Immediate Threat Analysis – New Dharma Ransomware Strain Found in the Wild
Originally an offshoot of CrySiS, the Dharma ransomware family has brought forth a new variant, as part of its ongoing creation of new strains. In this blog post, we analyze the latest variant found in the wild by malware researcher Jakub Kroustek.
Cymulate customers can check if they are vulnerable to this threat by running an Immediate Threat Intelligence simulation of this variant by logging in to their dashboard here.
Overview
Dharma has been operating since 2016 and the threat actors behind the ransomware continue to release new variants, the latest of which is currently not decryptable. You can keep apprised if the key to this latest variant has been uncovered at NoMoreRansomware.org.
This Dharma variant encrypts files and adds the extension, .nqix, which is completely different from the Dharma extensions seen to date; a tell-tale sign that it’s a new variant in the wild. It was also clear by the file’s signature that it’s a new Dharma strain.
The latest variant works like any other standard ransomware. As soon as the user executes the ransomware executable, the variant starts encrypting all the system’s files. All encrypted files are given the specific variant’s file extension, .nqix.
As with other run-of-the-mill ransomware, this Dharma strain removes the option to restore local system backups, called “shadow copies.” Most, if not all, ransomware variants do this, to make it impossible for victims to restore their systems without paying ransom to the threat actors behind the attack. Therefore, it is important for organizations to ensure they have offline backups, to enable resilience and business continuity in the event that they are affected by such ransomware attacks.
Like most ransomware strains, this one does not have lateral movement capabilities (unlike WannaCry), so it cannot move from one machine to another, and cannot infect additional workstations on the network.
Finally, judging from how this variant was written, it does not seem that the threat actor has a great degree of skill or sophistication. The variant is still effective, but it is rather simple, and does not seem to be written by a ‘professional.’
Dharma is usually disseminated via phishing. Not found in this specific variant, it notoriously lured users into installing the ransomware by offering to uninstall the ESET anti-virus from their system. The group’s use of a genuine, albeit old, ESET remover (opposite of installer) lent credibility to their attack. Distracted by their wish to remove the AV, users would not only remove ESET from their system, but also simultaneously execute the Dharma ransomware on their system, leading to its immediate encryption.
Basic Analysis
In this new variant, the extension it puts on encrypted files is. nqix as shown in the screenshot below.

The email address written for support is either support@qbmail[.]biz on the files that are encrypted – shown above, or reservesupport@cock[.]li on the ransomware notes – shown below:
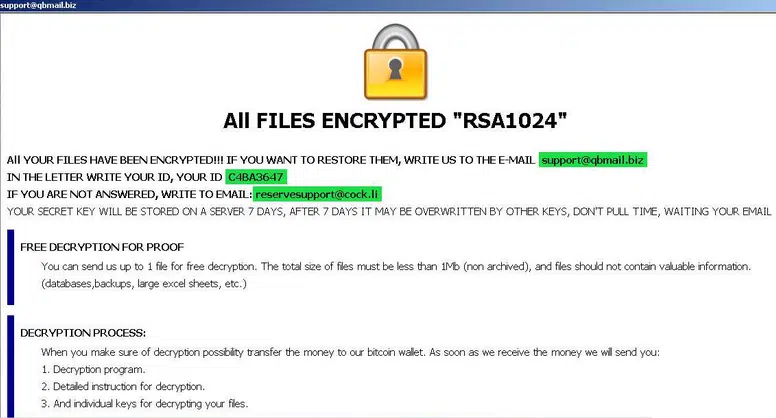
Dharma’s ransom note is shown above
- For persistence, this variant adds the binary payload to the registry at HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run. In case of failure it will add it at HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run, and will create a mutex and put the binary payload in C:\Users\<user>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
- To make sure the encryption functions on SQL-related machines and mailboxes, it stops services and kills processes, specifically those belonging to: Firebird Guardian, SQL and Microsoft Outlook (see further details in the deeper analysis below).
