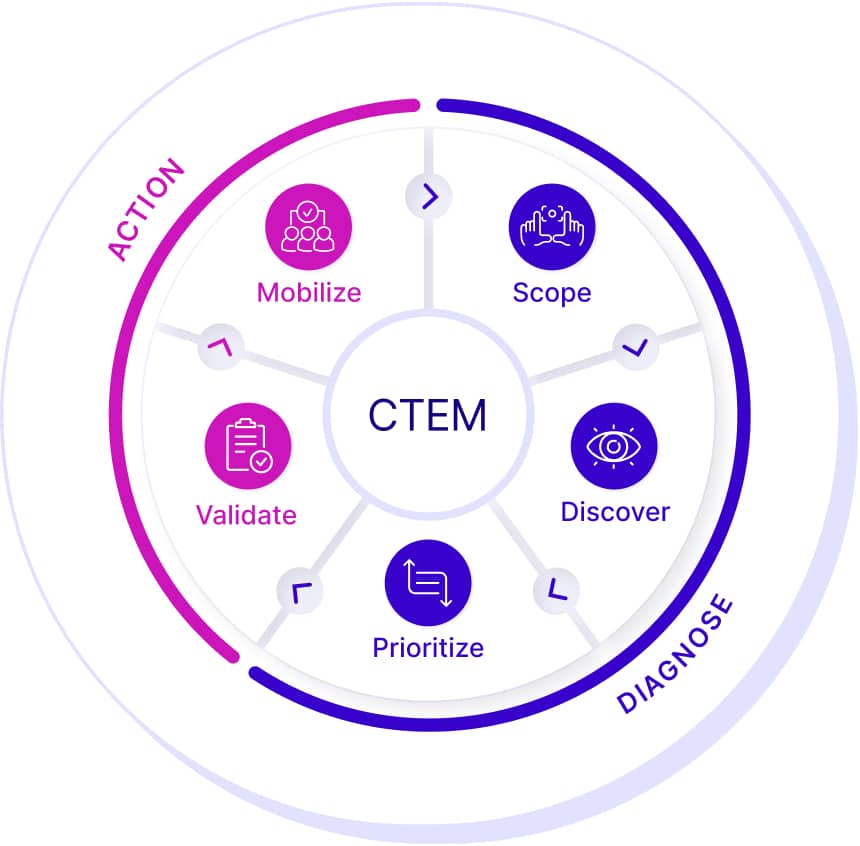
Attack Surface Reduction (ASR) is a critical element in modern exposure management strategies, particularly within frameworks like Continuous Threat Exposure Management (CTEM).
ASR serves as a foundational control that helps prevent, contain and measure cyber risk across the enterprise.
Fewer Exposures, Faster Detection
By reducing the number of exposed assets, services, and privileged accounts, ASR lowers the volume of alerts and anomalies. This helps security teams detect and respond to threats more quickly. Fewer exposed pathways mean less noise and a smaller "haystack" to monitor. ASR not only blocks some attacks entirely but also makes it easier to identify and contain those that occur.
Shortening Dwell Time and Reducing Spread
A smaller attack surface limits how far an attacker can move after initial compromise. For example, if a compromised device cannot reach sensitive systems due to segmentation, the attacker is blocked.
Techniques like least privilege, device isolation and network segmentation reduce lateral movement. Security exercises consistently show that with proper segmentation, simulated ransomware spreads to far fewer systems. By reducing exposure, organizations limit the blast radius of attacks.
Alignment with CTEM Practices
ASR supports key CTEM stages such as Discovery, Prioritization and Mitigation. It translates exposure findings into action. Without ASR, CTEM becomes incomplete, as exposures may be identified but not addressed.
