CISO Roadmap 2025: A Practical Guide to Building a Resilient, Validated Security Strategy

Key Insights
- The CISO Role Has Evolved – In 2025, CISOs are business-aligned executives, not just technical defenders, responsible for building resilient, validated security strategies that enable organizational agility.
- Resilience Requires Validation – Continuous control validation is essential to prove defenses work against real-world threats, moving beyond traditional vulnerability management.
- First 90 Days Are Critical – Early priorities should include breach and attack simulation (BAS), exposure management and rapid control validation to establish a measurable baseline.
- Metrics Matter – Board-ready KPIs such as mean time-to-detection (MTTD), attack path reduction and validation coverage tie security performance directly to business outcomes.
- Automation is Essential – Automated mitigation and Continuous Automated Red Teaming (CART) reduce mean time to containment and proactively close exploitable gaps.
- The Cymulate Advantage – The Cymulate Exposure Management Platform empowers CISOs to operationalize resilience with continuous validation, prioritized remediation and integrated automation across environments.
In 2025, cybersecurity leadership demands more than just technical acumen. Today’s CISOs must be strategic architects of resilience, integrating proactive defenses, validated controls and real-time insights into a cohesive, business-aligned security program.
The role has evolved from technical gatekeeper to operational executive, a responsibility that steers both security posture and organizational agility.
With increasing regulatory scrutiny, growing attack surfaces and threats augmented by AI, the expectations for CISOs are higher than ever. The CISO Roadmap 2025 delivers a practical, solution-driven framework to help security leaders build and maintain a validated, measurable and adaptive defense strategy.
Along the way, this guide has been informed by Cymulate's platform capabilities, industry best practices and real-world CISO insights.
Establishing a CISO Vision for 2025
A clear, forward-looking vision that fits your organization’s goals is the cornerstone of effective security leadership. For 2025, that vision must focus on:
- Cyber resilience: The ability to absorb, recover from and adapt to evolving cyber threats.
- Continuous visibility: Real-time awareness of assets, vulnerabilities and security control efficacy.
- Validated assurance: Ongoing evidence that security controls are effective under real-world conditions.
Resilience today is not a destination. It’s a required state, where readiness is the expected standard. To achieve this, CISOs must align their security strategies with business priorities, risk appetite and compliance mandates.
The Cymulate Exposure Management platform empowers CISOs to operationalize this vision. By continuously assessing risk across cloud, on-prem or hybrid environments and validating the performance of existing controls, security leaders can shift from reactive firefighting and constantly chasing alerts to strategic enablement.
Metrics generated from validation tests help set mission-aligned KPIs, tying security outcomes to organizational goals.
First 90 Days: From Assessment to Action
The early days of a CISO’s leadership often dictate the success of long-term strategy. Whether you're new to the role or recalibrating your program, the first phase should center on comprehensive visibility and prioritized action.
Baseline with Breach and Attack Simulation
Using Breach and Attack Simulation (BAS) capabilities from Cymulate, CISOs can run controlled, automated assessments against real-world attack techniques. These simulations test the actual performance of endpoint protections, firewalls, email gateways, DLP systems, and more. Unlike traditional assessments, BAS provides near-instant feedback and actionable findings.
Prioritize with Exposure Management
A complete inventory of digital assets, including shadow IT and cloud services, is critical for informed decision-making. Exposure Management from Cymulate provides attack surface visibility, contextualized risk scoring and asset prioritization. This allows security teams to identify which exposures pose the greatest threat and which controls need immediate attention.
