Cymulate IS the Evolution to Adversarial Exposure Validation
The 2025 Gartner® Market Guide for Adversarial Exposure Validation1 helps security and risk management leaders understand the key use cases of adversarial exposure validation and navigate the AEV solution market.
We invite you to take a look at the Gartner® report and identify the use cases and solution requirements.
With the convergence of automated offensive security testing into a single market, we believe that our unified exposure validation platform supports the core, recommended and optional capabilities that Gartner® advocates in the report.
While the Market Guide does not evaluate or rank specific vendors, the report highlights use cases, mandatory functionality and common features that we believe read like the Cymulate product documentation table of contents.
Cymulate Innovation Goes Beyond Breach and Attack Simulation
Since 2016, Cymulate innovation has provided the most advanced and easiest to use SaaS platform for automated security validation. We started with breach and attack simulation (BAS) to make automated controls testing accessible for every organization. We built on that success to offer more advanced testing geared toward red teams to build and customize attack chains and campaigns. We then added automated pen testing to target testing on specific environments and assets.
By focusing on the core outcomes for both offensive (red) and defensive (blue) security teams, Cymulate is the evolution to adversarial exposure validation. We cover the use cases with essential capabilities in a platform and workflows for security teams to adopt exposure management.
Exposure Validation Use Cases
Security buyers now have more choices than ever for breach and attack simulation, automated red teaming and automated pen testing. Security leaders need clarity to evaluate their options around use cases and the core features required to deliver.
Today, more than 1,000 security professionals rely on Cymulate to not just validate their security but improve overall security posture by:
- Maximizing threat prevention
- Optimizing threat detection
- Scaling red teaming and offensive testing
- Tuning cloud security for visibility and maximum protection
- Prioritizing exposures
The Gartner® report has a more concise view of adversarial exposure validation use cases.
“Solutions in the AEV market consist of technology that helps:
- Optimize defense
- Improve exposure awareness
- Scale offensive-testing capabilities”
Unlike other security validation products that focus on one or two of these uses cases, the Cymulate Exposure Validation Platform delivers the required technology, market expertise and history of customer success to fully deliver on every aspect of these use cases.
A few years ago, it would not be uncommon for blue teams to deploy breach and attack simulation to validate controls and for red teams to buy a separate solution for automated penetration testing. Today, Cymulate customers enjoy the benefits of a single, unified validation platform that serves both blue and red teams to automate testing for their specific needs and collaborate in a joint interface for purple teaming exercises, with live data simulations that validate prevention, SOC response time and response playbooks.
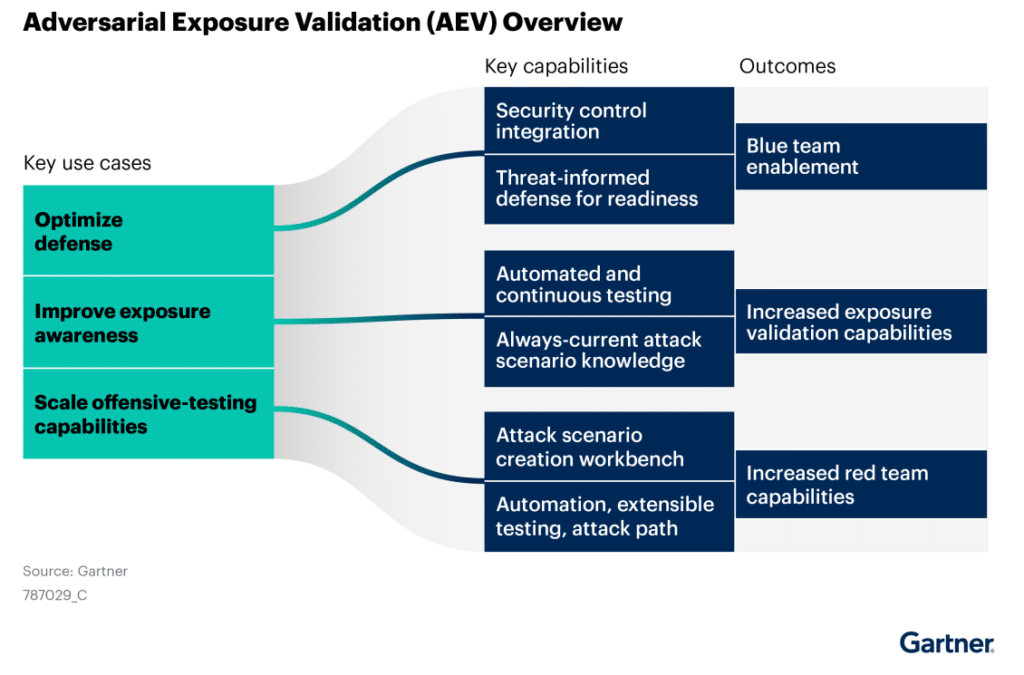
Figure 1. This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from https://cymulate.com/report/2025-gartner-market-guide-for-adversarial-exposure-validation/
Adversarial Exposure Validation Required Features
We feel the Gartner® Market Guide is a great resource for security teams considering automated security validation for the first time, replacing existing solutions or consolidating solutions to cover multiple use cases.