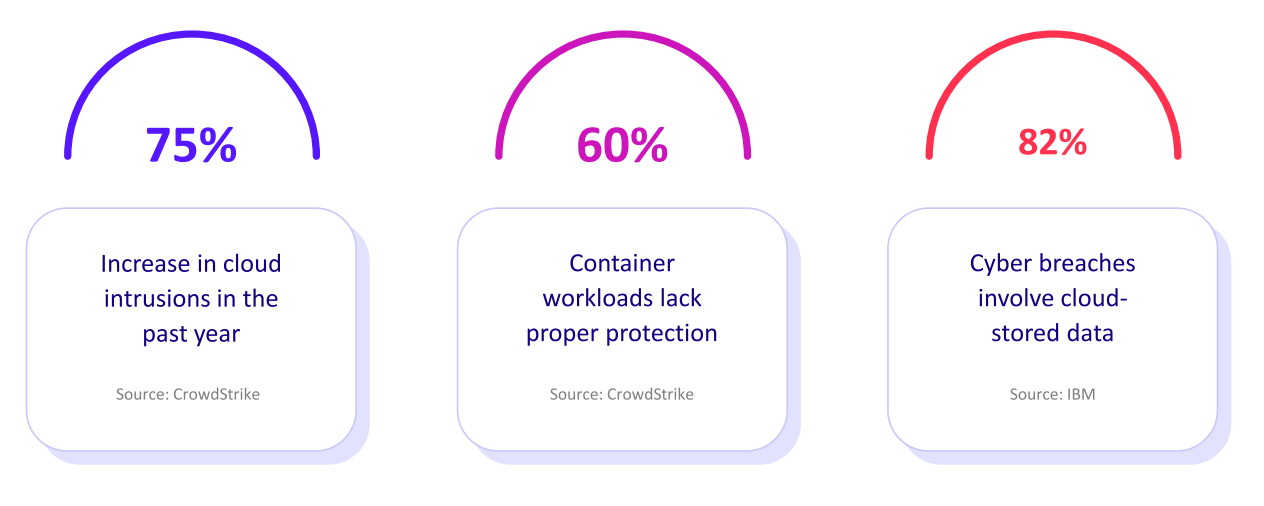
Organizations that run exposure validation efforts at least once per month report 20% fewer breaches on average. This supports the shift toward continuous, not periodic, security practices. In fact, 71% of security leaders believe that continuous exposure validation, including ASR, is essential in the current threat landscape.
Strengthening Control Validation
ASR works hand in hand with security control validation. When you reduce complexity by shrinking your attack surface, controls like firewalls and intrusion prevention become more effective. Breach simulations may reveal attack paths that should be closed entirely, not just patched.
For example, a misconfigured server that enables an attacker could be removed from public access, not just secured.
ASR also addresses risks that vulnerability scans may miss, such as exposed RDP ports or default credentials. This feedback loop between control validation and attack surface reduction helps continuously strengthen the security posture.
Enabling Risk Quantification
ASR provides tangible metrics that help communicate risk reduction to executives. Leaders want to know how much risk has been reduced, not just how many patches were applied.
With ASR, security teams can track metrics such as the number of exposed assets, percentage of internet-facing systems, or count of high-risk open ports. Many platforms generate exposure scores that reflect progress.
This allows security leaders to show that proactive efforts are reducing the organization’s overall risk footprint, a message that resonates in dashboards and board reports.
Cloud Attack Surface Reduction Strategies
As organizations increasingly shift to cloud infrastructure, the cloud attack surface expands. These environments are dynamic, decentralized and often internet-facing by default.
Reducing exposure in the cloud requires disciplined identity and configuration management, along with continuous oversight.
Identity and Access Management (IAM)
Overly permissive identities are a major cloud risk. To reduce exposure, enforce least privilege access across all cloud accounts, roles and API tokens. Remove unused credentials, enable multi-factor authentication, and monitor for abnormal activity.
Cloud-native tools like AWS IAM Access Analyzer or GCP IAM Recommender help detect excessive permissions. Remember, identity is the new perimeter in cloud environments. Protect it by limiting the number and power of privileged accounts.
Secure Configurations with CSPM
Misconfigured cloud services are one of the top causes of breaches. Common examples include open S3 buckets, exposed storage accounts, or overly broad security groups.
Use Cloud Security Posture Management (CSPM) tools to continuously scan your environment for unsafe settings. Adopt secure defaults when deploying new resources. Only allow public access when truly required and place development systems on private subnets.
Configuration drift happens quickly in cloud environments. Treat cloud hardening as a routine task, just like patching.
Reducing Common Cloud Attack Vectors
Cloud environments introduce new entry points, including management consoles, APIs, and orchestration layers.
Limit who can access cloud management interfaces. Protect consoles with MFA and restrict access by IP or device. Secure public-facing applications with WAFs or API gateways, and test them regularly.
