Cloud Security Automation: Key Practices for Success
In 2025, global spending on cloud services is projected to increase by 21.5% compared to 2024, reaching an estimated $723.4 billion. Growth like this clearly highlights how cloud services are reshaping organizations of all sizes and industries. In the modern business world, cloud security is no longer a luxury – it's a necessity. However, this growing reliance on cloud infrastructure introduces a complex set of security challenges that require constant vigilance. Cloud security automation helps eliminate repetitive security tasks while providing businesses with an edge in defending against increasingly sophisticated cyber threats.
Misconfigurations, identity-based attacks, and evolving malware can expose critical assets within minutes, outpacing manual security defenses. Automated cloud security tools enable businesses to quickly adapt to new threats and vulnerabilities, while maintaining a strong defense in dynamic environments. With the goal of reducing manual intervention, increasing efficiency and strengthening security posture within cloud environments, it’s easy to see why businesses have turned to cloud security automation.
What is Cloud Security Automation?
With approximately 60% of corporate data is now stored in the cloud, security teams face increased challenges in protecting assets across dynamic, distributed environments. Traditional, manual security measures are too slow and error-prone to keep up with modern cyber threats. Through the use of AI-driven tools, scripts and workflows to automatically detect, prevent and respond to security threats in cloud environments, cloud security automation is a total powerhouse. By integrating automation into security workflows, organizations can:
- Identify vulnerabilities in the cloud environment before attackers exploit them.
- Detect and mitigate cloud anomalies using machine learning and behavioral analytics.
- Enforce security controls consistently across multi-cloud and hybrid environments.
- Accelerate incident response through automated remediation workflows.
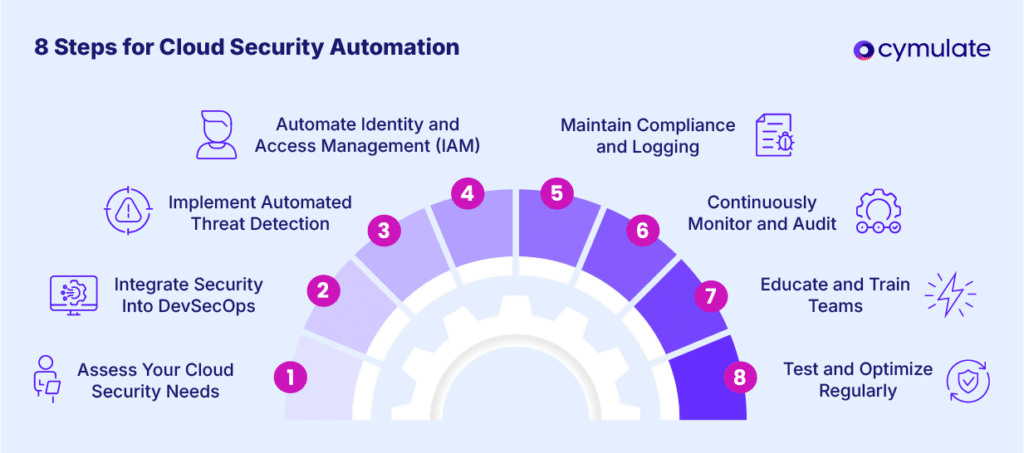
8 Steps for Successful Cloud Security Automation
To implement and execute a successful cloud security automation strategy, consider the following steps:
- Assess your Cloud Security Needs: Begin by evaluating your organization’s security requirements, potential vulnerabilities and automation goals. This initial step will help customize your approach to maximize efficiency.
- Integrate Security into DevSecOps: Embed security practices into your development and operations workflows. This step allows for early detection and mitigation of vulnerabilities during the development cycle. Utilize IaC tools to automate the provisioning and management of cloud resources, that will ensure application consistency and reduce manual errors.
- Implement Automated Threat Detection: Use advanced monitoring tools that leverage artificial intelligence (AI) and machine learning (ML) algorithms to detect and respond to anomalies or suspicious activities in real-time.
- Automate Identity and Access Management (IAM): Streamline the management of user roles, access permissions and authentication processes with automation to mitigate the risk of unauthorized access.
- Maintain Compliance and Logging: Automate compliance checks and logging mechanisms to ensure adherence to industry standards and regulatory requirements.
- Continuously Monitor and Audit: Deploy tools like Cymulate Exposure Validation Platform that provide continuous monitoring and generate automated reports to track the performance of your security systems.
- Educate and Train Teams: Develop automated workflows or playbooks (scripts) of how to handle a security incident and regularly update these playbooks as threats continue to evolve. Regularly conduct employee training on the automated cloud security tools to effectively foster a culture of collaboration between security, IT and development teams.
- Test and Optimize Regularly: Cloud Security Automation doesn’t end once implemented, it must be regularly tested to identify any gaps or inefficiencies to allow for refinement and full security.
Benefits of Automating Your Cloud Security:
Cloud security automation offers organizations a powerful approach to strengthening their security posture by streamlining and optimizing threat detection, response, and policy enforcement, reducing risk exposure and operational overhead. As cloud environments grow in complexity, automation ensures that security measures remain effective and responsive to emerging threats, providing a proactive and efficient defense strategy. The benefits below are just some of how organizations can get ahead by utilizing cloud security automation:
- Proactive Threat Management: Automated systems allow for continuously monitoring for threats and response in real-time, reducing the opportunity of a successful attack and potential damage.
- Scalability: Organizations need automations due to their flexibility to scale seamlessly with growth of any size while ensuring security.
- Speed and Agility: Automated security tools enable and empower organizations to adapt quickly to new threats or vulnerabilities, maintaining a strong defense in dynamic environments.
- Consistency and Accuracy: Human errors are unavoidable and in security configurations they can lead to exploitable vulnerabilities. Automated processes ensure consistent application of security policies across the whole organization.
- Improved Compliance and Risk Management: With many industries subject to strict regulatory and compliance standards, automation helps streamline meeting those requirements, ensuring that any pertinent legal, finance, insurance systems, etc. are up to par, avoiding potentially costly penalties.
- Cost Efficiency: Introducing automation of any kind reduces the need for constant manual intervention, saving both time and labor costs, while ensuring consistent protection.
How Cymulate Helps Automate Your Cloud Security
With the strength of the Cymulate Exposure Validation Platform, we can deliver customers a comprehensive continuous security validation and threat exposure management analysis in real-time based on real-life scenarios. The Cymulate platform automates testing of malicious and sensitive activities in your cloud environment to assess if they are detected and prevented by your cloud security controls.
These fully automated, production-safe assessments can and should be run often for continuous validation, performance monitoring and to track any changes over time. Cymulate supports testing for major cloud providers, such as Azure, AWS and GCP and their security tools like, AWS GuardDuty and Google Cloud Security Command Center. This approach helps identify areas for improvement and ensures ongoing readiness against potential cloud threats.
In a recent IT Services and Consulting case study, an organization in India with 250k employees knew they needed to make a big change to keep pace with the threat sophistication levels.
“We have almost all the same security solutions in the cloud as we do on-premises, but how do we know if the controls are also effective in the cloud environment? Cymulate allows us to understand the level of our control effectiveness —we can validate our cloud controls and policies, understanding which attacks would be prevented and which would be detected.”
Being able to validate security controls across various layers of the cloud architecture, including applications, containers and infrastructure ensures that any organization can remain on the offensive and prepared for any vulnerability.