Cloud Security Monitoring: Best Practices and Tools

Cloud security monitoring is a mission-critical practice as enterprises increasingly operate in the cloud. As organizations migrate workloads to AWS, Azure and Google Cloud, they inherit new risks including misconfigurations, exposed credentials, shadow workloads and identity sprawl.
Traditional network visibility no longer suffices. Cloud security monitoring enables continuous visibility into cloud environments to detect threats, ensure compliance and maintain operational resilience in multi-cloud and hybrid ecosystems.
Key highlights:
- Cloud security monitoring is the continuous process of analyzing security events and configurations in the cloud to detect threats, anomalies and compliance gaps.
- Best practices include automated log analysis, least-privilege enforcement and exposure validation across cloud services.
- Cloud security monitoring tools combine CSPM, CWPP, SIEM and compliance automation of unified visibility.
- Cymulate empowers enterprises to streamline threat validation and improve resilience through continuous exposure management and automated testing.
What is cloud security monitoring?
Cloud security monitoring is the continuous process of collecting, analyzing and responding to security events within cloud environments. It focuses not just on performance metrics but on identifying misconfigurations, data exfiltration attempts, privilege escalations and compliance violations.
At its core, cloud security monitoring provides the real-time visibility needed to protect dynamic workloads and data across SaaS, PaaS and IaaS environments. It ties together logs, telemetry and behavioral analytics to detect indicators of compromise and enable faster incident response. An effective strategy is tightly integrated cloud security management to align visibility with governance, compliance and control enforcement.
Benefits of implementing effective cloud monitoring solutions
Cloud monitoring forms the backbone of modern cloud security. It transforms data into actionable intelligence, providing measurable business and security outcomes.
- Improved visibility and control: Gain centralized insight into multi-cloud assets, configurations and access patterns to detect anomalies before they escalate.
- Faster threat detection and response: Identify and contain security incidents quickly with automated alerting and orchestration.
- Stronger compliance alignment: Maintain audit-ready visibility for frameworks like SOC 2, ISO 27001 and GDPR.
- Operational efficiency: Reduce manual investigation workloads and improve DevSecOps collaboration through automation.
- Reduced business risk: Prevent costly data breaches and outages by proactively identifying vulnerabilities and misconfigurations.
According to IBM’s 2025 Cost of a Data Breach Report, organizations with fully-deployed security monitoring and automation saved an average of $1.8 million per breach compared to those without.
Enterprise cloud security monitoring tools
No single tool covers every cloud risk. Enterprises typically adopt a layered stack that combines posture management, threat detection, compliance and validation. The table below summarizes key categories of cloud security monitoring tools and their primary focus areas.
These technologies complement one another by covering distinct dimensions of cloud security controls and ensuring a holistic defense posture.
Also, here is a guide to cloud security assessment tools if those are potentially a better fit for the needs of your environment.
| Types of cloud security monitoring tools | key focus of these tools |
|---|---|
| Security Information and Event Management (SIEM) | Aggregation and correlation of cloud logs for threat detection; security event analytics, alerting |
| Cloud Security Posture Management (CSPM) | Identification of misconfigurations and policy drift; continuous compliance, risk scoring |
| Cloud Workload Protection Platforms (CWPP) | Protection of workloads at runtime; host security, container protection |
| Compliance and reporting tools | Auditing and reporting automation; policy checks, dashboarding |
| Exposure management platforms | Validation of real-world exploitability; attack simulations, prioritization |
Security Information and Event Management (SIEM)
SIEM platforms aggregate logs from cloud services, network devices and applications, correlating events to detect anomalies and intrusions. They’re essential for organizations requiring centralized monitoring and incident response workflows.
Key features:
- Real-time event correlation and alerting
- Integration with cloud service APIs and IAM logs
- Threat intelligence enrichment
Limitations:
- High data ingestion costs at scale
- Complex tuning to avoid false positives
Cloud Security Posture Management (CSPM)
CSPM tools continuously assess cloud configurations to detect compliance violations, misconfigurations and security drift.
Key features:
- Automated discovery of assets and policies
- Benchmarking against frameworks (CIS, NIST)
- Remediation recommendations
Limitations:
- Limited visibility into runtime activity
- Often reactive, requires integration with other platforms.
Cloud Workload Protection Platforms (CWPP)
CWPPs secure workloads (VMs, containers and serverless functions) across on-premises, hybrid and multi-cloud environments. They focus on protecting workloads at runtime against exploits and malware.
Key features:
- Runtime protection and intrusion prevention
- Vulnerability and image scanning
- Host and container isolation
Limitations:
- Can be resource-intensive
- Limited visibility into identity-related risks
Compliance and reporting
These tools automate the tracking and documentation of security and compliance requirements across complex environments. They help organizations maintain continuous audit readiness.