If using containers or serverless platforms, apply best practices like image scanning, using approved base images and restricting function permissions. Periodic exposure scans often reveal forgotten systems that increase risk and cost.
Managing Third-Party Cloud Risk
Cloud environments often connect with third-party apps, APIs or external identities. Each connection adds potential exposure.
Keep an up-to-date inventory of third-party integrations. Apply least privilege scopes, monitor third-party activity and revoke access when it's no longer needed. For external consultants or vendors, isolate access using separate roles or cloud projects.
As supply chain attacks increase, require vendors to follow your security policies and limit their reach within your cloud.
Automation and Continuous Monitoring
The pace of cloud change demands automation. Use Infrastructure as Code (IaC) and policy-as-code to enforce secure deployments. Tools like Terraform, AWS Control Tower or Azure Policies can block insecure configurations from being launched.
Enable continuous monitoring with tools like Amazon GuardDuty, Azure Defender or GCP Security Command Center. Automate responses where possible, such as auto-closing an open port or alerting the team if risky behavior is detected.
Simulations using platforms like Cymulate can validate the effectiveness of your cloud defenses. These assessments test real scenarios like privilege escalation or data exfiltration to ensure your controls are working as intended.
How Cymulate Supports Attack Surface Reduction
Cymulate enables organizations to reduce their attack surface through visibility, testing and continuous validation. It shows security teams what attackers can see, simulates real-world threats, and helps prioritize efforts based on actual risk.
Visualizing and Prioritizing the Attack Surface
Cymulate provides real-time visibility into exposed assets across on-prem, cloud, and endpoint environments. Its Exposure Validation and external discovery tools identify high-risk systems, such as publicly accessible servers or misconfigured cloud resources.
These exposures are ranked based on exploitability, asset criticality, and missing controls. This helps security teams know exactly which parts of the attack surface to reduce first.
In addition to visibility, Cymulate continuously tests the effectiveness of ASR measures. If you’ve restricted lateral movement through network segmentation, Cymulate can simulate movement between segments to validate whether the barrier holds.
It also tests what would happen if an attacker obtained user credentials, highlighting whether multi-factor authentication and access controls are effective.
Simulating Real Attack Paths and Driving Improvement
Cymulate performs multi-stage attack path simulations that mimic how a real attacker might progress through your environment.
These simulations reveal weak points in defenses, such as insufficient segmentation, overly permissive cloud settings, or reachable data stores. This insight guides further ASR actions, such as isolating systems or adjusting IAM policies.
The platform also tracks ASR progress using risk scores and before-and-after comparisons. Teams can demonstrate that exposure has decreased over time, turning abstract security improvements into measurable results.
Cymulate uses remediation suggestions and integration with ticketing or automation tools to help operationalize these findings, making attack surface reduction part of ongoing IT workflows.
A Continuous Cycle of Validation
By combining visibility, simulation and feedback, Cymulate supports a continuous ASR process. It allows organizations to implement changes, validate them through real-world testing, and adjust based on results.
This approach is especially valuable in hybrid and cloud environments, where the attack surface shifts quickly.
ASR as a Continuous Practice
Organizations must treat ASR as an ongoing cycle of assessment, action and validation. As one industry analogy puts it, managing your attack surface is like trimming a garden: if you don’t regularly prune it, it will grow wild and expose weaknesses.
Regular scans, audits, and attack simulations should be scheduled to catch any new exposures, and there should be processes to address them promptly, keeping the environment as tidy as possible.
Crucially, attack surface reduction is a mindset that should influence decision-making at multiple levels. When designing new systems or rolling out changes, teams should be asking: “Can we achieve this with fewer exposed services? Is there a way to architect this solution more securely by default?” It’s easier to build something with a minimal attack surface from the start than to bolt on fixes afterward.
Principles like Zero Trust (never trust, always verify) and secure-by-design inherently lead to smaller attack surfaces for example, Zero Trust networking assumes every connection is hostile until proven otherwise, which naturally restricts open access.
With these principles, companies ensure that each new project doesn’t inadvertently undo the progress made in reducing risk. It helps to make ASR a key metric or objective for security and IT teams, for instance, including goals like “reduce the number of externally exposed critical assets by X% this year” or “eliminate all default credentials and open ports in our cloud by next quarter.” Clear goals reinforce that continuous reduction is expected.