Continuous Security Testing and Automated Cyber Risk Assessment Scores

Continuous security validation is the practice of challenging, measuring, and optimizing the effectiveness of an organization's security controls, infrastructure configurations, policy enforcement, and more on an ongoing basis.
Also called “security effectiveness testing,” the objective of continuous security validation is to enable constant optimization of an organization's security stack by testing it in production and providing security teams with immediately actionable insights to take corrective measures.
It achieves this goal by automating a comprehensive range of simulated threats, payloads, and attack tactics and techniques to uncover security gaps, weaknesses, and misconfigurations that may be exploited by potential adversaries.
The Advantages of Continuous Security Testing
Echoing a general move from binary, point-in-time security decisions to a more continuous and adaptive approach to implementing information security strategies, a continuous cyber risk assessment has emerged to address the reality of IT environments that are in constant flux, alongside an evolving threat landscape that requires greater focus and resources on early detection and response, rather than relying primarily on prevention (see Gartner’s CARTA model).
By implementing continuous security validation, organizations can better address the following:
Daily emergence of new strains
New variants of ransomware, trojans, cryptominers and cryptostealers surface every day, requiring preventive controls to be updated with the latest indicators of compromise (IoCs). Manually checking that these controls can block the latest phishing sites, infection points, command and control servers etc. is time-consuming and not practical. Continuous security validation operationalizes threat intelligence. It creates simulations of the latest threats for security teams to validate and optimize the effectiveness of their detection and prevention security controls and defend against them faster.
image
Evolving stealth techniques
Preventive IoC-based controls are useless against signature-less and fileless attacks, making behavior-based detection tools, such as deception honeypots, EDRs and EUBA tools essential for their detection. But how do you know if your machine learning and AI-based solutions are effective against these threats? By continuously testing their effectiveness against simulated cyber attacks, organizations can continually fine tune these tools’ configuration settings to enable their faster detection.
Frequent changes to the IT environment
Every day, IT environments change, whether it’s through deliberate network policy changes, the use of unvetted shadow IT, employees joining or leaving a company, or new software, hardware or virtual environments being deployed. Assessing the impact of these changes on an organization’s security posture removes blind spots that may be discovered as unpleasant surprises.
Frequent changes to the security stack
An often-overlooked area are changes in the security stack that inadvertently create security gaps. These can be created through human error, misconfiguration, or as a by-product of vendor software updates. Continuous security validation provides quality assurance to changes in the security stack.
Limited manpower and budget
Continuous security validation helps security leaders get the most out of their limited headcount and cybersecurity budget. By continually identifying gaps and prioritizing remediation efforts to where exposure is highest, security teams can extract the highest ROI out of their existing security stack. Plus, by having the tools and knowhow to improve their security posture, organizations are reducing their reliance on resource intensive infrastructure pen-testing, focusing them on pinpoint objectives or regulatory compliance audits.
State sponsored threat actors
Dozens of APT groups have been identified working for nation states for financial, political, and military gains. Equipped with zero-days that are found through research or purchased from private brokers, these groups have the money, time and skill required to carry out sophisticated, persistent attacks. By continually challenging security controls against techniques used by these groups, organizations can better position themselves for timely detection of these threats.
External touchpoints and supply chain attacks
Consumer-facing portals, health information exchanges (HIEs), financial services interconnected through payment gateways and automated clearing houses (ACHs), and enterprises automating their supply chain - all present a measure of security risk to an organization’s security posture. Configuration testing, including testing controls, such as WAFs (to prevent a CapitalOne-style breach), email gateways, infrastructure controls that limit lateral movement, and others, is critical to reducing the cyber risk created from these touchpoints and preventing supply chain attacks.
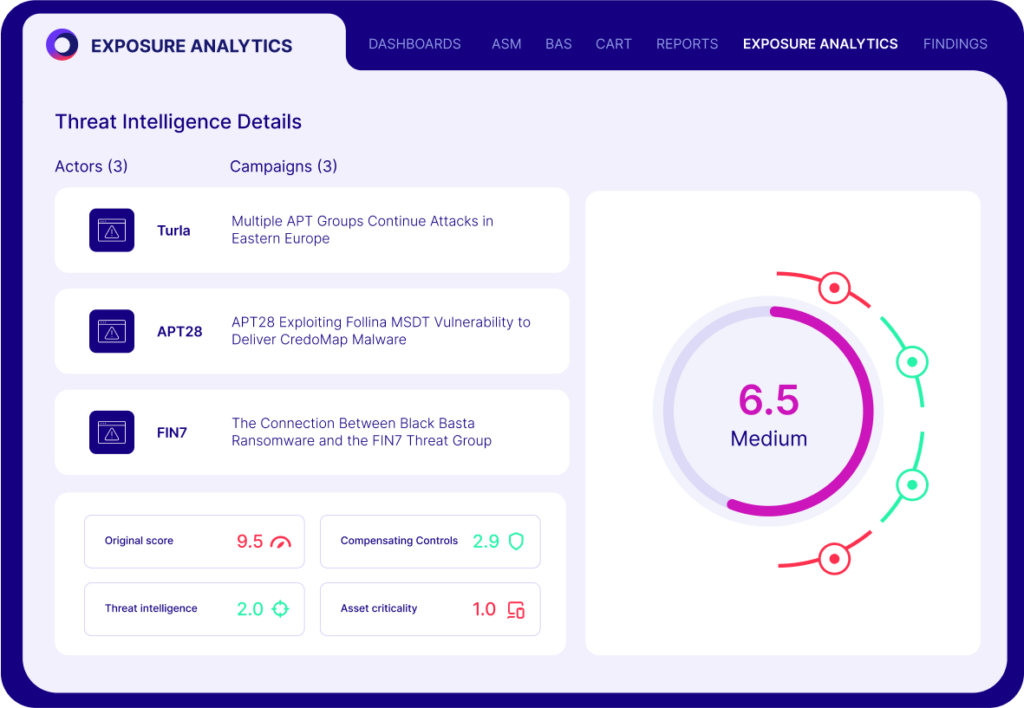
Turning Threat Intelligence into Real-Time Resilience
In a nutshell, imagine that you have at your disposal the accumulated skills of all your potential adversaries. Instead of wreaking havoc, they tell you where their attacks were successful, they tell you what you can do about it, and they do it on demand or all the time.
How is this achieved? Cymulate Research Labs stays abreast of the very latest threats and techniques, updating the platform daily with Immediate Threats Intelligence. They use the MITRE ATT&CK Framework to reference atomic executions and attack vectors for you to assure complete coverage.
The Framework also serves as a common language that can be used internally or with security service and technology providers. The accumulation of platform capabilities enables organizations to rapidly assess their resilience against a comprehensive set of attack simulations and latest threats.
Using automated breach and attack simulation, security teams can:
- Simulate cyber attacks across the full kill chain.
- Evaluate controls based on identified gaps.
- Remediate exposures using actionable insights.
- Repeat hourly, weekly, daily or whenever.