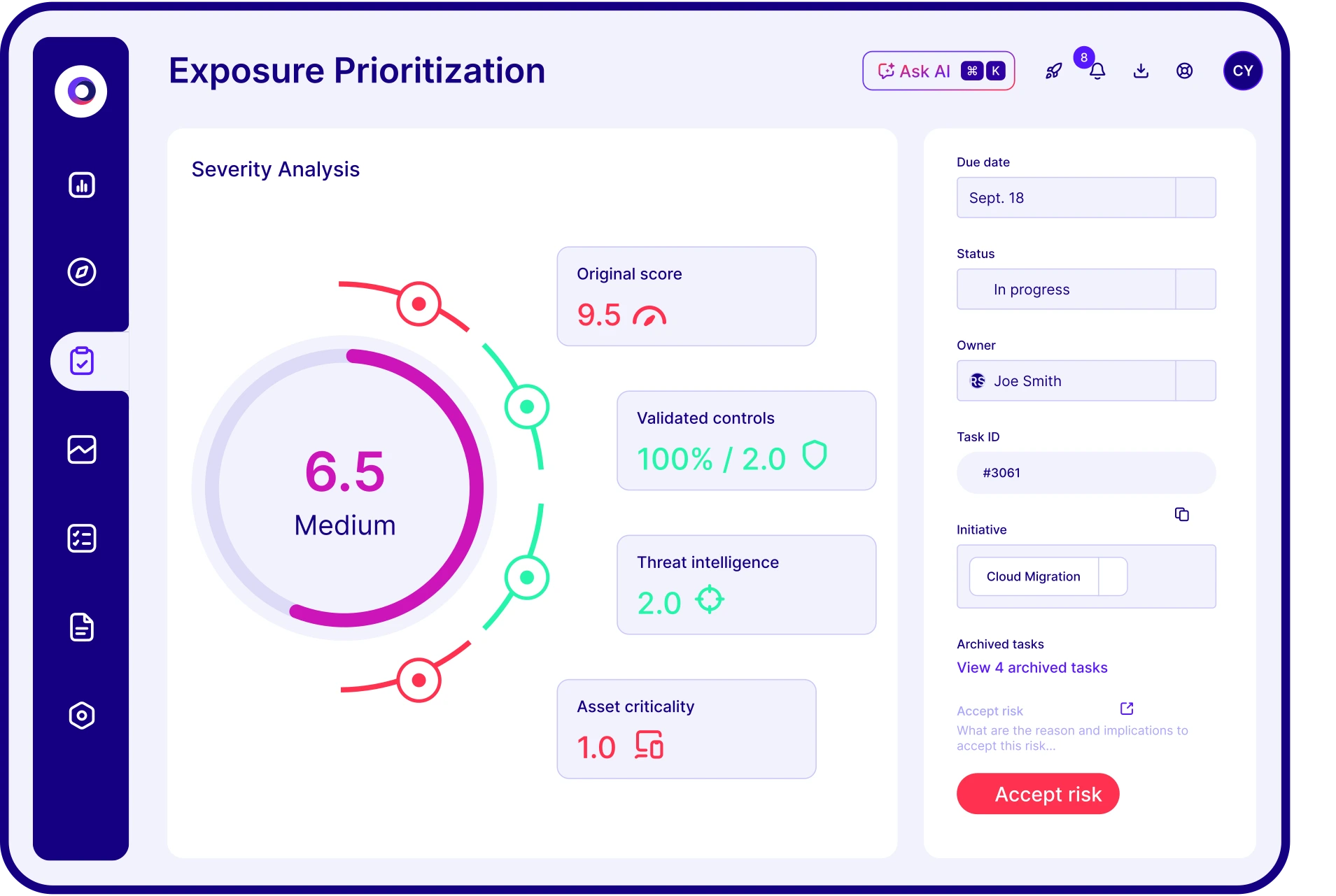
Act with Ready-to-Use Templates
Out-of-the-box validation templates can accelerate implementation. These Cymulate templates include test cases for ransomware, data exfiltration, privilege escalation and more. The ability to validate controls without needing custom scripts or consultants enables rapid time to value.
Together, these tools offer an agile, data-driven way to assess and fortify security posture during a critical transition period.
Building a Validated Security Posture
Modern adversaries move quickly. To keep up, security programs must adopt a continuous validation approach that goes beyond periodic audits.
Implement Continuous Control Validation
Cymulate enables persistent testing of security controls against a library of evolving threat scenarios. Instead of relying on assumptions or vendor promises, security leaders get real evidence about what works, what doesn’t and how well controls perform under attack.