Key features:
- Automated evidence collection
- Policy enforcement dashboards
- Reporting for SOC 2, ISO, HIPAA
Limitations:
- Narrow focus on governance, not active defense
- Requires alignment with broader security stack
Exposure management
Exposure management platforms, such as Cymulate, bridge the gap between visibility and validation. Gartner predicts that by 2027, 60% of enterprises will adopt CTEM programs to improve risk prioritization and remediation policy. They simulate real-world attacks to prioritize remediation and validate control effectiveness.
Key features:
- Continuous attack simulation and validation
- Risk-based remediation insights
- Integration with SIEM, CSPM and SOAR
Limitations:
- Validation maturity is required to realize full value.

How to select the right cloud-based security management solutions
Choosing the right solution is about finding one that integrates, scales and supports intelligence without adding unnecessary complexity. A comprehensive approach blends visibility, validation and automation to sustain resilience in fast-changing environments.
For best results, organizations should evaluate vendors based on integration, scalability, prioritization, compliance and validation capabilities.
Integration with your existing stack
An effective cloud monitoring platform must integrate seamlessly with SIEMs, ticketing systems and DevOps pipelines. Look for APIs, webhook support and native connectors that unify telemetry across diverse platforms.
This reduces operational silos and enables automated alert enrichment, ensuring consistent response across environments.
Multi-cloud and hybrid coverage
Since most enterprises operate across AWS, Azure and GCP, multi-cloud visibility is essential. The best solutions extend coverage to hybrid cloud security environments, ensuring unified monitoring from on-prem to SaaS.
A platform should normalize data across providers and offer consolidated dashboards to eliminate blind spots.
Risk-based prioritization
Traditional alerting can overwhelm teams with noise. Look for monitoring tools that apply risk-based scoring to rank vulnerabilities and misconfigurations by business impact.
This approach ensures remediation efforts focus on the most exploitable and high-value risks, improving efficiency and reducing MTTR.
Compliance reporting and audit support
Regulatory requirements demand continuous documentation. Monitoring tools should provide audit-ready reports aligned to industry standards.
The capability not only simplifies compliance but also strengthens internal governance and cross-team accountability.
Exposure validation
True resilience comes from validation. This ensures that security controls perform as expected under attack conditions. Tools like cloud security validation test the effectiveness of defenses through automated simulations.
By validating exposures continuously, organizations can confidently assess their readiness and proactively close critical gaps before attackers exploit them.
Cloud monitoring best practices for enterprises
To move beyond reactive defense, enterprises must embed monitoring as a continuous, adaptive process. The following best practices elevate security monitoring in cloud computing from tactical visibility to strategic resilience.
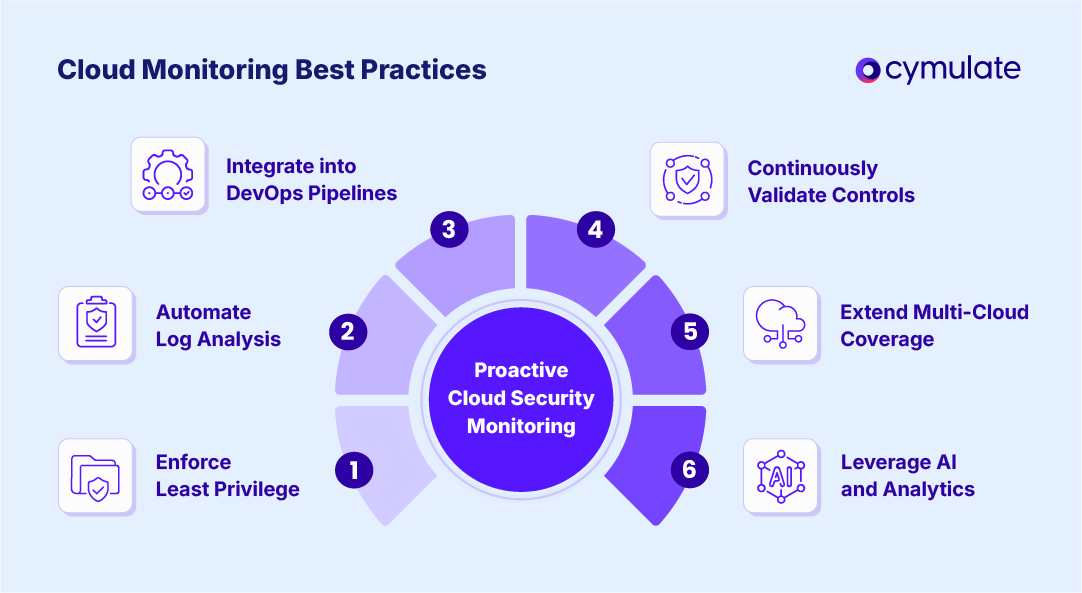
1. Enforce least privilege and IAM hygiene
Identity and access misconfigurations are a top cause of cloud breaches. Enforcing least privilege through IAM hygiene ensures only authorized users and services have the access they need.