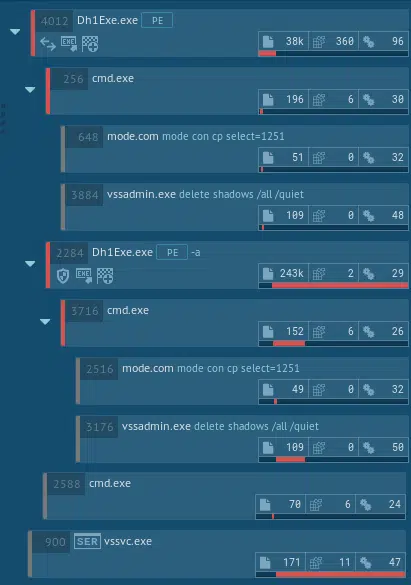
- Dharma deletes shadow copies with "vssadmin delete shadows /all /quiet" to make sure the backup option is not available to its victims.
- It then starts encrypting all files on the system, after which it drops the following pop-up message on the user screen, "ALL FILES ENCRYPTED RSA1024" with a specific ID.
The Any.run sandbox analysis session can be found here: https://app.any.run/tasks/c4a560dd-b21d-44f8-a8bf-8b007a80f1e3
The following is the Any.run analysis action tree (attack story):
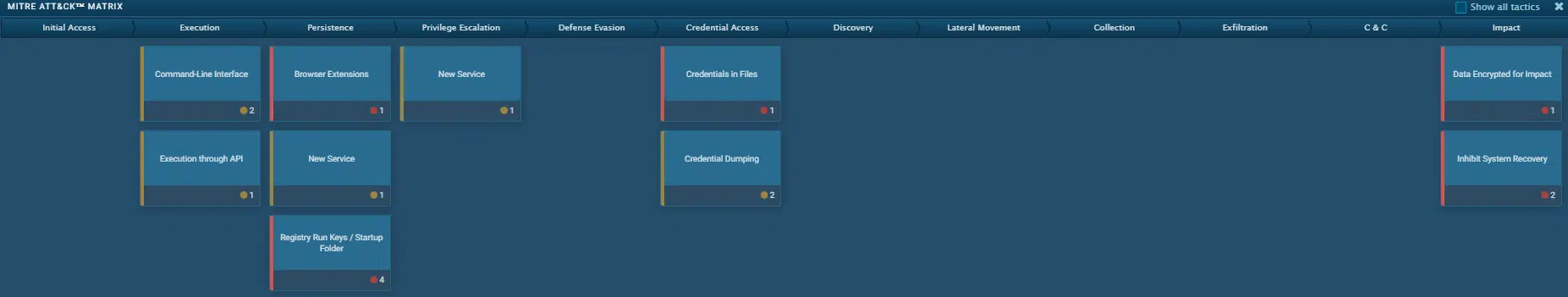
The Any.run analysis mapped the following MITRE ATT&CK™ techniques used in this ransomware:
Deep-Dive Dharma Malware Analysis
Additional characteristics:
Dharma ransomware implements its own runtime. It is not packed, but does obfuscate its imports by storing a rc4 encrypted array of dlls and import names
Execution information:
Decrypts internal structs, decrypt imports blob, load imports and zero out blob.
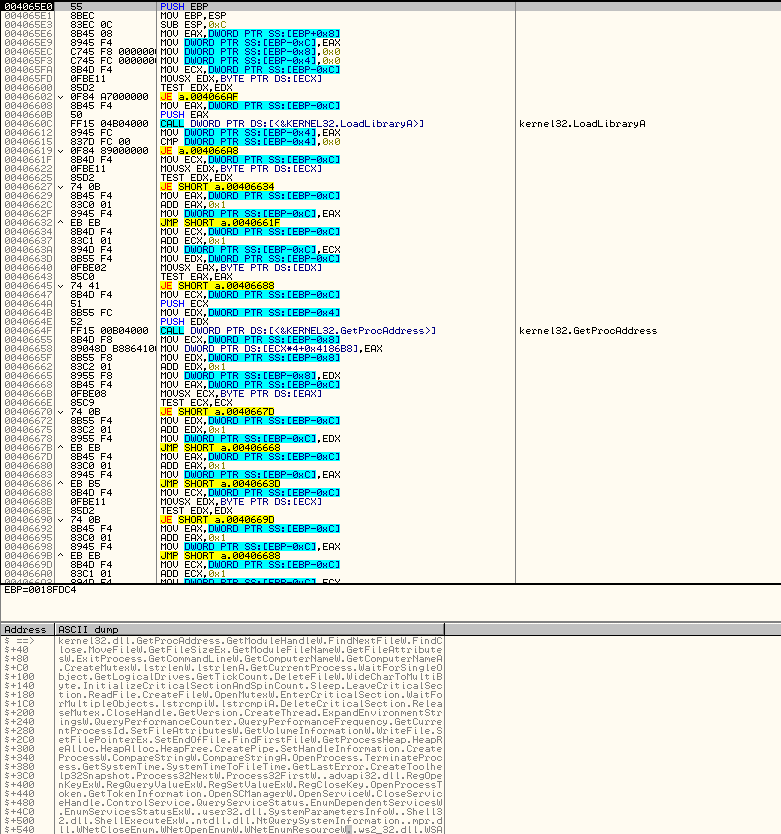
The above screenshot shows Dharma’s decryption process on potential victim’s system.