At the highest level, the market guide defines four mandatory features such as “Ability to scale defensive testing with vendor-supplied attack scenarios that require little to no hacking knowledge to execute and obtain results data.”
Gartner® also scopes out 11 common features such as “Ability to integrate with security controls via APIs or native interfaces to enhance the alignment of attack data with the defensive posture through contextualized content suggestions.”
The report goes deeper on each of the use cases and maps more detailed mandatory and common features for each of the three use cases – optimize defense, improve exposure awareness and scale offensive-testing capabilities.
While we can’t go into detail on each of these capabilities here, we believe that our unified exposure validation platform supports these mandatory and common features that Gartner® advocates in the report.
Blue, Red and Purple Teams
Cymulate provides the unified exposure validation for both blue and red teams. Blue teamers can focus on controls optimization with out-of-the box templates and daily threat updates to test the latest techniques without specialized hacking skills. Control integrations validate detection and provide actionable and automated remediation to strengthen controls for optimized defense.
For red teams, Cymulate provides its attack scenario workbench to either build attack chains and active campaigns from a library of more than 100,000 attack actions – or create and upload your own attack actions.
When blue and red teams come together for purple teaming exercises, Cymulate provides the deep integrations to map red team attacks to security control logs, alerts and response playbooks. At the end of the purple teaming exercises, Cymulate provides scorecards and heatmaps of strengths and weaknesses with actionable insights to improve cyber resilience.
Cymulate Goes Beyond Validation to Mobilize and Reduce Exposure
At Cymulate, we believe you don’t need another security assessment without a path to reduce risk – quickly, and preferably automated. This is where Cymulate really stands out from other solutions by going beyond the essential remediation guidance to push control updates and build custom detection rules for identified gaps.
When indicators of compromise can provide an immediate mitigation for a missed attack, Cymulate provides the option to automatically push these updates directly to endpoint, email and network security to block the threat.
To optimize detection for the missed attacks, Cymulate creates custom Sigma detection rules and then translates them into vendor-specific rules that can be directly applied to your EDR, SIEM and XDR.