Validation is no longer a "nice to have." Without true validation, your efforts around exposure management are probably just vulnerability management. That’s not good enough in 2025. Validation is a necessity for:
- Ensuring controls are deployed correctly and functioning as intended
- Identifying blind spots in detection and response workflows
- Reducing false sense of security and compliance-driven complacency
Enhance Visibility with CART
Cymulate offers Continuous Automated Red Teaming (CART), bringing attacker emulation into daily operations. CART leverages automation to simulate multi-stage attack paths and lateral movement without causing disruption. These simulations help security teams understand how threats propagate across infrastructure, offering insight into dwell time, privilege abuse and data access risks.
In the Threat Exposure Management Impact Report 2025, 67% of organizations surveyed said that infrequent testing (e.g. not automated or continuous) leaving gaps in assessment is an issue for their organization. Organizations that run exposure validation testing at least once a month reported a 20% reduction in breaches.
A strong strategy around CART leads to measurable improvements in risk reduction and operational efficiency.
Create an internal security awareness campaign to measure employee resilience against phishing attacks with Continuous Automated Red Teaming (CART)
Metrics-Driven Leadership
The boardroom demands clarity. CISOs must translate technical data into strategic insight, presenting metrics that demonstrate control effectiveness, resilience and business impact.
Establish Board-Ready Metrics
Dashboards and reporting tools from Cymulate provide a unified view of exposure trends, security posture evolution, and remediation progress. Metrics like mean time-to-detection (MTTD), attack path reduction and validation coverage map directly to board concerns about risk exposure and compliance.
Tell a Story with Validation Data
During the CISO Roundtable Webinar on Security Metrics, CISOs discussed how security and exposure validation provides the proof and evidence to measure and baseline cyber resilience.
CISOs can report on their company’s cyber risk in quantifiable terms and confidently advocate for continued investments and improvements.
Effective CISOs don’t just show performance; they prove impact. To do so you need the data to back up your analysis.
Automated Mitigation and Proactive Defense
Speed matters in cybersecurity. The faster a threat can be contained, the lower the damage. A great enabler of speed is automation. We’re not talking about the kind that eliminates headcount on your teams, it’s the kind that makes your systems work faster and cut off problems that could take down your business continuity and impact your bottom line.
That’s why automation is no longer optional. It’s essential.
Accelerate Response with Automated Mitigation
Cymulate offers Automated Mitigation features empowering security teams to translate validation results into direct action. By integrating with security orchestration, EDR and configuration management tools, Cymulate helps close the loop between detection and remediation.
For example, if BAS testing reveals an endpoint bypass, the platform can push configuration changes to resolve the issue automatically. This reduces mean time to containment and limits adversarial movement.
Combat Identity-Based Threats
Identity is the new perimeter, and it’s under constant attack. Cymulate has conducted research on unauthorized access, highlighting how often identity-based controls are misconfigured or over-trusted. Automated testing of MFA, session policies and privilege escalation controls ensures gaps are closed before attackers can exploit them.
Proactive defense requires acting before incidents escalate. Cymulate makes that possible with automation that reduces human bottlenecks and increases resilience.
Evolving with the Threat Landscape
In cybersecurity, standing still is falling behind. Threat actors continuously adapt by leveraging AI, supply chain vulnerabilities and new exploit techniques. CISOs must lead programs that evolve just as quickly.
