AI and ML for SIEM: The New Standard in SOC Defense
Traditional SIEM systems, while foundational to enterprise security operations, can reach a limit in increasingly-complex environments. As organizations face more sophisticated threats and exponentially growing data volumes, legacy SIEMs struggle to scale.
These SIEMs generate excessive noise, produce high false positive rates and place unsustainable burdens on teams.
Artificial intelligence (AI) and machine learning (ML) are transforming this paradigm. AI-powered SIEM solutions enable security operations centers (SOCs) to shift from reactive to proactive defense using real-time analysis, adaptive threat detection and automation to manage complexity, reduce manual overhead and accelerate incident response.
What Is AI-Powered SIEM?
AI-powered SIEM integrates artificial intelligence and machine learning into traditional SIEM architectures to enhance detection capabilities, reduce alert fatigue and optimize analyst workflows. These systems leverage algorithms trained on historical and real-time data to detect patterns, identify anomalies and prioritize alerts based on risk.
Core AI/ML capabilities within modern SIEMs include:
- Anomaly detection: Identifying behavior outside established baselines using unsupervised learning.
- Automated correlation: Linking related security events across disparate systems without predefined rules.
- Adaptive learning: Continuously improving detection models based on new data inputs.
- Natural language processing (NLP): Extracting relevant context from unstructured data like logs, tickets, and emails.
- Automated triage and enrichment: Reducing time-to-detection by correlating events and supplementing alerts with threat intelligence.
The result is a more intelligent, efficient, and scalable security architecture that supports both detection and response.
Key Benefits of AI/ML in the SOC
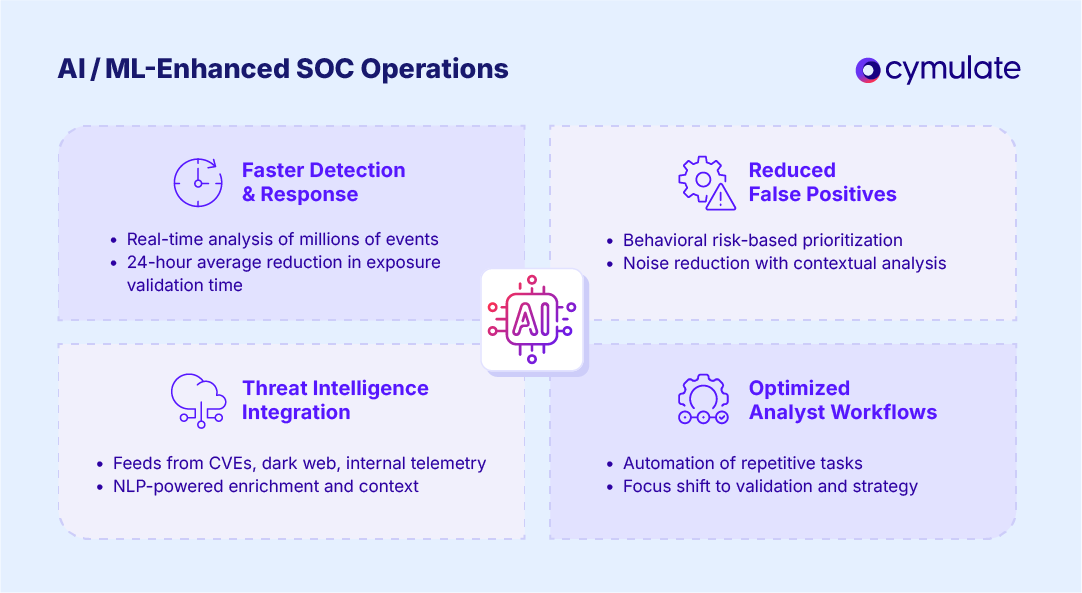
Faster Incident Detection and Response
AI SIEM tools can analyze millions of events in real time, flagging threats within seconds. Machine learning models trained on historical data can recognize subtle indicators of compromise (IoCs) that static rule-based systems miss.
In general, the introduction of AI into exposure validation processes has garnered positive results for organizations. According to the Threat Exposure Validation Impact Report 2025, it takes organizations who have implemented AI into their exposure validation process 24 fewer hours on average to test their defenses against newly identified cyber threats.
For SIEM, applying AI-driven rule validation and optimization can allow organizations to detect threats faster than those relying solely on manual correlation and static rules.
Reduced False Positives
Traditional SIEMs often overwhelm SOC analysts with redundant or irrelevant alerts. AI-based SIEM solutions apply contextual analysis to suppress benign events, prioritizing alerts based on behavioral risk, impact potential and threat intelligence feeds. This can reduce false positives, freeing analysts to focus on true threats.
Enhanced Threat Intelligence Integration
AI SIEMs ingest data from threat feeds, CVE databases, dark web monitoring and internal telemetry to enrich alerts with actionable intelligence. NLP and deep learning models can parse this data, assess relevance, and support predictive detection.