- Initiates own made PRNG (using different counters and sha1)
- Initiates inter process sync objects (Global\syncronize_BV6JP8A + Global\syncronize_BV6JP8U – Global\syncronize_ + BV6JP8(unique hardcoded sample id) + A/U(internal mutex type))
- Initiates target extensions dictionary (string bellow)
- Initiates a dictionary of services to stop and a dictionary of processes to close and act on them
- Sets autorun methods: – Copy the file to %windir%system32 or %appdata% and set ‘LOCAL_MACHINE/LOCAL_USER Software\Microsoft\Windows\CurrentVersion\Run’ – Copy file to ‘Startup’ folder – Copy file to ‘Common Startup’ folder
- Runs CMD with the following commands: “mode con cp select=1251\nvssadmin delete shadows /all /quiet\nExit” (The neat thing here is that it pipes the command to the CMD instead of giving it as a command line argument.)
- Start a process and service watchdog thread, whose sole purpose is to constantly stop and close a set of defined services and processes.
- Starts a thread which on certain conditions executes itself again with the ‘-a’ argument, which does nothing, probably a kind of ‘keep alive’ mechanism.
- Creates a thread responsible for network shares’ file encryption (WNetOpenEnumW and family API) and for new drive detection and encryption.
- Runs encryption routine: – For each logical drive, start two EncryptionWorker threads, one for encryption and the other for a different purpose as it is the same thread but using different parameters.
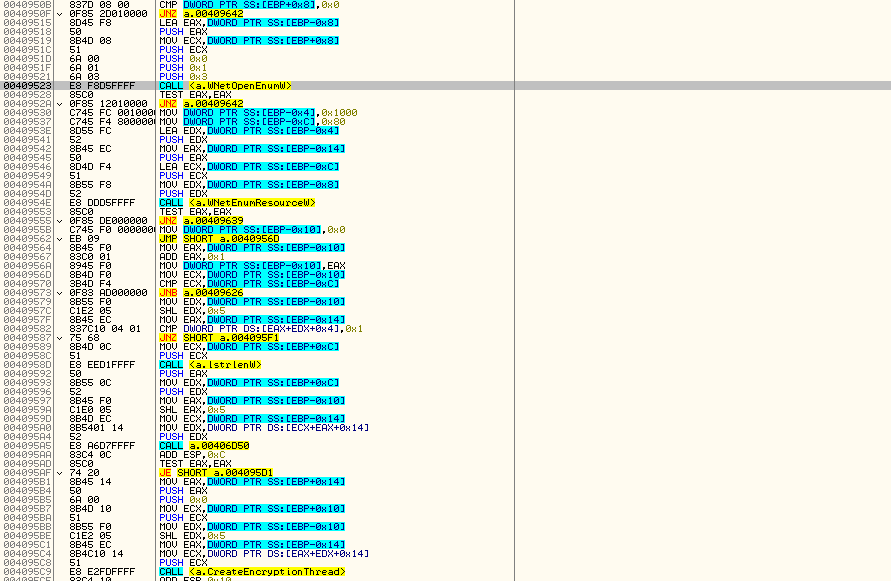
The above screenshot shows Dharma’s listing of logical drives and their encryption.
- Runs CMD commands again
- Drops ransom notes in various forms.
- ExitProcess
EncryptionWorker actions:
- Creates 4 encryption threads, which are responsible of encrypting files which are catalogued in a different thread (encryption is using aes-128 for data and rsa-1024 for encryption key).
- Creates a catalog thread, which is responsible of going through all the folders and sub folders and list matching files.