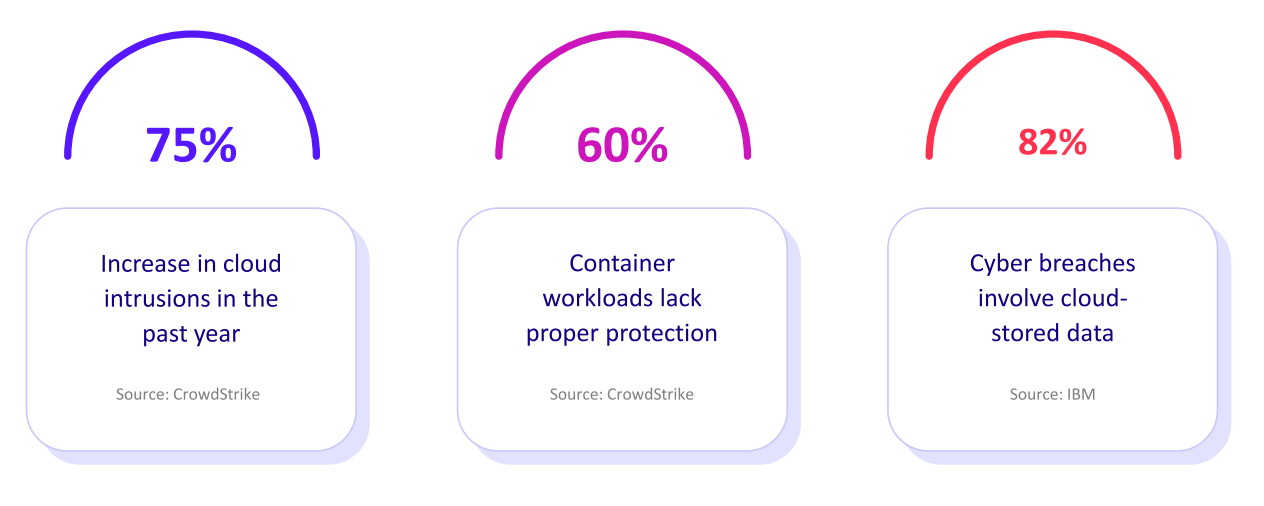
Operationalize Threat Intelligence
Threat intelligence has limited value unless it’s actionable. Cymulate turns intelligence into action by allowing teams to test their environments against current threats. When a new CVE or ransomware strain emerges, Cymulate can emulate it safely within hours, helping security teams validate their preparedness.
Maintain Security Agility
Things change quickly in the business world. CISOs must build agility into their programs, enabling swift adaptation to:
- Business expansion (e.g., M&A, cloud migrations)
- New regulations (e.g., DORA, SEC disclosures)
- Vendor and supply chain risks
Using the scalable platform from Cymulate ensures security remains effective even as complexity grows. By integrating with existing SIEM, SOAR, EDR and cloud platforms, Cymulate enhances, rather than replaces, your current tech stack.
Roadmap Framework for CISO Success
An effective security strategy requires a structured yet adaptable roadmap. Rather than relying on fixed day-based timelines, consider a layered model that guides both short-term execution and long-term evolution.
Foundation: Assessment and Visibility
- Baseline current security posture with breach and attack simulation
- Discover and prioritize exposures across on-prem, cloud, and SaaS environments
- Establish validation KPIs tied to risk and business impact
Maturity: Validation and Automation
- Implement continuous control validation for key attack surfaces
- Emulate attacker behavior with CART to assess lateral movement and defense depth
- Deploy automated mitigation workflows to reduce MTTR
Optimization: Metrics and Communication
- Align reporting with executive expectations and compliance obligations
- Use validation metrics to prioritize budget, training, and technology investments
- Foster cross-functional collaboration with IT, risk, and legal teams
Agility: Threat-Informed Adaptation
- Regularly update validation scenarios based on threat intelligence
- Adjust exposure priorities as business operations evolve
- Test security changes before deploying to production
This iterative model ensures that security is not only robust, but also responsive to change.
How Cymulate Exposure Management Helps CISOs and Their Teams
The best security professionals understand that the paradigm has shifted. The game is no longer about reacting to threats; it's about building and proving resilience proactively. Cymulate's Exposure Management platform is designed precisely for this mission.
As a CISO, Cymulate helps your teams validate threats, prioritize exploitable exposures and continuously optimize their security posture. With an emphasis on validated threat exposure rather than theoretical risk, the platform enables CISOs to implement a practical and scalable strategy for resilience.