Optimized Analyst Workflows
AI can automate repetitive tasks such as log parsing, event triage, IOC correlation, and incident reporting. SOC teams can interpret findings and validate detection logic, drastically improving operational efficiency.
Use Cases of AI and ML in SIEM
Behavioral Analytics for Insider Threat Detection
By building behavioral baselines across users, devices, and networks, AI-powered SIEMs can detect deviations that may indicate insider threats, lateral movement or compromised accounts. Behavioral analytics SIEM models operate continuously and adapt to new behavioral patterns without manual input.
Automated Playbooks for Incident Response
Integrated AI enables dynamic, conditional workflows that can automatically trigger containment actions, ticketing or forensic investigations based on event severity. This level of orchestration reduces mean time to remediate (MTTR) and supports scalable security operations.
ML-Powered Anomaly Detection and Prioritization
AI SIEM tools use clustering and classification algorithms to detect anomalous patterns such as unusual login behaviors, privilege escalations, or uncommon data exfiltration attempts.
These are then scored and prioritized using ML-based risk models, ensuring high-fidelity alerting.
How AI Is Changing the Role of SOC Analysts
AI and ML are not replacing analysts—they’re augmenting them. With intelligent automation handling alert triage and enrichment, analysts can shift focus from low-level event management to strategic threat hunting and response planning.
This shift enables:
- Faster threat validation
- Higher-quality investigations
- Proactive security posture management
- More time for tuning detection logic and controls
SOC analysts become orchestrators of AI-driven defense rather than passive responders to alert fatigue.
Real-World Example: AI-Driven Exposure Validation
AI’s role in SIEM is amplified when paired with continuous exposure management and validation. Cymulate helps SOC teams validate detection efficacy by simulating attack paths and evaluating how well existing SIEM rules and detection logic respond.
For example, Raiffeisen Bank International (RBI) used Cymulate to validate and fine-tune their SIEM rules. They achieved improved detection rates and significantly reduced false positives.
When they create a new detection rule in their SIEM they can’t validate with historical logs, RBI uses Cymulate assessments to generate the appropriate events and see if the rule was successful in its detection. That immediate feedback is useful when fine-tuning the SIEM and practicing detection engineering.
This approach ensures that SIEM systems aren’t just ingesting data—they’re responding accurately to verified threats.
Challenges and Considerations
While the benefits of AI and ML in SIEM are substantial, implementation comes with challenges:
Data Quality and Normalization: AI models are only as good as the data they’re trained on. Poorly normalized, incomplete, or noisy logs can lead to inaccurate detections or model drift.
Model Bias and Drift: ML models can develop bias if trained on unrepresentative data. Continuous monitoring and retraining are essential to maintain detection quality.
Integration Complexity: AI SIEM tools must integrate with diverse data sources, security controls, and response platforms. Organizations need a robust architecture and skilled teams to operationalize these capabilities effectively.
The Future of AI in the SOC
The future of AI SOC operations is trending toward:
- Generative AI for Alert Summarization: Providing high-level context, summaries, and recommendations in human-readable form.
- Predictive Threat Modeling: Using historical and environmental data to predict where attacks are likely to occur.
- Decision Support Systems: Recommending the most effective containment or mitigation steps based on real-time threat intelligence.
As generative AI models improve, they will support SOC analysts not just in detection but in communicating risk to stakeholders and automating decision-making at scale.
AI and ML are no longer experimental technologies in cybersecurity—they’re foundational to modern SIEM architectures. AI SIEM solutions deliver scalable, intelligent threat detection, enabling SOCs to operate efficiently in high-volume, high-stakes environments.
AI-Powered SIEM Rule Validation and Detection Engineering from Cymulate
Detection alone isn't enough. Continuous validation is critical to ensure your AI-powered SIEM detects what’s important. Detection engineering capabilities should automate the most critical and resource-intensive tasks. Using AI-powered analysis and a massive library of real-world attack simulations, teams can continuously build, test and fine-tune threat detection — so organizations can see what works, fix what doesn’t and continuously optimize detections.
That’s where Cymulate stands out—by helping organizations operationalize AI for threat exposure validation, rule optimization and actionable insights.
Cymulate offers an AI-powered detection engineering assistant for SIEM rule threat coverage validation. Cymulate automates and streamlines the detection engineering process for blue teams and SecOps, allowing for building, testing and optimizing threat detection with AI-assisted live-data attack simulations and personalized threat detection.

This approach eliminates the friction of manual detection validation by automating the correlation and testing process. Teams will know if their rules work and what threats are covered by the rules.
It will only take minutes for teams to identify coverage gaps and tune rules. Without AI, mapping detection rules to relevant threats was an hours-long, tedious and manual process of reviewing rule logic, identifying threat coverage and testing scenarios one by one.
Security teams looking to evolve from reactive alerting to proactive defense should evaluate AI-driven SIEM capabilities—supported by continuous validation—to build a resilient, adaptive and intelligent SOC.