Regularly review permissions, disable unused credentials and use just-in-time access models to minimize your attack surface.
2. Automate log collection and analysis
Automation accelerates detection and reduces manual overhead. Centralize cloud logs using a SIEM or native service like AWS CloudTrail and automate analysis through machine learning or rule-based engines.
This enhances the security of cloud services by detecting anomalies faster and reducing mean time to respond (MTTR).
3. Integrate monitoring into DevOps pipelines
Integrating monitoring into CI/CD pipelines allows security checks to run automatically before deployment.
Embedding security into development cycles ensures that vulnerabilities and misconfigurations are caught early. This reduces rework, and aligns DevSecOps teams around shared visibility.
4. Continuously validate security controls
Validation ensures that your cloud security assessment tools and controls are working as intended. Use breach and attack simulations to test detection, prevention and response workflows.
Regular validation helps teams understand how real-world threats behave across environments and strengthens their incident response posture.
5. Extend coverage across multi-cloud
Enterprises can struggle with fragmented monitoring across providers. A unified dashboard with standardized metrics provides a consolidated view of cloud risk.
Invest in cloud monitoring solutions that offer consistent telemetry, correlation and reporting across AWS, Azure and Google Cloud.
6. Future-proof workflows with AI integration
AI and analytics help predict risks before they materialize. Incorporating AI into your strategy can help keep up with cloud security trends. Anomaly detection, behavioral analytics and adaptive defense models will be able to evolve with emerging threats.
Streamline your cloud monitoring with Cymulate
Cymulate offers a robust and comprehensive platform that significantly enhances SaaS and hybrid cloud security through its validation capabilities. Cloud security validation enables you to optimize your cloud security controls and better protect the systems and data hosted in your cloud platforms.
The platform offers thousands of cloud attack scenarios to simulate high-privilege actions with an “assume breach” mindset, identifying exploitable vulnerabilities across AWS, Azure, and GCP.
These scenarios simulate real-world attacks, such as identity-based attacks, API vulnerabilities, and lateral movement attempts, allowing organizations to validate the effectiveness of their security controls. The full suite of test cases is completely production-safe and will not harm your cloud environment.
By combining visibility with validation, Cymulate enables organizations to transform cloud security monitoring from reactive defense to proactive resilience.
Book a demo today to discover how the Cymulate platform can help streamline cloud security monitoring for your enterprise.
Frequently asked questions
Logging and monitoring are vital in the cloud because they provide the visibility required to detect anomalies and potential breaches in real time. Without centralized logs, it’s nearly impossible to trace unauthorized access, configuration changes or data exfiltration attempts.
Moreover, comprehensive logging supports compliance and forensics. When integrated with automation, it accelerates response time, reduces manual investigation and supports continuous assurance for auditors and regulators.
Security monitoring in cloud computing matters because the dynamic nature of cloud resources introduces constant change and risk. Continuous monitoring identifies deviations, misconfigurations and malicious behaviors as they occur.
It also empowers security teams to respond proactively. With automated insights and correlated telemetry, organizations can maintain trust, compliance and resilience in distributed cloud environments.
Cybersecurity monitoring in the cloud works by collecting and analyzing logs, metrics and events from cloud services, applications and network layers. Tools like SIEM, CSPM and CWPP aggregate this data and apply analytics to detect threats.
Modern platforms use AI-driven correlation and anomaly detection to spot suspicious activity early. These insights allow teams to act on validated alerts rather than noise, improving accuracy and response efficiency.
An effective cloud monitoring strategy includes centralized log management, multi-cloud visibility, automated analysis and continuous validation. It should integrate across security and DevOps tools to ensure unified response and coverage.
Organizations should also define clear metrics (detection speed, false-positive rate and compliance adherence) to measure performance and improve maturity over time.
Key challenges include tool sprawl, data overload and inconsistent visibility across multi-cloud environments. Misconfigurations and lack of standardized policies often create blind spots that attackers exploit.
Organizations must also balance monitoring depth with cost and performance. Automating correlation and prioritization helps overcome these challenges while maintaining scalability.
Implementation timelines vary, but many organizations can achieve initial deployment within two to three months. This phase typically includes log integration, policy baselining and alert tuning.
Scaling across multi-cloud or hybrid environments may take longer due to custom API integration and compliance mapping, but platforms like Cymulate accelerate the process through automation and validation workflows.