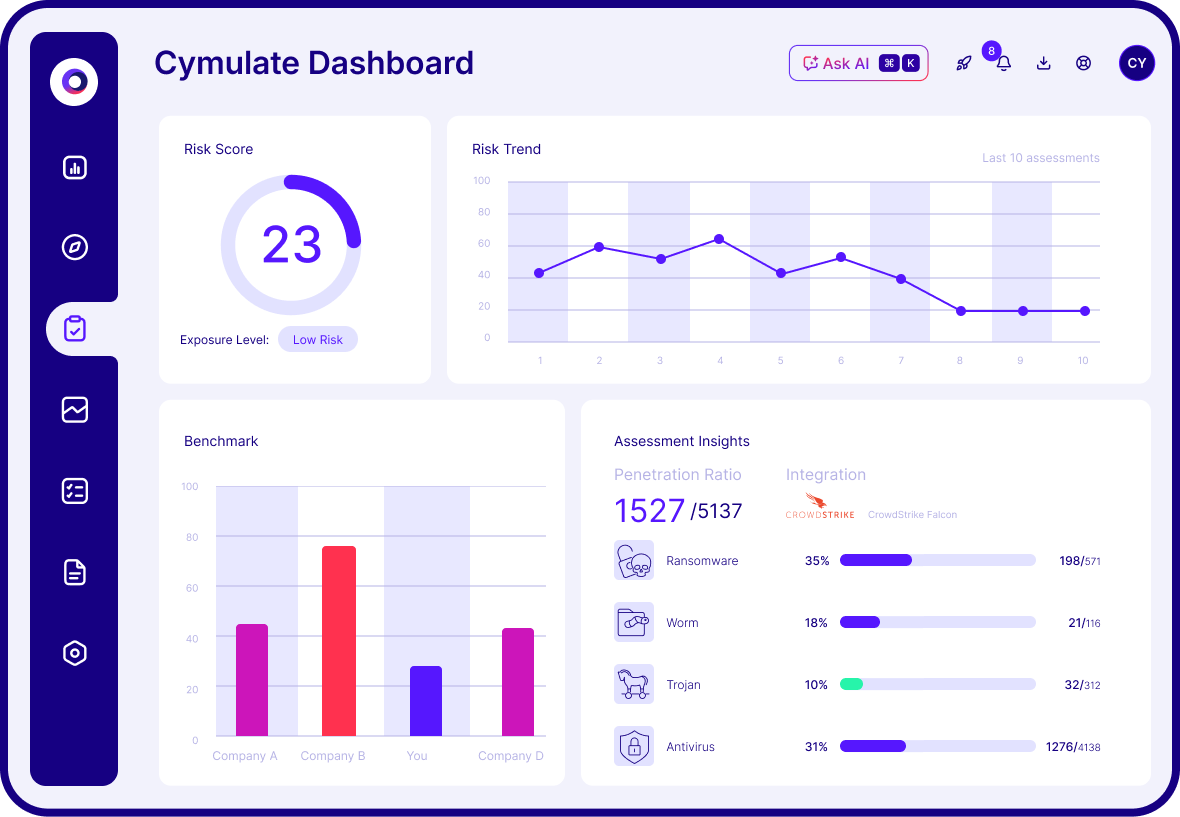
Cymulate dashboard showing real-time exposure validation results and prioritized remediation insights
Blue teams use Cymulate to validate defenses and optimize security controls. On average, Cymulate customers improve their threat prevention rates by 20 points—from 70% to over 90%, with some achieving 98% validated threat prevention. This shift from reactive response to preemptive validation transforms security from a cost center into a business enabler.
Red teams benefit from Cymulate’s AI-powered attack builder, which creates sophisticated attack chains in minutes, a process that could take hours using traditional open-source tools. This enhances offensive testing capabilities while scaling red team efforts efficiently.
Vulnerability management teams use Cymulate to identify exposures that are not just present but exploitable within their specific environments. The result? Over a 50% reduction in critical and high vulnerabilities, allowing teams to focus where it matters most.
For organizations running CTEM (Continuous Threat Exposure Management) programs, Cymulate drives collaboration and clarity across teams. Security operations, threat intelligence and IT remediation groups all benefit from a shared, validated view of risk. On average our customers show a 60% increase in efficiency prioritizing and mobilizing remediation using our platform.
Cymulate works with any security team that’s focused on proactive security, from Fortune 100 corporations to mid-sized organizations that have a dedicated security team.
Your Road to CISO Success
The 2025 CISO is more than a defender. They are a strategist, communicator, and innovator tasked with reducing cyber exposure while enabling business outcomes. A validated, resilient security program is within reach—but only if it’s built on automation, visibility, and continuous testing.
Cymulate offers the tools and insights CISOs need to operationalize resilience. From breach simulation to automated mitigation and real-time metrics and analytics, Cymulate can help you get on the road to success for you and your organization in 2025.