Evolution to Exposure Management
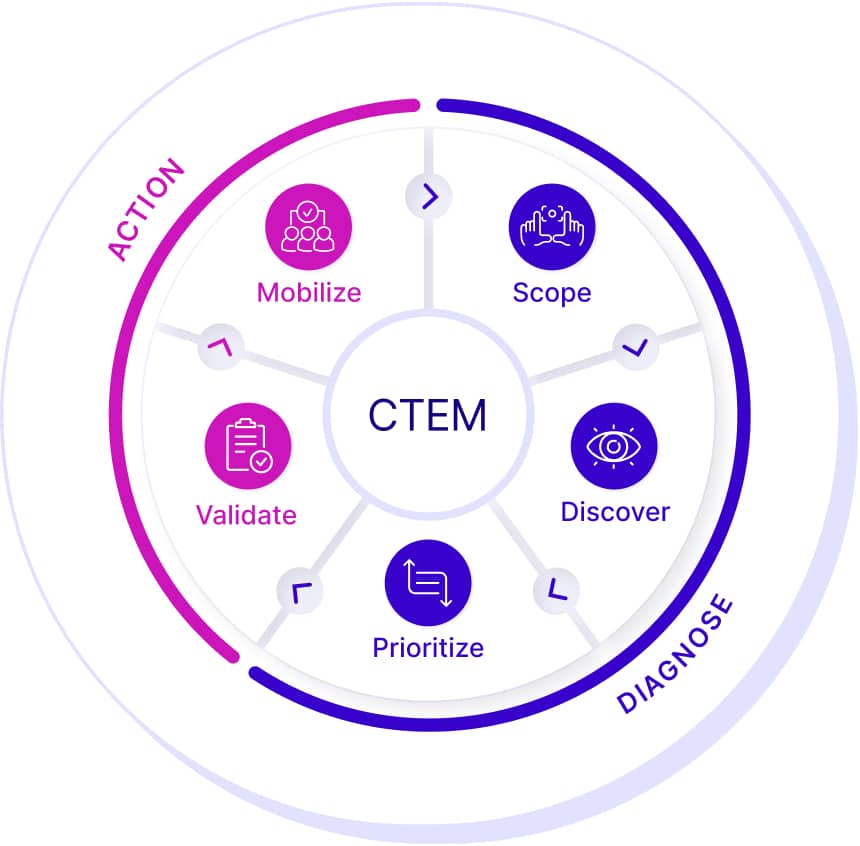
Beyond essential control optimization, more mature cyber teams are moving to adversarial exposure validation as an essential piece of their evolution to continuous threat exposure management (CTEM), and indeed, many Cymulate customers are embracing this program. CTEM is a continuous process that includes scoping, discovery, prioritization, validation and mobilization in a coordinated program to proactively manage threat exposure.
In a CTEM program, validation provides a key differentiation from traditional vulnerability management. Because security teams cannot possibly patch and remediate the hundreds (if not thousands) of new exposure findings each week, validation provides the filter of what’s truly exploitable, so security team can focus on the validated threat exposure.
CTEM also goes beyond typical CVEs to consider the un-patchable exposures that require risk mitigation of effective security controls. That proof of mitigation requires continuous validation.
“Adversarial exposure validation, via technologies like breach and attack simulation (BAS) and automated penetration testing, extends the use of evidence to find vulnerabilities. Gartner strongly advocates for the use of adversarial exposure validation, and it is a mandatory capability in CTEM.” 2
Cymulate automates this process of exposure validation by emulating the threat to prove the effectiveness of security controls to prevent or detect an exploit of the threat. If controls are proven to mitigate the threat, patching and configuration updates don’t have to be an emergency that disrupts operations; they can be included in the next schedule of updates. For the un-patchable exposures, Cymulate validation provides proof and evidence of mitigation.
Of course, there’s a lot more to exposure validation and CTEM. Cymulate provides the platform for continuous, ongoing testing against target environments and assets. We update the platform with new attack scenarios and techniques every day, so teams can test against the latest threats, and can even automate their inclusion in attack scenarios. And this includes attack paths and root cause analysis of the exposure.
The Future of Exposure Validation
Gartner® predicts that “through 2027, 40% of organizations will have adopted formal exposure validation initiatives, most relying on adversarial exposure validation technologies and managed service providers for maturity and consistency.”
Cymulate recognizes that security teams need options for how they implement exposure validation, so we’re working with technology solution providers and MSSPs to roll out new offerings designed for the needs of their specific customers who require services and bundled solutions – like a self-healing EDR.
We’re continuing to innovate by building automation and valuable applications of artificial intelligence that make exposure validation both easier to use and more advanced. We’re researching and building prototypes for both autonomous adversarial emulation and adaptive control updates where context-aware AI agents target objectives. Once breach possibility is proven, an AI agent with context of the security controls automates (or suggests) the mitigation in real time.
At Cymulate, we’re excited about both the present and the future of exposure validation. We invite you to download the report, identify the use cases and core capabilities for your security team, and please reach out when you’re ready to see Cymulate in action.
Click here for the full Gartner® report: Market Guide for Adversarial Exposure Validation
1 Gartner, Market Guide for Adversarial Exposure Validation, Eric Ahlm, Dhivya Poole, Angela Zhao, Mitchell Schneider, 11 March 2025
2 Gartner, How to Grow Vulnerability Management Into Exposure Management, Mitchell Schneider, Jeremy D’Hoinne, Jonathan Nunez, Craig Lawson, 8 November 2024
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.