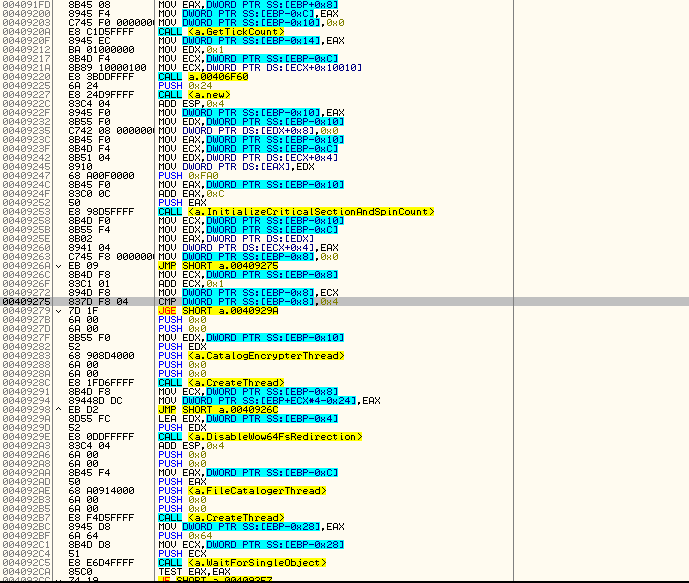
The above screenshot shows Dharma’s encryption flow, including the file extensions targeted for encryption.
Dictionaries used:
Full extensions target: “.1cd;.3ds;.3fr;.3g2;.3gp;.7z;.accda;.accdb;.accdc;.accde;.accdt;.accdw;.adb;.adp;.ai;.ai3;.ai4;.ai5;.ai6;.ai7;.ai8;.anim;.arw;.as;.asa;.asc;.ascx;.asm;.asmx;.asp;.aspx;.asr;.asx;.avi;.avs;.backup;.bak;.bay;.bd;.bin;.bmp;.bz2;.c;.cdr;.cer;.cf;.cfc;.cfm;.cfml;.cfu;.chm;.cin;.class;.clx;.config;.cpp;.cr2;.crt;.crw;.cs;.css;.csv;.cub;.dae;.dat;.db;.dbf;.dbx;.dc3;.dcm;.dcr;.der;.dib;.dic;.dif;.divx;.djvu;.dng;.doc;.docm;.docx;.dot;.dotm;.dotx;.dpx;.dqy;.dsn;.dt;.dtd;.dwg;.dwt;.dx;.dxf;.edml;.efd;.elf;.emf;.emz;.epf;.eps;.epsf;.epsp;.erf;.exr;.f4v;.fido;.flm;.flv;.frm;.fxg;.geo;.gif;.grs;.gz;.h;.hdr;.hpp;.hta;.htc;.htm;.html;.icb;.ics;.iff;.inc;.indd;.ini;.iqy;.j2c;.j2k;.java;.jp2;.jpc;.jpe;.jpeg;.jpf;.jpg;.jpx;.js;.jsf;.json;.jsp;.kdc;.kmz;.kwm;.lasso;.lbi;.lgf;.lgp;.log;.m1v;.m4a;.m4v;.max;.md;.mda;.mdb;.mde;.mdf;.mdw;.mef;.mft;.mfw;.mht;.mhtml;.mka;.mkidx;.mkv;.mos;.mov;.mp3;.mp4;.mpeg;.mpg;.mpv;.mrw;.msg;.mxl;.myd;.myi;.nef;.nrw;.obj;.odb;.odc;.odm;.odp;.ods;.oft;.one;.onepkg;.onetoc2;.opt;.oqy;.orf;.p12;.p7b;.p7c;.pam;.pbm;.pct;.pcx;.pdd;.pdf;.pdp;.pef;.pem;.pff;.pfm;.pfx;.pgm;.php;.php3;.php4;.php5;.phtml;.pict;.pl;.pls;.pm;.png;.pnm;.pot;.potm;.potx;.ppa;.ppam;.ppm;.pps;.ppsm;.ppt;.pptm;.pptx;.prn;.ps;.psb;.psd;.pst;.ptx;.pub;.pwm;.pxr;.py;.qt;.r3d;.raf;.rar;.raw;.rdf;.rgbe;.rle;.rqy;.rss;.rtf;.rw2;.rwl;.safe;.sct;.sdpx;.shtm;.shtml;.slk;.sln;.sql;.sr2;.srf;.srw;.ssi;.st;.stm;.svg;.svgz;.swf;.tab;.tar;.tbb;.tbi;.tbk;.tdi;.tga;.thmx;.tif;.tiff;.tld;.torrent;.tpl;.txt;.u3d;.udl;.uxdc;.vb;.vbs;.vcs;.vda;.vdr;.vdw;.vdx;.vrp;.vsd;.vss;.vst;.vsw;.vsx;.vtm;.vtml;.vtx;.wb2;.wav;.wbm;.wbmp;.wim;.wmf;.wml;.wmv;.wpd;.wps;.x3f;.xl;.xla;.xlam;.xlk;.xlm;.xls;.xlsb;.xlsm;.xlsx;.xlt;.xltm;.xltx;.xlw;.xml;.xps;.xsd;.xsf;.xsl;.xslt;.xsn;.xtp;.xtp2;.xyze;.xz;.zip;”
