Cloud Security 101: Common Risks, Threats and Challenges and How to Mitigate Them Efficiently
Cloud has become the latest frontier in the threat landscape as threat actors now focus their attention on exploiting cloud platforms. Common cloud misconfigurations are the root cause of many cloud data breaches, requiring continuous validation given the very dynamic nature of a cloud environment.
Statistics suggest that 82% of data breaches occurred in the cloud environment. Therefore, understanding cloud security risks, threats and challenges is crucial for maintaining a robust security posture. A secure cloud strategy not only safeguards against cyber threats but also ensures regulatory compliance and maintains the confidentiality, integrity, and availability of sensitive information, which is essential for customer trust and operational resilience.
Understanding the Difference Between Risks, Threats and Challenges
Let’s first start by understanding the core basic terminologies revolving around the span of this article, i.e., risks, threats, and security challenges.
- Risks are often associated with vulnerabilities existing in a cloud network or, more precisely, possibilities for data theft or damage.
- Meanwhile, a threat can be a malicious actor or a factor that acts upon critical information to disrupt critical operations and affect the data integrity of valuable information assets.
- Similarly, challenges could mean obstacles that make the implementation of cloud security solutions more difficult.

The Most Common Risks in Cloud Environments
A cloud security risk is a potential cause that can expose a vulnerability or damage a cloud’s valuable information assets that could compromise the security, privacy, confidentiality, integrity or availability (CIA) of data and systems hosted in a cloud environment. For maintaining a robust cybersecurity posture, it is critical for organizations to be aware of the most common cybersecurity risks, and how to protect against them using the right tools at the right time. Understanding the fundamental cloud security risks is critical to preventing them and protecting data and system integrity. Here are some significant cloud security risks:
- Misconfigurations: Cloud misconfigurations lead to situations like vulnerable public S3 buckets resulting from incorrectly setting up cloud resources. It can expose them to vulnerabilities, making them easy targets for malicious actors.
- Insecure APIs and interfaces: Threat actors can exploit vulnerable or improperly secured APIs and interfaces, which can help them gain unauthorized and unintended access to cloud services.
- Identity and access management (IAM) issues: Issues with IAM solutions can allow malicious threat actors to access your network systems and data, resulting in privilege escalation and compromise of critical data.
- Data breaches and data loss: Unauthorized access and fraudulent attacks can lead to data theft or loss of sensitive information, significantly compromising data privacy and security. It can have a direct and/or indirect impact on an organization, including financial losses, penalties and loss of brand reputation.
- Lack of visibility into cloud workloads: Cloud environments have become susceptible to cybersecurity threats in the absence of diligent and continuous monitoring since there is a lack of proper visibility into cloud workloads, making it more challenging to detect anomalies or security breaches efficiently.
Mitigating Cloud Security Risks
Mitigating cloud security risks is crucial to protecting sensitive information, ensuring business continuity and maintaining customer trust. Cloud security involves fortifying the entire cloud infrastructure against cyber threats and vulnerabilities, thereby preventing breaches, data loss and service disruptions. The following actions are vital in ensuring a significant level of mitigation:
- Ensuring proper configuration management: Proper configuration management involves correctly setting up and maintaining cloud resources to prevent vulnerabilities. It includes using automated tools to detect and rectify cloud misconfigurations, regularly auditing configurations, and adhering to best practices and security guidelines to reduce the risk of exposure.
- Using multifactor authentication and identity management tools: Multifactor authentication (MFA) and identity & access management (IAM) tools are integral to cloud security architecture because they provide an additional security layer by ensuring multiple verification methods before granting access to data to any user. Thus, they prevent unauthorized access, ensure that only authenticated users access sensitive data, and manage user permissions effectively.
- Adopting continuous monitoring and compliance checks: Cloud security governance involves monitoring and using tools and processes to observe and analyze cloud activities continually. This helps detect and respond to cloud security issues in real-time. Regular compliance checks ensure proper adherence to regulatory requirements and security standards. This helps mitigate potential risks and ensure a secure cloud environment.
Common Cloud Security Challenges
Cloud security threats are potential cybersecurity incidents that could compromise the confidentiality, integrity and availability of data and services in a cloud environment. They include malicious infiltration, data breaches, insider threats and ransomware in the cloud. Malicious actors can use these threats to explore vulnerabilities, which could lead to significant financial and reputational damage for the organization.
Malicious actors can take various forms and unleash their attack on a cloud network from near or far. They look for vulnerabilities to exploit to cause damage and disrupt business operations. They can be external agents or those inside an organization. Here are some examples.
- External threat actors and malicious groups: Infiltrators with nefarious intentions are the primary threat actors that can disrupt an organization's cloud resources. They use various malicious techniques, such as malware, ransomware and phishing, to steal data, extort money and disrupt services.