Noted as ‘Valuable’ extensions target by Dharma author: Documents: .doc, .docx, .pdf, .xls, .xlsx, .ppt Archives: .zip, .rar, .bz2, .7z Dbf: .dbf 1c8: .1cd Jpg: .jpg
Skip targets: “boot.ini”, “bootfont.bin”, “ntldr”, “ntdetect.com”, “io.sys”
Skip folder: expanded “%windir%”
Services to stop: “FirebirdGuardianDefaultInstance”, “FirebirdServerDefaultInstance”, “sqlwriter”, “mssqlserver”, “sqlserveradhelper”
Processes to close: “1c8.exe”, “1cv77.exe”, “outlook.exe”, “postgres.exe”, mysqld-nt.exe”, “mysqld.exe”, “sqlservr.exe”
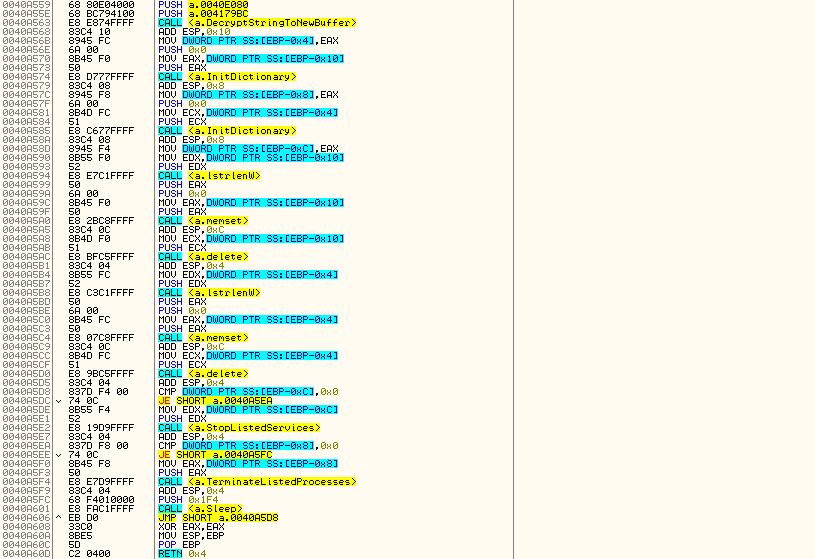
The above screenshot shows where Dharma stops services and closes processes.
Mitigation and Countermeasures
- Make sure you have a business back-up strategy in place, including offline backups, as local restore points are ineffectual since Dharma first removes them prior to encryption.
- Make sure you have a well-configured and up-to-date AV, EDR, and Email gateway solutions in place to defend against known threats and behaviors.
- Make sure you provide employees security awareness training – whether completed with a product or by your security expert.
Indicators of Compromise
Monitor the following indicators of compromise (IOCs) on your SIEM system and make sure they are blocked in all relevant security controls (AV, EDR, Email Gateway, etc.):
- 9b96be6c2ac05decb4b8d41469cb864e
- 9a77e8be9dd41d0e9b8a77e9a2abf4de
- 0e54c3ae592f46def82c6b153bb642c8
To know if your organization is vulnerable to Dharma, and the very latest Immediate Threats circulating in the wild, including ransomware, worms, Trojans and cryptominers and more, get started with Cymulate’s Breach and Attack Simulation.