- Insider threats: Organizations must be wary of insider threats involving employees or contractors accessing sensitive information. These individuals could misuse their privileges maliciously or negligently to cause data breaches and operational damage.
- Nation-state actors and APTs: Significant threat actors include government-sponsored groups engaging in cyber espionage and advanced persistent threats (APTs) at the state level to gather intelligence, sabotage systems, and exert geo-political influence.
- Supply chain attacks targeting third-party services: Malicious attackers compromise the vulnerabilities in a third-party vendor network as a means to infiltrate larger organizations, exploiting their trust and access within the supply chain.
How to Address Cloud Security Threats
Cloud security threats must be neutralized to prevent financial and reputational losses. As threats to the cloud can originate from diverse sources, a multi-pronged approach is essential to prevent them. Organizations can fight these threats to preserve a health security posture using the following measures.
- Conducting regular threat assessments: Combating cloud security threats involves identifying and addressing vulnerabilities continuously by evaluating the organization’s security posture and potential threats to the cloud environment.
- Using advanced threat detection and response tools: Organizations must implement AI and ML tools to detect anomalies and effectively respond to security threats in real time. Advanced security tools based on disruptive technologies, such as AI and ML, can detect a threat with the highest efficiency and even predict a threat before it occurs.
- Securing your cloud supply chain: Vetting third-party vendors thoroughly is critical to ensuring effective cloud security. Any vulnerable spot in a vendor’s supply chain can open doors for malicious actors to an organization connected to it, irrespective of the strength of security precautions internal to the organization. Therefore, organizations must adhere to robust security practices to prevent breaches throughout the supply chain.
Cymulate Cloud Security Validation and Exposure Management
Securing cloud environments, particularly multi-cloud setups, requires precise, custom-tuned security solutions and rigorous best practices. Cymulate’s breach and attack simulations for the cloud test and validate security controls across multiple layers of cloud architecture, assessing the effectiveness of both prevention and detection in various phases, from pre-exploitation to post-breach scenarios.
For example, cloud workloads like Windows virtual machines (VMs) can be tested with Cymulate’s Endpoint Security module, while a cloud-based web application firewall can be assessed using the Web Application Firewall module—each tailored to enhance security for specific cloud components.
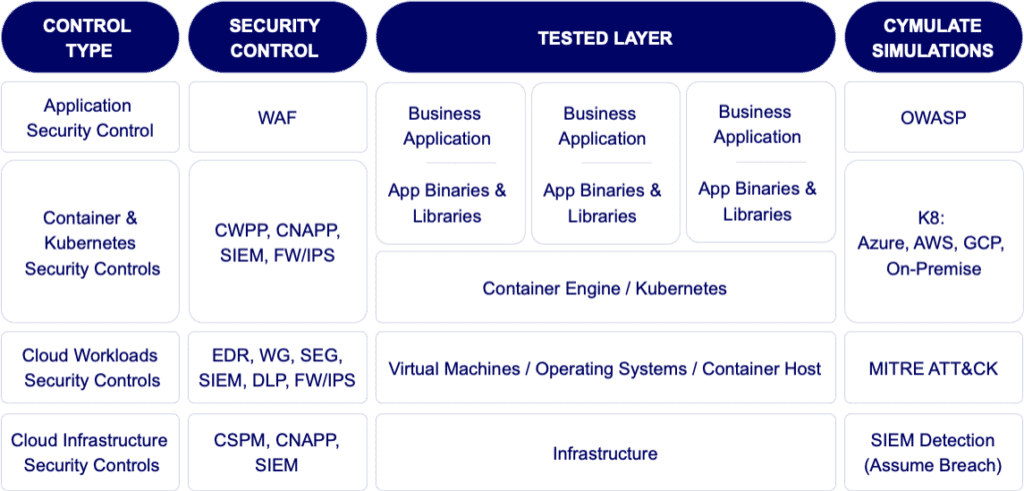
Cymulate’s Cloud Security Validation & Exposure Management follows these key steps to help address cloud security challenges:
- Validating Security Controls Against Emerging Threats: With the constant evolution of cloud security threats, regular updates and adjustments to security controls are essential. Cymulate ensures that defenses stay resilient by continually testing against new attack vectors.
- Continuous Cloud Configuration Testing to Detect Vulnerabilities Early: Automation reduces human error and bolsters cloud security efficiency. By automating penetration testing and scans, Cymulate helps detect and mitigate security gaps before they can be exploited.
- Exposure Management for Prioritizing Critical Risks: Cymulate prioritizes vulnerabilities by assessing and ranking potential risks based on impact and likelihood, allowing organizations to address the most critical cloud security issues first.